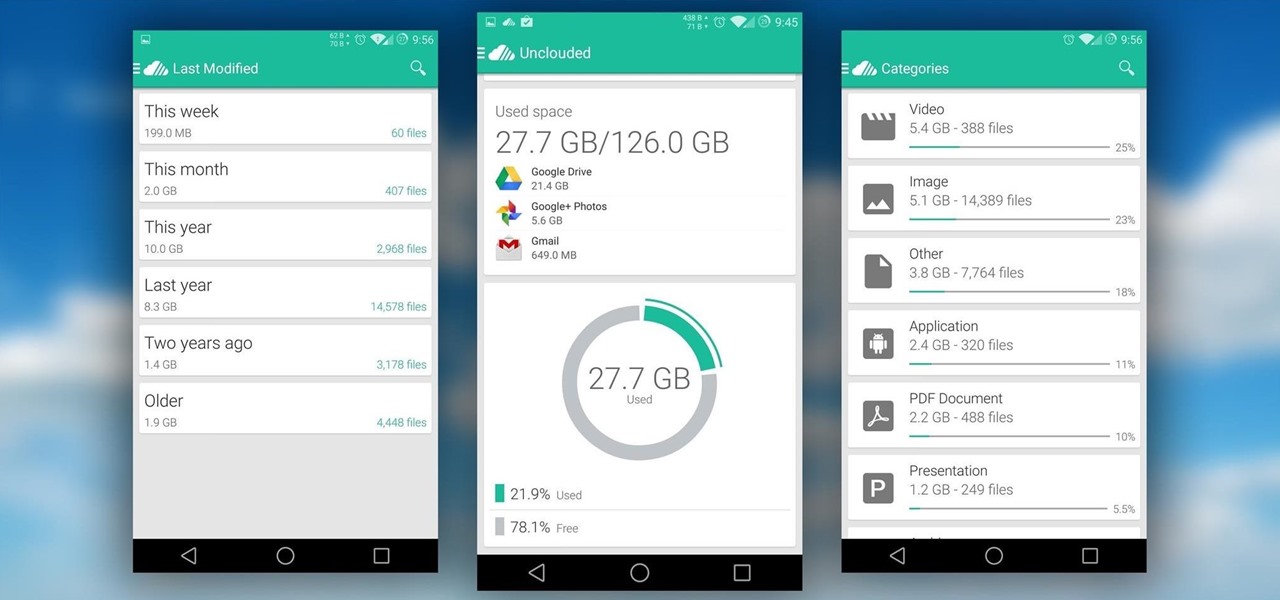
It seems like every cloud service out there is offering tons of upgrade options and free promotions to give people as much space as they need to store their files online. I personally have over 100GB of Google Drive space which is shared between multiple computers, phones, and tablets, so keeping track of everything can be a huge pain in the ass.

The next generation gaming systems are so close to release I can almost taste the plastic. The new PlayStation 4 is set to be released in just a couple days on Friday, November 15th, but if you're like me, there's only one thing preventing you from upgrading in a second.

With the global COVID-19 pandemic preventing Pokémon GO players from venturing into the real world, developer Niantic has adapted the game for trainers to play in a socially-distanced manner.

One of the main goals of Google Wifi (and Nest Wifi after it) is to make managing your internet connections as simple as possible. A great example of this is how easy it is to prioritize one device and allot it more bandwidth when your network is bogged down with other traffic.

Apple just released the first developer beta for iOS 13.4.5 on Tuesday, March 31. The update follows the previous week's stable release of iOS 13.4.

The coronavirus continues to disrupt the tech industry, including the augmented reality segment, with Apple and the iPhone the latest to feel the impact.

After dipping its toes into the AR cloud arena last year, Ubiquity6 is now jumping in with both feet this year.

While Magic Leap World gets its share of fun apps for playing with Porgs, watching TV, and exploring the ocean's depths, developers are making a strong business case for the Magic Leap One as well.

While the technology companies continue to drive forward with autonomous vehicles, Nissan's vision of the future of self-driving automobiles lies in a cooperative experience between human and machine, facilitated by augmented reality.

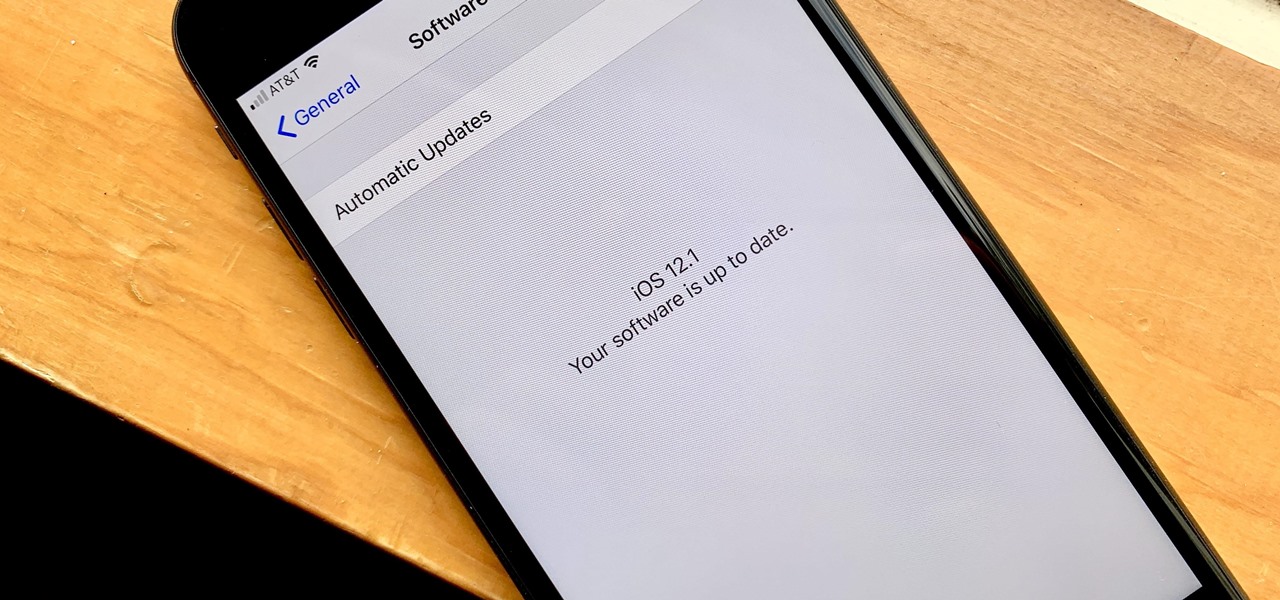
Apple released the first major iOS 12 update Tuesday, Oct. 30, just hours after the company's iPad and Mac presentation. While iOS 12.1 is the first official update to hit iPhones since iOS 12.0.1, beta testers had enjoyed an exclusive first-hand look at all the new features the latest OS has to offer. So what's new in iOS 12.1?

Apple revealed three new iPhone models on Wednesday, Sept. 12, at its "Gather Round" event in Cupertino, as well as announced the official release date of iOS 12, its newest mobile operating system. If you missed it and want to watch the full event, here's how to do it on your computer, smartphone, or Apple TV.

The Augmented World Expo is winding down in Santa Clara, where Qualcomm, Vuzix, and Meta Company were among the companies making big announcements.

Before the Sept. 2017 event held by Apple, we thought the new iPhone X would come in three different colors. While only a Space Gray and Silver option made it to the Nov. 2017 release, the missing third hue may finally be on its way, if the latest rumors are to be believed. If you can't wait for the new Blush Gold color, here's when and how you can expect to get your hands on one.

This week, saw two companies leaning on AR to prop up their financial futures. On one hand, Apple made quite a bit of AR-related news ahead of its quarterly earnings report next week. On the other hand, Vuzix launched a pre-order program for its Blade smartglasses and closed the largest financing deal in the company's history to fuel its ongoing headset production.

Update 1/17: Tim Cook chimed in about the upcoming iOS upgrade with expanded battery health data. We'll expand on that below.

A Russian augmented reality startup wants the next frontier in real estate to be augmented reality estate.

According to Digi-Capital, investors poured $1.8 billion into augmented and virtual reality companies over the last 12 months, including $300 million in the third quarter. These investments are not made without a means to monetize products and services.

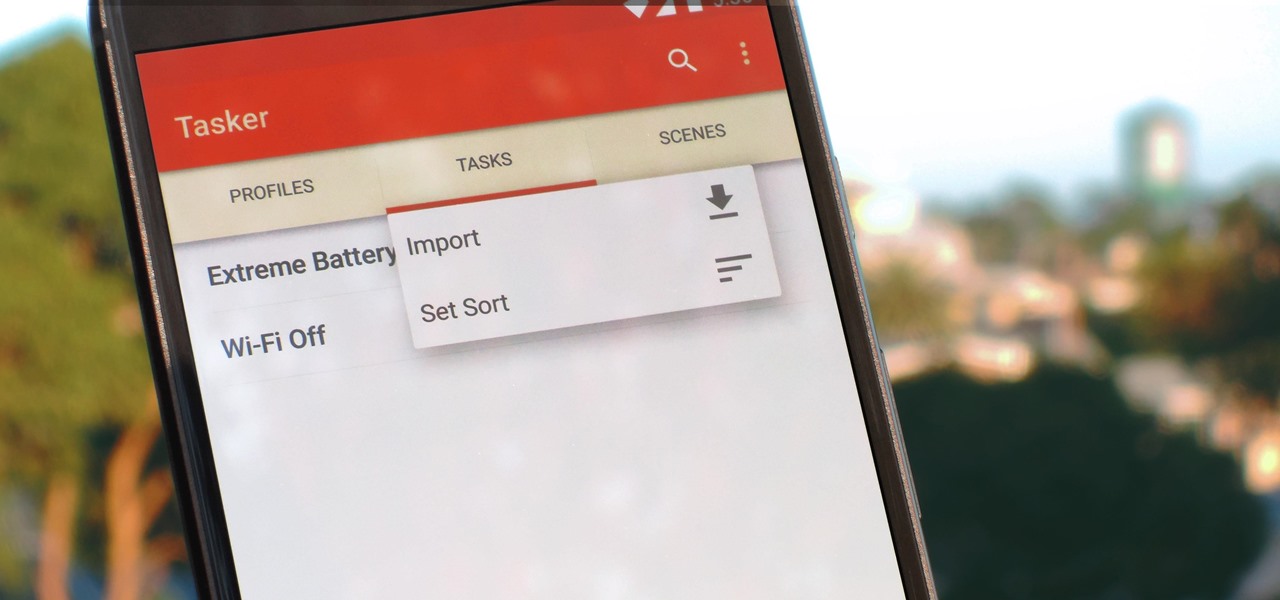
Regardless of what you're trying to accomplish with Tasker, there's a good chance that someone else has already walked through the same steps. If you're unfamiliar with creating tasks and working with profiles, simply importing someone else's work would be a great shortcut. After all, there are 2 billion Android devices out there, so someone must've created a setup that suits your needs, right?

Elon Musk's SpaceX is launching the world's most powerful rocket. The Tesla founder and CEO says the company is about to go through "manufacturing hell" to make delivery schedules for its new Tesla 3. Somehow, Musk says Tesla will offer Level 5 driving (so you can take a nap while your car drives you to and from work) within two years.

If you are an NYC commuter like me, then I'm sure you know how bad the city's transportation has gotten.

Results of an early-stage clinical trial of an HIV vaccine could mean a hoped-for breakthrough in the battle against AIDS.

We might think of Zika as a mosquito-borne virus that effects developing fetuses, but, it also can be passed through sex by either a man or a woman, just like herpes and other STD viruses. New research has shown that vaginal bacteria can inhibit sexually transmitted Zika virus and Herpes Simplex Virus-2 in women.

I have spent a good portion of this year traveling between cities and various emergent technology conferences and events. Most of these events have been really good, but in terms of augmented and mixed reality, the Augmented World Expo, in its eighth year running, definitely stood above the rest.

Cruise Automation is actively seeking to recruit a lead engineer to head its development efforts of 3D maps with expertise in city environments, signaling the GM driverless unit's move towards a mobility-as-a-service business model.

The US driverless market has become a competitive – and crowded – arena, with big names like Google, Apple, Uber, and even Intel intent on leading the pack. Not to be outdone, the EU is also getting in on the automated car action with self-driving fleets launching in both the UK and the Netherlands within the next two years.

Obstetric tetanus in an unvaccinated Amish woman after a home birth has emphasized the need for preventative healthcare.

According to Electrek, Tesla CEO Elon Musk, in a covert conference call with a select few investors, commented in detail about his plan to have Tesla's Model 3 driving on the road earlier than we all expected.

Before the iPhone 7 models were released, there were many rumors pointing to the inclusion of wireless charging, which obviously didn't happen. Now the rumor mill is back at it again for Apple's next smartphone, most likely being called the iPhone 8, and the possibility of wireless charging is more certain this time.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

You're at your friend's house. All you've heard about all day is his new laptop. He's got a brand new top-specced MacBook Pro, and he won't stop going on about it. It particularly annoys you as all you've got is a 4 year old cheap laptop, even if it is running Linux.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

Think eating food is as easy as putting it in your mouth? It's considerably more complicated than that. Your brain plays a big role in determining what and how you eat. Understanding how your brain interprets food choices is key to managing your eating habits.

While their merger with Microsoft has lead to a seemingly complete halt of new device development, some Nokia employees are still hard at work to bring new software to the table.

Google recently released a new mesh router known as Nest Wifi. The updated and rebranded Google Wifi brought many improvements, such as faster processing power and an increased level of wireless security called WPA3. But while it's not enabled by default, you can still get the new WPA3 security on your original Google Wifi.

We may or may not see Apple's long-awaited take on AR smartglasses this year, but the company is more than getting its practice swings in with its current wearables business, which hit record revenue in 2019 according to financial results released this week.

New year, new me. You finally committed to working on the best physical you by going to the gym multiple days a week. Except about an hour in, you start getting really tired of it all. Before you run to the exit, pick up your phone.

Stadia is a lot like an Xbox or PS4, except there's no console — the games just stream from Google's servers to your phone, computer, or TV. But Stadia is limited to Pixel phones for right now, and when Google does expand support, it will still only be for select phones. Thankfully, there's a workaround for that if you're rooted.

Augmented reality plays a key role in the evolution of adjacent technologies, such as 5G connectivity and brain-control interfaces (BCI), and the business news of the week serves up proof points for both examples.

The recent Oculus conference in California revealed just a bit more about Facebook's secretive plans to compete in the augmented reality space with its own wearable devices.

This week, Next Reality published profiles on the leaders in augmented reality hardware industry, with Magic Leap CEO Rony Abovitz topping the list. So, it should be no surprise that two app makers want to align themselves with Magic Leap's flagship product.