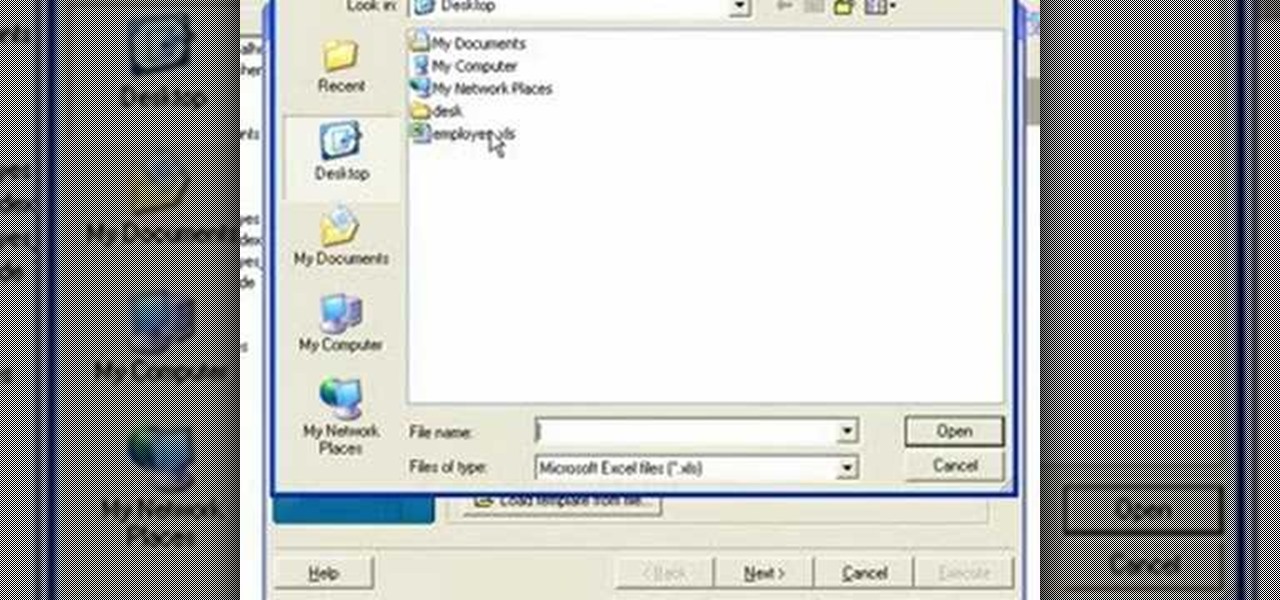
If you're new to DreamCoder for MySQL, one of the first things you may want to know how to accomplish is how to import data to a remote MySQL database. Happily, this tutorial will walk you, step by step, through the process. Take a look!

This MS Office software tutorial gives tips and tricks on integration between Access and Outlook. Access is Microsoft's database software and Outlook is the email software. So if you need to work with your database and email at the same time, check out this tutorial on integrating Access 2007 with Outlook 2007.

Learn how you can plant and care for sweet peas with this gardening tutorial. Sweet peas are one of the best annual climbing plants for the garden and they can be grown in several different ways to get a superb display of flowers through the summer months. Traditionally sweet peas were sown in the autumn and planted out in early April, but spring sown plants can be planted out into May and will still flower well, albeit slightly later. If you haven't sown any seeds but would like to grow some...

SQLite is a small C library that implements a self-contained, embeddable, zero-configuration SQL database engine. SQLite implements a large subset of SQL-92 and stores a complete database in a single disk file. The library footprint is less than 250 KB making is suitable for use in embedded devices and applications where memory space is scarce.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

Most of us have never put much thought into this, but the question needs to be asked — what exactly happens to all of our online accounts when we die? No, the internet won't just know and delete accounts for you, so you need to plan for life's one guarantee. Because without a plan, things become a lot harder to sort out.

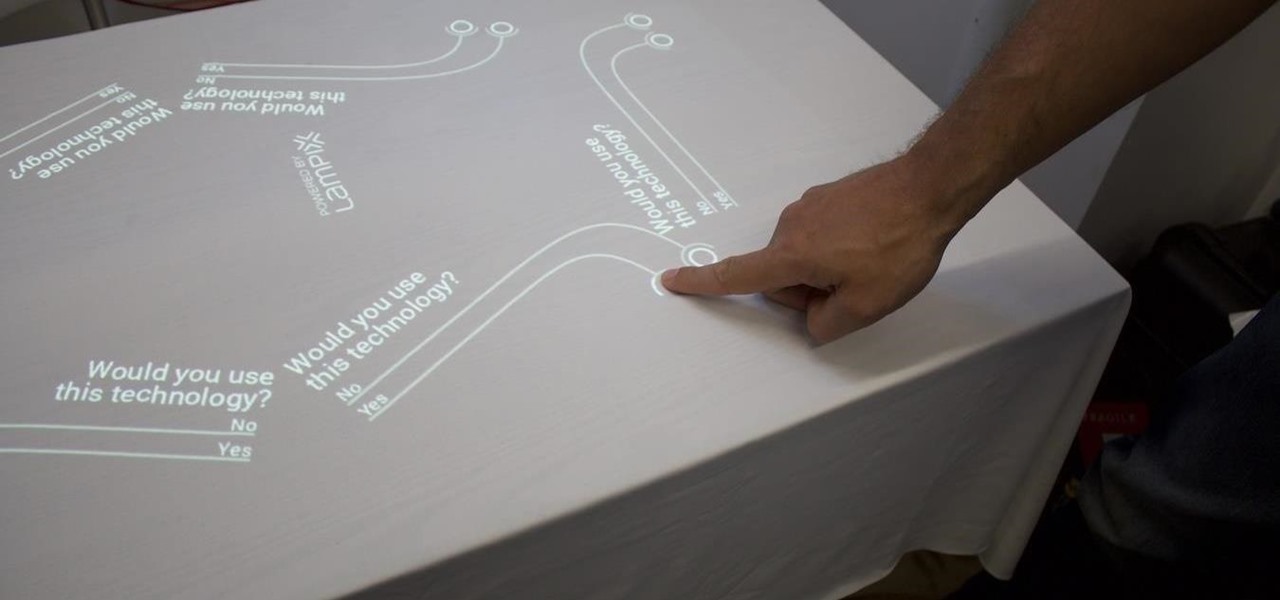
Over the past week, companies took a variety of approaches to investing in augmented reality. Lampix is backing its own effort to build an ecosystem for augmented reality platforms. Nokia and Xiaomi are teaming up on numerous fronts, potentially including augmented reality.

Greetings all. I'm back with another informational review of the diversity of utilities for use in the sphere of hacking at your disposal. Today we are going to cover the insides of CUPP (Common User Passwords Profiler) in its entirety. The tool is very basic in nature, as there is little to no configuration needed to get cracking (worst pun ever). So let's get started, shall we?

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

Welcome back, my aspiring hackers! As mentioned several times in previous Linux tutorials, nearly everything in Linux is a file, and very often they are text files. For instance, all of the configuration files in Linux are text files. To reconfigure an application in Linux, we simply need to open the configuration file, change the text file, re-save, and then restart the application and our reconfiguration is applied.

Learn how to access the PS3 secret recovery menu by following this tutorial. You will need a PS3, PS3 remote, and a USB charger cable. Hold the power button on your system. Listen for three beeps (as you keep your finger on the power button). The third beep will turn your system off. Repeat this process, but this time, you will hear only two beeps (one beep followed by a quick double beep). Turn your TV on and it will tell you to connect your controller to the PSP. Connect your USB cable to t...

DBAs, developers and designers are often tasked with building and managing databases. Especially when the database has been developed by someone else, you have little to no insight into the database structure. Join Quest Software to learn more about Toad Data Modeler and its features that provide:

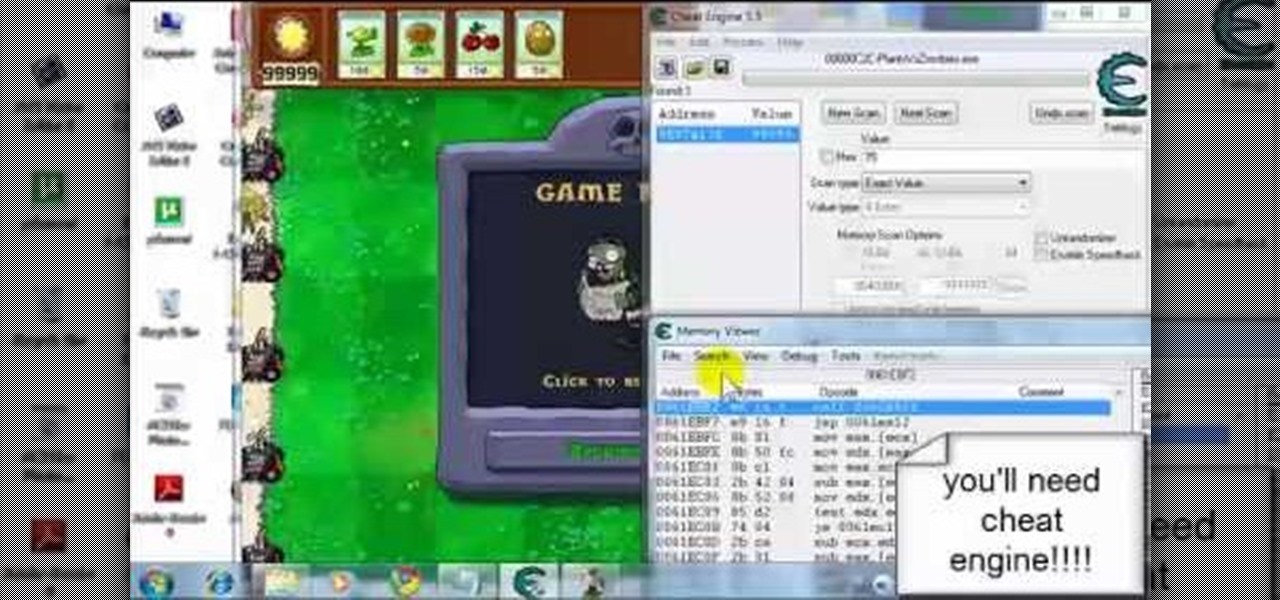
Want to make your next game of Plants vs Zombies much, much easier? You can hack the game to make it happen! Get the latest version of Cheat Engine. Then, use the steps outlined in this tutorial to get infinite sunshine and no loading plants.

It is important to use mulch in your garden if you wish to slow the evaporation of water and keep your soil moist longer. Mulch looks nice and is helpful to put around newly planted plants. four to six inches of mulch will allow you to water your plants less.

Plants propagate themselves through the structures we know as flowers. At the base of the flower, one finds developing seed. The plant will eventually shed flowers and the seed with be propagated on its own. Or we can harvest the seed, dry them down, and germinate them. For more information on the propagation process, watch this green video tutorial.

When you design your irrigation system and pick the plants for your garden you need to think about picking plants that have certain characteristics in common. This tutorial gives you tips on how to group similar plants together by light and water requirements.

If the thought of drought resistant plants makes you picture only cactus and succulents, think again. There are many other beautiful plants that can help you conserve water. This gardening tutorial teaches you how to create a xeriscape or drought resistant landscape. These plants do need to be watered regularly at first but once they have developed their root system you can pretty much leave them to fend for themselves.

This how to video gives you some great ideas for having plants in small spaces. These miniature plants are easy to care for and are perfect to have in a condominium or apartment. Watch this gardening tutorial and learn how you can have a garden of miniatures in your apartment.

Magic. Does it really exist? Can you really put a hex on somebody… or a love spell? Can you really cast supernatural spells? Believing is up to you, but anyone can be bewitching with the help of a little black — and white — magic.

How does one fertilize plants? Well, a fertilizer is a material that supplies the essential elements for plant growth. Most fertilizers are concerned with nitrogen, phosphorous and potassium. It isn't always easy to know which type of fertilizer to use. In this video tutorial, you'll find a guide to selecting the right fertilizer type for your application. Grow strong, healthy plants for a green garden with this how-to.

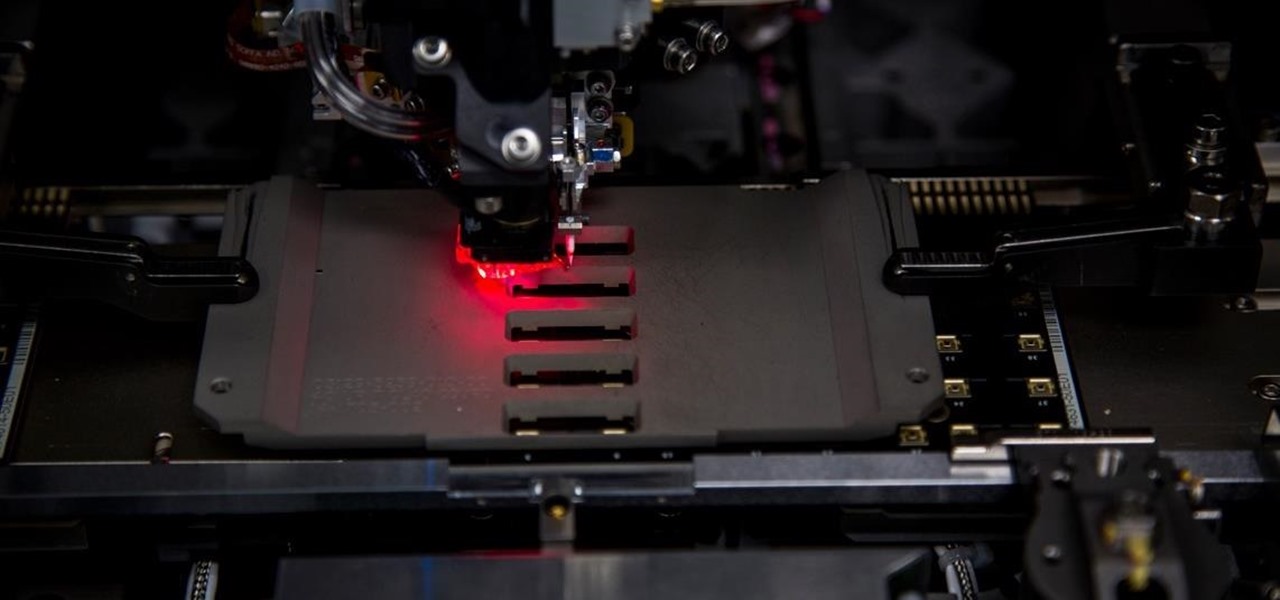
In a move that will increase production capacity for its TrueDepth camera system, Apple has awarded vendor Finisar with $390 million from its Advanced Manufacturing Fund.

So it's 2017 and there are no flying cars and teleportation devices around, but there might be holographic smartphones sometime soon. As cool as that sounds, should we trust a holographic smartphone from a company that has never made smartphones before?

General Motors (GM) has begun production of 130 Chevrolet Bolt EV driverless test vehicles at its Orion Township, Mich. plant as it expands its fleet to total 180 models deployed in San Francisco; Scottsdale, Arizona; and Detroit.

Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.

In this article, I will be showing you how to make a crude form of aspirin from the bark of a willow tree. It is a great remedy for headaches, hangovers, and other minor pain. The use of the willow tree as a mild pain reliever goes back to the Native Americans, who used it in much the same way that I do.

In order to clean your fish tank, you will need the following: a bucket, water conditioner, aquarium salt, a clean filter, a suction tube, and clean fresh water.

Deer can wreck havoc on your plants and yard. No need to go to war with the deer, when with a few tricks of the trade, deer can be discouraged from feeding on your yard. The neighbor‘s yard, on the other hand, might seem that much more appealing.

You don't have to throw away those broken pots and re-pot the plants inside. In this gardening tutorial, Martin Fish from Garden News shows viewers how to repair cracked pots. With this the tips from this how to video you can save money on plant pots.

It is ideal to tie your climbing plants against a wall in order to train it to grow up. In this how to video, Martin Fish from Garden News demonstrates how to use a new product called Soft-Tie to tie his climbing plants.

Plant nurseries have thousands of trees and shrubs in stock. To keep them from drying out and dying, it is important to water them on a regular basis. This how-to video will show you how to water thousands of trees and shrubs. Learn to test the soil around the plants and about irrigation systems that will help you keep you plants alive

Researching genealogy takes a little enterprise and the skills of a master sleuth.. Watch this video to learn how to research your genealogy and family tree.

In this tutorial, we learn how to create a water garden arrangement. To start, have a box filled with foam and rocks, then place branches on the inside of the foam and rocks. Now, add in a few liatris branches at different sizes. Next, add in yellow daisies, green spider mums, foxtail ferns, ivy leaves, and any other plants and flowers you prefer. To give the arrangement a garden feel, make the plant out of order and make the plants and flowers at different levels and heights. Arrange the flo...

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

Just days after the launch of Google Poly, the marketplace for 3D virtual objects that developers can use for augmented and virtual reality apps, SketchFab, the current leader in the space, is firing back with a major enhancement to its platform.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

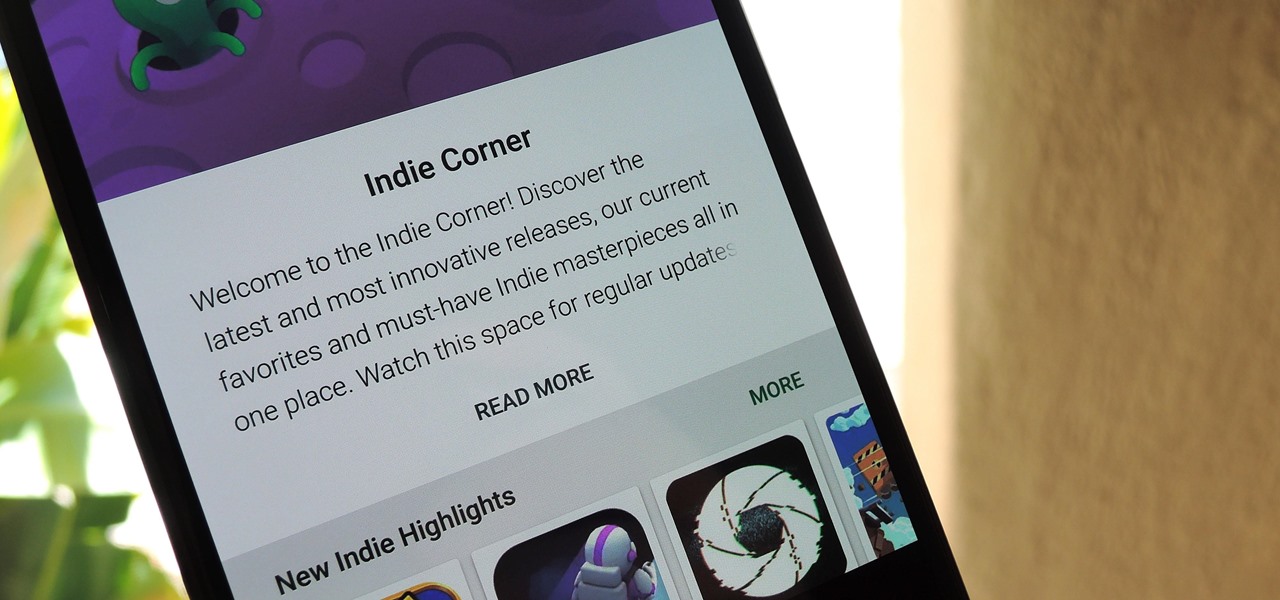
Mobile gaming is a huge industry that raked in more than $91 billion in revenue in 2016, and of course, all of the major players get most of the glory. But smaller, independent game developers make some of the most fun and unique games out there — it's just harder to find their stuff because they don't have the promotional budget of studios like Rovio and Gameloft.

Welcome to the first coding tutorial on SQL here on Null Byte. Typo: