
How To: Care for African violets
African violets make great household plants. Learn how to grow and care for African violets in this free gardening video series.


African violets make great household plants. Learn how to grow and care for African violets in this free gardening video series.

Geraniums are extremely hardy flowers that can be planted both indoor and outdoors. Learn how to grow and care for geraniums in this free landscaping video series.

All tea comes from the same plant; however, the way the tea leaves are prepared are very different. Learn about green, white, Oolong, and black tea in this free video series about making the perfect cup of loose leaf tea.

Learn how to do stability ball hammer dumbbell curls. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do stability ball dumbbell skull crushers. Presented by Real Jock Gay Fitness Health & Life.

We next visit the farm, where the real production takes place. They are growing some unusual items. Several herbs, like Shiso or Perilla (Perilla frutescens) are available in green or red varieties. They have a very unique flavor, almost nutty with a touch of citrus and a very aromatic flavor. Jerry uses them to make a green apple shiso ice. And you can use it as a salad green when it's young and actually use the seeds as well. Use the tips in salads and the seeds when they start to form, the...

If you're new to DreamCoder for PostgreSQL, one of the very first features with which you'll want to acquaint yourself is the data table browser, which will permit you to display entries in a given PostgreSQL database. For a detailed walkthrough of this feature, take a look at this video tutorial.
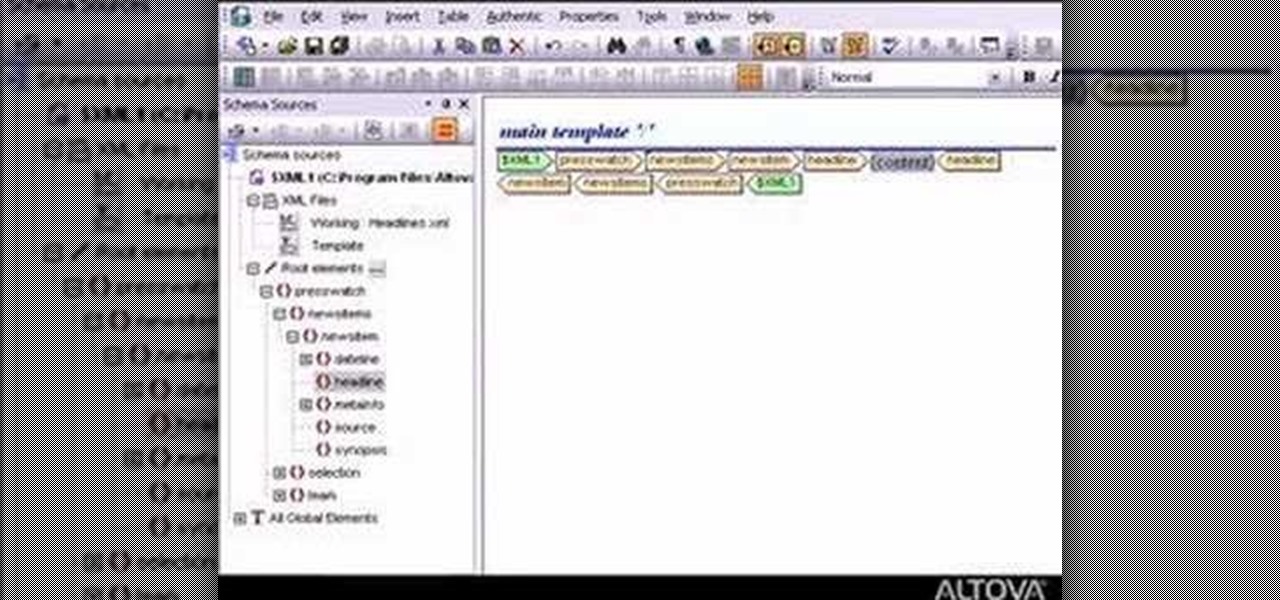
Watch this video to learn how to design an XSLT stylesheet to transform XML or database data into HTML, PDF, or Word documents. XSLT programming just doesn't get any easier than with StyleVision.

Learn in this video how to use XMLSpy to create and edit XQuery documents, debug them and profile execution speed and bottlenecks, and execute them against local XML data or XML stored on a database server. XML editing can't get easier then this.

Park Skateboarding: Show Off Your Skills The first skateparks appeared in the 1970s, and nowadays, they're the epicenter of the skateboarding world, a place to see and be seen. That being the case, you don't want to show up to the park without your "A" game. Let our trick guide get you up to speed. Watch this video tutorial to see how to do skateboard eggplants at a skatepark.

If you want some large, bold foliage in a border during the summer, canna lilies take some beating. They are really easy to grow either in the border or large pots and produce large paddle shaped leaves and tall flower spikes. Canna lilies aren't hardy plants so unless you live in a very sheltered area it is wise to dig them up in autumn and store the fleshy roots in a frost free place. Increasing your stock of canna plants is very easy with the tips from this how to video.

In this gardening tutorial, Martin Fish from Garden News shows you how to take cuttings from Salvia patens or blue flower sage. Cuttings are a way to root new plants from a larger plant. Watch this how to video and you can get tips on how to take a cutting and root a blue flower sage plant.

It has often been said that the only constant is change. IT's ability to manage change is an important business success criteria in today's competitive markets. Change can either be planned or unplanned. This presentation will help you understand the effects of change, and how to manage change properly. It will help Oracle database administrators better prepare to implement changes and measure the positive (or negative) affects those changes produce on the system.

KeePass, the free, open-source password manager, has an excellent Android client in Keepass2Android. Its UI is slicker than many of the other ports, it's packing most of the features you'd find in the official Windows version, and it's completely free. Now, it's even adding native biometrics support.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.
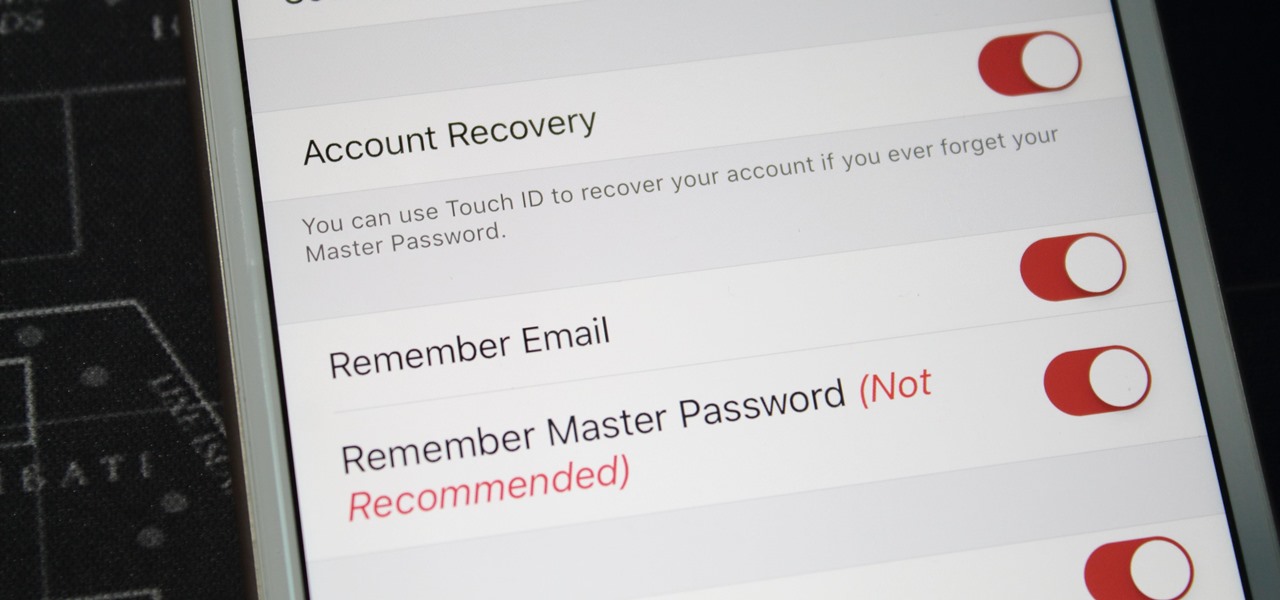
With any password manager, the only password you need to remember is the master password that locks the vault from both hackers and the company. This makes the master password very important. But what happens if you forget this password? Well, LastPass has you covered.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

RIP Touch ID. Apple's fingerprint sensor on iPhone and iPad models with Home buttons is about to become phased out on Wednesday, Sept. 12. While Touch ID will remain an integral part of models from the iPhone 5S to the iPhone 8 Plus, as well as the iPad Air 2 through the sixth generation iPad, Face ID will completely take over as the default security method for unlocking future iOS devices.
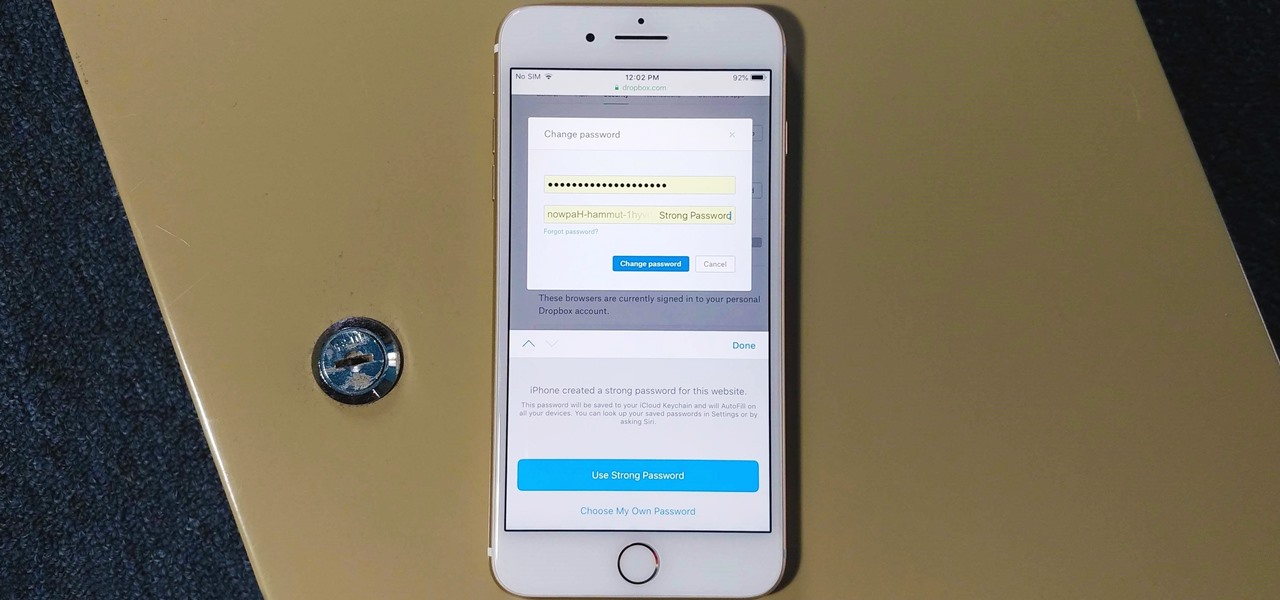
The option to auto-fill passwords on your iPhone has been around a while now, but iOS 12 improves on it by suggesting strong passwords when first creating an account online in Safari or within apps. Apple has also added "password reuse auditing" for your iCloud Keychain, where all your logins are housed, which will find and change your weak passwords to strong ones.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

With an eye toward future iPhone X-focused augmented reality functions, Apple's new investment in one of its components vendors will increase production capacity for the technology behind its TrueDepth camera, but could also apply to its future AR ambitions.

Sex makes the world go 'round, and when it does, so does gonorrhea. Finally some good news on the growing menace of drug-resistant gonorrhea — a large, long-term study shows a vaccine may work in reducing the incidence of an increasingly dangerous infection.

A promising new antibiotic has been discovered in, of all things, another bacteria. Burkholderia bacteria live in diverse habitats, including soil, plants, and humans where they thrive by knocking out other microbes that compete with them for resources or threaten their existence. Scientists have discovered they accomplish this by producing a very effective antibiotic.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

No one can dispute the evolutionary success of bugs. The oldest insect fossils were found encased in crystallized mineral silica in Scotland in 1926, and they're between 396 and 407 million years old.

If you've got big plans to lose weight and get healthier in 2017, know up front that it will be an ongoing challenge. It's not easy to break bad habits, and it's even harder to form new and better ones.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

Black lights come in all shapes and sizes, and they're useful in a variety of ways. They can help you spot fake currency, urine stains, interesting rocks, and deadly scorpions, and they can even help you view cool fluorescent artwork.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

Welcome back, my hacker novitiates!

Eating flowers is a time-honored culinary tradition, from nibbling on nasturtiums to grazing on candied violets. And why not? They look beautiful and lend a unique floral flavors to salads, desserts, and anything in between.

Welcome back, my budding hackers!

Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.

Fish is delicious, and as the Harvard School of Public Health points out, incredibly good for you. There are many studies that show regularly consuming a couple of servings of fish per week can help prevent heart disease and may well reduce your chances of stroke, depression, and getting Alzheimer's. After all, there's a reason why fish is called "brain food."

Welcome back, my hacker novitiates! Recently, I demonstrated a hack where you could redirect traffic intended for one site, such as bankofamerica.com, to your fake website. Of course, to really make this work, you would need to make a replica of the site you were spoofing, or better yet, you could simply simply make a copy of the original site and host it on your own server!

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.