In keeping with its focus on loading the Magic Leap One with content at launch, Magic Leap has inked a creative partnership agreement with augmented reality production studio Square Slice Studios.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

A peek inside the code of the Snapchat app has revealed that the company is expanding the search capabilities of its augmented reality camera to include visual search that may link to items within Amazon's massive online store.

With the opening round of Wimbledon, one of professional tennis's four major tournaments, beginning on Monday, Snapchat is serving up an augmented reality tennis mini-game.

Hip-hop artist Drake once rapped that "goin' online...ain't part of (his) day," but that's not stopping him from promoting his new double album, Scorpion, via augmented reality on Snapchat.
Snapchat is enjoying a high field goal percentage when it comes to securing movie studio business with its sponsored augmented reality experiences, the latest coming through the basketball movie Uncle Drew.

The spirit of Google's Tango augmented reality platform lives on at Vivo, a China-based company that has developed its own 3D sensor for mobile devices.

Just in time for the release of Pixar's highly anticipated sequel, AR Emoji based on characters from The Incredibles 2 have arrived for Samsung Galaxy S9 and S9+.

The company behind Japan's beloved Gozilla, Japan's Toho Studios, has for years tried to give fans the sense of what a giant, nuclear-powered lizard invading Tokyo might feel like. Until now, those attempts have been limited to the movie theater, but now, with the help of the Microsoft HoloLens, Godzilla is finally getting its chance to invade the actual city, with terrified fans looking on from a safe distance.

New Balance is helping Liverpool Football Club (FC) fans see how they look in the team's new kits with an augmented reality experience in Snapchat.

Location services company Mapbox has added new capabilities to its location-based gaming tool to fend off Google's challenge for the same mobile app category.

Like Marvel's Avengers, Facebook's Camera AR platform now has a number of new AR superpowers at its disposal, so it is fitting that Earth's Mightiest Heroes have the distinction of displaying them.

As if its users weren't already having enough fun with dancing hot dogs and face effects, Snapchat is upping the ante with a new kind of shared augmented reality content.

Before Google Chrome entered the scene and subsequently dominated the market, Firefox trailed only Internet Explorer as the most popular web browser. Now, Mozilla has its sights set on a new opportunity to revive its browser for immersive experiences.

The augmented reality cloud and multi-user experiences are shaping up to be one of the hotter areas of augmented reality, and now Google is the latest entity to back these emerging branches of AR.

Despite the wide availability of markerless augmented reality experiences for mobile devices, there is still a market for scanned triggers for content, as evidenced by the new image recognition capabilities on Facebook's Camera AR platform.

A very low-key update to the ARCore developer's site has expanded the universe of officially-supported devices for Google's augmented reality toolkit to include the Samsung Galaxy S7, S8+, and Note 8 handsets.

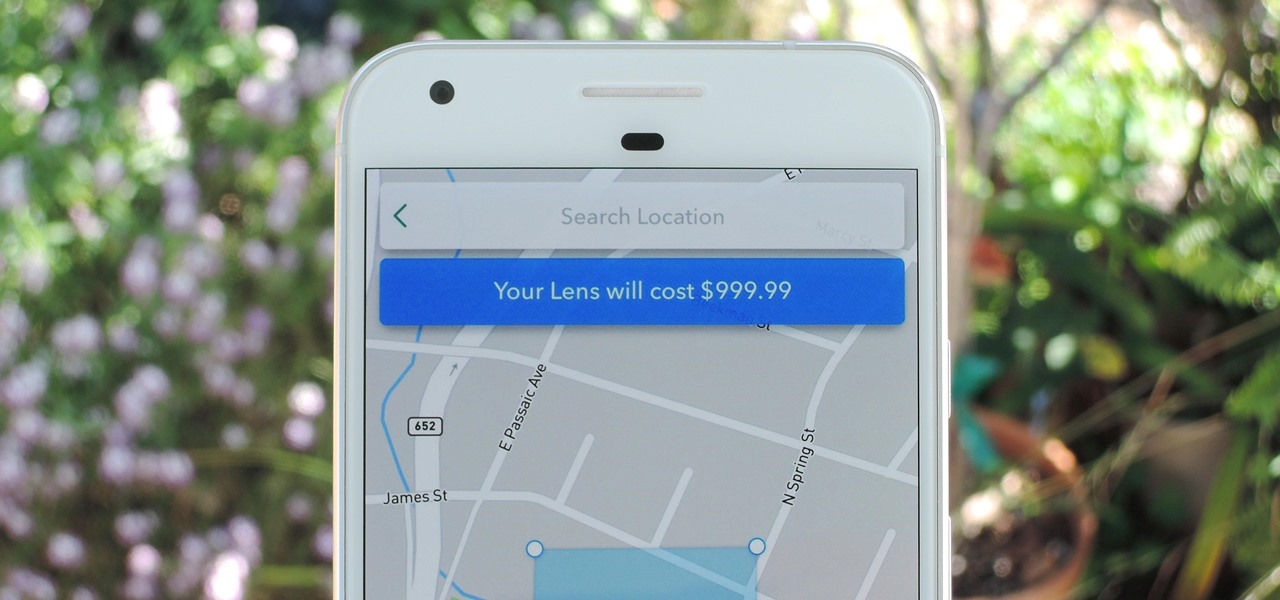
Snapchat just rolled out a feature that lets you create custom Filters and Lenses. While the average Geofilter won't run you more than a few bucks, it's not that hard to exponentially jack up the price. Amazingly enough, Snapchat's latest attempt to monetize their platform can ultimately cost you as much as $999.99. Ignore the penny, let's call that a cool grand.

Earlier this week, Snapchat announced a partnership with NBCUniversal regarding the 2018 Winter Olympic Games in South Korea. Starting on February 10, Snapchat will be streaming a feed of NBC's live broadcast of the Olympics in Pyeongchang.

Thanks to Apple's beta preview of iOS 11.3 released last week, app developers are already experimenting with the ARKit capabilities that will be available to regular users this spring.

Instagram updated its iOS and Android apps recently with an "Activity Status" indicator. This status allows your friends to see when you are currently active and when you were last active on Instagram. The problem is, Instagram was pretty quiet about this update, so many of you have it enabled without realizing it. Fortunately, it's simple to turn off.

Scary movies seem to be a natural fit for augmented reality experiences, with the latest example coming from the Insidious film franchise.

Whether you're a veteran augmented reality developer looking for a quick access point to add a new platform to your arsenal or just getting started with your first AR head-mounted display, get ready to start developing for the Meta 2.

It seems fitting that Time magazine's first augmented reality cover is an issue guest edited by Bill Gates, since the company he founded is currently leading the AR charge via the HoloLens.

Harry Potter fans can set down their wands for a spell, as the highly-anticipated augmented reality game from Niantic based on the franchise won't arrive until after July at the earliest.

Augmented reality developers are rapidly bringing science fiction tropes into the real world, with the latest example leveraging the TrueDepth camera on the iPhone X to emulate the cloaking technology made famous by movies like Predator and Marvel's The Avengers.

To commemorate the rollout of the AR+ update for Pokémon Go, Apple CEO Tim Cook took to Twitter to promote and celebrate the moment his company's ARKit platform made possible.

Augmented reality has given companies worldwide great powers for innovating business practices and engaging customers, but on Monday, Honda demonstrated that with great power, also comes great social responsibility.

Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a simple cable. If you don't have a power source, you can also power your Linux distro over the cable at the same time.

Lately, any subject in the realm of politics is a figurative powderkeg primed to explode on the nearest social media channel. Now, one app wants to use your iPhone and AR to strike a match.

Do you know when you're going to die? Your iPhone or iPad does. That's the premise behind Death Mask, an experimental app developed by Or Fleisher and Anastasis Germanidis.

Two characters from the popular sci-fi animated comedy Rick and Morty have already made their way into augmented reality courtesy of ARKit experiments. Now, it's possible to become one of them on the iPhone X.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

Samsung just began rolling out the Oreo Beta 2 to registered users of the Galaxy S8 and S8+. The update's changelog promises the inclusion of the October 2017 security patch. Unfortunately, after downloading the update, we've noticed this is not the case. Omission of the more recent security patch is notable in that it leaves devices vulnerable to several known exploits, such as KRACK.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

At their event in San Francisco today, Microsoft announced that they have begun accepting pre-orders for Windows Mixed Reality headsets from Acer, Dell, Lenovo, and HP, with the devices arriving on Oct. 17 along with the Windows 10 Fall Creators Update.

With the official release of iOS 11, the availability of an app that uses the much-hyped ARKit platform to place virtual furniture in one's home was expected.

From all the demos we've seen, we know for sure that the marketing world is going to change drastically thanks to Apple's ARKit.

The developers at Immersion VR are clearly fans of both Apple's ARKit and Rick & Morty, as the company has shared its second demo in as many weeks of the augmented reality platform that is influenced by the animated sci-fi series.

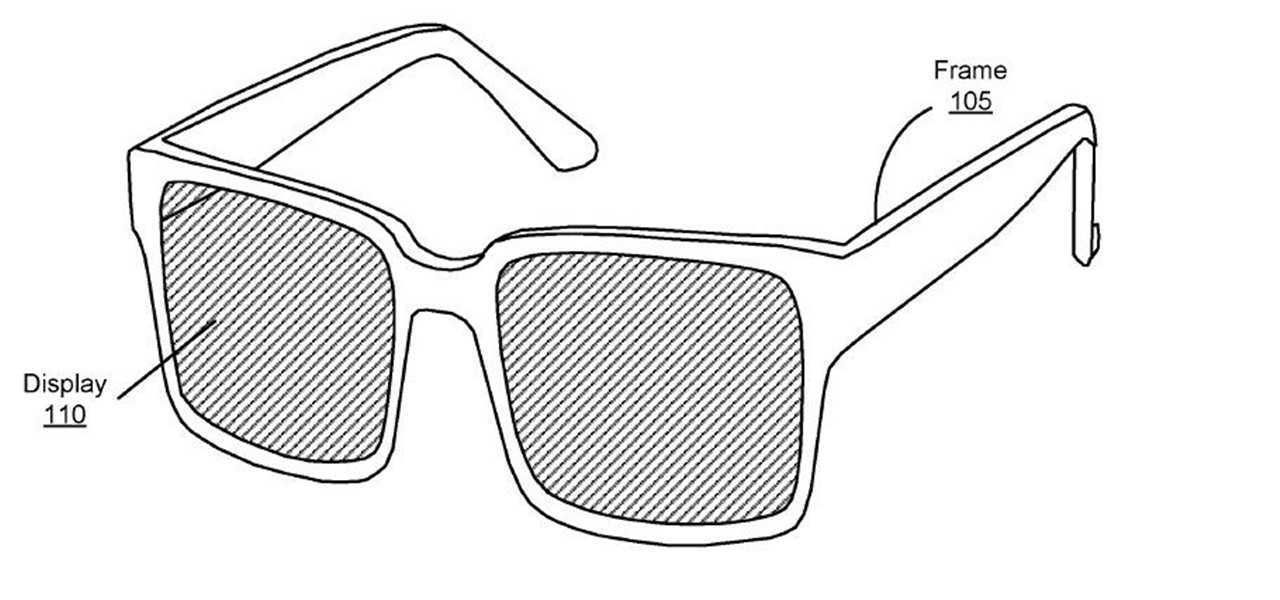
A patent application for waveguide-based smart glasses submitted by way of their subsidiary Oculus sheds light on Facebook's plans to escalate their augmented reality efforts.