Although the initial reception for the Galaxy S9 has been generally positive, recent reports paint a potentially bleak image — some S9 owners are complaining that their new devices have "dead zones" in their displays, which don't register their touch inputs. Luckily, there are steps you can take to fix this problem.

Business cards are a great way to keep tabs on the contacts we network with. So why shouldn't our smartphones make them even more useful? Enter Google Lens, which will help you save, search, and expand on the contact information found on all of the business cards you've collected.

In any business, there are a number of questions companies must answer in order to get customers to buy a product or service. The same holds true for companies selling augmented reality headsets.

Augmented reality software maker 8th Wall has closed a Series A funding round of $8 million in capital to feed the growth of its development platform.

Your email is just that — yours. You shouldn't have to worry about other people gaining access to it on your iPhone. Fortunately, Outlook agrees, and has included a way for you to protect your messages with one of two keys no one possesses but you — your face or fingerprint.

With the advent of ARKit, apps that can place virtual furniture in a real room have become nearly a universal practice for furniture retailers, with Pottery Barn being the latest to join the fray.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

The staff at Next Reality News is legitimately excited about the prospects that Google's ARCore could bring not only to smartphones and tablets running Android, but also to Android-based hardware such as smartglasses.

The ride-sharing firm Lyft and Faraday Future, a troubled electric carmaker and potential Tesla competitor, have quietly appointed new top executives, but like the rest of the industry, they struggle to find talent for their driverless programs.

All eyes will be on Tesla CEO and founder Elon Musk tonight to see if he is reveals details about the status of Tesla's challenged Autopilot at tonight's official Model 3 launch party.

With mobile developers near and far primed to implement augmented reality into their iOS apps with Apple's ARKit, uSens offers them a new tool for markerless location tracking.

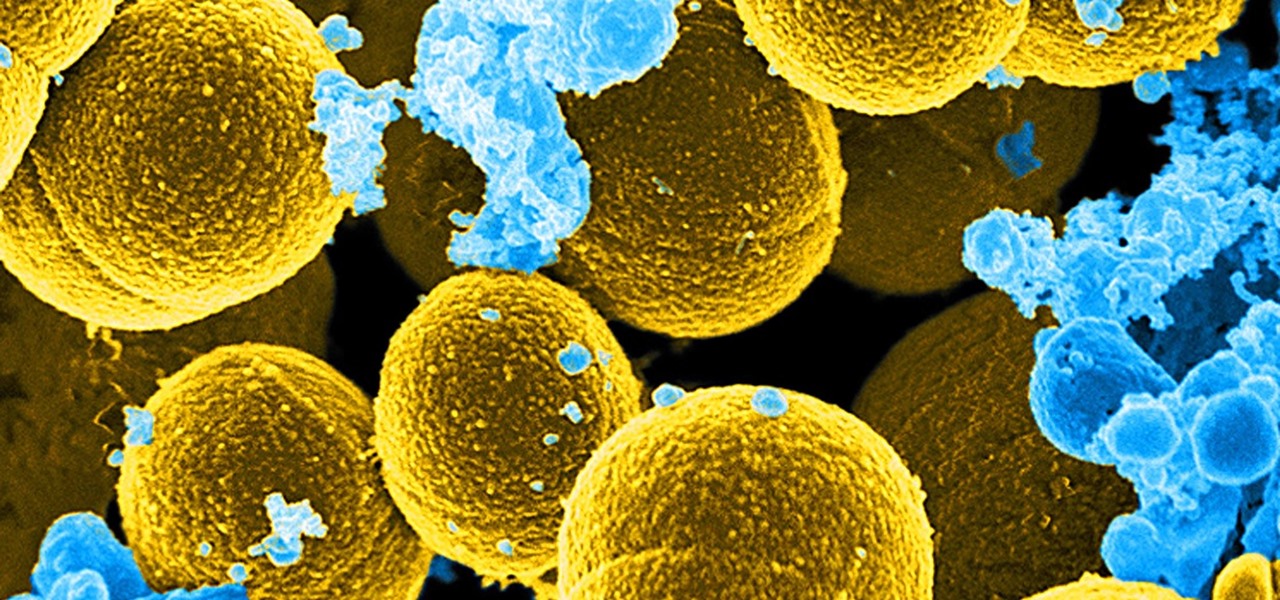
For once there is good news — surprising news, but good news — in the fight against antibiotic-resistant organisms. A recent study found that Staphylococcus aureus bacteria is becoming more sensitive to some key drugs used to treat it.

Reigns recently went on sale on the Google Play Store (sorry, iPhone users), and that inspired me to give it a go. I've wanted to try this one out for a while now, but the steep price tag kept me away. ($2.99 is a lot for me, okay?)

Waymo claims in court documents filed yesterday in its lawsuit against Uber that ex-Uber CEO Travis Kalanick knew that former Google engineer Anthony Levandowski was in the possession of stolen documents while employed at the troubled ride-sharing firm.

Mitochondria are known as the powerhouses of our cells because they generate energy to power them. But they also play a key role in the death of cells when they're damaged, infected, stressed, no longer needed, or at the end of their life.

If you've ever wanted to turn your favorite GIF into a live wallpaper for your iPhone or even just make it a 3D Touch-friendly Live Photo that you can share, there's a super simple way to do so.

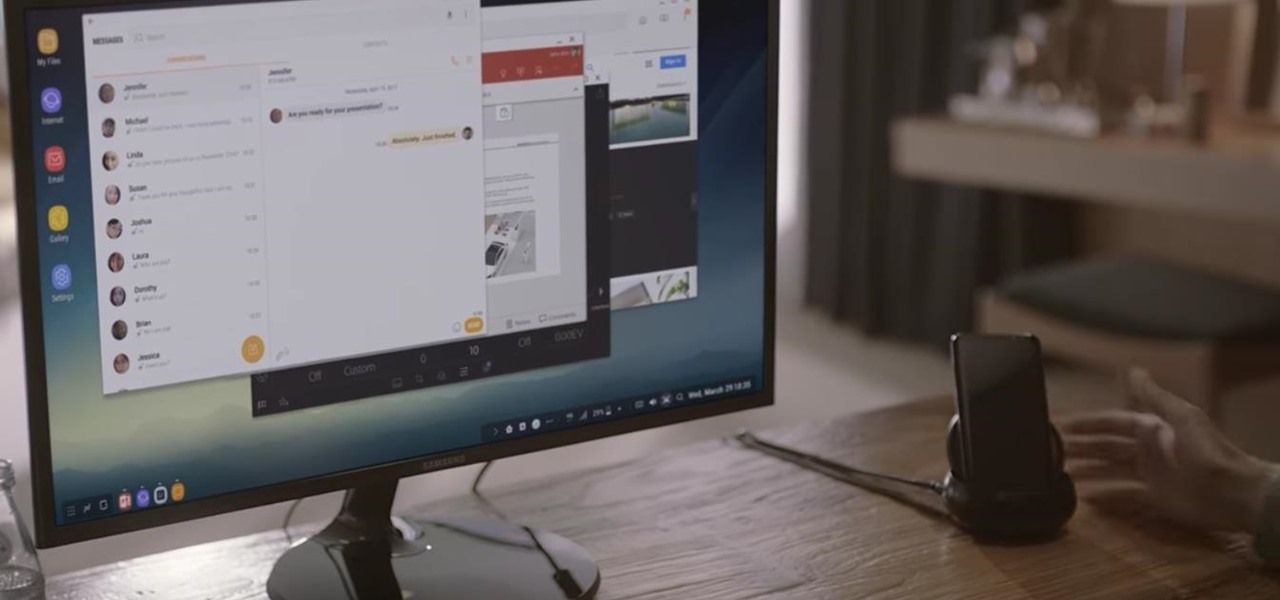
Samsung's new Galaxy S8 can turn into a PC with its DeX dock, but while that may sound like the future of mobile computing on the surface, there are definitely a few issues with the entire setup.

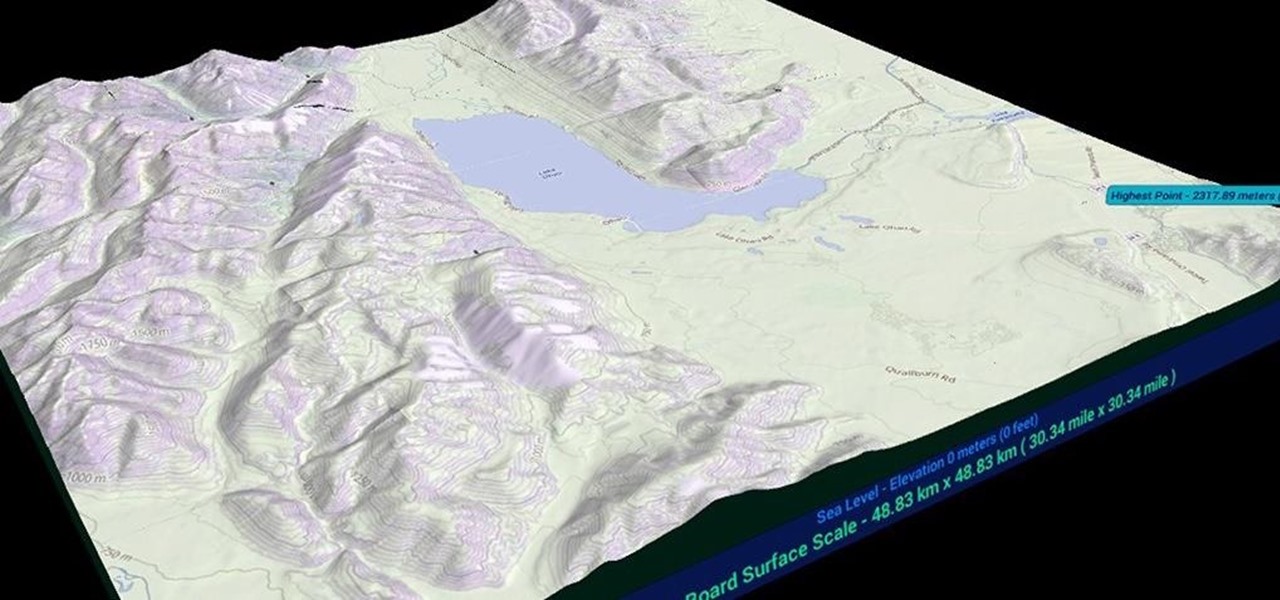
After what appeared to be an issue with the Windows Store for HoloLens not showing many newer applications, including one that I had released over a month ago, Microsoft finally squashed the bug. So, at first glance, it would seem as if there were lots of new HoloLens projects that just appeared in the store, even though they've likely been hiding out there for a while. HoloTerrain is one of those apps.

The Pixel and Pixel XL come with an awesome data-saving feature called Wi-Fi Assistant that automatically connects to open internet hotspots, then creates a secure VPN on your device to keep your data safe.

The HTC Vive and Valve's SteamVR make for one of the more compelling virtual reality experiences, mixing in real-world motion tracking with the immersive headset. But third-party manufacturers couldn't tap into the Vive's full potential and make creative new peripherals—until now.

The newest version of Apple's mobile operating system, iOS 10, has been out for about a month now. But like every year beforehand, some of you who updated will not be happy with the latest and "greatest" iOS version.

Hello guys, I recently made a how to about whatsapp but the problem with that script is that it is way to long and you need to copy and paste it so many times so I made a new one that works just fine and is more easy to use lets get into it (Here Is How The Code Supposed To Look)

If you find yourself switching between Android devices frequently—for instance, your Nexus 6P and a Samsung tablet—you've probably noticed how the button placement can be different. Normally, it's back, then home, then the recent apps button, from left to right. But Samsung devices have this backwards, which can lead to frustration when muscle memory kicks in and the back button isn't where you expect it to be.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

SentrySafe puts all sorts of measures in place to protect your valuables and important documents. This particular SentrySafe has an electronic lock, four 1-inch bolts to keep the door firmly in place, pry-resistant hinges, and it's able to withstand drops of up to 15 feet. That all sounds great, until you find out that you can open this safe—and pretty much every safe like it—in a matter of seconds using only a magnet. A rare earth magnet, to be precise.

Screenshots are an indispensable tool when it comes to relaying information about what's currently showing on your monitor. Whether you need help troubleshooting an issue or you just want to save and share a protected image, screenshots are often your best bet.

We spend over 30 percent of our lifetimes sleeping—yet it never seems like enough, does it? Distractions ranging from work issues to personal relationships keep our minds racing well after they should be shutting down for the night, and the onset of smartphones has only added to this problem with the instant information and easy entertainment that they offer.

Microsoft's "Fall Update" to Windows 10, code named Threshold 2, has a lot of new tricks up its sleeve. It's the biggest update we've seen since Windows 10 was released this summer, and it's rolling out to all users right now.

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

In an age where restaurants can charge $20 for eggs Benedict at brunchtime (if you're lucky enough to even get a reservation on a Sunday), many people long for a way to create this classic dish at home. But once you've taken pains to perfectly poach an egg and gently crisp your sourdough, the problem of the hollandaise still lies before you. The key to any good hollandaise sauce is to apply enough heat to cook the egg yolks, but not enough to scramble them. The minute the eggs begin to solidi...

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

All of those keys on your keyboard can do much more than just help to update your Facebook status or fire off a scathing tweet. By learning all of the keyboard shortcuts for apps on your Mac, you can cut back on mouse or trackpad usage to perform actions faster and more efficiently.

Malware often disguises itself inside of seemingly non-malicious files, such as installer packages, where it can then gain root access to your computer to track activity or steal your information.

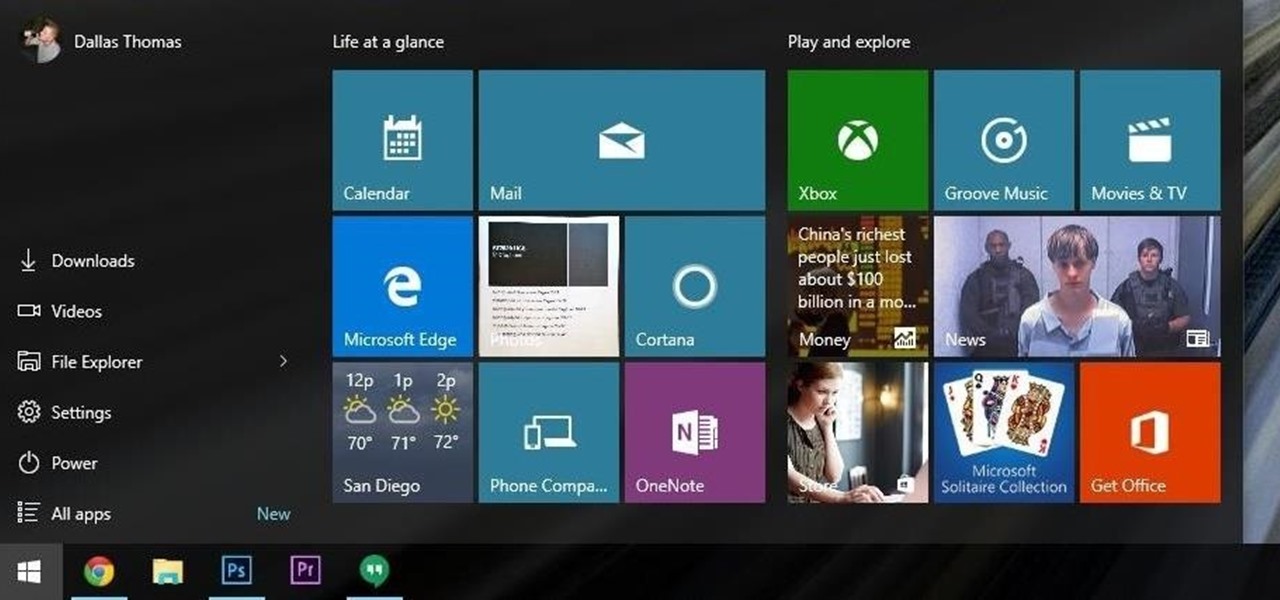
The desktop Start menu is finally back! After receiving a lot of negative user feedback, Microsoft ditched the touchscreen-first approach of Windows 8 and went with a more traditional setup for mouse-and-keyboard users in Windows 10.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

Hello Hackers/Viewers, It is a new day, and you might be thinking, It is so boring, why not try to be cool with computers in front of my friends? That is why, I have made this tutorial to make fake viruses using notepad to look cool!

The Samsung Galaxy S6 includes a pretty nifty feature known as "Gesture wake up," which lets users wave their hand over their locked display to wake it, making those periodic notification checks from the lock screen a lot more simple than having to press the power or home key every time.