With many office workers in the US being asked to work from home if their job allows, Magic Leap's customary updates for the Lumin OS and Lumin SDK brings some help to keep distributed workforces connected.

We've been so worried about volumetric scans possibly robbing celebrities and performers of their agency and right to control their image that, somewhere along the way, we forgot that scans may not always be necessary to produce passable holographic performances.

The next phase of the holographic display is upon us, and Looking Glass is aggressively making sure that it's at the tip of the spear when it comes to leading that charge.

The long wait is over — the best augmented reality device on the planet is finally available.

Smartglasses from Apple have become the holy grail of augmented reality, and 2020 has been the rumored time horizon for the product's arrival for the past two years. The latest analyst report sheds more light on its potential debut next year.

As demonstrated by holographic experiences for the Microsoft HoloLens and the Magic Leap One, volumetric video capture is a key component of enabling the more realistic augmented reality experiences of the future.

Facebook and its Oculus subsidiary have been open about their intentions to bring AR wearables into the mainstream for some time now.

Magic Leap is making it easier for developers to share their spatial computing experiments with other Magic Leap One users.

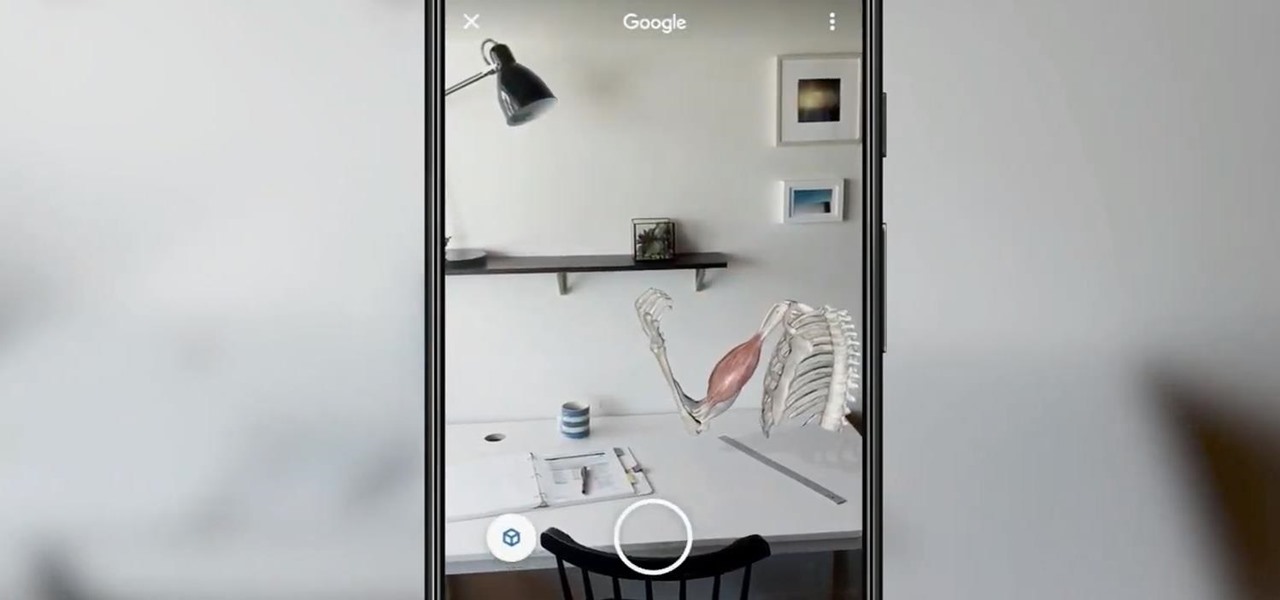
With Android 10 hitting the streets (at least for those mobile devices that get quick updates) and the public release of iOS 13 dropping on Sept. 19, Google is releasing an update on Thursday to ARCore that adds some fantastic new benefits to its cross-platform capabilities.

When it comes to the business of augmented reality, companies that aren't already introducing new products or apps are focused on producing the AR technology of the future. But in the realm of real products and apps, Magic Leap continues to show off what its headset can do, this time via a new app that transports users to the ocean's depths.

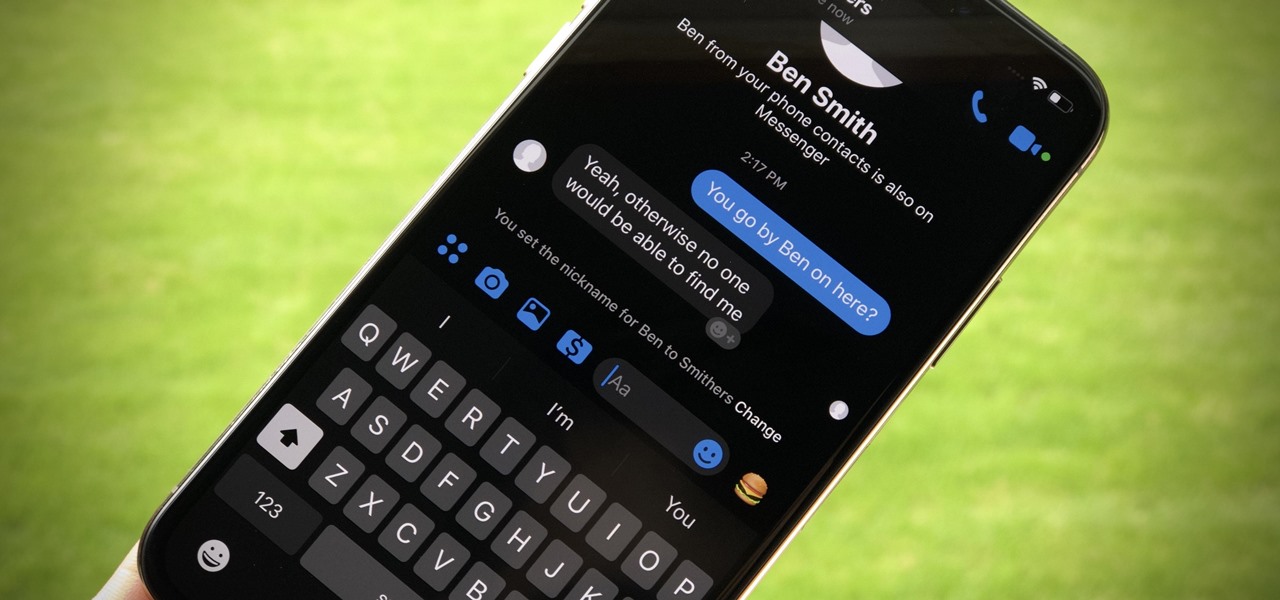
For the most part, people use real names on Facebook. That's all fine and well for keeping tabs on those you know, but it can make friendly Messenger chats feel oddly formal. Skirt around this stiffness by giving your friends nicknames in Messenger for Android and iOS, so your conversations reflect the way you and your friends communicate in real life.

The ability to shift between virtual reality and augmented reality seamlessly on one device is a dream of many AR fanatics, but the execution is usually fairly buggy or underwhelming.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

Having already solved for functionality and form factor, Nreal appears poised to pull ahead of its consumer smartglasses competition as the third piece of the puzzle now falls into place.

Magic Leap and Samsung are putting their money where their augmented reality plans are, with the former acquiring an AR collaboration technology and the latter funding a waveguide display maker.

If Google hasn't already demonstrated that it is serious about augmented reality, then it made it abundantly clear at the Google I/O keynote on Tuesday.

Describing how and why the HoloLens 2 is so much better than the original is helpful, but seeing it is even better.

Location-based gaming company Niantic knows its business model is inextricably tied to the outdoors, so it is in its best interest to help preserve that environment to give players a place to play.

While the long awaited HoloLens sequel is scheduled to arrive later this year, Apple may force Microsoft to share the AR wearables spotlight, if reports of the company's first entry into smartglasses territory end up coming to fruition.

In the last couple of days there's been a lot of speculation about the powers of Microsoft's HoloLens 2, but few have had a chance to get their hands on one to see if the company's claims live up to what HoloLens inventor Alex Kipman showed off on stage.

Now that we've officially seen the HoloLens 2 and Microsoft has shown off the improvements and new superpowers of the augmented reality headset, what about the specs?

With Magic Leap One approaching six months since launch, Magic Leap is fully focused on building a content ecosystem and developer community.

The emerging narrative as CES begins is that consumer-grade smartglasses require a heavy compromise in functionality in order to arrive at a form factor and price point that appeal to mainstream customers.

While the technology companies continue to drive forward with autonomous vehicles, Nissan's vision of the future of self-driving automobiles lies in a cooperative experience between human and machine, facilitated by augmented reality.

Last year's augmented reality investments roundup was impressive. And in 2018, the dollars flowing toward AR haven't decreased, as venture capitalists and strategic investors continue to aggressively fund AR startups at a rapid pace.

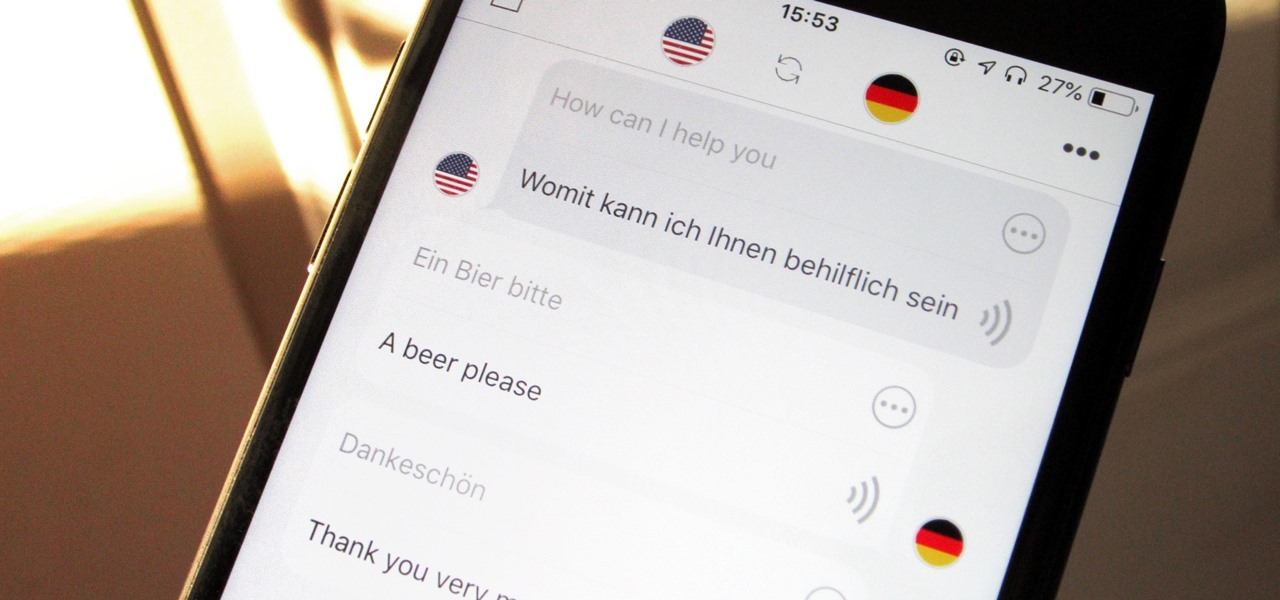
Nothing beats a human translator, but Google Translate and other software-based solutions have developed into decent alternatives for help with basic translations. Need an English word translated into German? No problem — but what if you need to have a conversation with someone who doesn't speak your language? Is Google Translate capable of doing that? The answer is not really.

While many retailers have introduced try-before-you-buy features in their apps, Walmart has gone in another direction by bringing shoppers an augmented reality tool to help them compare products they want to buy.

While we've seen Snapchat apply sky segmentation to AR content, the makers of the Blue Sky Paint app have applied similar capabilities to create and share airborne art.

Microsoft is adding another important piece to its growing immersive computing arsenal by putting its newest Mixed Reality Capture Studio in the center of the movie business: Hollywood.

We've spent years waiting to see what all the secretive fuss was about, and now that the device is in our hands, we can finally begin showing you images of what the Magic Leap One experience looks like.

Computer vision company Blippar has already dabbled with outdoor AR navigation, but now it wants to make it easier for people to make their way through indoor spaces with augmented reality.

The mainstreaming of augmented reality won't happen overnight, but it's becoming increasingly clear that traditional media is leading the charge in the effort to introduce the public to immersive computing. A recent example came from none other than USA Today via its 321 Launch app.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Last month was a whirlwind for the augmented reality industry, with the Augmented World Expo, Apple's Worldwide Developers Conference, and an exciting Magic Leap Twitch livestream all wrapping up before the ides of June. Now that we've had a chance to fully digest it all, we have a real sense of where the augmented reality industry is heading.

The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely.

Escape rooms, those real world puzzle games that challenge teams to solve a mystery and gain their freedom from a locked room, are all the rage right now. But augmented reality games such as The Lockdown could make them obsolete.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

The premise of Jurassic World revolves around splicing genes to create new dinosaurs, so it is fitting that the location-based AR game is a clone of Pokémon GO merged with the DNA of the Jurassic Park franchise.

One of the primary factors that separates an augmented reality device from a standard heads-up display such as Google Glass is dimensional depth perception. This can be created by either RGB cameras, infrared depth cameras, or both, depending on the level of accuracy you're aiming for.

With all the recent activity around augmented reality, the possibilities involving immersive computing and commerce are quickly becoming obvious, and digital payments giant PayPal has no plans to sit on the sidelines