Want to play Playstation games on your computer? Learn how to download, install, and configure the ePSXE Playstation emulator for the PC. In order for the program to work you will need to install several other programs and plugins.
In this video we learn how to compose a hip hop beat in Fruity Loops. First, go to the website www.class4beats.com and download all the samples and plugins. Once you have these downloaded you can use them in Fruity Loops. Play around with the different sounds that you have in this and then put a new beat together. Once you have a beat put together, change it to a hip hope type of beat and then add it in with a melody for a new sound. This will make a great hip hop beat that is all your own an...
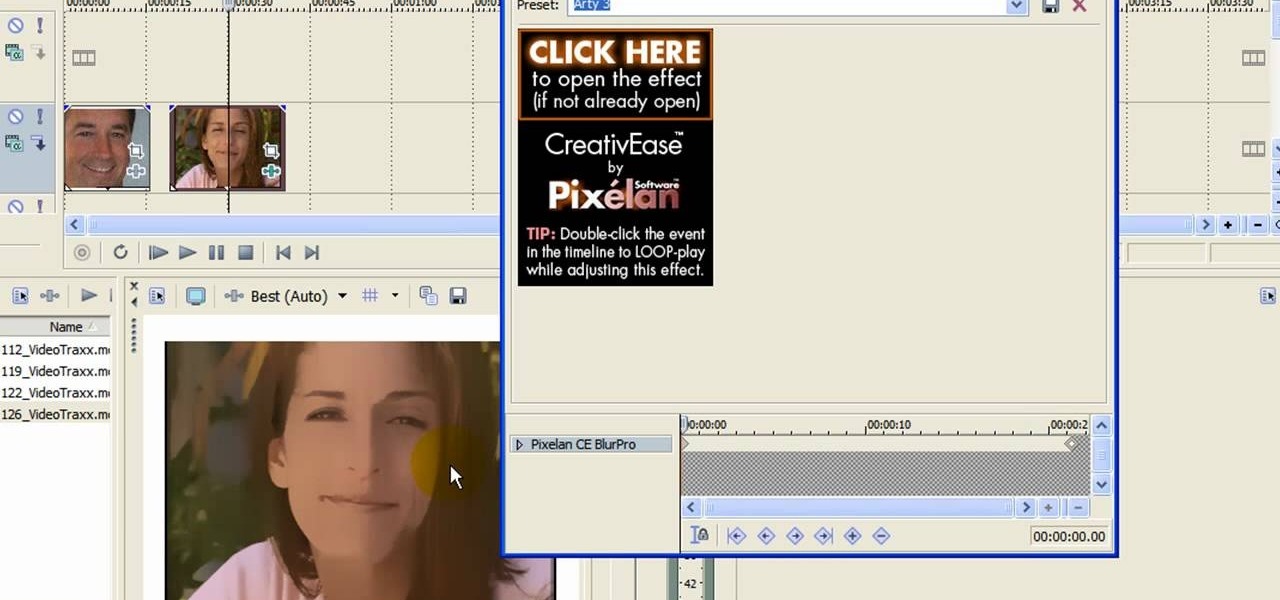
First click on Video Event Fx, it will let you select the plug-ins that you have. Now select pixelan CE blurpro and click on OK. Now select remove blemishes 1 in preset menu. It will remove the first set of blemishes from the video now go for the blemishes 2 and then go for the blemishes 3. Now you can see the difference by playing that video. If you choose arty 3, it will make the pictures of the video as cartoony. Now go again for the blemishes 3, it will make the video even more better. Yo...
Wondering how to create an app bundle in Mac OS X? In this two-part video tutorial series, you'll learn how to create an application that is completely self-contained and is drag-and-droppable/relocatable. Frameworks, PlugIns, and Resources are embedded in the .app bundle, thus avoiding the need for installers and avoiding issues like dll-hell. There is also a quick demonstration on how to enable Universal Binary building at 15:46. Take a look!

The 13-megapixel camera on the OnePlus One is capable of taking some pretty impressive shots, but the stock CameraNext app doesn't do the hardware justice. When compared to the camera app that ships on the ColorOS version of the One, you can immediately see an increase in clarity and low light performance.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

With new messaging services being pushed out constantly, it can be a pain trying to keep track of them all on your Android device. We had previously shown how to stay on top of them all with a unified "inbox" app, but that still requires you to have each individual app installed. While looking for a true one-stop messenger, I came across Disa.

The biggest complaint I have with my Nexus 7 is the lack of support for different types of media files. I have a lot of movies and music that I've downloaded off the web, in many different formats, and I want them on my tablet.

If you use Ubisoft's uPlay browser extension, you should probably get rid of it right now. An Information Security Engineer at Google discovered that the plugin has a hole in it that allows programs to be installed through uPlay, essentially letting anyone who feels so inclined to take over your computer. How the Exploit Works

Wordpress is one of the world's most-loved content management systems (CMS). The user-friendly interface and ease of use have made this open-source system a no-brainer for millions of people. Over one-quarter of the top 10 million websites on the planet use Wordpress.

You've probably heard of RCS messaging. The new standard has been promoted by Google as their answer to iMessage and is the backbone behind the new "Chat" features in Android Messages. With RCS, Android phones will now enjoy enhanced messaging like iPhone users have had for years — but is it really the same?

If you're Apple computer needs a little cleaning, not the hardware, but the software, then MacKeeper is the way to go. This application will help protect your hard drive from junk and other useless data, freeing up much needed space on your Mac. Also, you can recover files, hide private files, clean up your login items, apps and plugins, and more! Watch this video to see how to use MacKeeper.

The Snapdragon version of the Galaxy Note 20 and 20 Ultra — the one sold in the US — can't be rooted. Without root, the level of customization is limited. Such a large group of Android users shouldn't miss out on mods, and they don't have to.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

If you've tried watching a video that requires Adobe Flash Player installed on your Samsung Galaxy Note 2, then you're probably well acquainted with the "Flash Player is not installed" message. If you try tapping the deceiving Install Flash Player button it takes you directly to the Adobe website, where you're greeted with a message saying:

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.

Recently, a user on Reddit complained that their Snapchat account had been temporarily banned because Snapchat noticed the user's account was going through a third-party service. In reality, the account in question was running on a jailbroken iPhone, and it was far from the first to be banned by the messaging app.

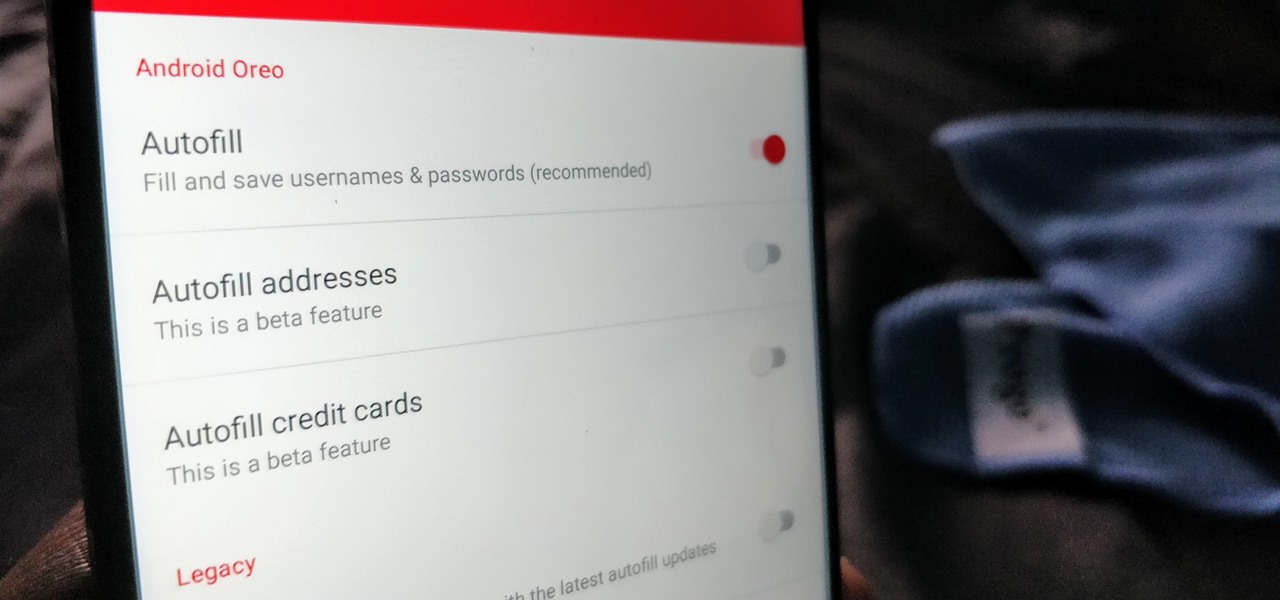
One of the more exciting features in Android Oreo is the Autofill API. With this tool, third-party password managers can autofill login information into other apps. LastPass added this feature to their beta app a while back, but now, Autofill is finally available in the official stable version of LastPass.

Welcome back, my tenderfoot hackers! WordPress-based websites are among the most numerous on this planet (maybe other planets too, but I can't vouch for that). According to WordPress's own website, WordPress powers 23% of the top 10 million websites. That's approximately 2.3 million sites using WordPress!

Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effort into maintaining the fluidity and security of their desktop Flash plugin.

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

Samsung's stock Galaxy Themes system leaves much to be desired with its restrictive and expensive theme packs. Back in the day, the gold standard for Android theming was CyanogenMod Theme Engine. And while it no longer exists, a successor has emerged to fill the void.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

Video: . This map requires the 12w37a snapshot or better, and you must turn on command blocks to use it.

There are a lot of things on your computer that can reveal information about you when you are surfing the Internet. If you are like me, then you will do anything to maintain your privacy and prevent those little leaks of information from happening. Here's a list of a few of the "threats" that can reveal information about you:

Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.

When Google introduced their new launcher alongside the Nexus 5, one of the most innovative features was the "always listening" voice search, meaning that at any time you were on your home screen, triggering a Google search was as simple as saying "Okay, Google."

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

HTC is entering the augmented reality market through the back door by giving developers access to the stereo front-facing cameras on the Vive and Vive Pro VR headsets.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Greetings my fellow hackers.

Apps are now very much integrated with social media, especially with your Facebook profile. Pretty much every app these days lets you log in using Facebook, while some actually force you to, giving you no other option. But, the most annoying part is that these apps leave notifications all over your Facebook timeline, cluttering the hell out of it. So, how can you completely banish all of these apps from being able to access your Facebook?

Facebook has always been notoriously difficult to customize. Personally, I think this is an improvement over MySpace's totally open platform (some people should not use code), but users should still have the option to change a few things if they want. While you'll never be able to choose your own background image or add an obnoxious number of aWeSoMe quiz results to your profile, there are a few browser plugins that let you at least change the color scheme.

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.

Notch loves Halloween. He must, because he keeps putting scarier and scarier things into Minecraft around Halloween time!

One of the greatest trends to emerge from this period of home isolation is the live concert broadcast from bedrooms and living rooms across the planet. Though public gatherings are on hold, you can still impact people with your music and mixes. In fact, it's helping many people get through this confusing time.

In iOS 13, Apple finally took the built in Files app from an extremely rudimentary file browser to a full featured app that can serve the needs of most any user. Among the new features is the ability to compress a file or series of files into a standard ZIP archive right from your iPhone.

Sketchfab, one of the leading 3D model aggregators, continues to defend its turf from encroachment by Google. This time, the company has deployed a new API that gives developers even easier access to Sketchfab's extensive library.