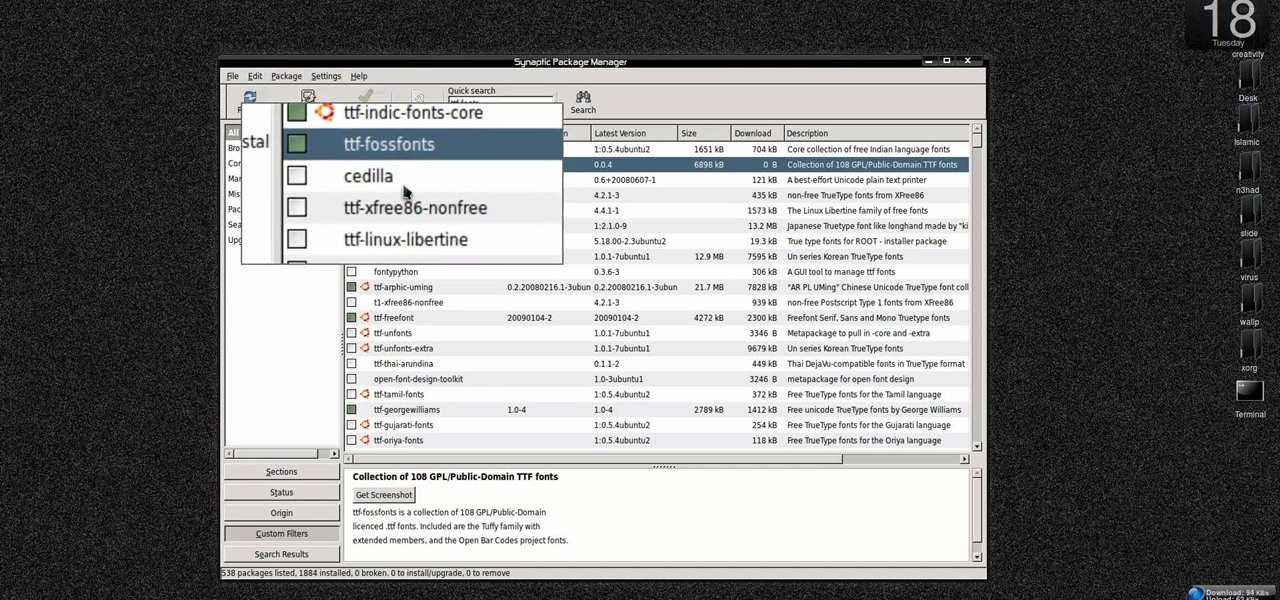
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install additional TTF fonts on Ubuntu Linux.
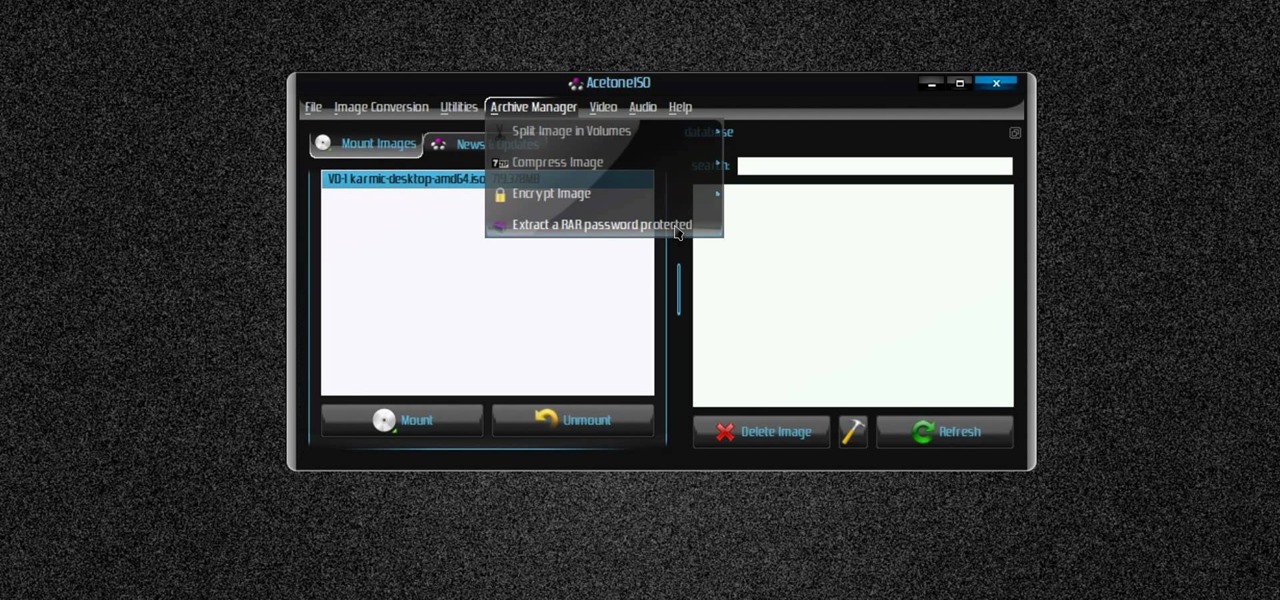
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to manage CD/DVD images with ease on Ubuntu Linux.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install 200+ screensavers on Ubuntu Linux.
In this clip, you'll learn how to utilize the system performance and reliability monitor on a desktop or laptop computer running the MS Windows Vista operating system. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.

In this video, we learn how to install a Toad Stop braking system for towed vehicles. First, determine where you are going to install the braking system. Insert the electrical wires into the appropriate spots by reading the labels that are on them. After this, use a drill to lock down any parts that are loose. Once you place the braking system in, you will need to lock it down using the wires that come with it. Make sure these are installed properly throughout the entire vehicle up until you ...
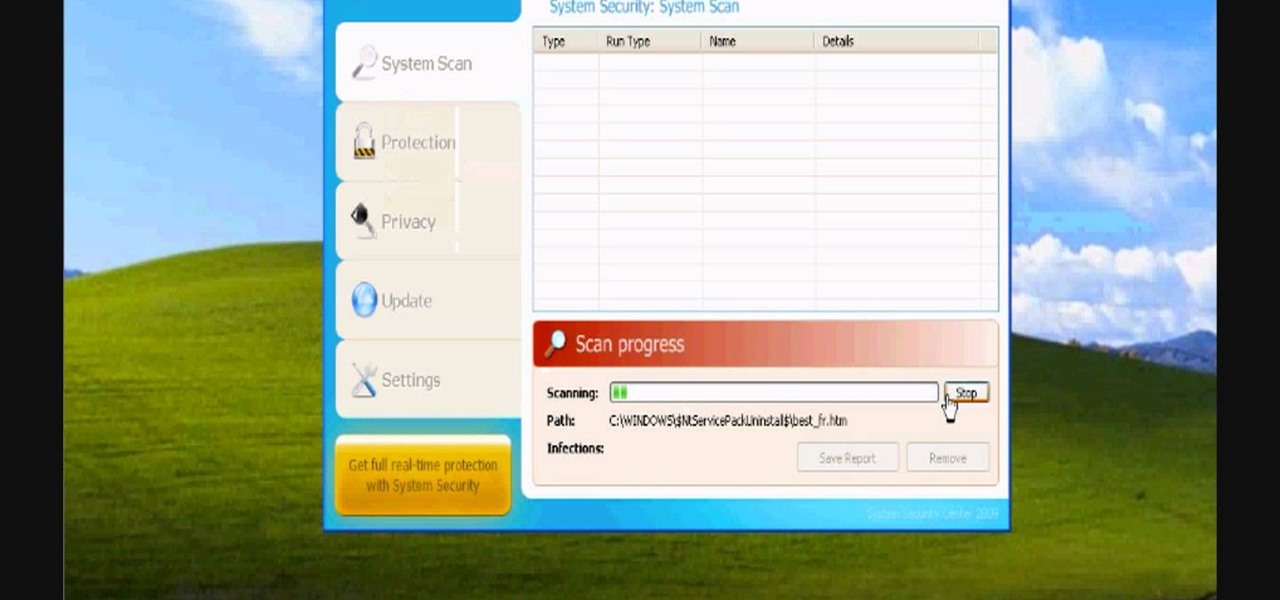
In this video, we learn how to avoid getting infected by "system security". Make sure you avoid the website that show the System Security Anti-Virus. Once you install this onto your computer it will pretend like it is doing a scan, but in reality is hurting your computer. It will pop up showing you that you have problems on your computer, but the alert will never go away. If you delete this, it will just re-install on your computer instead. To do this the correct way, you need to go to your m...

In this tutorial, learn a great, fast way to get your plants growing. This hydroponic system will keep your plants happy and healthy for much longer than old fashioned planting.

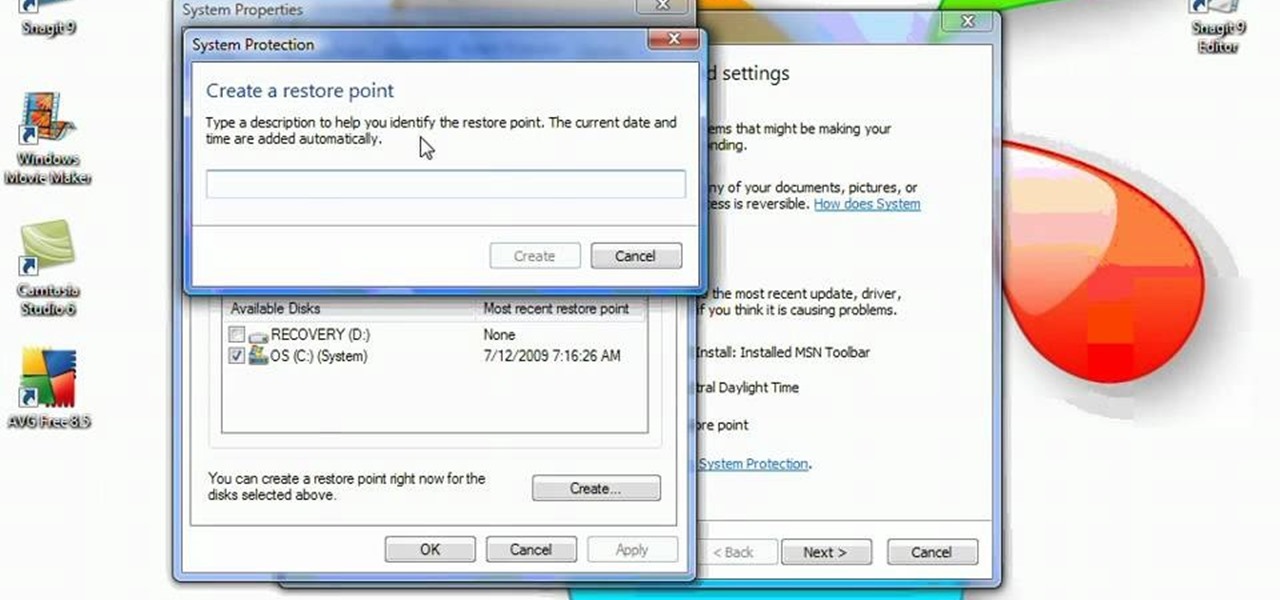
System Restore helps can help fixing the problems that might be making your Computer run slowly or stop responding. Please follow the steps below to restore the Computer running the Windows Vista Operating System.

Although it is a rare and potentially frightening occurrence, knowing how to do a system restore in Windows XP is an important thing to know how to do. To get started with a system restore, select the Start menu in the lower right of your screen. Then select All Programs. Then from the All Program menu, select Accessories and then from Accessories, select System Tools. There are several items under System Tools, but you want to select System Restore. You will follow through the next few scree...

Check out this instructional climbing video that demonstrates how to set up the ascent system for crevasse self rescue. Hooking up the prussik is the subject of this video and stops at the second ascender required for upward mobility. Watch all the crevasse self rescue series and you may get the hang of this. It is best to practice this somewhere dry and safe before the real thing happens. When you are in the hole things get tougher.

In this automotive repair video Rolf shows you how to diagnose and fix a fuel system problem in a Volkswagen Fox. In this VW Fox the gas gauge isn't working properly and the car is sluggish. Rolf will show you how to check and fix the fuel system to resolve these problems.

Check out this tutorial on the Tria at home laser hair removal system! This new system is the first FDA approved laser hair removal system.

This medical how-to video demonstrates a bilateral lymph node dissection in a patient with endometrial cancer using the da Vinci system with the HD optical system. The HD optical system allows surgeons to perform more precise anatomical dissections with enhanced dexterity. Watch and learn how a dissection of a lymph nodes is performed on a patient. This surgical video is intended for medical students.

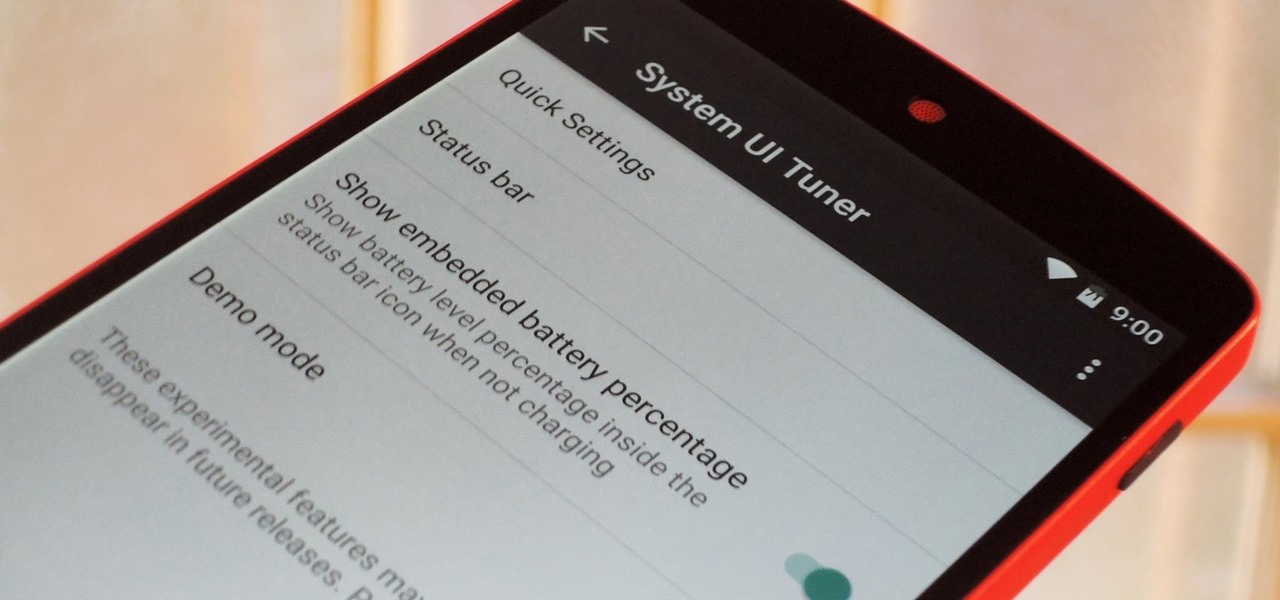
Prompt and frequent system updates are a big part of the Pixel's identity — we're even getting quarterly feature drops now. But not all devices receive these all-important updates at the same time because of Google's staged rollout system. If you want the update right away, there's a way to manually check without having to dig around in Settings every time.

While Elon Musk is in Los Angeles showing off the future of personal transport via the Cybertruck, another, unaffiliated group is taking one of his most popular ideas to market, with augmented reality as a key part of the plan.

With big-name tech companies like Apple and Facebook gearing up to push out their own smartglasses in the coming years, engineering conglomerate Bosch has been working on the optical components that could help the competition catch up.

For many, the stock version of Android is often considered the epitome of what the operating system should look and feel like by default. It's clean and clear of unwanted extra apps that come pre-installed with the system, provides a fluid and fast user experience, and runs on just about any device that has an unlocked bootloader to install a custom ROM with the stock version ready to go.

Augmented reality developer Blippar has created a new visual positioning service based on computer vision that is two times more accurate than GPS in urban locales.

The Raspberry Pi loads an operating system from whatever SD card you insert, allowing you to keep different operating systems on separate SD cards depending on which OS you wish to run. A tool called BerryBoot cuts down on the number of SD cards needed by providing the ability to boot multiple operating systems from a single SD card, similar to Boot Camp for Mac computers.

German groups ZF Friedrichshafen AG and HELLA are collaborating to add to their autonomous portfolios with camera and radar development.

Uber has been in the hot seat for awhile now, for many reasons, especially for being sued by Waymo over stolen LiDAR designs. But now, perhaps the attention will be taken off both Uber and Waymo as a new contender enters the LiDAR arena; A small, independent company called Luminar has finally let the world in on what it has been cooking up.

Trimble is integrating its mixed reality applications into the DAQRI Smart Helmet to enable outdoor and on-site support for design, construction, and heavy industry as part of a collaboration the companies announced today.

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

Greetings null-bytians. Firstly, I would like to apologize for the no images thing. I guess I can't upload them.

Android 6.0 Marshmallow is bringing in lots of changes to our favorite smartphone operating system, ranging from battery-saving tweaks like Doze to a Now on Tap feature that essentially bakes Google right into every app on your phone. But for folks that like to tweak the interface of their device, a new hidden menu might be the most exciting addition of them all.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

One more business has decided that rewarding hackers to find flaws in their computer systems is a wise investment! As you know, a number of software companies offer bug bounties, and some of these can be quite lucrative. Google, for instance, offers a bounty of $150,000 for anyone who can hack their Chrome operating system, and many other companies are offering similar bounties, although, not quite as lucrative. Now, United Airlines has decided to offer frequent flyer miles to hackers who fin...

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Welcome back, my budding hackers! In my continuing series on Linux basics for aspiring hackers, I now want to address Loadable kernel modules (LKMs), which are key to the Linux administrator because they provide us the capability to add functionality to the kernel without having to recompile the kernel. Things like video and other device drivers can now be added to the kernel without shutting down the system, recompiling, and rebooting.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

The problem of system freezes is not new to the world of Windows and this has come to light even in the latest Windows 8 release. In the event that your system freezes, you cannot open your desktop files, some controls stop functioning, or you are unable to launch the start screen applications either. You may experience this unusual behavior after updating Apps in the store or due to a driver issue. Sometimes, freezes occur because of video card problems too. In order to do away with these Wi...

When your clutch pedal is dropping down and not coming up again, the cause is most probable one of the cylinders in the hydraulic clutch system. The video will give you a step-by-step tutorial on how to replace both, the master and the slave cylinder. In addition, it is a good idea to also replace the pressure hose in-between the cylinders.