More and more car parts are controlled by computers, and the results are not always what we hope they will be. They often break for what seems like no reason and are expensive to fix. In this video you'll learn how you can fix a broken air conditioning control system on your car with a $30 bypass switch that will be much more reliable than your computer was.

If you've got a school science project coming up, or are looking for something fun to do with the kids, you can make this awesome solar system diorama that's shaped like a telescope so you can view the planets by looking into the telescope! In this video you will learn how to create this diorama that will impress even the most stern teacher!
In this video tutorial, we learn how to install, delete and browse OpenType and TrueType fonts on a MS Windows 7 PC through use of the Windows Font Manager, which can be found in your system's Control Panel. For all of the details, watch this home-computing how-to.

You keep all kinds of important and sensitive information and data on your computer, and if your hard drives crashes, you're done for… unless you've backed it up. CNET has some "Insider Secrets" on how you can backup your system with an external hard drive, network-attached storage, and online services.

Do you have a car that is overheating? Do you know what to do if you have a car that is overheating? How can you find out the problem for your car overheating?

This video describes how to free up system resources on your Mac, resulting in better Pro Tools performance. Whether you're new to Digidesign's Pro Tools 8 or simply looking to pick up a few new tips and tricks, you are certain to benefit from this free software video tutorial. For complete instructions, take a look.

In this clip, the eighth installment in Sean Devlin's "Full Disclojure" series of Clojure video tutorials, you'll see how to use Leiningen, a popular Clojure build system. One of the most obvious perks of using the Clojure is the user community organized around it, which make learning the language a pleasure (and a simple one at that). For more information, including detailed, step-by-step instructions, take a look.

\When both equations in a linear system are in the form Ax + By = C, you can solve the system using elimination. How is this method different from substitution? The idea behind the elimination method is to create a new equation from a combination of the original equations in the system. The new equation is formed by adding or subtracting the originals. When we combine two true equations, the sum or difference must also be true.

Need to know how to solve a system of algebraic equations? From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of free math tutorials, you'll learn how to work with and solve system...

Cyber Security is a horrible computer virus. It mimics a virus protection program and invades your system, making it nearly impossible to remove. In this tutorial, learn how to remove this annoying trojan horse from your PC and save your computer.

This video tutorial will take you through all of the necessary steps of the Master Cleanse. The Master Cleanse is a fast that has been around for over 60 years. Created by Stanley Burroughs, the diet is based on the idea that we are constantly putting toxins into our systems and need to periodically flush them out.

This video shows you how to fix the annoying "Open Tray" error that you will occasionally get when you turn on your XBox 360 console. You turn your system on and even though the tray is shut and has a disc in it, it says you left it open. This is easily fixed though. Start by turning on your XBox 360 console, and wait for it to load. Then start to gently knock on the top of your system, if you have it laying down, and eventually it should start to load your disc. If this doesn't work, either ...

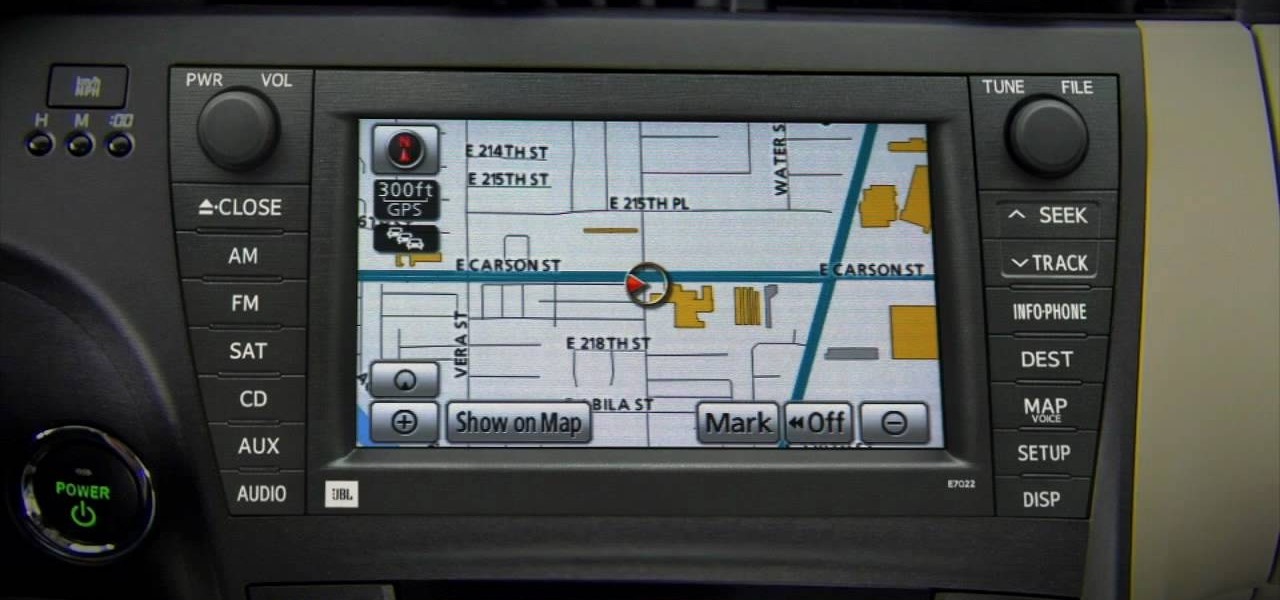
Learn how to use the navigation system in a new 2010 Toyota Prius in simple steps. It has DVD based navigation system with easy to use touch screen display. All the navigation routes of USA, Hawaii and parts of Canada are available in it supporting English, French and Spanish languages. When you start the car it opens the map and you can input the destination using voice command or entering text. You can also input your home address and five other special location address.

Learn how to use the parking assist mode in the new 2010 Toyota Prius in simple steps. Press the Intelligent parking assist button located under the power button when you park you car. Now select the type of parking you want to park your car which is either parallel parking or back in mode. For the parallel parking stay 3 feet away from the vehicle to your right and stop when you hear a beep. Press OK when ready, release the steering and gently control the speed as the system will steer for y...

This video shows you how to make a security device out of a door bell. The concept is that most thefts happen when people are away from home. To make sure of this the thief rings the door bell to make sure that nobody is home, if nobody answers then they will break in. A lot of people have dogs and alarm systems which will scare off the thieves, but this alarm system combines both. To make this devise you have to buy a speaker system that connects to your door bell. When the door bell rings i...

In this web TV presentation the host is talking about Grub 2. In Grub 2 you can mount an ISO file like a device with the loop back function. In Grub 1 you can use tack tack mem to mount iso files if the files are not fragmented by using the map command. Grub 2 is an application available for download that will be available after download as a chain from Grub 1 to Grub 2 to your operating system. Grub is a program that compresses all of your favorite boot programs into one.

Do you have a broken NES system lying around somewhere at your house? This video shows you how to fix it yourself with very few tools required.

You’ve decided to protest an unjust political system or organization. Make the most impact with these tips. Protest with courage, communicate with exiles and know your rights. If you disagree with a political system, concentrate your beliefs and opinion. Study famous dissidents like Ghandi and Martin Luther King.

In this installment from the Unorthodox Hacking series of computer security videos, you will explore a few of the areas in Windows that most Sysadmins don’t even know exist. See how to become Local System through the Task Scheduler and abuse long filenames. Take a look at some of the features within Windows—registry—that many system administrators don't know exist with this hacking how-to.

Watch this video to learn how to use glove molding systems. Glove molding systems are ideal for working on medium and large projects, this process involves creating a thin layer of flexible material and backing it up with a stronger, rigid material.This process can be used in automotive, mechanical, fine art and film special effects uses.

This video is a tutorial for setting up Native Instruments' Traktor Scratch system. While the setup can seem a bit confusing, with this video's help, you will be able to setup and use your system easily. You should practice setting this system up repeatedly, especially if you intend to use it in live performance, so that setup is quick, and troubleshooting is straight forward rather than a sweaty, nervous mess!

Your car's radiator needs to be cleaned to be cool. As time goes on, a car's radiator builds solid deposits that can clog the cooling system. A quick, inexpensive radiator flush can keep the system in shape. This automotive tutorial video will give you tips on how you can flush and fill the radiator and cooling system of your car.

Watch this video to learn the basics of installing an underground sprinkler system. The points discussed in this video are just a few of the ways a sprinkler system can be used and applied. The video covers ways to set up the system and calibrate it to effectively water your lawn and garden.

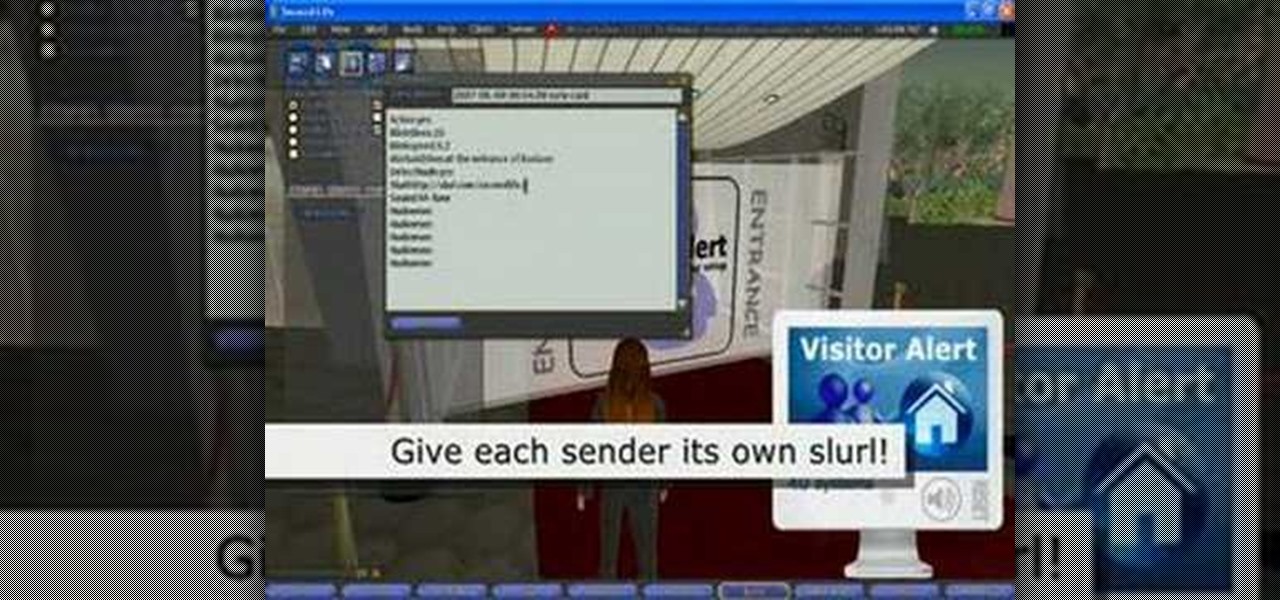
Concerned with strangers entering your Second Life domicile? Learn how to use the visitor alert system in Second Life to alert you when avatars enter your space.

You no longer have to completely convert your default or primary system language to change the language of a single app on your iPhone. Thanks to iOS 13, each app can now have its own language settings: if you want Spanish for WhatsApp but English for Instagram & Twitter, you can do that.

The interactive displays of the future as visualized in Steven Spielberg's science fiction classic Minority Report, as well as the augmented reality interfaces used by millionaire playboy Tony Stark in the Marvel Cinematic Universe, are now closer to becoming reality in the military realm.

In the latest example of life imitating art, IBM has applied for a patent for a video censoring system that looks a lot like the "Arkangel" child monitoring system from the latest collection of modern sci-fi fables from Black Mirror on Netflix.

Our universe has never been closer thanks to Apple's ARKit. YouTube user Jenil Kansara has been playing around with ARKit features and created a solar system in his room.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

Just recently, I was experimenting with a dual-boot Windows setup, and somehow managed to wipe my primary Windows installation in the process. "Why," I asked myself, "Why didn't I make a backup before I started this?" Still to this day, I'm going through the painstaking process of installing and configuring all of my favorite programs, and I may not ever get things back exactly the way they were.

Nostalgia sometimes gets the best of us—hence the reason we geek-out when we see emulators for SNES on Apple devices or N64 on Android.

Welcome back, my novice hackers! It has become clear from some of your questions that quite a few of you are unfamiliar with the hexadecimal system, or simply, hex. The hexadecimal system is used throughout computing and if you have never studied this Base16 numering system, it may appear relatively opaque.

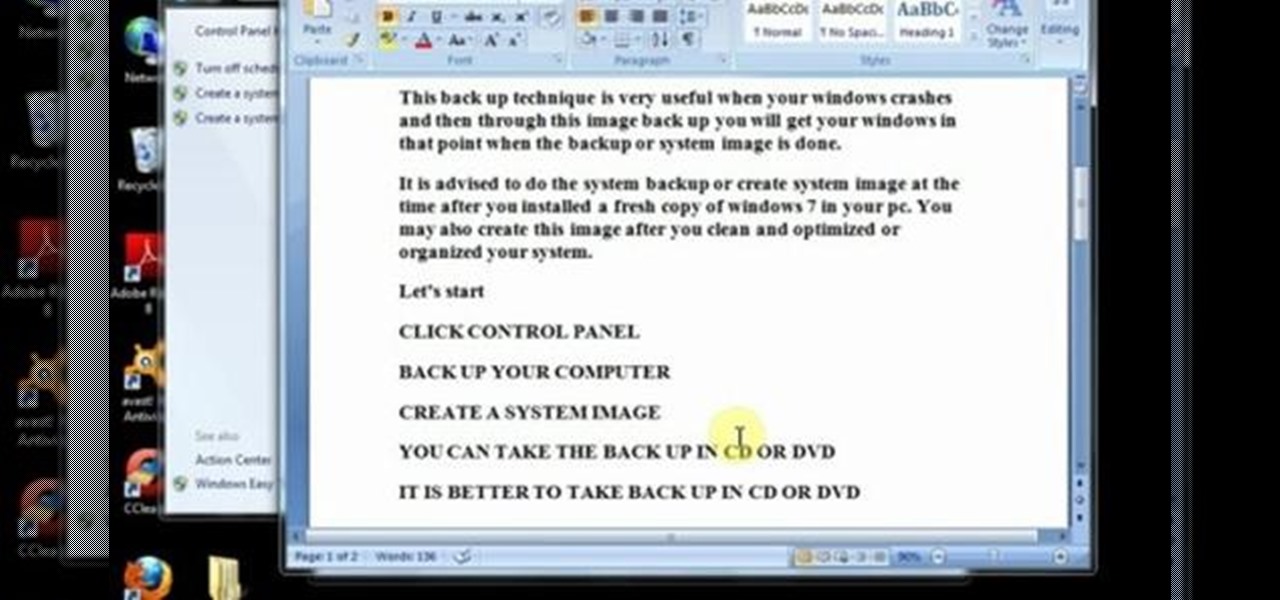
This video will help you how to create system image backup in windows 7. If you create an image of your system you could restore after crashes. Watch the video and follow the steps to create system image backup in your PC.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

Rooting your Samsung Galaxy Note 2 grants you access to system files, giving you the ability to change things on the device that you normally wouldn't be able to. Sounds great, right? There's just one problem. How in the hell do you manually change those system files?

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

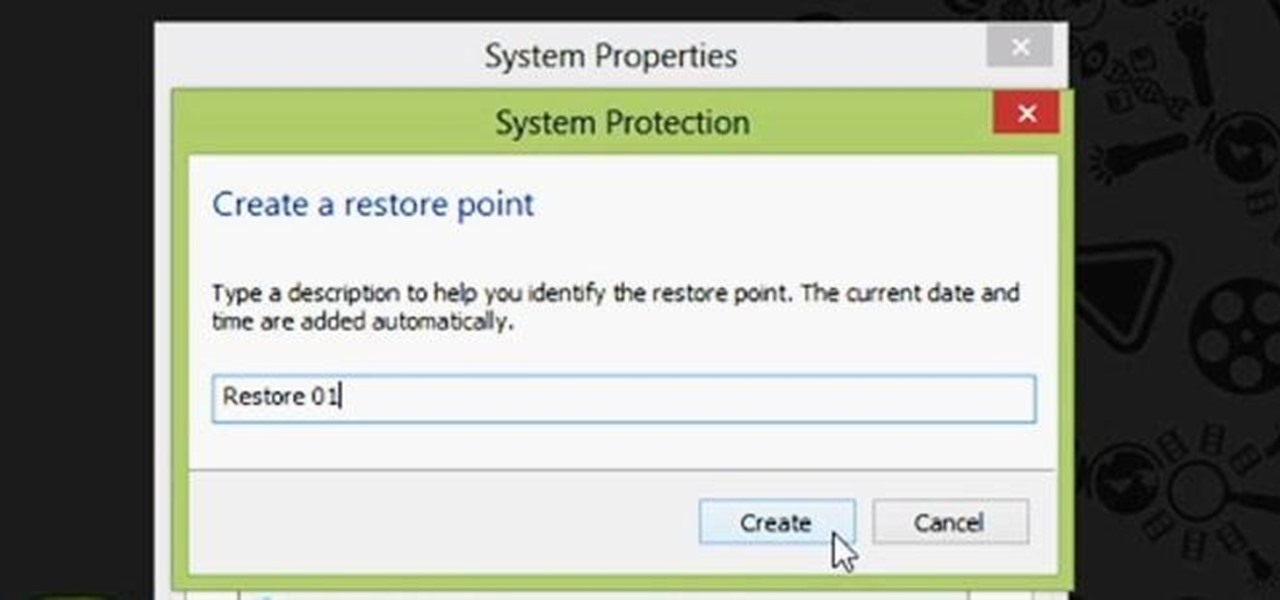
Restoring your computer to a previous point is an extremely important thing if something goes wrong. I've restored my computer at least a dozen times after downloading some suspicious software or running into an error I couldn't remedy on my own.