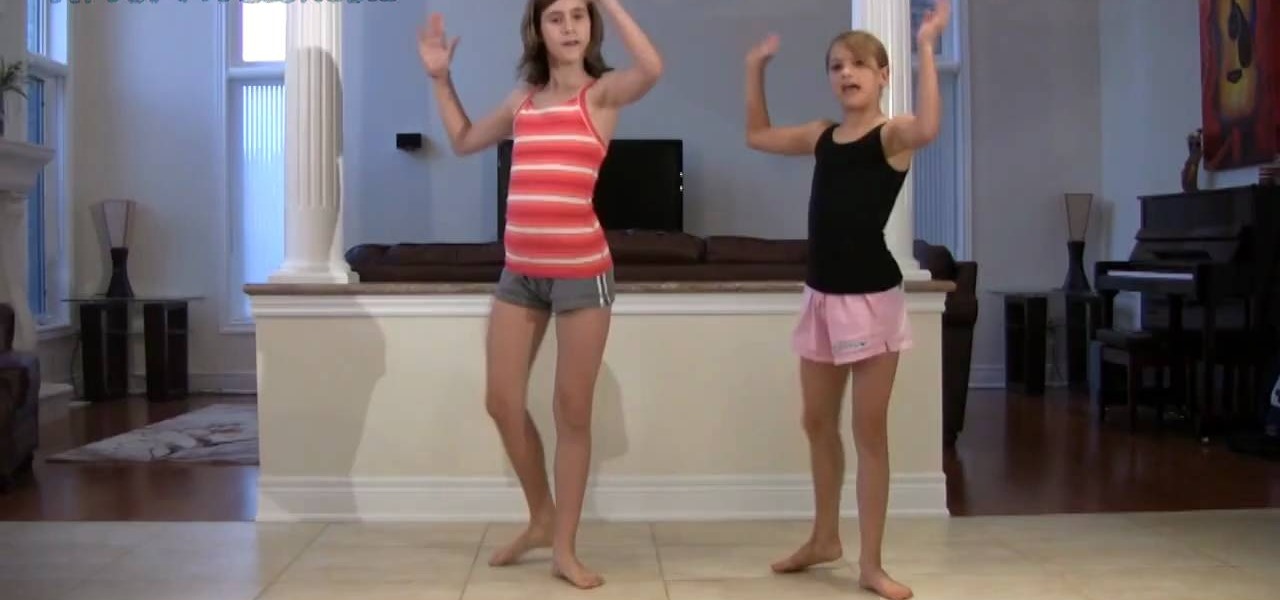
Ownspy is powerful program which can be used to backup your iPhone remotely. This program can be used in both good and bad ways. If you have children you can keep track of them by installing this program on the phone. This regularly uploads the content from the phone to the website. So in this way you can know in what way the phone is being used. Also this can be used by a jealous boy friend to spy on his girl friend. This programs tracks your location, backs up your messages, pictures. It al...

Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords.

This video describes how to insert keywords and SEO with the fusion essentials in the website. He asks you to first go to the site mode and then click on the home page and from there you can get in to the property box. There you can find three choices or tabs. He explains that the first one can be used to change the page name and page title and also can adjust the master border. The second tab is used to mention the page status, if it is done and can be displayed to the viewers or if it shoul...
In this video from PCRescueRepair we learn how to record streaming audio from any website using audacity. To get audacity just go to google, type in audacity, click on the link for audacity, and download audacity to install this on your computer. Also you need the LAME mp3 encoder which is on the audacity website. Now he takes you through the steps to do this task. Go into audacity and from the drop down change to stereo mix from microphone. On output adjust to max. and on input adjust the vo...

In this video the author gives an HTML Website Design tutorial showing how to make a side menu bar. He goes on to show how to write the HTML page, explaining about the different HTML tags like <html>, <head>, <title>, <table> etc., He shows how to set page color and add styling to the page. He shows how to align the page elements and does the font settings. He goes on and makes a HTML table. Next he shows how to make a menu bar using the table element and shows how to do the various settings ...
Orianna is a unique champion that focuses her abilities on the use of a ball she carries with her. The ball allows you to pull off some pretty cool tricks, including slowing your opponents in an AOE around it and harassing with it during the laning phase.

The League of Legends champion Kayle, or Judicator, received a rework a while back and now plays slightly differently because of that. Take a look at this champion spotlight guide by Riot Games on how to build Kayle as a hybrid support champion using the right runes and masteries. Be sure to take advantage of her ult so that you can save someone at the right time with invincibility!

Having cool photos as your desktop can make your computer a welcome sight, but having to find a fresh one every so often can get pretty stale fast. Thankfully, freeware utility Flickr Wallpaper Rotator for Windows PC's can import images for your desktop from Flickr automatically at intervals you set. You can even set it to use photos from a Flickr search or show favorites from a specific user.

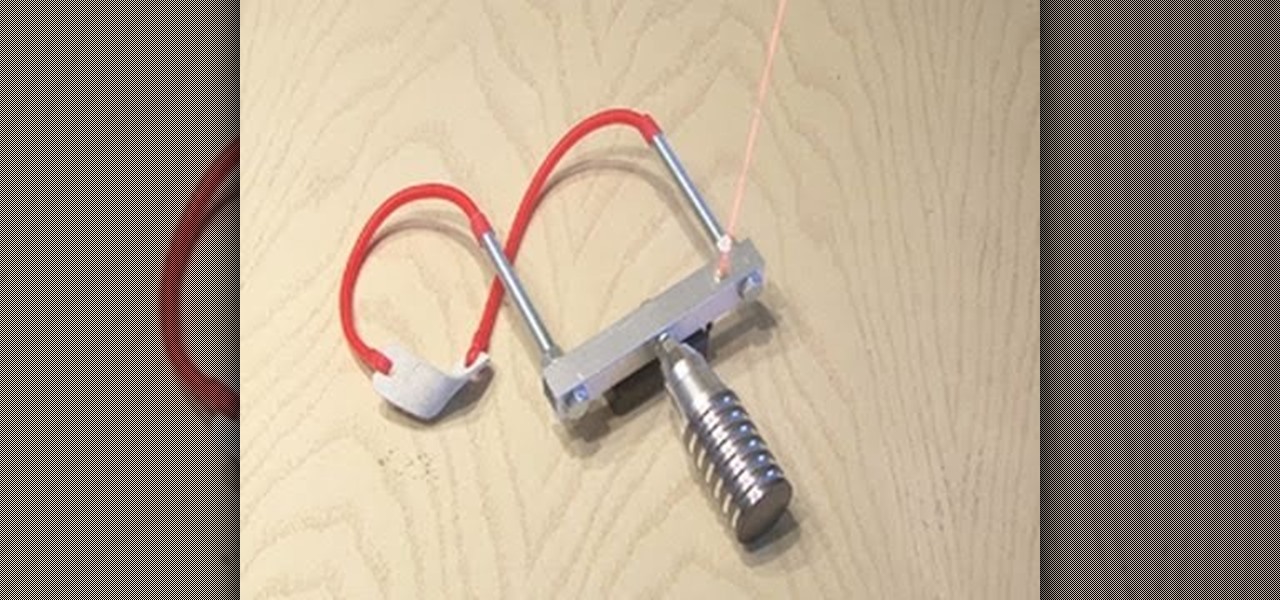
In today's day of mobile devices and improved technology, anything of yesterday can be considered retro— even a freakin' slingshot! Yes, that's right— forget fallen down tree branches. A rubber band and tree limb ain't going to cut it anymore. These days, kids need accuracy, and Kipkay has the knowhow.

FL Studio is one of the biggest names in digital music-making software, and Korg the biggest in physical gear. Unfortunately, FL Studio and the Korg nanoKontrol USB controller don't get along out of the box, and the transport buttons on the Korg won't work with FL Studio. That is, until you perform the steps in this video that will lead to a blessed union of software and hardware.

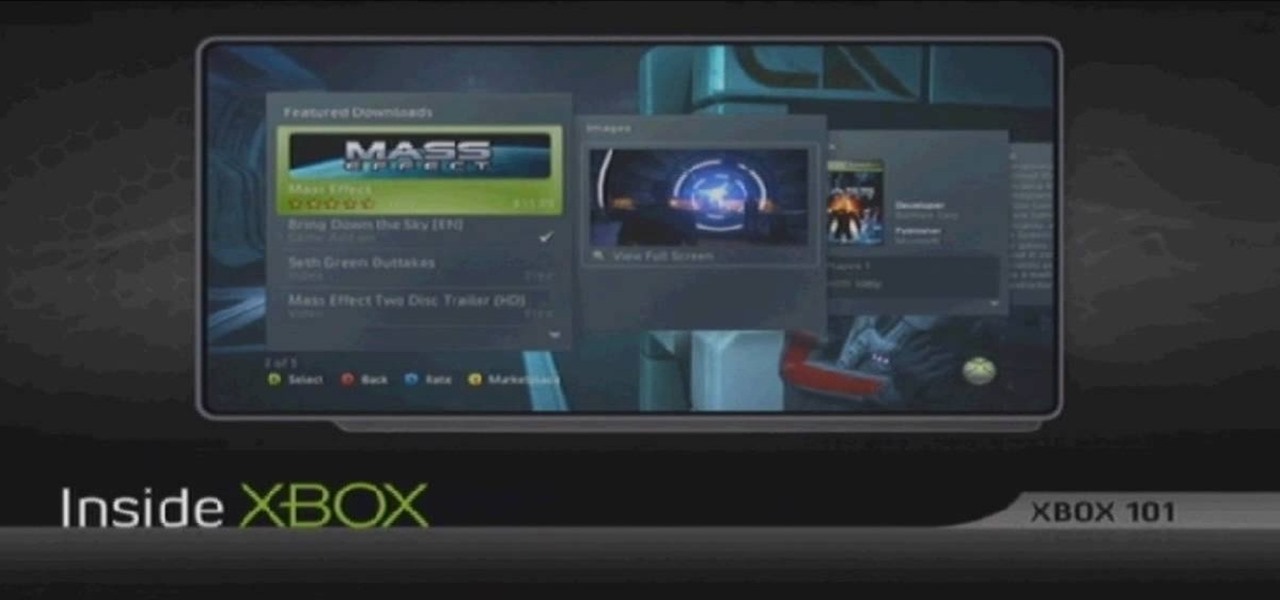
In this tutorial, we learn how to get Games on Demand on Xbox LIVE (Xbox 101). You will find all the newest games as well as classics and downloading is easy. It's the same process as downloading the demos. Just head to the marketplace and select from the title choice. You have the option to charge the title to your credit card or using points to purchase it. Each game is several gigabytes in size, so give it lots of time to download. To familiarize yourself with games, go to the website for ...

Create links and change elements with AS3 in Flash CS3 Use buttons to change the appearance of a button, navigate to a different place in a time line and link to a website. Use action script 3.0. Publish settings. Need to apply actions. Create an event listener. Attach to a button that you want it to listen for something to happen. When it hears a mouse click, it will execute the function. Give the buttons instance names R_btn, G_btn, and B_btn.

Photoshop might be the best software out there for creating effects on text and other still images. This video will show you how to create one really cool effect in Photoshop on a title. The creator calls this a glowing particles dust effect, and that sounds about right. The end result is words that are surrounded by a unique cloud of glowing particle dust. It looks really cool, and should really spice up your website or film titles.

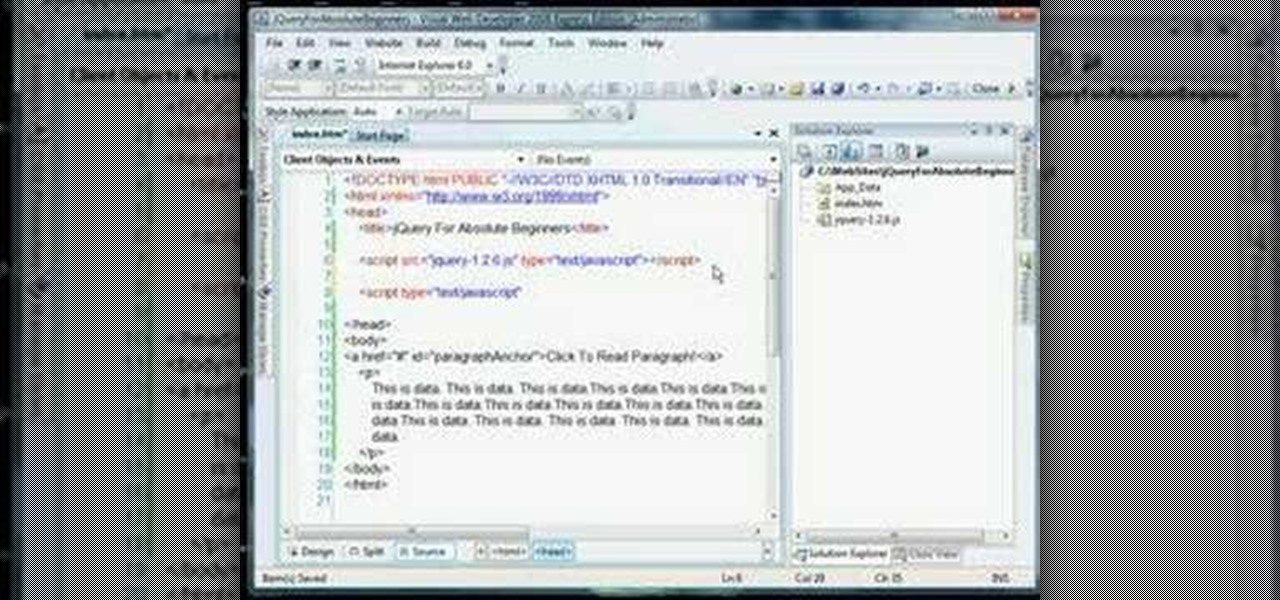
jQuery is a popular and powerful Javascript that is easy to use and heavily extensible. Have you wanted to learn how to use it, but lacking in the Javascript skills expected of you by many tutorials on the subject? This video for beginners will introduce you to the basics of using jQuery, from downloading it to making your first projects. Now you can take advantage of this powerful library to make your websites more dynamic and increase traffic.

In this video tutorial, viewers learn how to split their browser. This can only be done on the Mozilla Firefox web browser. Begin by going to the Firefox add-on website and search for "split browser". Then click on "Add to Firefox" to install the add-on. Once installed, users are able to right-click on any tab, go to "Split Tab to" and select the direction (up, down, left or right). Now click on the arrow and it will duplicate the tab in that space. This video will benefit hose viewers who us...

Photoshop is the photo-editing software of choice for just about everyone these days. It is very complex; but you're in luck! We have many videos here on site dealing with how to use Photoshop's many functions. This video will teach you how to display a picture inside of text by using masking. The effect is very cool, and sure to zest up your website or film.

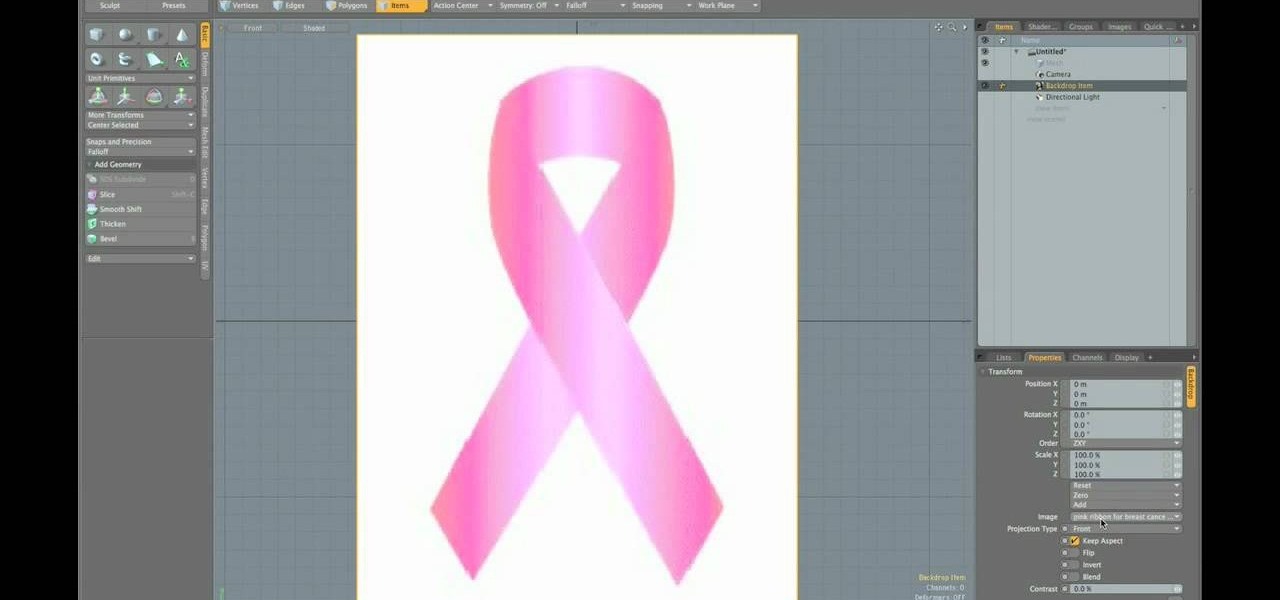
Breast cancer is one of the most deadly and tragic diseases afflicting women today. If you are interested in spreading breast cancer awareness and also in 3D modeling, then this video is a must-watch. It will teach you how to create a 3D model of the pink ribbon synonymous with breast cancer awareness, which you can then use on your website or in any other digital locale you wish.

In this video tutorial, viewers learn how to browse web pages without a mouse. Users will need to use the Mozilla Firefox browser. When you're in the Firefox browser, press F7 or click on Firefox, click on Preferences and select the Advanced tab (Mac OS X). Now check "Always use the cursor key to navigate within pages". This will activate character browsing, allowing the user to use the arrow keys to move up and down the page. Holding Shift will allow users to select a text. This video will b...

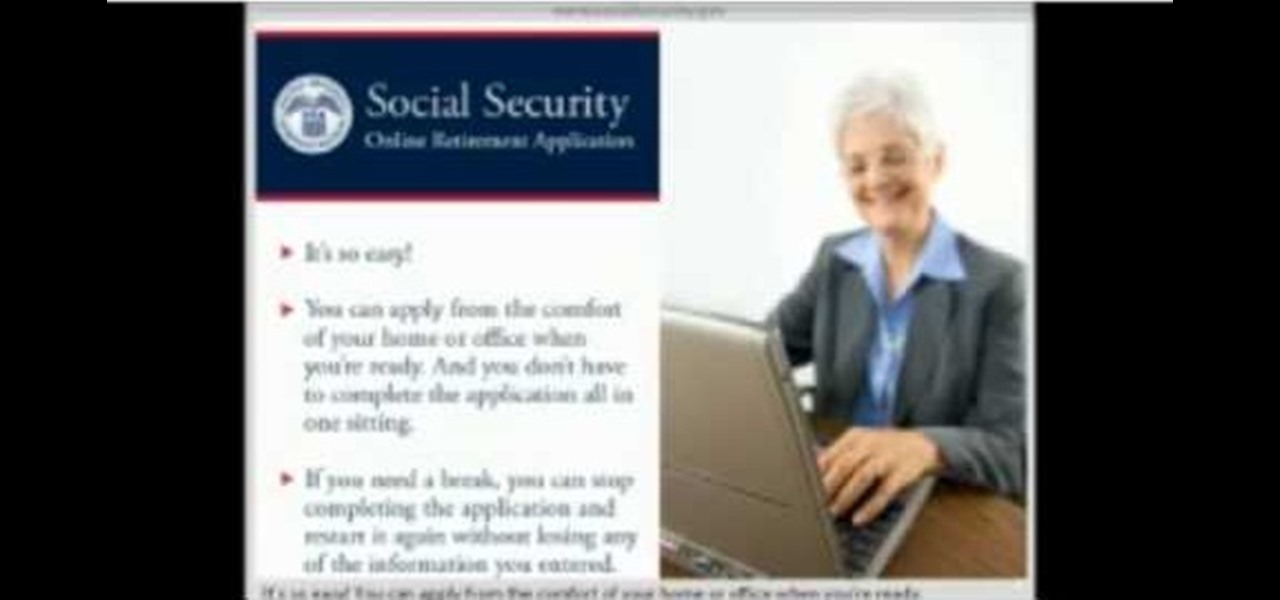
When you decide its time to retire, you will most likely need to cash in your Social Security benefits. In this official two part tutorial, presented by the American Social Secuity Administration, learn exactly how to use their website and apply online. Applying online is very easy, and takes a lot less time than applying in person. By applying online for social security, you will bypass all of the long lines and waiting that usually happens in one of the offices. Plus, you won't ever have to...

Want to disguise your URLs so that they appear suspicious? In the style of websites such as Tiny URL that take your original URL and give you a shortened one to post on your blog or twitter feed, Shady URL takes your original URL and gives you one that might convince people not to click it. Go to Shady URL and paste the URL you wish to disguise. Click submit, and on the next page it will give you a URL that looks, well, shady. It might include something about a mail order bride or an investme...

Learn how to update your contact information on your XBox 360 in simple steps. First to update your information through the XBox website go to My XBox and select 'Manage profile'. Now click 'Contact information' and update you information and details. To do it from your XBox 360 console go to My XBox and select 'Manage account'. Now click on 'Contact information' and then update your details. Do not give fake details because if you are selected for any offers you cannot be contacted.

Watch this tutorial to learn how to draw a hand giving a thumbs up. Make sure to pause the video after each step and look at the screen every few seconds while you are drawing.

Have you ever found yourself calling up a company, only to be denied due to not calling from the number listed on your account? Thanks to a website called Spoofcard, this is no longer an issue! SpoofCard let's you spoof the number you are calling from, as well as modify your voice (Male -> Female or vice versa). Best of all, it all looks completely legitimate.

Kids... it's dance time! Check out this dance video tutorial on how to do the Miley Cyrus Hoedown Throwdown dance. This dance is from the Hannah Montana movie from 2009 where Miley Cyrus performs the Hoedown Throwdown in Tennessee.

Check out this informative video tutorial from Apple on how to build songs in GarageBand '09.

Check out this informative video tutorial from Apple on how to mix songs in GarageBand '09.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to make calls and use voicemail on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

Household Hacker brings you fun hack how to projects in a variety of areas: electronic hacks, computer hacks, pranks, etc. Search Household Hacker on WonderHowTo for more videos by this creator. In this video, learn how to make YouTube paper.

In this video I show you how to get a Flash plugin to allow you to play videos in safari. Your iPhone/iPod Touch does not have to be jailbroken to do this. If you are having problems not getting the email make sure you look in your bulk or spam folder of your email. Just click the activation link in the email refresh the safari page and everything should work.

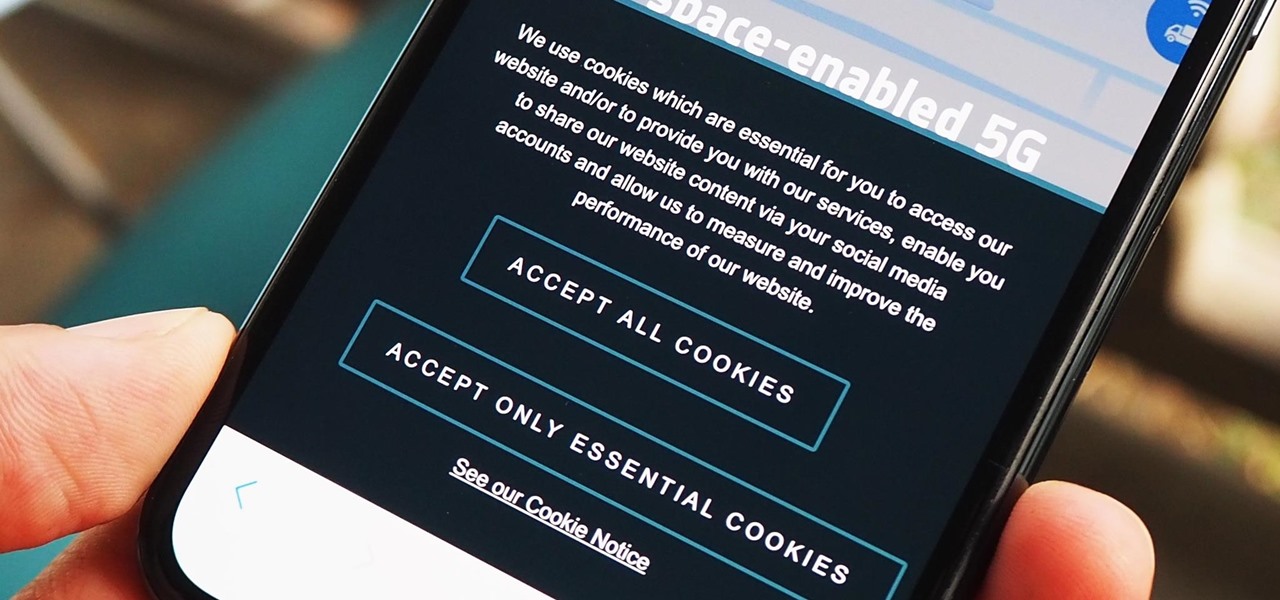
As a means to combat annoying and intrusive advertisements in Safari, Apple added native support for content blockers on the iPhone. Instead of being bombarded by notifications, banners, and pop-ups, content blockers prevent them from opening, which can also be said about those annoying cookie consent notices that many websites now have.

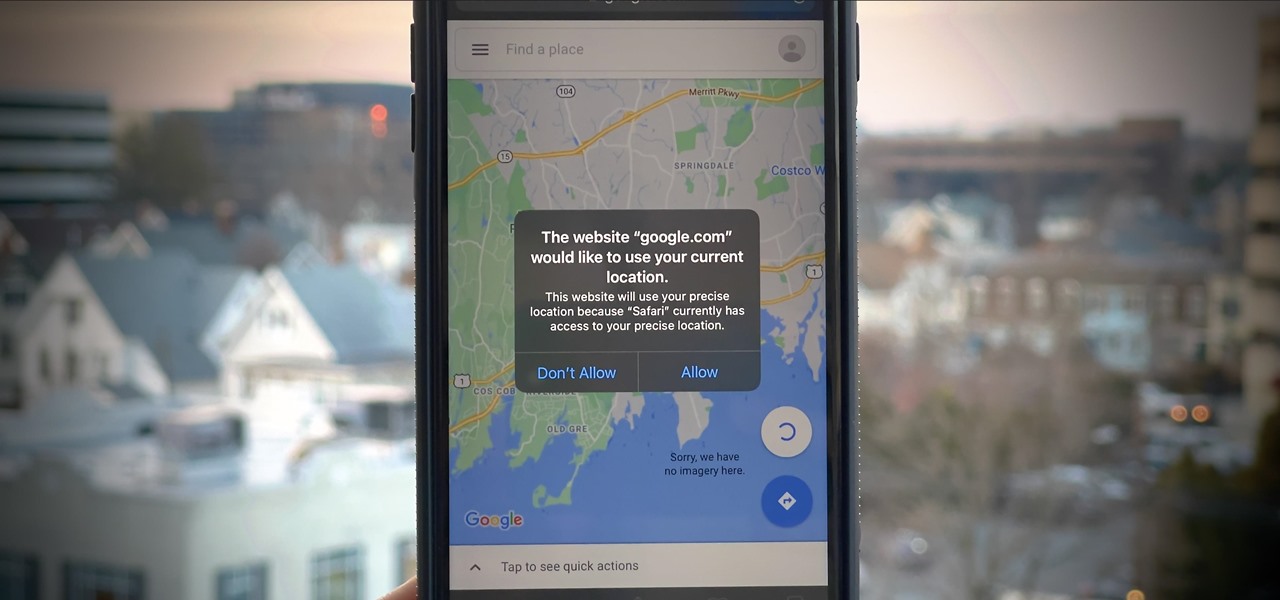
If you surf the web on your iPhone, you no doubt run into this problem all the time: a website wants your location. It can happen when performing a location-based task, such as using a store locator, or whenever a web app just wants to deliver better ads or local recommendations. If you're tired of allowing or denying permission each time, there's an easy way to stop the annoying security pop-ups.

It's pretty much a given at this point that Facebook has a lot of data on us. While you might be conscious of the data you share with Facebook when you post, upload photos, or chat with friends on Messenger, you might not be thinking about all the data it receives from websites and apps you use outside the social media giant. Now, you can actually do something about it.

Apple has seemingly always made it a priority to show how much it cares about user security and privacy — enough that it has a page dedicated to it, proclaiming that "privacy is a fundamental human right." It's true that there are few issues more important than user privacy when it comes to technology, and Apple only makes things better in iOS 13.

Business hours and addresses change, but they're not always updated on Yelp by business owners for the rest of us to see. Showing up when a business is closed or going to the incorrect address is a major annoyance, which is why the company allows us, the customers, to help update business information through the Yelp mobile app on iOS and Android. If owners won't do it, somebody has to.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

During the keynote at WWDC earlier this year, Apple introduced the latest iteration of its mobile operating system, iOS 12. Despite a thorough demo on stage, Apple glossed over new eye tracking features that use ARKit 2. Developers can now use the TrueDepth camera on the iPhone X, XS, XS Max, and XR to determine where your eyes are looking, opening up incredible new possibilities for new apps.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.