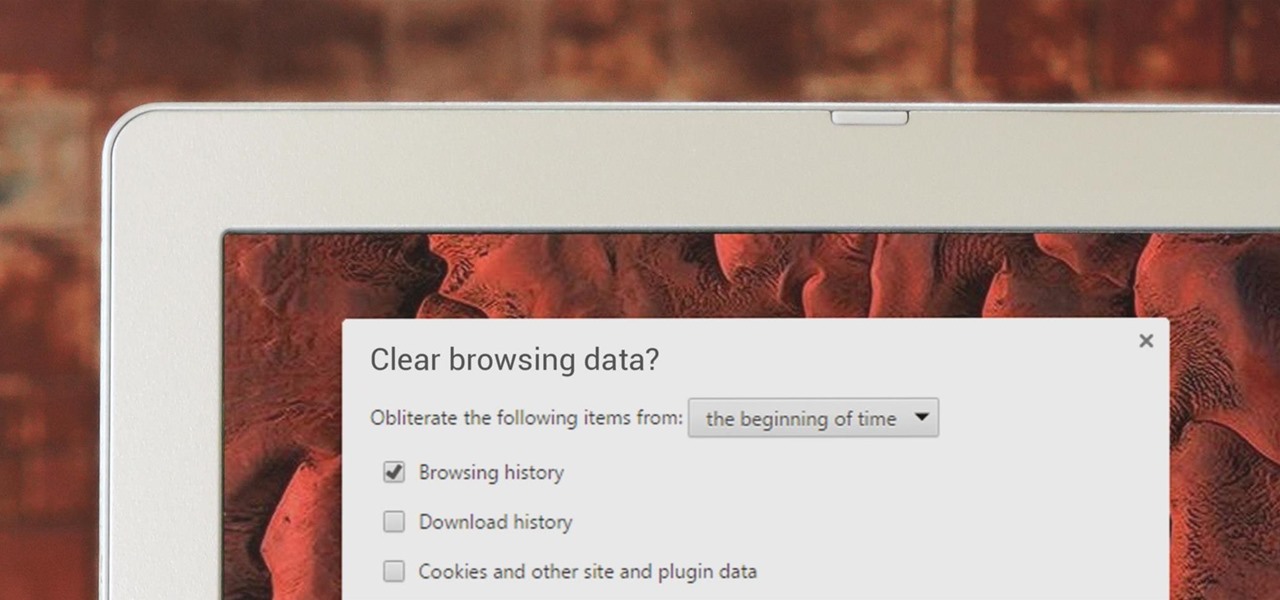
If you've been visiting websites of ill repute, or if you've been Christmas shopping and don't want to spoil the surprise, it would be a disastrous situation if anyone were to come across your browsing history. Visited sites, cookies, and cache can paint a very clear picture of your recent internet activity, and depending on the situation, you may only have a few seconds to delete your history before someone else barges in.
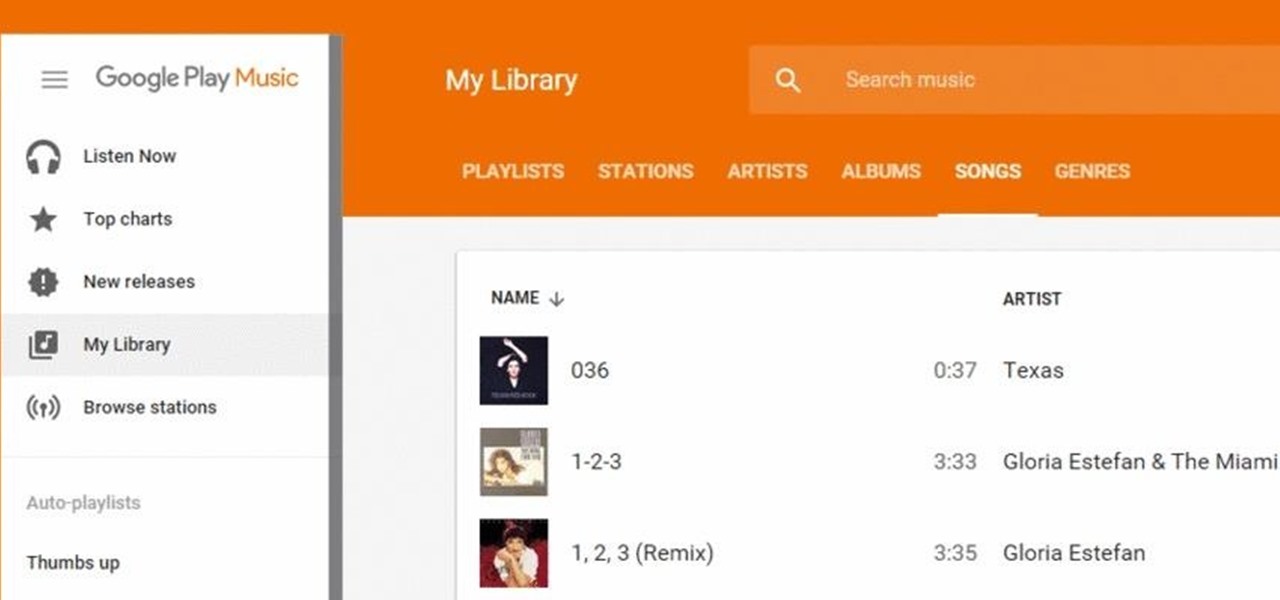
Google Play Music has been my go-to music service ever since its release. The free cloud storage for 50,000 songs and full access to Songza-powered radio stations make it a great music app, even without the $10/month streaming service.

This is My Review of the Electric Hair Brush Straightener LCD Iron Brush. I have had a Bad Experience please Watch this Video for more info!

I found this article a while back and I found it underneath a bunch of junk. Anyway, it's a article on 9 notorious hacker including Walter O'Brien (You know the T.V. show Scorpion? Well that's him). Not to mention the weird names:

As you all know, Anonymous have declared cyber war on ISIS and have already proven what they are capable of and whats to come.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

This Video will Show you how to Prepare Yarn before you do your Yarn Wraps, Braids, Faux Locs....etc

This Video will Show you how to make a Semi-Southern Meal Quick and Easy! I will be Having Fried Chicken, Greens, Sweet Potato Soufflé

With iOS 8.4 and iTunes 12.2, we got our first look at Apple Music, Apple's new streaming subscription service. While it's a little late to the party, there is definitely an incentive for iOS and Mac OS X users to switch over from competitors due to its heavy integration with the Apple ecosystem.

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

Video: . Hi, this is a quick demo about how to backdoor executables (software) sent over HTTP using MITMF, backdoor factory

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

An app called Launcher was released for iOS 8 last September that let users open any installed app directly from a widget in the Notification Center pull-down. For some reason, Apple didn't take too kindly to this and banned Launcher from the iOS App Store just a few days after its release.

Hi there, Elites Welcome to my 6th post, This tutorial will explain how to hack windows, using a program (No-IP)

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

Now that we have our vulnerable server, it's time to start up BeEF. Getting Started

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.

With all due respect to the fine folks at DrinkTanks, it's a little surprising that no one came up with their idea sooner. After all, last I checked, beer was pretty darned popular.

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

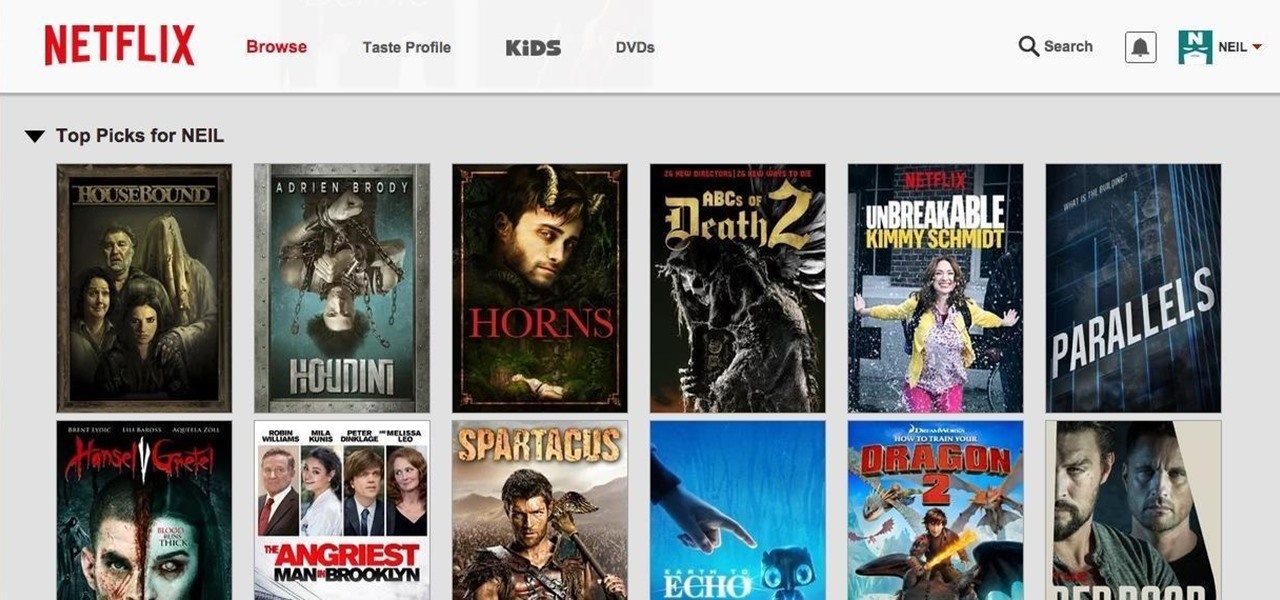
Netflix was my proverbial gateway drug to cord-cutting, as I'm sure it was for many others. Yet as much as I truly love Netflix and its service, there are some annoyances I have with the interface of the desktop web version.

Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...

Thanks to its longevity and familiarity among web designers, Flash is still alive and thriving, but HTML5 is catching up since it can render faster in web browsers, can be customized by developers on a per platform basis, doesn't need a plugin to run, and is less vulnerable than Adobe Flash Player to attacks (for the moment).

Here's a short and to the point tutorial teaching how to Bass Boost your songs with Audacity. To download Audacity for FREE you can go to the official Audacity website. You may want to Bass Boost your songs for many reasons, so here's a tutorial on how to do just that with the popular, Free, and easy to use software called Audacity.

With over a billion monthly active users, it seems that Facebook is nowhere close to being dethroned as the most popular social media service in the world (sorry, Ello). While their stats may be impressive, it doesn't mean that Facebook is as good as it can be.

In today's world, we're constantly switching back and forth between all of our internet-connected devices. A PC may be great while you're at your desk, but the living room couch is tablet territory, and nothing beats the portability of a pocket-sized smartphone while you're on the go.

This tutorial is for everyone who has been waiting for a solution to stream web videos to a Chromecast by using an iPhone or iPad. It is easy as a cakewalk.

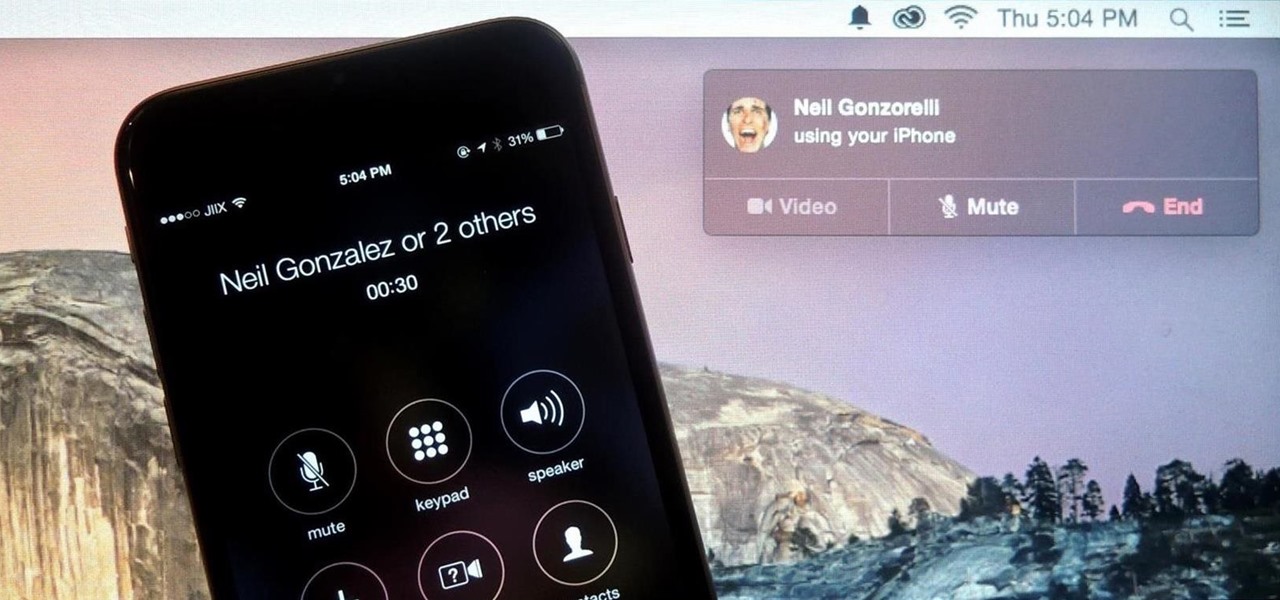
Earlier this year, Apple announced Continuity, a feature for Yosemite and iOS 8 that lets you connect your iOS devices to your Mac in order to access apps, receive phone calls, send text messages, and more while seamlessly switching between the two.

After about 3 weeks of working on it, I finally finished my Cookie Clicker! It's a concept that has been done before by sethbling and others, but I wanted to try and make something closer to the original since one of my subscribers asked me to. I think I delivered! Check my website for a download link (linked)

Apple introduced Touch ID on the iPhone 5S back in 2013, which let you unlock the device with your fingerprint. While it was an impressive feature, it could only do that one thing—unlock the device.

A shady practice in place by AT&T and Verizon Wireless—and possibly more wireless carriers—was recently uncovered. Outgoing data requests sent from devices on these service providers are being injected with a Unique Identifier Header (UIDH) that allows websites, the carriers, and potentially even government agencies to track your online activity.

The new iPhone 6 and 6 Plus have bigger displays, and that means more overall screen real estate, something that the new Safari app has taken into account by letting you access desktop versions of mobile websites. Even if you're sporting an older device, you'll still be able to request the desktop version of a site online in the browser.

Earlier this month, John Oliver spent a segment on Last Week Tonight explaining native advertising, a practice followed by many online media outlets such as BuzzFeed, The New York Times, and VICE, which combines editorial content along with sponsored advertisements.

One day I was contemplating about a canard paper airplane design. After several attempts, here is what I got - the Eurofighter Paper Airplane.

Over the course of the past few years, many websites have begun offering up a mobile-friendly HTML 5 version of their content. Videos that once required Adobe's Flash can now be played on any modern mobile web browser.

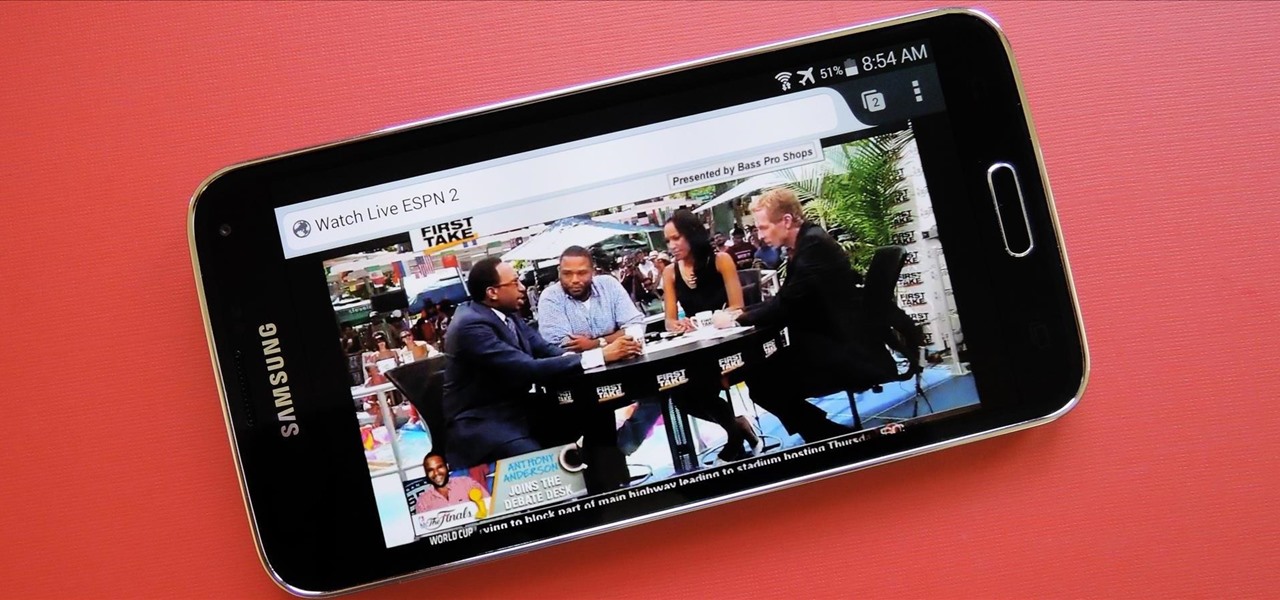
While FIFA may be one of the most corrupt organizations in the world (depending on who you talk to), that won't stop millions of us from tuning in this Thursday, June 12th, to watch the first game of what's going to be a month-long World Cup affair.

Welcome back, my greenhorn hackers!

Unless you've been living under a rock with no internet connection, it's safe to say that you've heard of the Heartbleed flaw that allows practically anyone with the right knowledge to steal your personal information, such as passwords, credit card numbers, and e-mail addresses using OpenSSL.

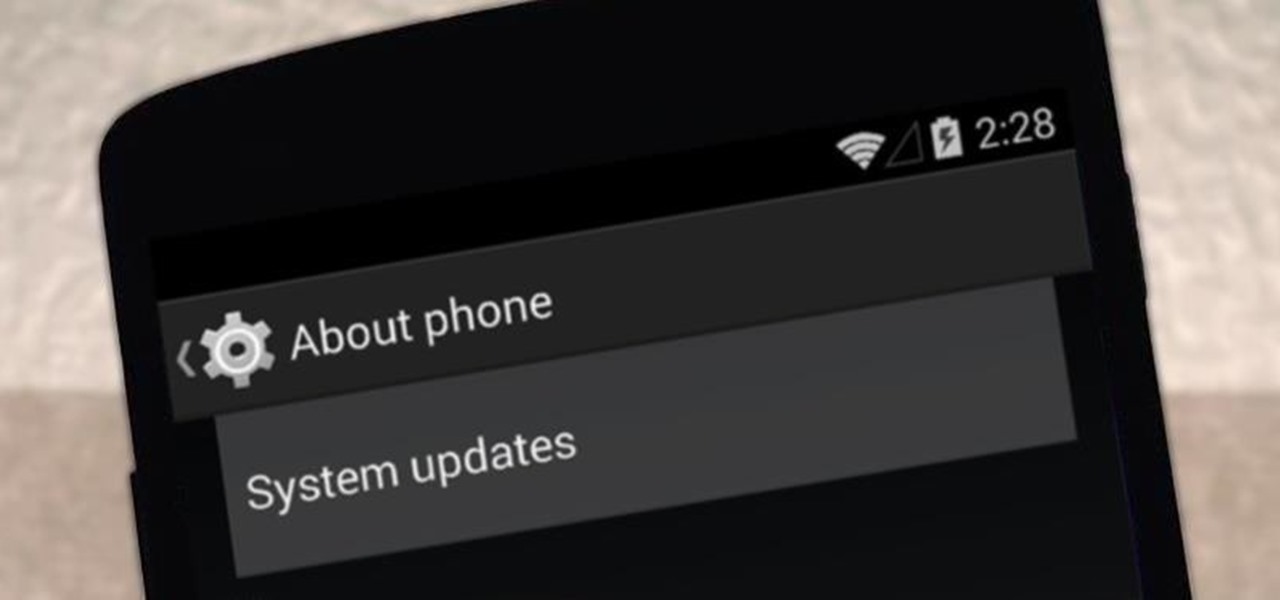
It appears that the next iteration of KitKat, Android 4.4.3, is fast approaching. If the past is any indication, today's update to the Nexus 5 software changelog on Sprint's website tells us a new version of Android will begin rolling out within 24 hours. Sprint has broken the news of a forthcoming Android release twice in the past. With 4.4.1 and 4.4.2, a mini-changelog was posted on the Sprint website about a day before Google began pushing updates to its Nexus devices.