Halloween is a night to dress up as any character you'd like—but for women, that typically means wearing something skimpy or downright absurd. From "sexy" policewomen to nearly undressed fairy tale princesses, we're surrounded by costumes that leave little to the imagination. And, let's be honest: who wants to spend a chilly October night in barely-there clothing?

We use smartphones for just about everything, and while that may be beneficial to us in our day-to-day lives, it can also be used against us in the court of law.

"After driving onto frozen river, man locks keys in car, engine melts ice." - Detroit Free Press. Avoid such a fate.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

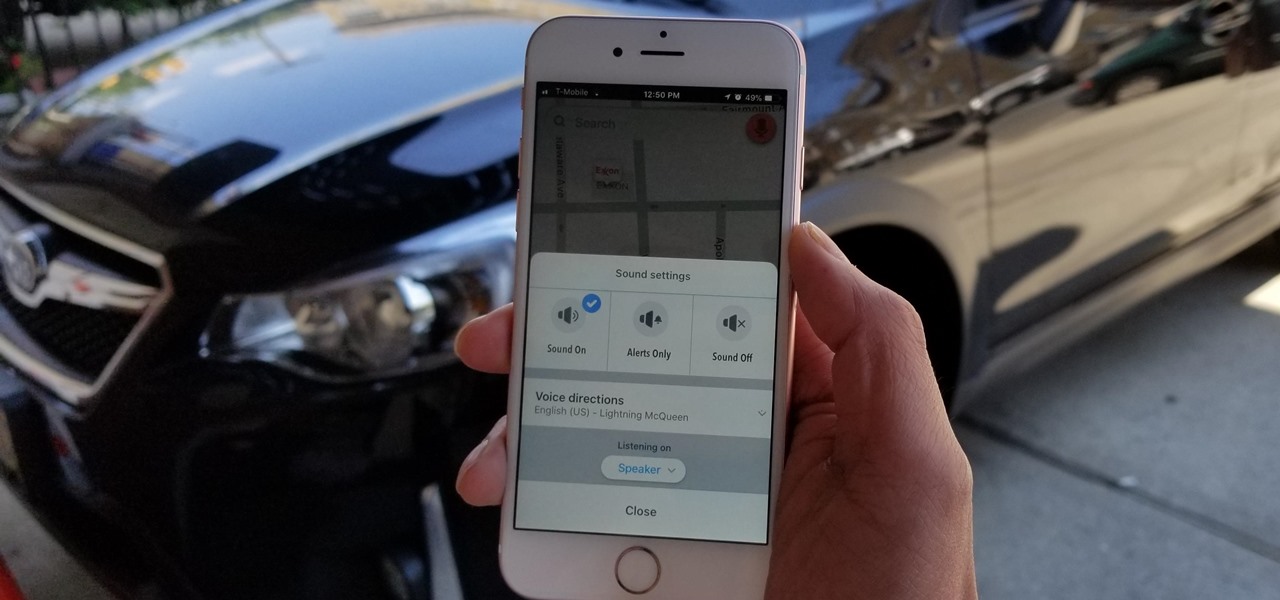
Waze is the go-to navigation app for millions of drivers, and it's easy to see why. Benefits such crowd-sourced traffic data, police trap locations, and road work avoidance are just the tip of the iceberg. It can almost be overwhelming, but with these simple tips, you'll master Waze and start navigating like an expert in no time.

Pokémon GO made waves as the first augmented reality game to gain popular adoption. In fact, it was so popular that it only took a few days to uncover some the benefits and serious issues with combining physical and digital worlds.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

There was recently a case that came to national attention where a gentleman was arrested at an airport for having a watch that looked like a bomb, among other things. As it came out, the watch was, in fact, not a bomb, and the man was just an artist who was probably trying to make a statement of some sort. Well, that message was lost amongst the hail of people shouting that either he had been stupid for bringing that watch on the plane and so deserved to be arrested, or that it's a free count...

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

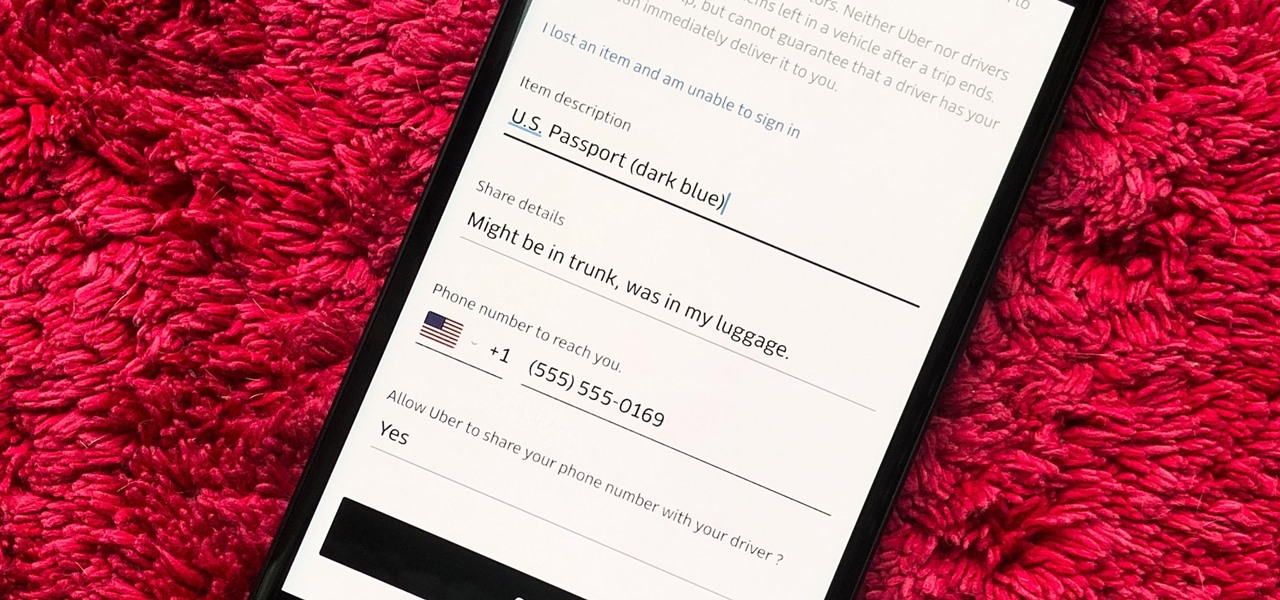
You would think that recovering your smartphone or another important item that you leave behind in an Uber ride would be a simple process, but it can actually be a pain in the ass. You have to find out how to report it to the driver, hope the driver is honest, pay a fee, and contact Uber directly if none of that works. But we're here to help make this process as easy as possible for you.

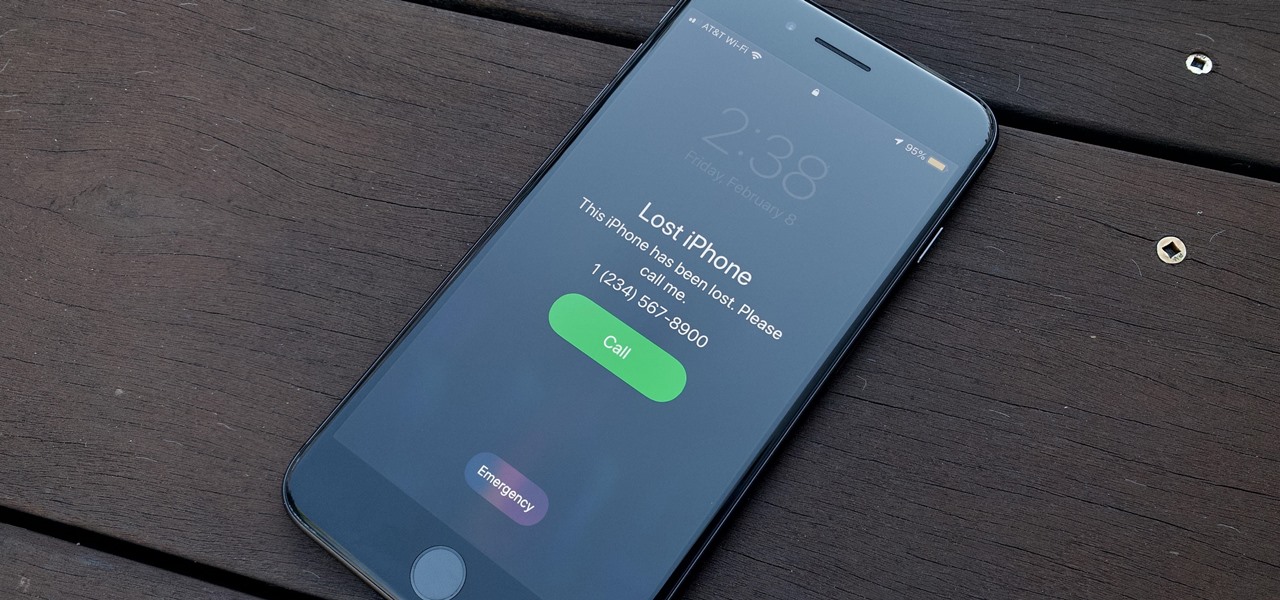
So, you're on the way back from a restaurant and realize you left your iPhone there, but you're late for a meeting and can't go back yet. You may as well kiss that iPhone goodbye, right? Not yet, as long as the right person gets their hands on it first. But that potential do-gooder won't know to contact you, and that's where Find My iPhone's "Lost Mode" comes in handy.

Everyone from first responders to hotel cleaning staff use radios operating in the sub-megahertz range to communicate, often without even encoding the transmission. While encoding and encryption are increasingly used in radio communication, an RTL-SDR adapter and smartphone are all it takes to start listening in on radio conversations happening around you.

If you've been looking for an alternative to Google Maps, look no further than Waze. In addition to benefits like crowd-sourced traffic data, police trap locations, and road work avoidance, the app even lets you personalize the voices used for navigation and directions.

If you're a Doctor Who fan, you've likely always hoped to see that iconic blue box appear on your doorstep with the Doctor asking you to come on an adventure. With the 13th Doctor just announced, this seems like the perfect time to tell you that thanks to Apple's ARKit, exploring the TARDIS is now possible!

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

Uber resumed its pilot program for driverless cars after one of its autonomous vehicles crashed in Tempe, Arizona last weekend.

Google Camera, the default shooting app on Nexus devices, is finally getting a feature we've been anticipating for years. As evidenced by a recent APK teardown done by Android Police, the beginnings of a new RAW capture mode have already been baked into the latest version of the app, which indicates that Google Camera will soon have the ability to store an unprocessed copy of the exact image your camera sensor captures.

Speeding tickets suck, and I don't know a single person that can tell me otherwise. But the reality is, most of us will break the speed limit for one reason for another, regardless of the pricey risk.

One thing you have to love about Google is their sense of humor. From their annual April Fool's Day pranks to the hidden Flappy Bird mini-game in Android to tons of hidden commands in Hangouts, you can just tell that those smart guys in Mountain View still like to have a little bit of fun with their work.

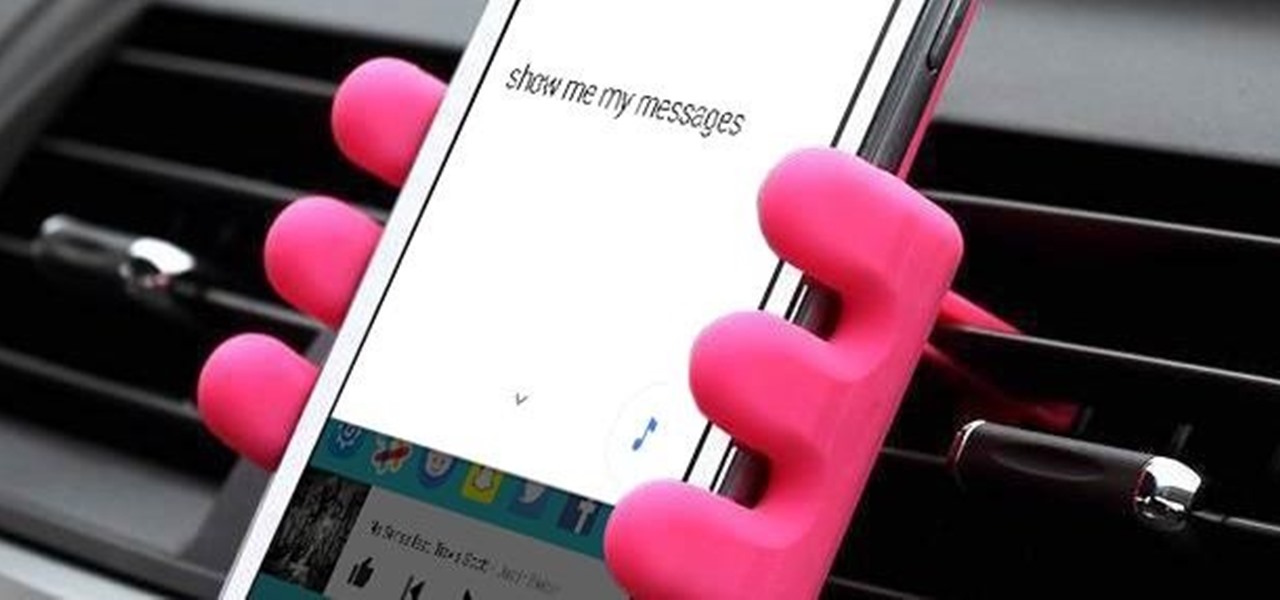
For some time now, iPhone owners have been able to use Siri to listen to and reply to text messages, but that functionality has been lacking on Android. That is, until Google silently rolled out a similar feature for Google Now (thanks to Android Police for the tip).

The biggest pet peeve of many Google Now users has always been the fact that you can't toggle basic system functions with voice commands. In fact, this was such an annoyance that folks even went so far as to apply root mods to get the functionality.

With most of HTC's staff working on getting Sense updated to Android Lollipop, their piecemeal approach to individual app updates now comes to their Gallery app. The new update is available for all HTC devices running KitKat, but if you have the HTC Service Pack installed, it will run on any Android device running 4.4 or above.

Google's original messaging service got a nice version bump today. Hangouts now sports stickers, video chat filters, an updated Material Design interface, and a few new features that should make the service a little more fun and easy to use.

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Unfortunately, there are plenty of situations where having a can of pepper spray could come in handy. Even worse, in most of those situations your state of mind isn't really conducive to remembering important details like the facial features of the person who's trying to mug you, which means the police will have a harder time catching the culprit.

Before lead was removed from gasoline, lead from car exhaust got into the air, was breathed in by kids, lowered their IQs, and increased crime rates (there is a very strong correlation between IQ and criminal behavior).

Alright guys sorry for the delay, lets just get to it: » Pelosi Says Holder Contempt Charge About Suppressing Vote.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

A spare key is one of those things that never seems like a huge deal until you need it. If you've ever lost your keys, had them stolen, or locked yourself out of your house or car, you know how difficult and embarrassing it can be trying to get your door open.

When it comes to platform games on mobile, endless runners are some of the hardest to play since they can go on seemingly forever. There's always room for improvement since your goal is to beat your previous score (or someone else's high score). But which endless running games are worth your time?

Lions and tigers and bears are just a few of the animals that Google users can now bring into their physical environments.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

You don't have to be a frequent flyer to know how indispensable navigation apps have become. Many of us rely on these apps for traveling from state to state and getting around in foreign cities, but even more of us count on these apps to beat rush hour traffic and find the quickest routes to school or work. So naturally, we all have our favorite mapping apps, but which one is truly the best?

Augmented reality gaming developer Niantic has decided to give its players the opportunity to make their mark on Pokémon GO with a PokéStop nomination system.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

It appears that the new AR app from LEGO is inching closer to release.