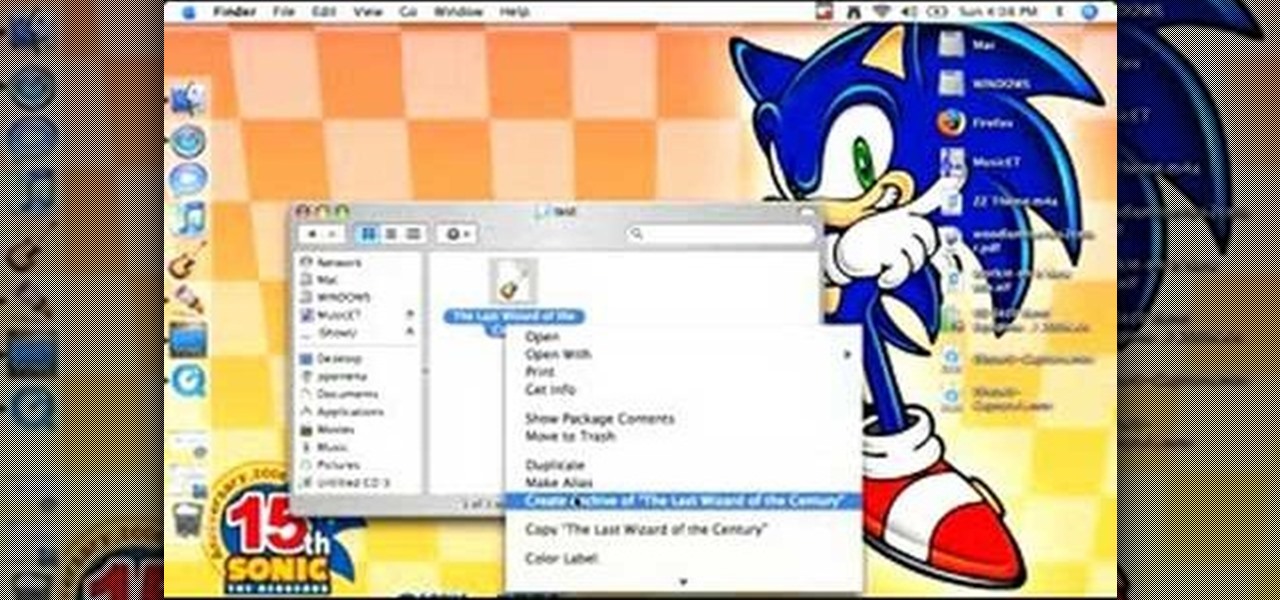
This video teaches you how to open .zip files with a just few easy steps. First, you need to download a program Winrar. The download can be found at http://www.rarlab.com/download.html and the download should start immediately. Once the download is complete, open the program.
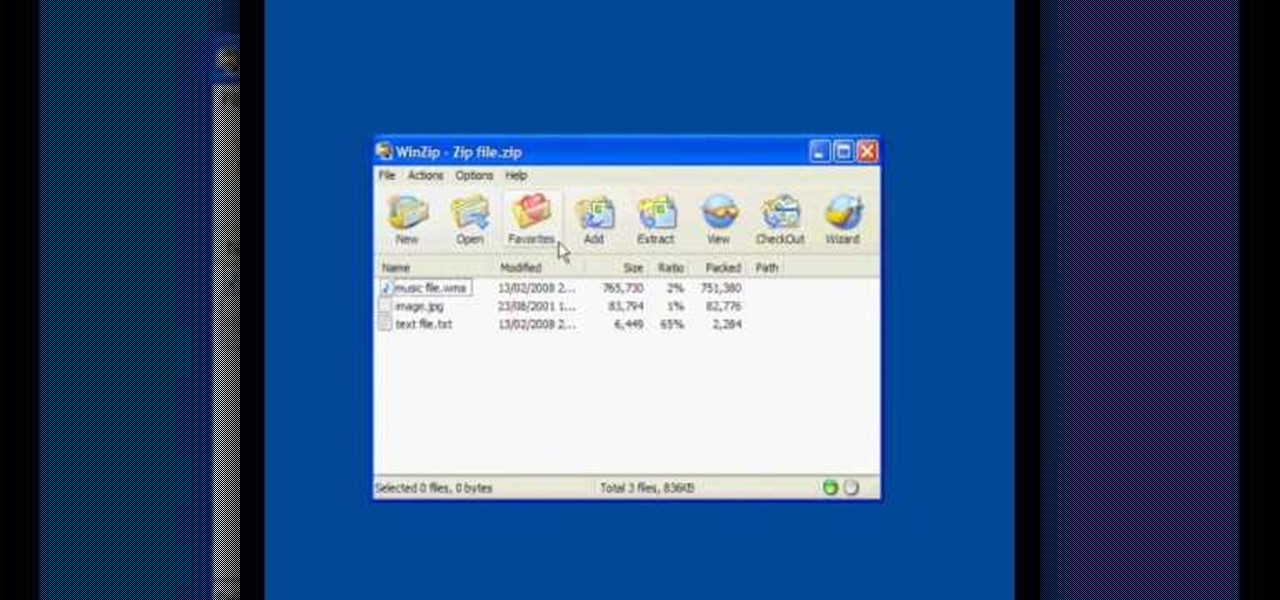
Do you have a hard time extracting/unzipping files using WinZip? If you follow along we will be shown a couple simple steps on how to unzip files using WinZip.
A tutorial on how to recover lost files once deleted from the recycle bin. The program illustrated in the tutorial is "Restoration". To download "Restoration", go to SnapFiles. The tutorial advises viewers to stop whatever they were doing once they realize a file is missing. Because the file is simply marked as free space, it is still present in the computer's memory but easily overwritten. To recover the file, a user will simply need to know part of the file name (preferably an extension, fo...
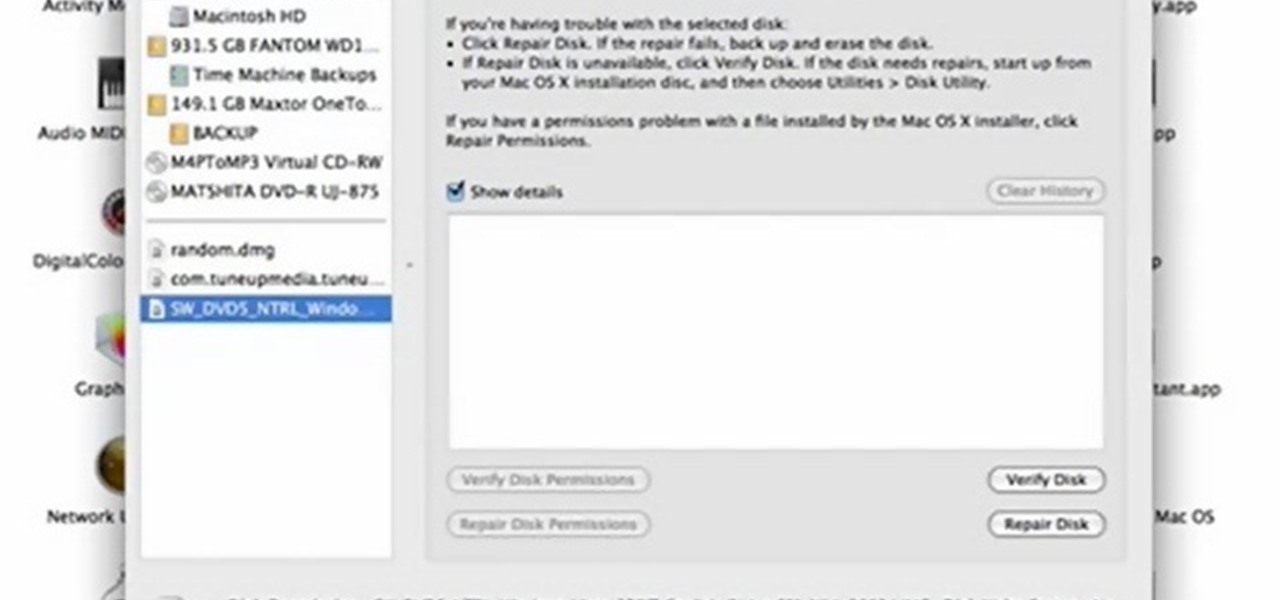
In this quick video tutorial Mike will show you how to burn an IMG file to DVD on the Mac. Follow these steps to burn an IMG file to DVD on the Mac: Click on Finder Applications Utilities Disk Utility. Highlight the file, click Burn. You will be asked if you want to burn it to the superdrive. Click Burn. It may take a while, but when you are done you will have a CD or DVD that is ready to use.
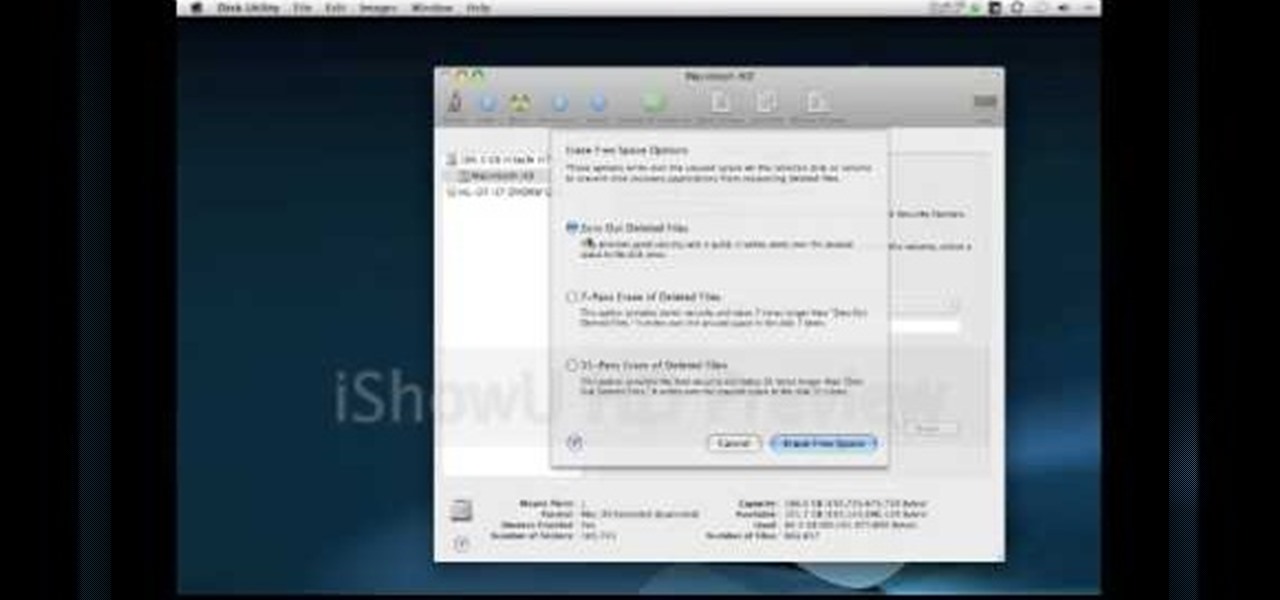
The guy in this video shows us how to permanently delete files on a Mac. First one would click on your desktop so the finder pops up and one would go to "utilities" and click "disk utilities". Next, one would click on the disk which they would like to clear, then click "erase" and then click "erase free space". After clicking, a box will pop up asking if you want to erase 0 times which clears the disk 1 time, 7 times which clears the disk 7 times to delete unwanted files, or 35 times, which r...

Have some files you don’t want anyone to see? Or maybe it’s just been a while since you’ve emptied your trash bin. The trash bin function is not a permanent delete but you can erase files off your Mac with this tutorial.

This video tutorial is all about recovering the deleted files in Windows Vista. If you are using the Windows Vista and you have unknowingly deleted a file and emptied the recycle bin, then you can recover it. This can be done by using the Shadow Explorer. Shadow Explorer is a Vista program that accesses the Vista Volume Shadow Copy Service. In Vista, the shadow copy service is turned on by default. It creates backups of files on a regular basis. Shadow Explorer provides access to these backup...

Do you actually trust your friends to not mess around with your files when you let them check their email or get on Facebook on your computer or laptop? You should think long and hard about that. If you insist on letting anyone get access to your computer, you should check out this tip from Tekzilla. Learn how to prevent people from messing with your files. Keep your files from being deleted or renamed, and keep them secure.

Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

New to Windows? No problem... here's a beginner's video tutorial that will teach you how to prevent cut, paste, copy, and delete on Windows files.

Check out this cool hack from The Emo Lab. This video tutorial will show you how to do a few Windows registry hacks!

Got video files on your computer? Watch them on your big-screen TV – using your Xbox! You Will Need

This software tutorial will show you how to email GarageBand files. Learn how to zip the GarageBand file and create an archive so you can email your GarageBand music files.

You have an assignment due, whether it's homework for school or a project for work, but you've only got a few hours left. There's no way you're going to finish in time and do a good job, and you don't want to turn in anything incomplete or half-assed. While it may seem you're out of luck, there's a simple way to buy yourself more time.

The built-in Files app on your iPhone has only gotten better since it was introduced in iOS 11, with small improvements after each new iOS version. You can manage files on your internal storage as well as in iCloud Drive, but one of the best features is being able to manage media and documents from all of your cloud storage accounts in one place.

OnePlus phones are easy to root, but that also means they're easy to brick if you get trigger happy with your superuser privileges. If you find yourself in this situation, you'll quickly realize the OnePlus firmware download page doesn't provide files you can flash in Fastboot mode.

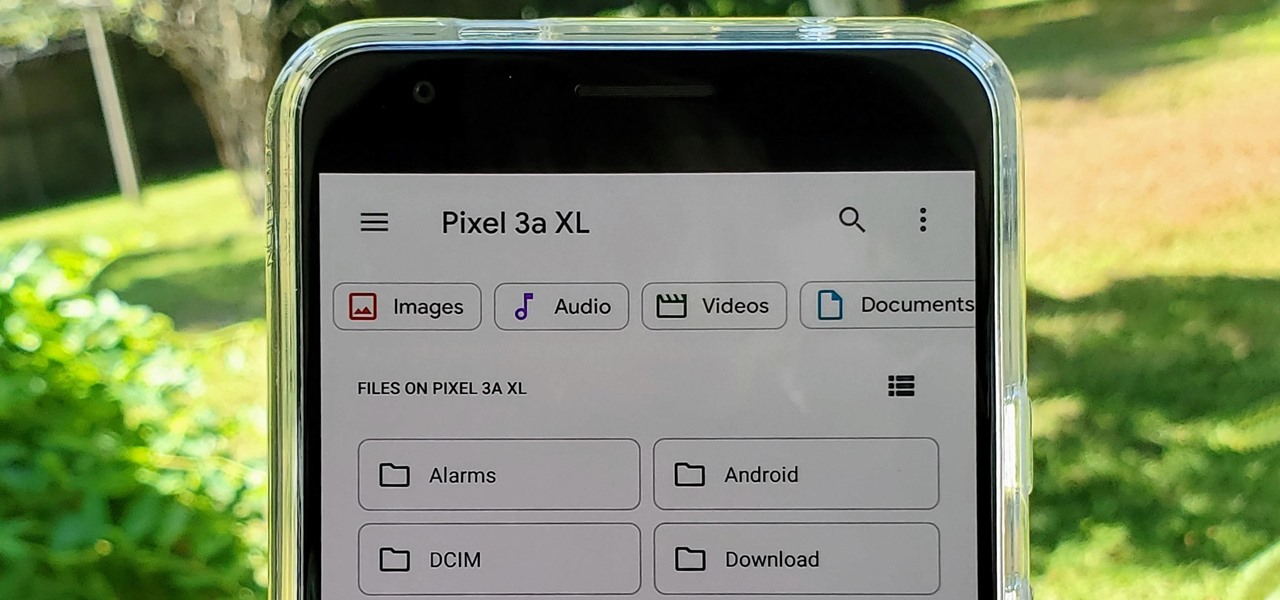
With the files on our devices getting more important as the years go by, the need to keep things organized continues to rise. The longer you have a device, the messier the internal storage might become. Having a file manager would be extremely useful in this situation. You could also reorganize the folder structure as well, just like you could on a desktop computer.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

When we reviewed the best file managers on Android, MiXplorer easily topped our list with its abundance of features, including tabbed browsing, support for up to 19 different cloud services, file and folder encryption, and much more. The only major complaint we had was the fact it couldn't be installed from the Play Store, but now, that is no longer the case.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Think back to when you last wanted to transfer some music or videos to your friend's smartphone and how difficult and slow it was. As powerful as our phones are, the default file sharing options are limited. There are, fortunately, some better options which make moving files easy, secure, and painless.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

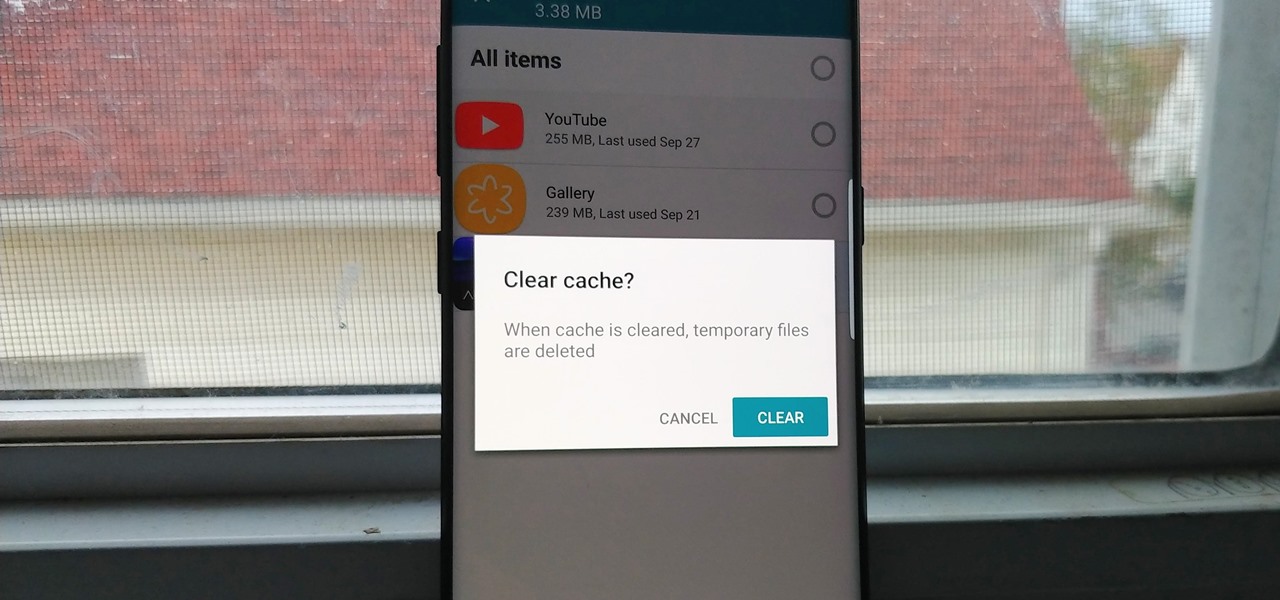
Since the release of the T-Mobile G1, the Play Store has been flooded with apps that claim to improve performance by clearing cache and storage. These apps are typically useless, rarely providing more than a temporary fix which Android undoes immediately. As Android has continued to improve cache and storage management, such apps have become more trivial. However, there are few decent ones out there.

Apple has finally given us a decent file manager in iOS 11. The new "Files" app replaces the not-very-old iCloud Drive app that appeared in iOS 9, but you can still access your iCloud Drive files in the new Files app, as well as files from third-party cloud services. A nice improvement, right?

A fairly hidden feature in iOS 10 let you turn websites and documents into PDFs, but thanks to the new Markup function in iOS 11, this process has become a lot more streamlined.

The LG V20 was released in the fourth quarter of 2016 as a flagship phone with audio capabilities far superior to that of anything else on the market—but only if you have your headphones connected. The single bottom-firing speaker, on the other hand, is just unpleasant to listen to. At first, it was believed there was a software issue with the speaker. However, it turned out to be an issue with the speaker grille impeding sound.

Copying files from a computer to your Android device has always been pretty straightforward—just connect the two devices with a USB cable, open your desktop file explorer, then move the files over. But what if you didn't need any wires at all?

As the first phones to be made by Google, the new Pixel and Pixel XL have several slick customizations that you won't find on any other Android device. There's tons of functional stuff like the new Google Assistant and a much-improved camera app, but also a few aesthetic tweaks to help class up the joint.

Android Nougat came with a lot of new features, including a futuristic and sleek circle animation. When this article was originally published, it was rumored that the circular design would be used as the new boot animation in Android 7.0—but as it turns out, you'll only see this screen while you're installing a firmware upgrade or working with ADB.

When you delete a file, Android doesn't actually remove it from your storage drive—instead, it simply marks that space as empty and pretends the file doesn't exist anymore. But deep down inside, the file that you originally wrote to that location is still physically there, at least until you randomly happen to save another file on top of that same spot.

Starting in Android 4.3, Google added some code to AOSP that tagged your internet traffic when you were running a mobile hotspot, which made it incredibly easy for carriers to block tethering if you didn't have it included in your plan. But as of Android 6.0, this "tether_dun_required" tag has been removed, which means you no longer have to edit a database file to get tethering up and running.

Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.

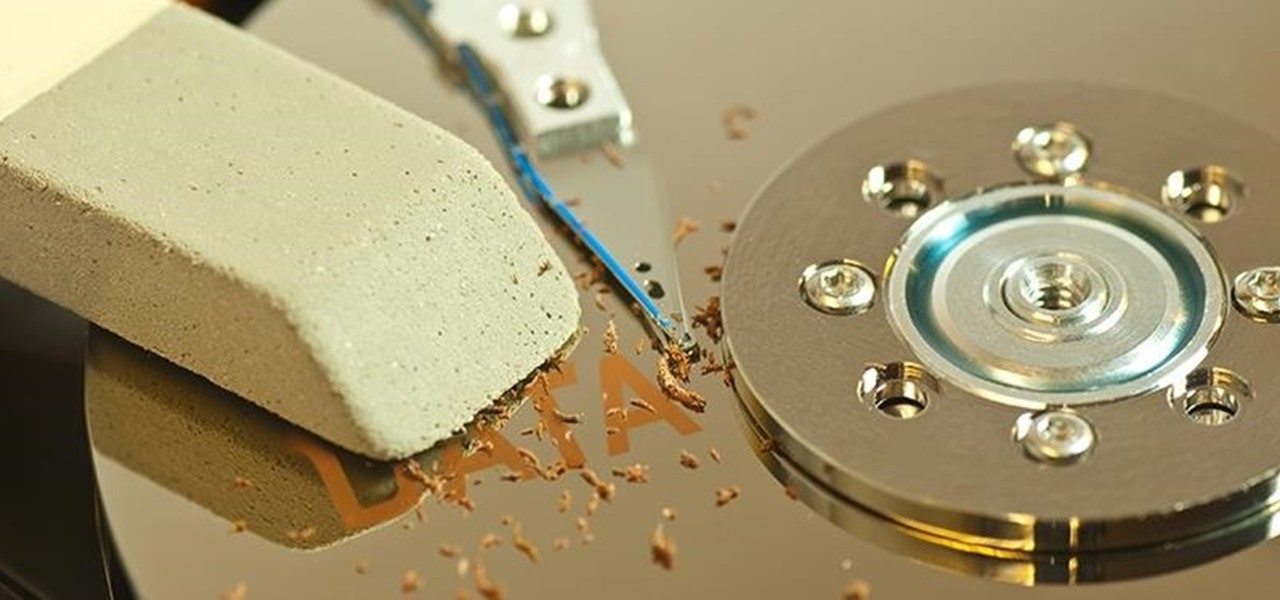
Do you have a file (or many files) that, in the wrong hands, may cause you trouble? Don't worry about it, because I'll show you how to wipe it (or them) from your computer in order to leave no trace behind.