Did you know you can help protect yourself when traveling with a gun? No, not like that; and not in any way that's going to land you in prison. Simply by packing a gun, you can ensure that not only will your luggage be safer, but that the airline will make certain that it reaches its destination. Photo by Alamy
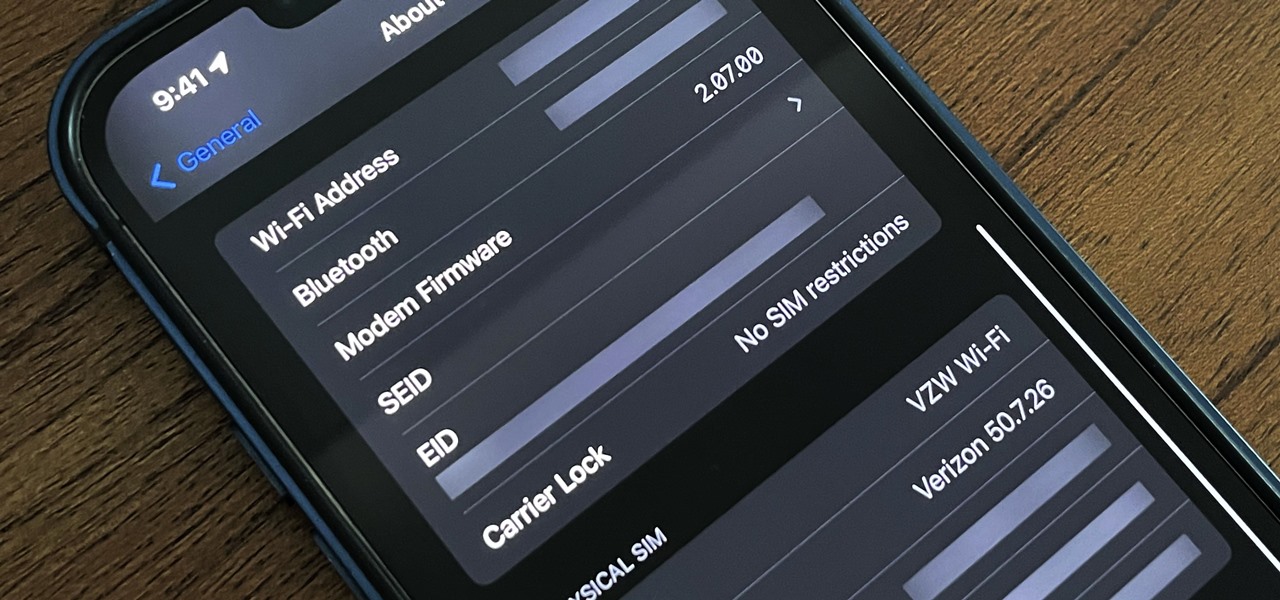
If your current cellular provider costs too much, has poor reception in your area, or doesn't support features you'd like to use, switching to another carrier is the obvious move. But can you bring your current iPhone or Android phone?
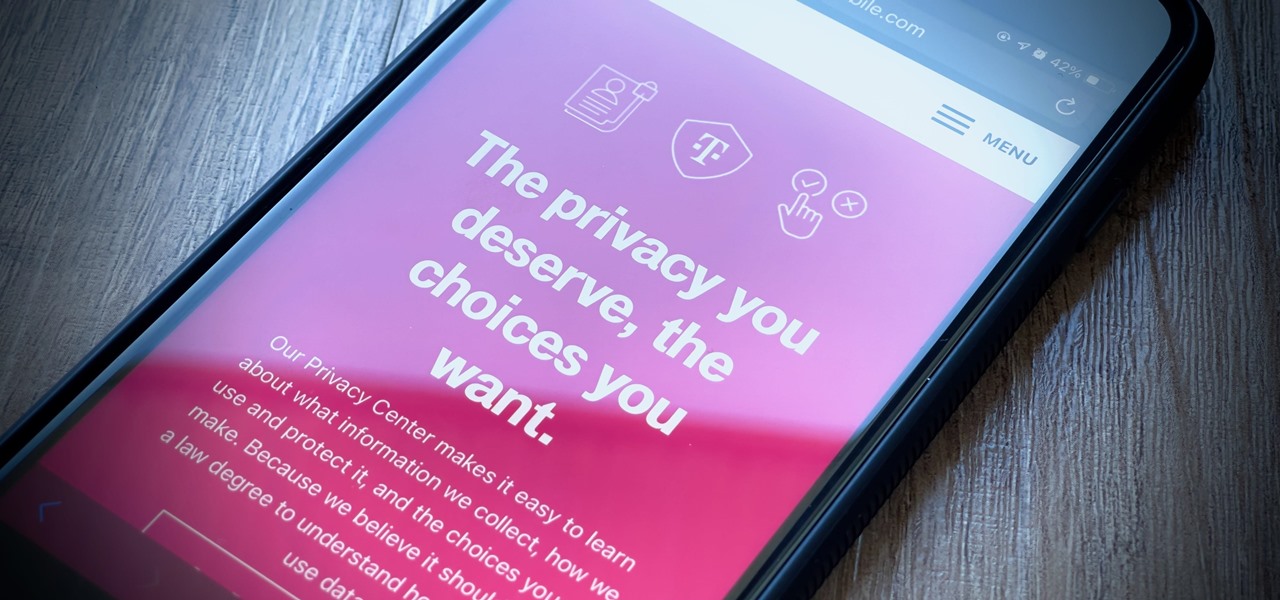
It's getting harder and harder to escape ad tracking by the day. For the latest example, look no further than T-Mobile. The No. 2 carrier updated its privacy policy on Feb. 23, 2021, indicating that it would start sharing customer data with advertisers under the guise of more relevant ads starting April 26. If that's not something you'd like to participate in, there's a way to opt-out.

There are countless tutorials online that show how to use Netstat and Tasklist to find an intruder on your computer. But with a few PowerShell functions, it's possible for a hacker to evade detection from the almighty command line.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

If you work for a company you are probably entitled to maternity leave. Gather as much info as possible and then have an honest conversation with your employers. With tact and civility should be able to have time to recover with your baby and keep your job too.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Facebook and its Oculus subsidiary have been open about their intentions to bring AR wearables into the mainstream for some time now.

I love finding new artists on Spotify to listen to but hate when musicians I don't like keep popping up in recommended playlists and radio stations. For the longest time, there was nothing you could do about it, but now, Spotify lets you block specific bands and singers from ever playing again.

Thanks to recent reports, we now know third-party apps have a lot more access to our Gmail than we may have initially thought. In fact, these third-party apps have the ability to read our emails, not because these companies are necessarily shady, but because we agreed to it. Luckily, there's a way to view which apps have this access, as well as a way to boot those apps from your Gmail entirely.

With each year that we anxiously await Apple's next big version of iOS, there comes the sad reality that the eldest iPhones will not continue to receive support. That's not the case with iOS 12, however, as the software is compatible with all iPhones currently running iOS 11, going back as far as the iPhone 5S.

A development duo has concocted an iPhone app that displays related tweets based on objects recognized by the device's camera.

In late June, the biggest measles outbreak to strike Minnesota since 1990 seemed to be winding down. Today, public health officials announced a new confirmed measles case in the area.

Much work needs to be done before laws and regulations no longer block driverless' rollout in the US, Rob Csongor, vice president and general manager of Nvidia's automotive division, said today during a US Senate committee hearing.

Apple is notoriously private when it comes to perspective products, but the latest leak from their De Anza office in Cupertino suggests that a new augmented reality device could be coming to a store near you.

Apple seems to want the public to perceive it as an environmentally-conscious entity, as evidenced by the company's recently published Environmental Responsibility Report. But as it turns out, they may be hindering recyclers from salvaging old iPhones and Macs by ordering the devices to be shredded instead.

The Huawei Nexus 6P was released a little over a year ago, but despite doing moderately well in sales, the device has had more than its fair share of issues. When first released, there were numerous reception and memory management difficulties that left users extremely frustrated, though, those problems were solved with updates pushed by Google.

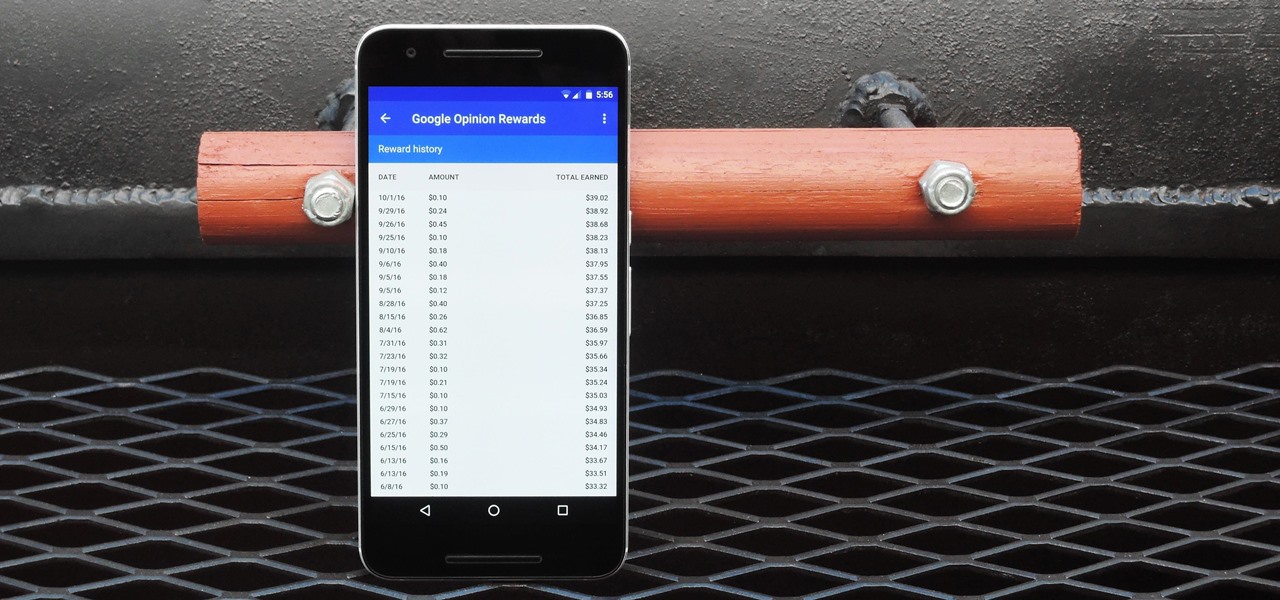
In case you didn't know, Google has an awesome app that gives you free money to spend on apps, games, movies, books, and virtually anything you can buy on the Google Play Store. The app is called Google Opinion Rewards, and all it asks in exchange for the Play Store credit is that you answer a few questions every now and then.

If you're looking to customize your Android beyond its stock options, things can get confusing quickly. One of the best places to get into developer mode is the XDA forums.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

While CNN, FOX News, and MSNBC are valuable sources of information for what's going on in the world today, they may not be the best news stations to watch if you actually want to learn something. They, along with local news stations, are great at grabbing your attention, but if you truly want to learn something about recent events, you're tuning into the wrong channel.

Welcome back, my apprentice hackers! In this series on password cracking, I have been attempting to develop your skills in the age-old art of password cracking. Although it might seem like a simple and straightforward exercise, those of you who have attempted password cracking know that there are many subtleties to this art.

Apple's new iOS 8 has a ton of new features, and so does their revamped Safari app, only some of the features aren't quite as obvious as others. In this guide, I'll show you my 5 favorite Safari secrets in iOS 8 for your iPad, iPhone, or iPod touch.

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

Amazon.com has been around for a long time now, but there are still a few things most people don't know about when it comes to buying products from them. Here's a quick roundup of tips to help you get the most out of Amazon and save some money in the process. The holidays are the busiest time of year for online shopping, but these tricks will work all year around.

Every time you Google something or click on an ad in a YouTube video, Google gets paid. They are estimated to make well over $100 million a day, and I honestly think that's low-balling it.

It starts innocently enough, with a nosy friend hovering over your shoulder to see what you're texting. Somehow, that doesn't satiate their inexplicable thirst for curiosity, so the first chance they get, they're rummaging through all of your super private photos—even though you told them not to.

Many people ultimately remarry when their first marriage eds in divorce or had mistakes written all over it. The choices you made do affect you future relationships and it is up to notice these and correct those problems so it does not happen in your next committed relationship. Learning Reasons Why Your First Marriage Culminated in Divorce

If you don’t have any little children to blame for an inadvertent or misguided app, book, or music purchase from Apple, you might still have a fighting chance. Apple has a very strict return policy, specifically stating that all sales and rentals of products are final for purchases made in the iTunes Store, Mac App Store, App Store, and iBookstore. But if you play it carefully and do a little digging, a return and full refund may still be possible.

Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...

Hello! This post is not about craft, it's about cyber bullying. If you ever had such an experience, that an unknown hacker was bullying you for no reason at all, please follow my words. Thank you! Step 1: Let All the People You Know That Your Are Being Harassed.

If you are looking to sell a lot on eBay, while maintaining satisfaction and product integrity then you are in prime position to be an eBay PowerSeller. As long as you stay within the bounds of the requirements, you can hold this particular title.

On this platform, we talk a lot about the future of augmented reality, and we pay attention to what is being said elsewhere as well.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.