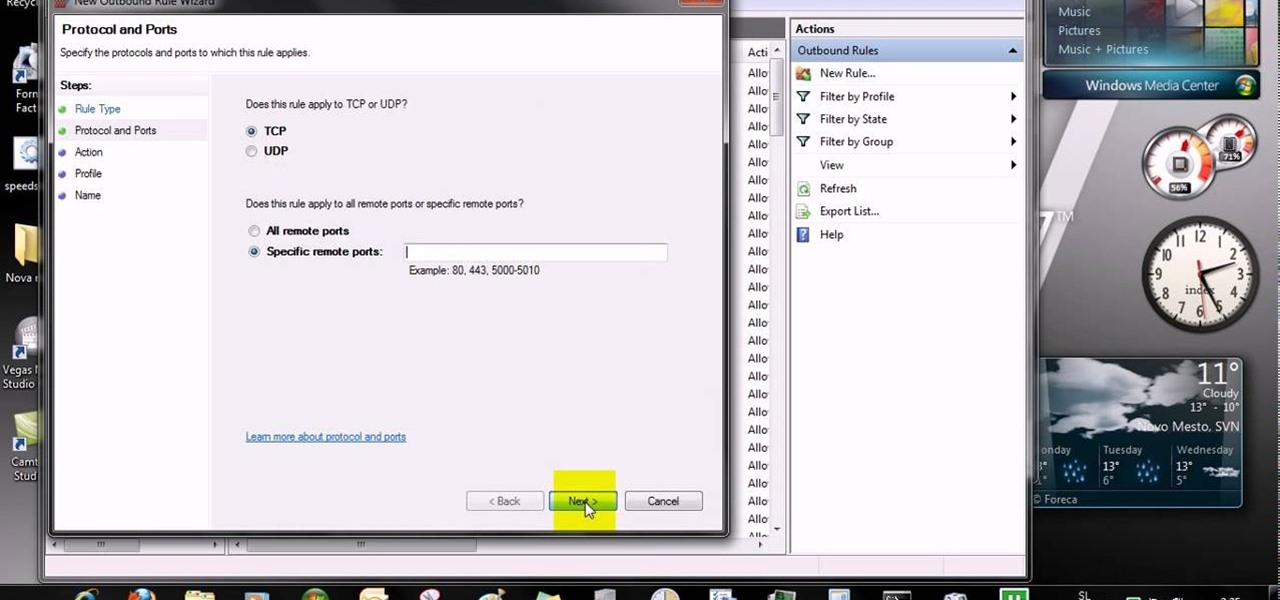
This video tells us the method to open ports in Windows 7. Click on myu icon and go to 'Preferences'. Copy the port number from the resulting window. Go to 'Start', 'Control Panel' and 'System and Security'. Go to 'Windows Firewall' and 'Advanced Settings'. Go to 'Inbound Rules' and 'New Rule'. Click on 'Port' and select 'TCP' and 'Specific Local Port'. Type the port number in the text box. Click 'Next' and 'Allow Connection'. Press 'Next' twice and put the name in the space provided for it. ...
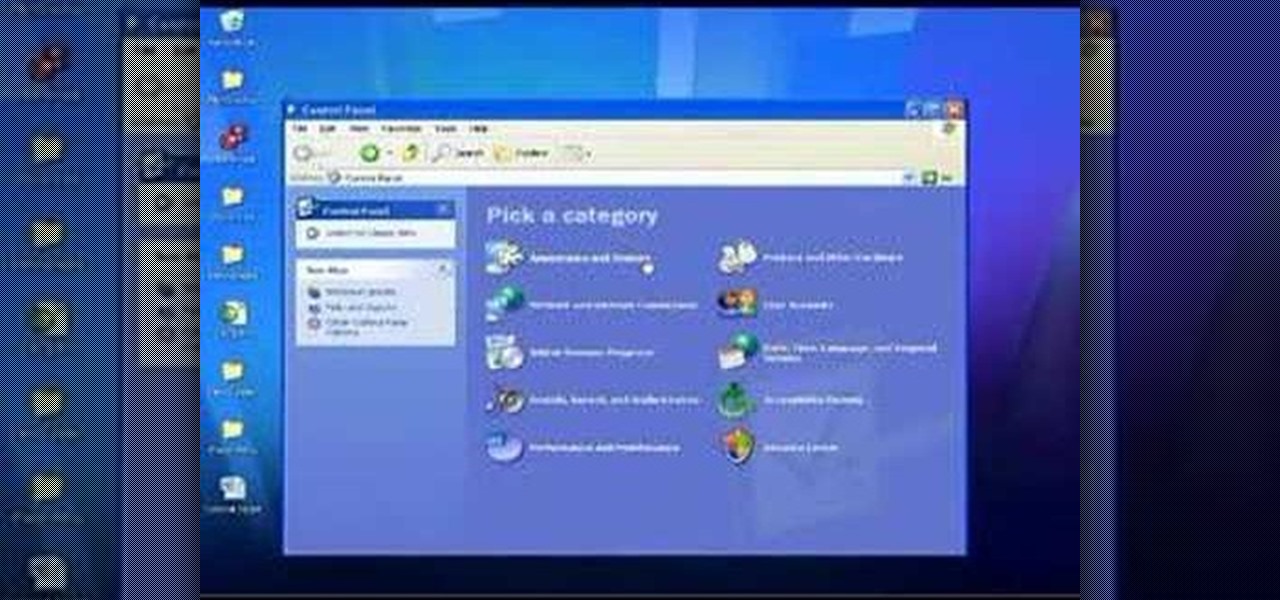
In this Computers & Programming video tutorial you will learn how to use the Remote Desktop feature within Windows XP. This application will enable you to access your home computer from office using the internet. This application is really very easy and simple to use. You have to ensure 3 things for this to work. Ensure that the computer on which your files reside that you want to access has all the components of XP installed. This is the host. The computer that you want to use to access the ...

Dafistps3dude4life shows us how to remove friends you have already requested and accepted from your Facebook account. First, sign in to Facebook with your account email and password. Next, look for a tab at the top of the screen with the "Friends" title. Click on it and you will be taken to a new page. Look to the left and click the "All Connections" button. Find the friend you wish to remove. There should be a small box with an "x" on it. Click on it. You will then be shown a prompt asking i...

In this video tutorial you will see how to Pandora a PSP slim battery. You will need a knife for this. When the normal battery is in the PSP, when you switch it on, it will log on just normal. Now remove the battery, put the knife in the joint of the battery case and move it up and down and slit open the case. Then pry it open and remove one half of the case. Then flip open the flap on the battery and cut off one connection on the battery as demonstrated in the video. Now put the battery back...
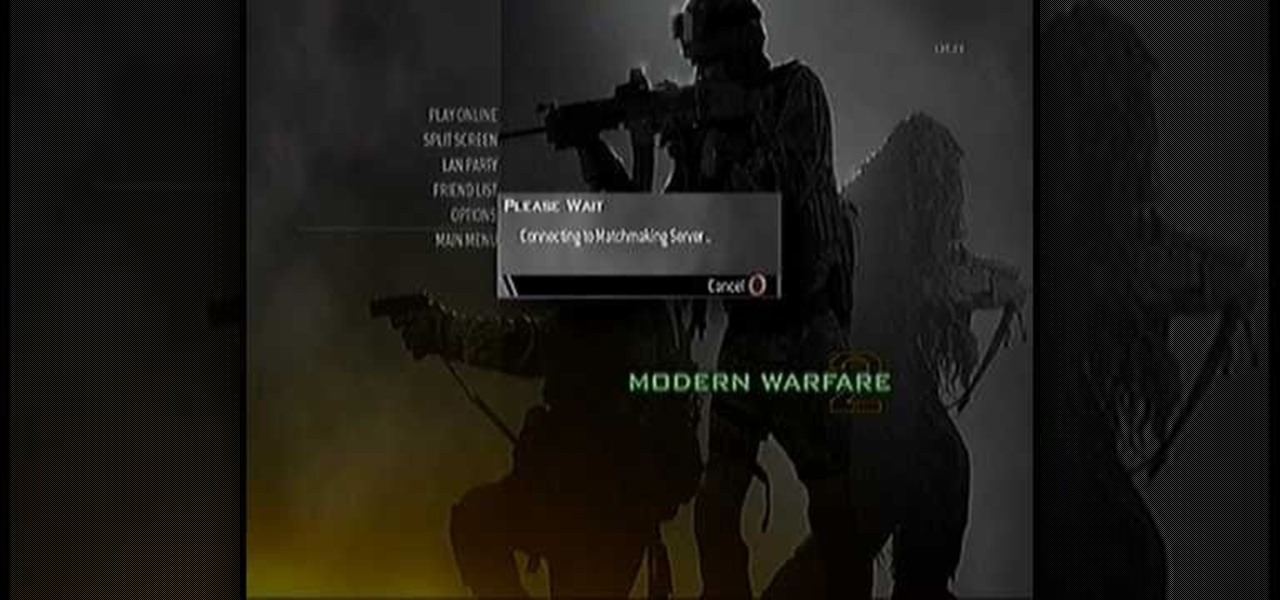
FROMAN1115 teaches you how to change your NAT type to Open on your PlayStation 3. On the PlayStation 3, go to Settings-Network Settings-Settings and Connection Status List and write down your IP. Go to your PC and start your internet browser. Type in 192.168.1.1. This will bring up the router settings page. Go to Applications and games and then DMZ. Check the first box that says Enabled. Enter your IP address below and click ok. Your settings have been saved and you can enter a new internet m...
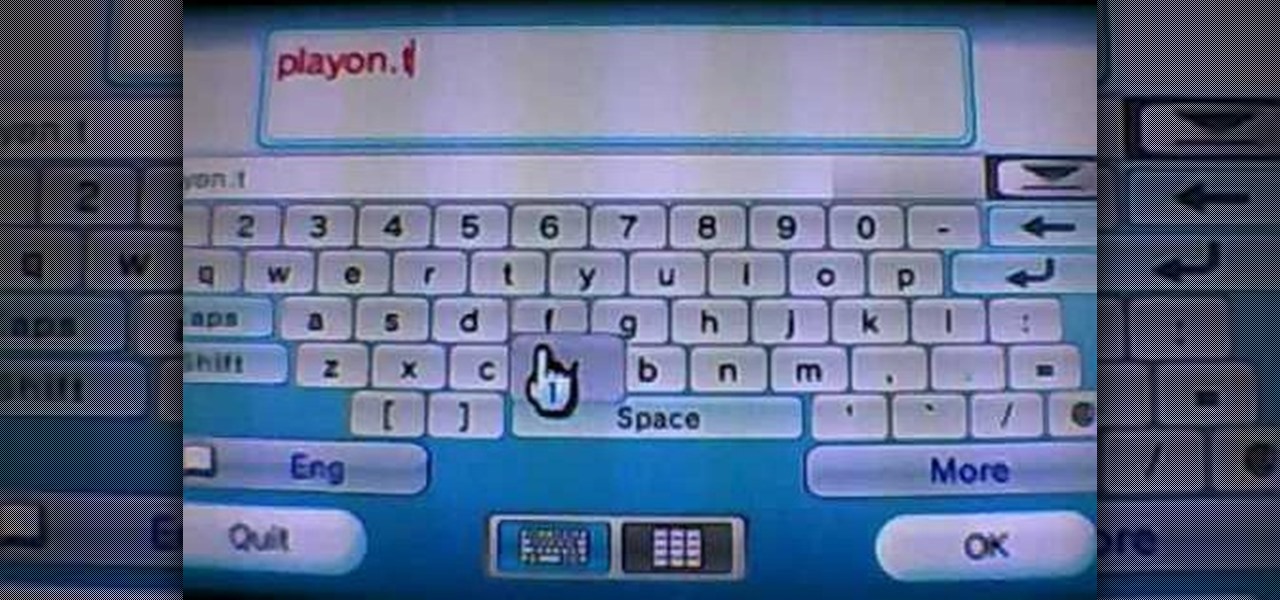
Evan shows viewers how you can use the PlayOn option on your Wii to watch videos on Netflix or Hulu. He starts off by showing how you can set up your wireless network and your connection settings. You will need to do this first if you have never done this before. To get PlayOn you will have to purchase it from the Wii Store using Wii Points. Evan also shows how you can link your internet channel to PlayOn so that you can view videos in just seconds. Watch all his tips and techniques and you c...

Leeann of Hierchiss explains how to turn a TV into an oscilloscope. Turn the TV on and make sure it works. First, unplug the power. Take the back off the television. Cut the four picture wires that attach to the circuit board. Strip the ends of the wires. Tape the remaining wires off to prevent short circuiting. Clamp the red and yellow wires and attach to a 1/4 inch jack which feeds into a tape player. Repeat the same process for the green and blue wires. Plug in the TV to make sure the conn...

This video will show you how to find your own IP address in Windows Vista, which is more difficult and confusing to use than Windows XP was. First, you should go down to the bottom right hand corner and find an icon of two computers, which is your network connection button. Click on the Networks and Sharing selection and find the section which says "View status". After clicking on this, you will find a section which will be labeled "IPv4". The numbers which are indicated after this are the nu...

Slow down? What!?! You've got to love the simplicity when it comes to long drive tips from long drive competitors. The long hitting Jamie Sadlowski shares his simple tip for more power, and it's not what you might think. See how to slow your golf swing down for more power.

This tutorial teaches you how to warm up your cello playing for an audition. By working the "pulling" muscles of your left hand you will create stronger more precise fingers, like "core training" for your hand. When you add these variations you will wake up and warm up your brain, open up new connections by challenging the coordination between your left and right hands. Watch this how to video and you will improve your cello playing with these warm up exercises.

Do you have the perfect timing? Timing your swing is important, but sometimes a clock can do a whole lot more to help your golf swing. By imagining the face of a clock, you can effectively train your body to calculate the proper swing length for shots from various distances. Sound intriguing? Let Doug Hammer, PGA, show you the way. Watch this video golf tutorial and learn how to clock wedge shots.

Samsung, like other OEMs, partners with third-party companies to include their apps on Galaxy devices. For example, Microsoft pays Samsung millions to pre-install certain Office apps. But one of these partners might not be on the up and up.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

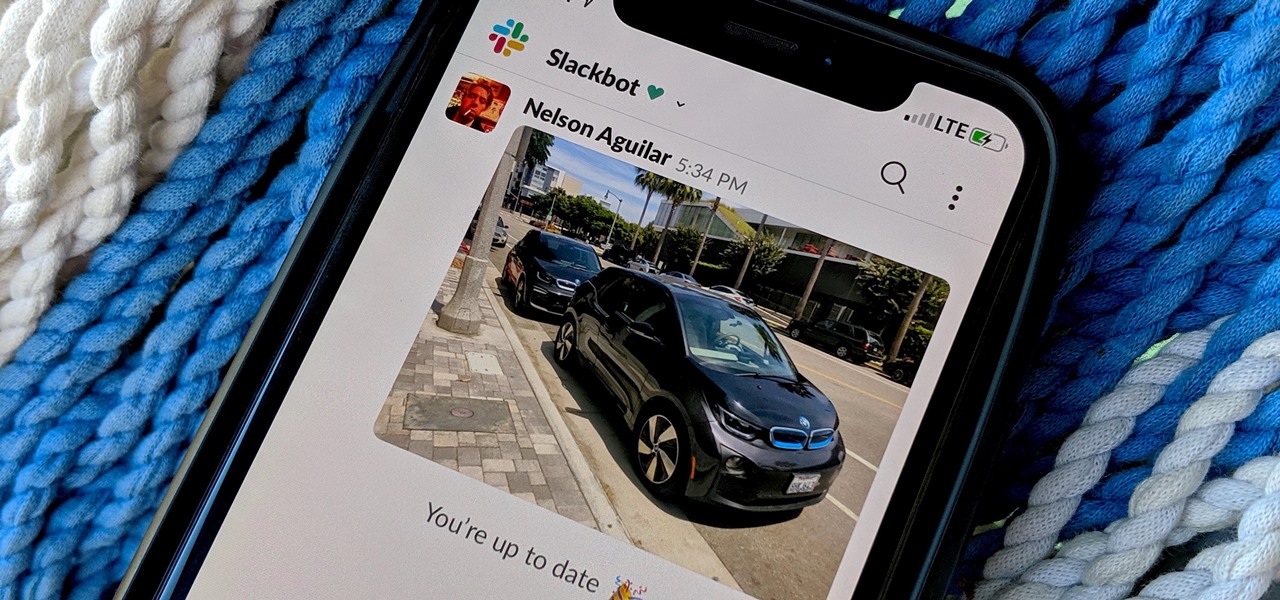
By default, Slack optimizes the images you upload and send to other users in your workspace. Although optimization lowers the resolution of the image, it does send quicker, which is better if your internet service is poor. However, you may want to send the highest-resolution image possible, so how do you stop Slack from sending only optimized and lower-quality photos?

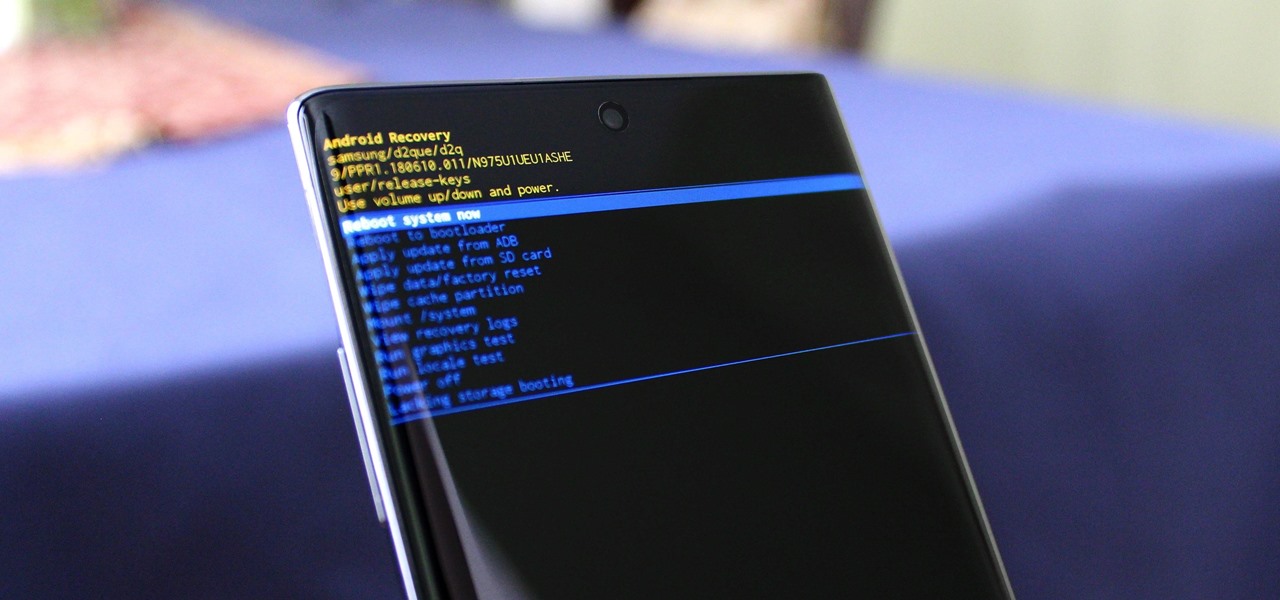
You can't call yourself an Android pro without knowing about Recovery or Download Mode. These menus are critical to do more advanced tasks on your phone, include sideloading software updates and un-bricking a device. But this year, Samsung changed the button combinations that will get you there.

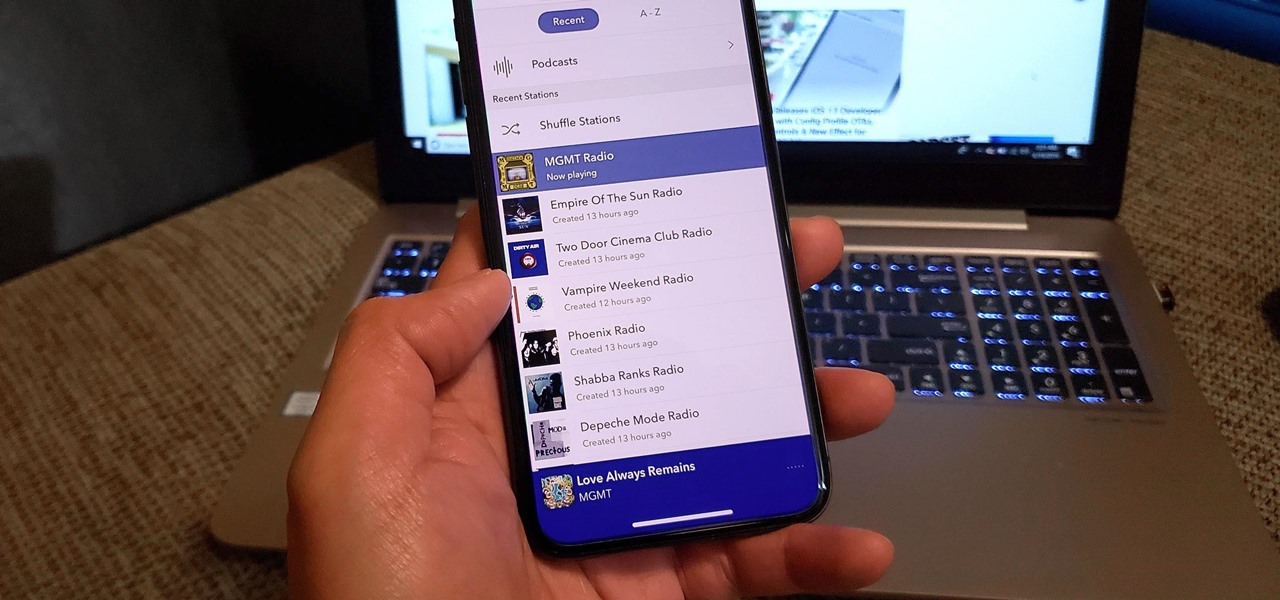
With such a vast selection of music genres available, it's easy to build up a massive list of stations in Pandora that can make your go-to playlists harder to find. Fortunately, the app lets you easily remove unwanted stations to streamline your experience and listen to your favorite tunes in the fewest taps possible.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

If you're looking into buying shoes from DSW on Black Friday, then you can save an extra 20% — but only if you smile more.

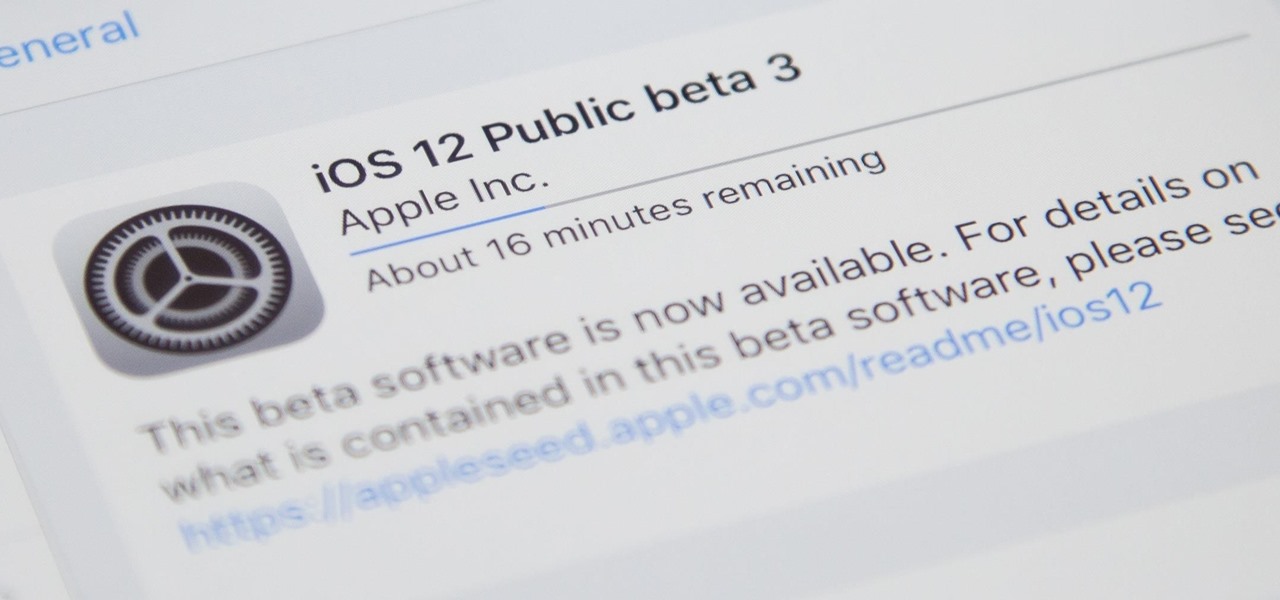
Last week, iOS 12 developer beta 7 was quickly pulled upon release, due to complaints of poor performance and instability issues. While Apple tackled these bugs with the release of developer beta 8 two days later, testers are seeing beta 7 again in their Software Update settings. Why is beta 7 back, and, more importantly, is it safe to download?

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

The updates just keep on coming. Apple released the third beta for iOS 12 to public testers Wednesday, July 18, just after seeding the fourth iOS 12 developer beta to registered developers the previous day. This update comes thirteen days after the release of the second public beta, which itself came hot on the heels of the third developer beta.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Apple CEO Tim Cook told us that augmented reality would change everything, and now we have a better idea of exactly what he meant.

It's not rare to see an advertisement in tech directly call out the competition. Whether it's the famous Mac vs. PC ads from back in the day or the Pixel burning the iPhone 7's lack of a headphone jack, rivalries in these commercials are certainly commonplace. Samsung's new ad campaign takes a more subtle approach to this "throwdown" advertising, but the message is still clear — Samsung wants you to know its AMOLED displays are better than Google's and LG's POLED.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Augmented reality developer Blippar has created a new visual positioning service based on computer vision that is two times more accurate than GPS in urban locales.

Netflix added the ability to download TV shows and movies on Android and iOS for offline binging back in Nov. 2016, and the process is the same as it is today. So if you anticipate having some downtime to catch up on Narcos or give Bright a try when you'll be away from a secure Wi-Fi connection, download videos onto your phone and save your data for more important things.

We're all passionate about something. Maybe it's the environment. Stopping poverty. Finding the best taco joint ... Whatever your cause, the last thing we want is to support companies whose practices go against what we believe. After all, you can't trust someone who doesn't like tacos. So it can be difficult to know which companies to avoid; there are just too many doing too many shady things to keep track of. Until ...

Stop me if you've heard this one before. You plop a marshmallow down in front of a kid and propose the following: You can eat this marshmallow now, or you can wait twenty minutes and eat two marshmallows. What do you think the kid is going to do? Better still, what do you think you would do? Personally, I'd eat the first marshmallow without hesitation. But now we're getting off track ...

Once upon a time, Flash games reigned as some of the best entertainment the internet had to offer. But then came the smartphone, which quickly overtook this genre with similar games that you could play no matter where you were. If you yearn for the good old days, though, you'll be happy to know that you can still use the Puffin browser to safely play old favorites and discover new gems.

When you think of high quality music, your phone isn't the first thing to pop into your mind, even though 68% of US smartphone owners stream music on a daily basis. Most of us tolerate the audio quality from our devices simply because music is something we can't live without — but we shouldn't have to put up with poor quality, and as it turns out, we don't.

Bluetooth 5 was announced and made officially available on December 7, 2016. It comes with a handful of improvements to speed, range, maximum device connectivity, and anti-interference from other nearby devices. While this might be great for those special few who use Bluetooth on a daily basis to send and receive (or steal) data, what about the average Joe?

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

Virtual reality and horror were meant for each other. You'll get all the positive aspects of experiencing a terrifying situation such as excitement and an adrenaline rush, without any of the real-life consequences, like being ripped to shreds by a herd of flesh-eating monsters.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

When attempting to gain access to a server, there may come a point when you need to get around file upload restrictions to upload something. If we can find a way to get around the restrictions, then we can upload anything we want to the server, effectively compromising it. That is what we'll be doing here today, so let's get started!

Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

Flashing people in an oversized trench coat is both old-fashioned and exhausting (and also very illegal). But like the evolution from school-yard bullying to cyber-bullying, it seems as if the new trend is "cyber-flashing" (it's even has an official hashtag). In the U.K., police are now investigating what they are calling the first cyber-flashing case.

The art of taking secret photos is one that requires keen awareness and skill. Not only do you need to ensure that your subject remains oblivious, but you also need to make sure that no one near you notices what you're attempting to do. It's great when you buddy is acting a fool, but sucks when they stop their shenanigans when they notice you pulling out your camera phone in an effort to evade your picture.