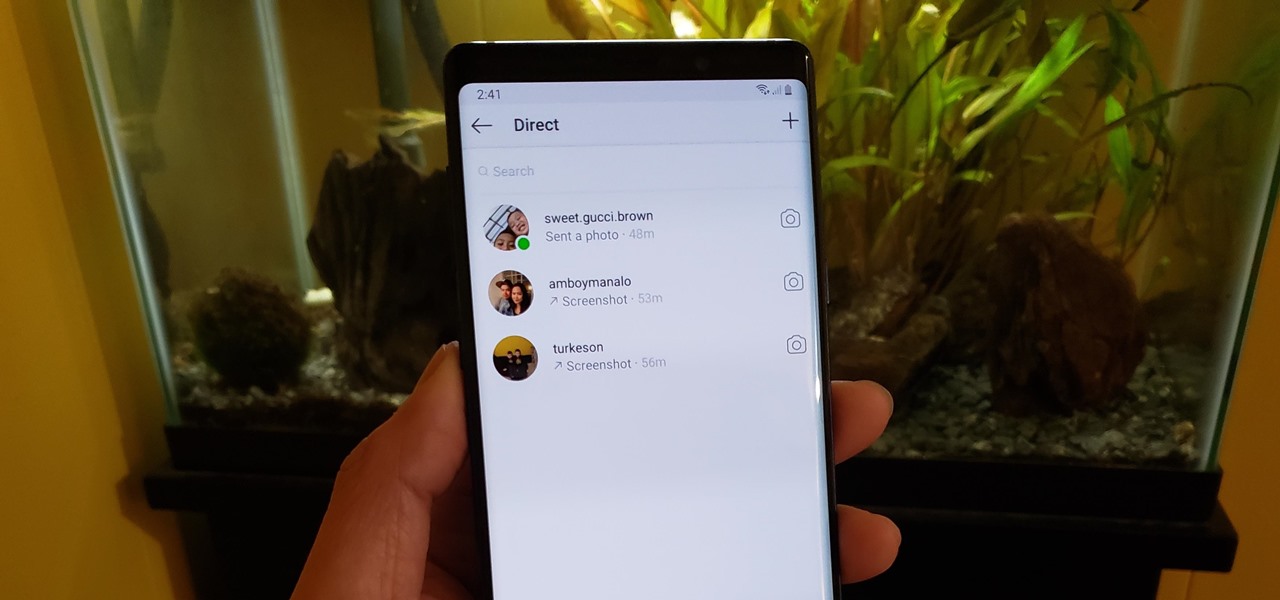
If imitation truly is the sincerest form of flattery, then Snapchat must be blushing profusely as Instagram continues to shamelessly copy its features and dig into its wallet. Instagram has also managed to copy some of the security aspects — or lack thereof — of one of Snapchat's hottest characteristics.

The HoloLens is the world's first untethered holographic head-mounted computer, which Microsoft has been rather proud of—and they have every reason to be. Of course, as soon as we developers get adjusted to the idea of keeping the scope of our projects inside the bounds of the HoloLens' processing power, Microsoft hits us with the Holographic Remoting Player.

You need a good microphone on your computer in order to make audio recordings, voice chat, or use speech recognition. However, not every computer comes with a built-in mic, and not every built-in mic works great.

Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my original script can download files, upload files, make changes to registry, create user accounts and more. I'm sure you could do it on your own too.

If you're just starting out with Android—or smartphones in general, for that matter—there are a lot of little things to learn. One of the first terms you'll likely encounter is "Wi-Fi," which is a wireless internet connection served up by a router in your home, office, or local coffee shop. This differs from your smartphone's regular "Mobile Data" connection, which is provided by your cellular carrier and included as part of your monthly bill.

When it comes to smartphones, the biggest complaint voiced by most users is battery life. Sure, it's unrealistic to expect your Android device to run for weeks without a recharge, but many folks struggle to even make it through the day without having to top off their battery.

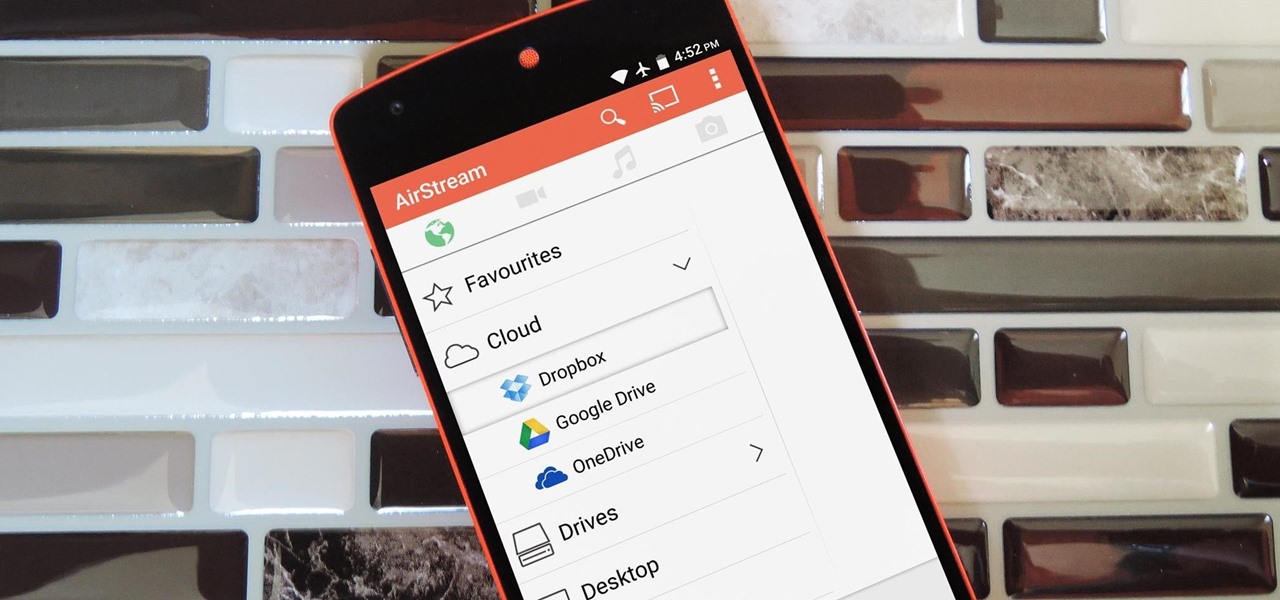
Smartphones generally have limited storage, but counter this issue with an always-on internet connection. This led to the proliferation of cloud storage services, which allow us to store and access our large media libraries remotely.

Rumors have had Google making a foray into the mobile carrier world for quite some time, but today, the Mountain View tech giant finally made things official. The new service, dubbed Project Fi, will be a Mobile Virtual Network Operator, or MVNO, that uses existing Sprint and T-Mobile cell towers.

Those of us with girlfriends understand that in order for the relationship to run smoothly, you have to keep your woman happy and let her know that you're thinking of her—even when you're not.

Dating can sometimes be a cruel and embarrassing game. You could be having a great time with someone, only for the situation to turn awkward and uncomfortable when a little bit of information is released, especially when that information is your use of medicinal or recreational marijuana.

Using shortcuts to control the playback of your music on your computer makes life just a little bit easier. Instead of needing to open up an app, we've shown you how to use keyboard shortcuts, a Notification Center widget, and even Siri to control music on your Mac. Now we're going to show you how to use your iPad, iPhone, or iPod touch as a remote control.

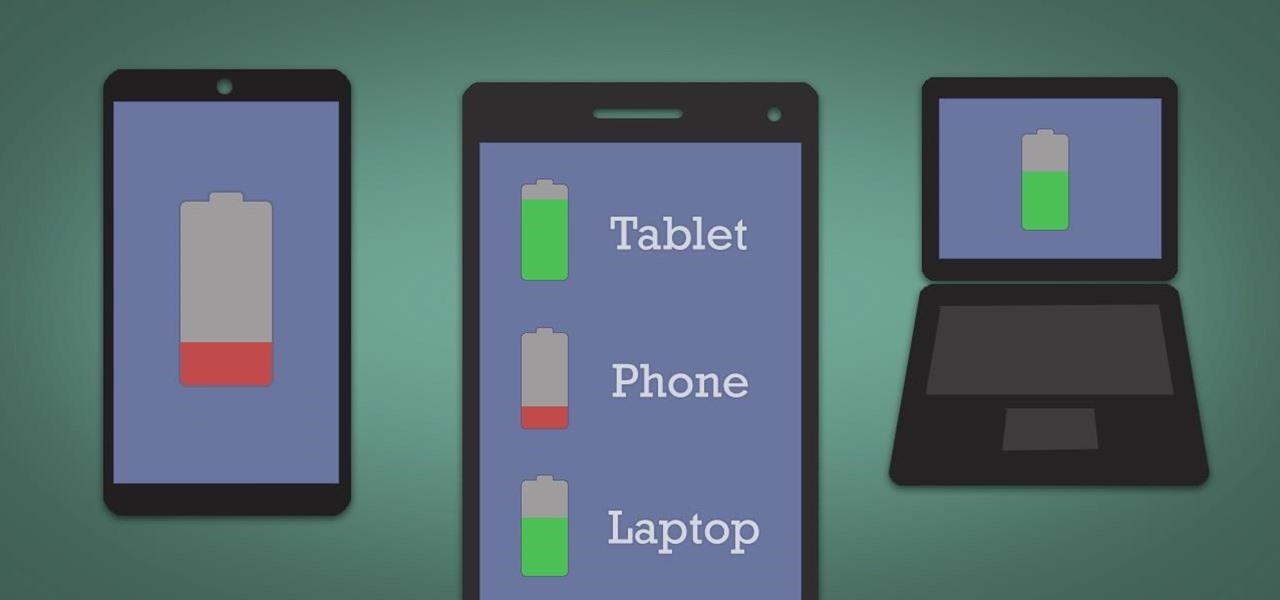
It's hard enough to keep tabs on the battery life of one device, let alone all of the different gadgets that a typical consumer owns in this day and age. Say your smartphone is running low on juice, so you switch to your tablet only to find out that it's almost dead as well. Better hope your laptop is fully charged, right?

Ever use an open hotspot on your Note 3, only to find out that it's severely restricted to what sites you can access? While getting online with free Wi-Fi is great for those who have a limited data plan, when that one site you absolutely need to visit is blocked, you're left frustrated and sent back into the Wi-Fi menu for another access point.

If you're breaking a sweat in the summer heat, but not trying to break the bank, this dead simple trick will show you how to make your own air conditioner for under ten bucks.

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

Apple and Google are not only two of the biggest names in the tech world, but also two of the biggest competitors. So, it's no surprise that you can't watch movies or TV shows purchased from iTunes on an Android device. Likewise, you can't watch any videos purchased on Google Play with your iPad or iPhone—until now.

As of this week, Gmail is going to start letting Google+ users email each other using a new option called "Email via Google+." There's nothing wrong with making it easier to get in touch with people you want to hear from, but the default setting allows anyone with a Google+ account to send a message to your Gmail inbox. After the feature is in use, Gmail will start to suggest Google+ connections along with your other contacts as recipients. Email addresses will not be displayed for Google+ co...

Welcome back My sleepless army of young hackers, Everyone uses internet, right? So for this tutorial, i'll start with the basics and slowly we'll get to the UPD Protocol.

For the most part, transferring files from your computer to your Nexus 7 (and vice versa) is a simple process. Just hook up your tablet to your computer with the USB cable and transfer. However, most of the time you'll need additional software on your computer to do this, and then, of course, you need the USB cable.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Even if you have the fastest internet connection in the world, it's not going to be fast if your Android device isn't optimized to use all of the bandwidth. I have pretty fast speeds at home, but every now and then my web surfing on my Nexus 7 tablet is halted in its tracks—for seemingly no reason.

The first thing I do when I get a new phone is ditch the USB cable. At least, when it comes to data transfer. My brand new HTC One came with a USB cord that feels sturdy, but like any other cable, it will eventually fall apart from overuse. It will probably still charge just fine, but at that point it will be unreliable for transferring data. Lucky for me, there's a solution. Transfer files over the air. This will let you save that USB cord only for charging and the occasional situation when ...

Cars are quite different than they used to be. Sure, modern cars have some cool things, but repairing them are becoming difficult. Even simple things like changing a headlight bulb.

Back in 2007, YouTube user HouseholdHacker posted a parody video on how to make a high-def speaker for under a buck. MythBusters took on the challenge and busted it.

Sprint has announced that it will be the first U.S. carrier to release Jelly Bean 4.1 for the Samsung Galaxy S III. The over-the-air updates have already started, with users receiving a notification on how to update on their phone. The reason Jelly Bean has garnered so much attention is due to several, well-known features like Google Talk, Project Butter and expandable notifications.

The reason that Facebook is so popular is because it connects us to people that we could have never been connected to before. When people log on, they look for messages, comments, likes, and any other notifications that connect us to those people. These same notifications, though, distort our view of Facebook. We tend to appreciate statuses (I prefer stati) that have more likes. We're geared towards people that have more friends, so we tend to like pages that already have hundred of thousands...

Lightning has struck, but not everyone is excited. Apple's new 8-pin Lightning connector for the iPhone 5 has replaced the aging 30-pin connector. Many users have concerns that their current third-party devices will no longer operate properly with the smaller all-digital design, not to mention the expensive price tag for each adapter. What Does This Mean for the User?

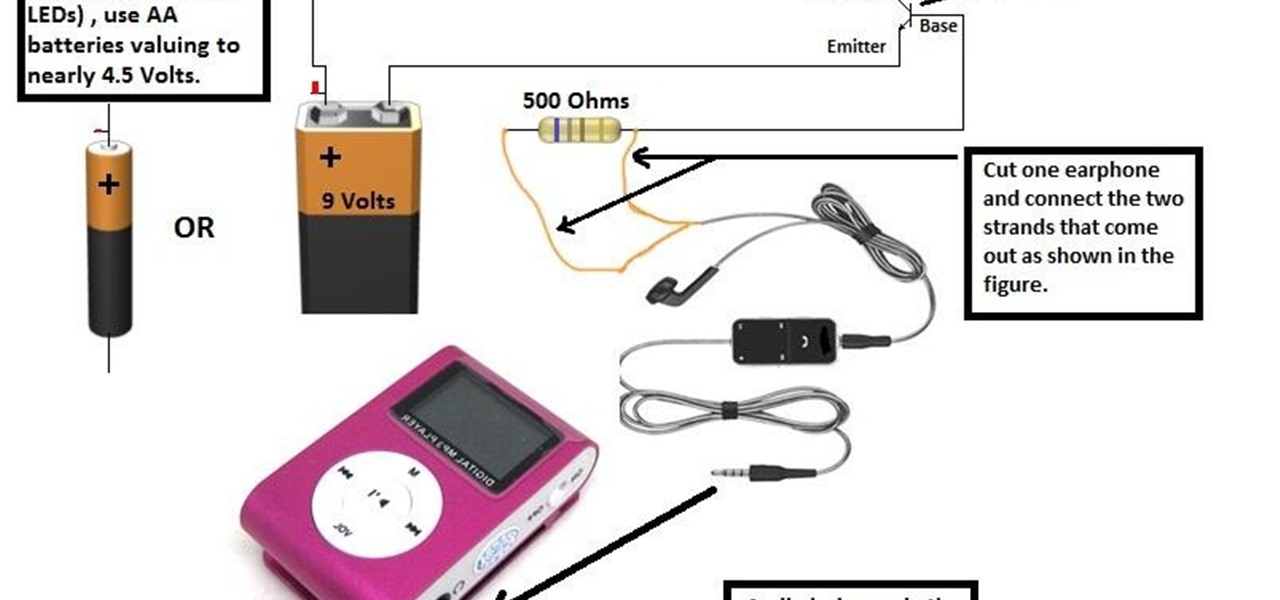
You must have seen some expensive mp3 players and CD players which have LEDs fixed on them and they dance to the tune looking really pretty.

Wish your home wireless network was faster? You can always buy a signal booster, but if you'd rather not spend the money, here are a few tips and tricks to speed up your wireless connection, including how to make a homemade signal booster with things you probably already have lying around.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

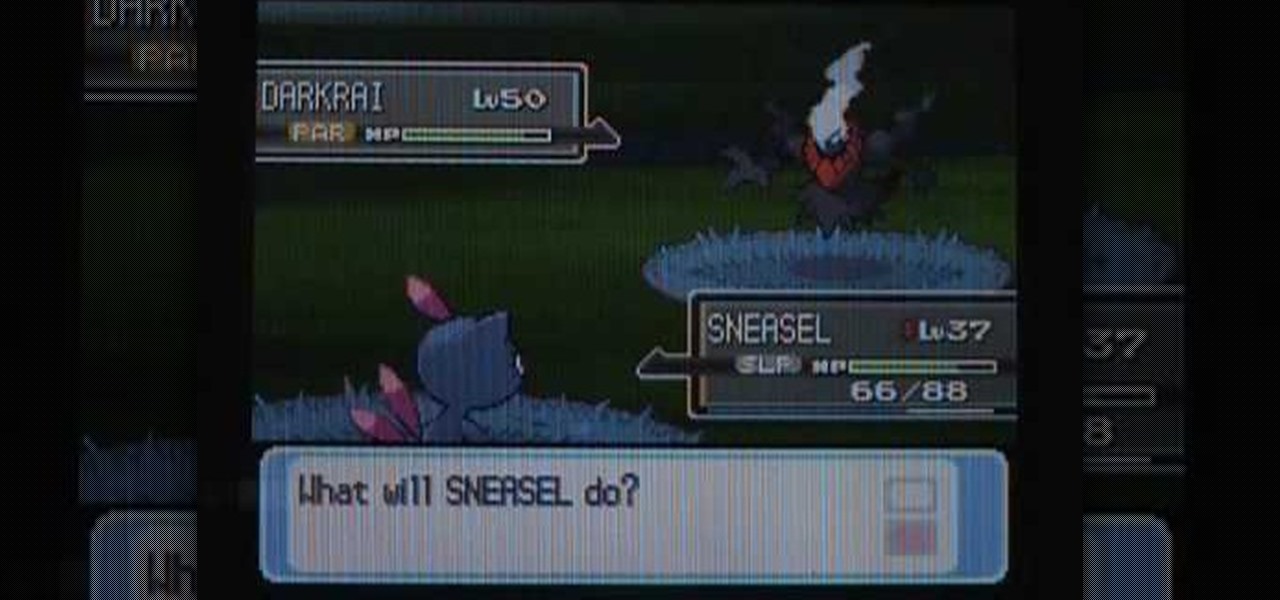
Pokemon's Darkrai is one of the most coveted levels of the game. With this tutorial, learn how to find Darkrai in a few easy steps, as well as secure a Membership Pass and a Mystery Gift in Pokemon Platinum. So grab your Nintendo DS and follow along!

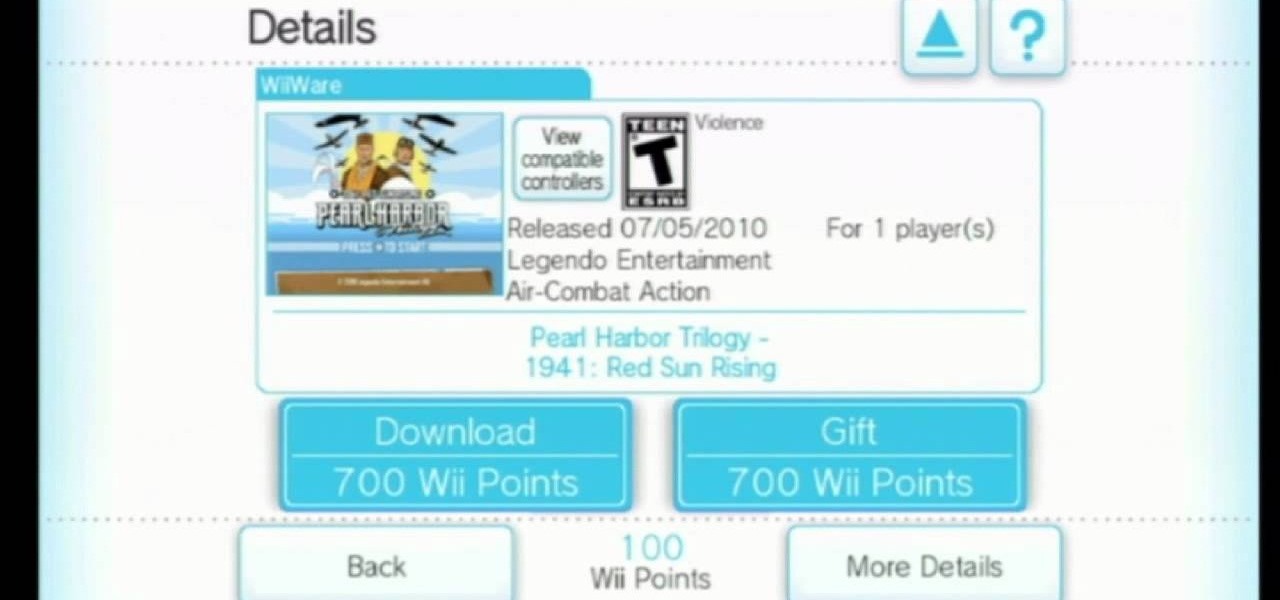
This video tutorial will teach you how to use the Nintendo Wii Shop Channel to download and play your favorite console games on your Nintendo Wii. To follow along, you'll need either a WiFi Internet connection or Wii Lan adapter.

Software manufacterers always advise you to read the instruction manual first before attempting to do anything on a new program. But who has the time to obsess over ever little boring detail in a 300-page tome when just playing around the controls on your own gets you attuned to the program immediately?

Solo camping is a scary and exciting prospect. Alone in the woods at night, no one can hear you scream. But for those who crave solitude and love the wilderness, there can be no greater thrill, no greater connection to the primitive part of yourself. In this nine-part video, we learn all kinds of useful survival and camping skills by watching our host Colhane experience a three-day solo camping trip in the Brazlilian bush. You will learn how to cook, how to make fire, how to prepare a campsit...

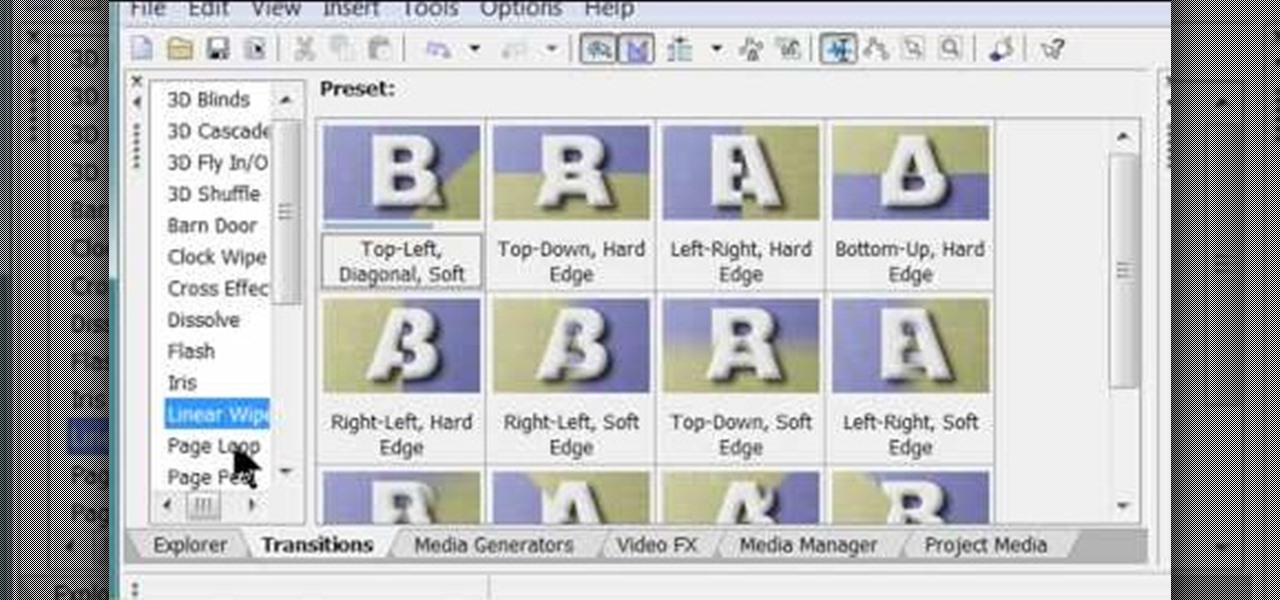
Chris Davis with the Educational Technology Center shows us a few easy steps to putting YouTube videos in our Microsoft PowerPoint 2007 presentations. To start you'll need to have an active internet connection and you should have the developer tab in PowerPoint active. To do this go to the Office menu, PowerPoint options, popular and click show developer tab. Locate the hammer looking more control option button and scroll down to Shockwave Flash Object and click it. This allows you to draw a ...

Peggy Erbison shares her knowledge of palmistry in this video. The heart line starts under the pinky and moves across and up towards the middle and index finger. The next line she talks about is the head line. This line is the center line that explains how your thinking is. The line that rounds out and wraps around the base of the thumb is the life line. This line connects to the head line at the beginning. These are the 3 main lines on the palm. Contrary to popular belief, the life line does...

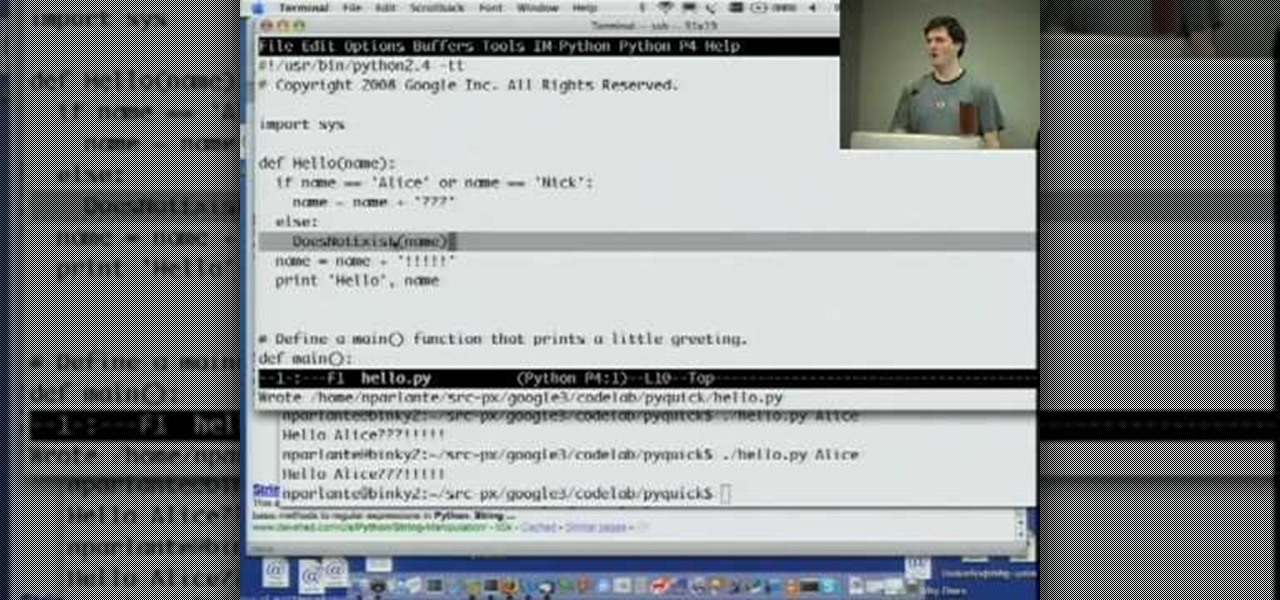
Welcome to Google's Python Class – a seven-segment, two-part free virtual class for people with a little bit of programming experience who want to learn Python. The class includes written materials, lecture videos, and lots of code exercises to practice Python coding. The first exercises work on basic Python concepts like strings and lists, building up to the later exercises which are full programs dealing with text files, processes, and http connections. The class is geared for people who ha...

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install cool themes on Ubuntu Linux.

XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection between the attacker and the victim open to allow the attacker to continuously manipulate the victim's browser. XSS Shell works by setting up an XSS Channel, an AJAX application embedded into the victim's browser, that can ob...

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.