This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!

If history holds true, we'll see the iPhone 7 arrive this September, and just like many times before, there are already a ton of rumors about its features. As usual, many claims are pure speculation, but there are some trustworthy reports and lots of good information we can use to make some educated guesses regarding Apple's upcoming flagship.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

If you're ever lost or hurt out in the middle of nowhere with a dead cell phone, you might be able to "flag" down help as long as you're near some railroad tracks.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Chicken breasts have gotten a bad rap. Dry, flavorless, boring... poor white meat gets no love, and dark meat gets all of the credit for being sinfully flavorful and delicious. But the truth is, even though chicken breasts are lower in fat and calories, they can also be incredibly versatile and full of flavor... if they're prepared correctly. You're probably familiar with poaching, which is a technique that gently cooks more delicate meats such as chicken or fish fully submerged in a liquid b...

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

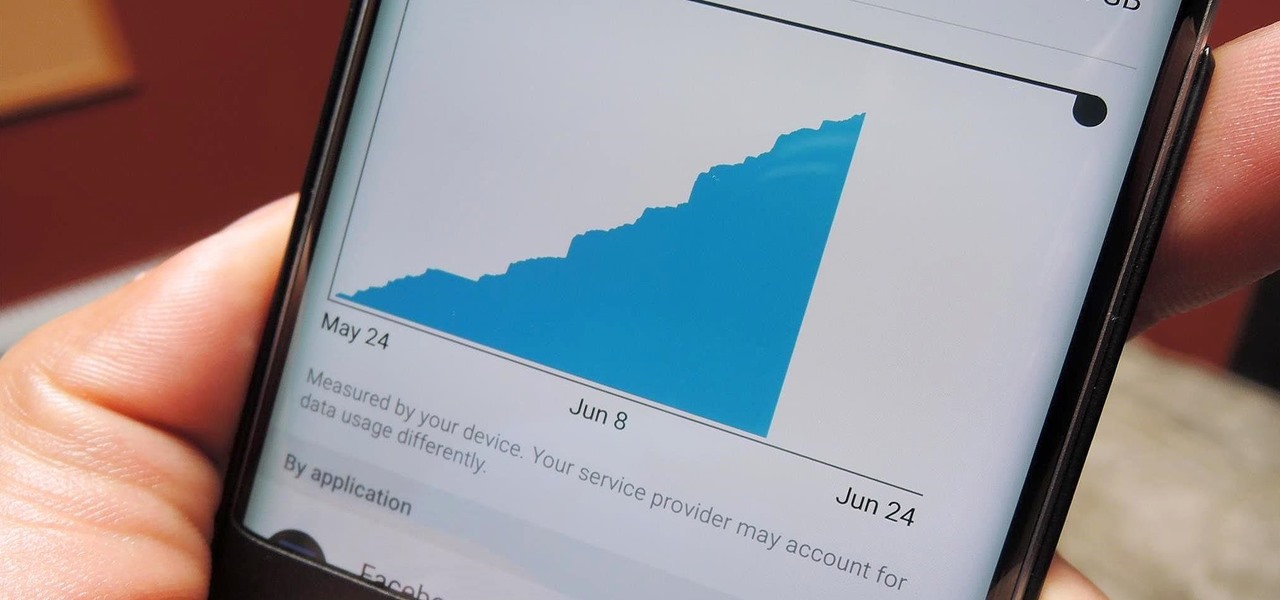
In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.

When you finally turn the privileged age of 21 in the U.S. (or 18 in most other countries), the first thing you'll probably do is sprint to the nearest pub, order a drink, and revel in your new freedom. Congratulations, you've survived two decades on Earth, you've earned that drink.

Let's say you got a little careless while installing apps from unknown sources, and now your Android device has been infected by malware. Or perhaps your friend has come to you for help after they had haphazardly installed random apps until their phone was filled with popups and garbage like that.

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

The peanut butter and jelly sandwich has officially left the building. When you eat this every other day in elementary school, you've sort of reached your limit. The thing is, peanut butter itself is delicious and quite versatile if used in the right way. Let's explore this kitchen cabinet staple and showcase it via the three dinner courses.

With all the stress that goes into booking flights and lodging, packing (and not forgetting) everything you'll need, finding pet sitters, and everything else that goes with a trip overseas, there's the added stress of staying connected while abroad.

Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

Poor chickens. Bacon fat is revered (and justifiably so), and duck fat is a staple at most fine grocers. Marbles of fat make a steak divine, and goose fat is the holy grail of fatty goodness. Yet chicken fat is usually thrown away.

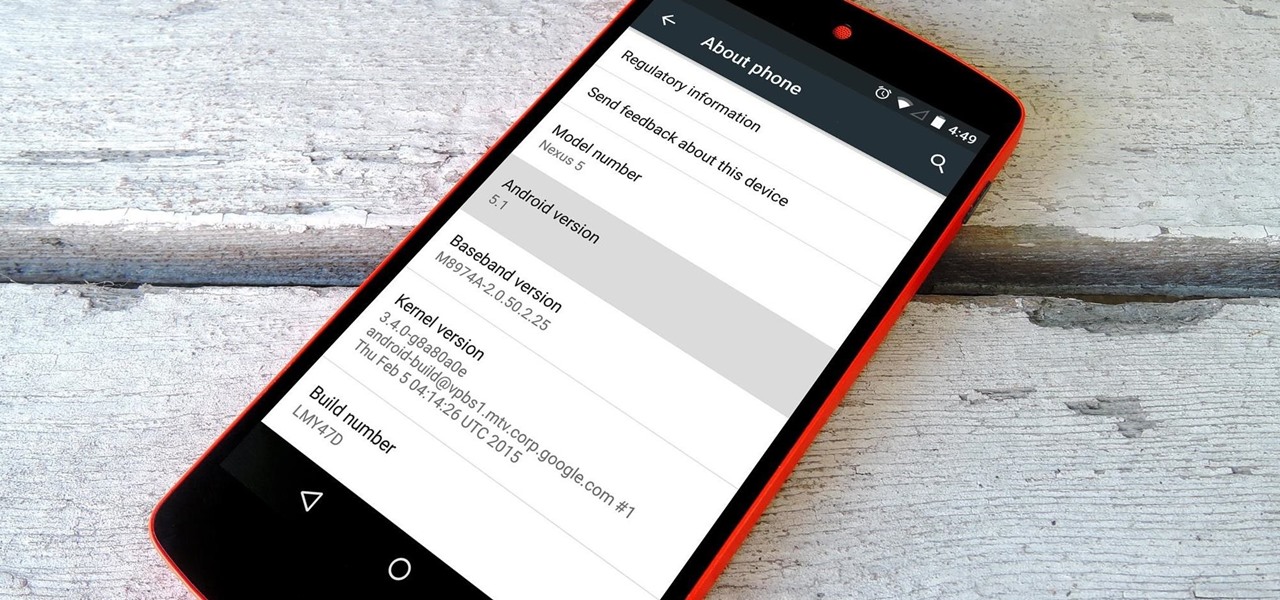
Google inconspicuously announced an Android update yesterday, and while it's not quite the overhaul that the initial Lollipop release was, version 5.1 brings plenty of bug fixes and new features.

Hello my fellow hackers, Welcome to my republished revision of the ruby programming language, Part 1.

Can't stand seeing your Facebook news feed full of peoples' good news and awesome accomplishments? Those oversharing friends are, in a sense, hampering their great news simply by sharing it. If you hold back and keep your accomplishments from friends, you might find even more success than if you'd shared with your support network.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Due to their large size and added screen real estate, Apple included a new feature for the iPhone 6 and 6 Plus known as "Reachability." Essentially, this function makes reaching the top part of the display easier by double-tapping the home key to shift the screen down closer to your thumb.

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

Creating a haunted house for Halloween was a big deal when I was growing up, and the neighborhood kids were always coming up with ways to try and out-do each other when it came to this frightful night. One beloved game was to blindfold the participants and play the Withered Corpse.

If you are having problems playing your sweep picking arpeggios fast and clean then you are not alone. Many guitarists have the same problem. I suffered from the same problem, years ago. In fact, playing sweep picking arpeggios with poor technique is one of the most common problems that I encounter with my guitar students. After helping them overcome these challenges I have discovered 2 different approaches to improving your sweep picking technique. The first will keep you frustrated with bad...

With AirPlay for iOS, Chromecast Screen Mirroring, and even third-party PC-pairing apps to play around with, getting your devices to interconnect could not be any easier than it is today.

Airports are terrible germ-infested purgatories where people sit around for hours without Wi-Fi while they anxiously await to get wherever they really want to go. Unfortunately, there isn't much we can do about waiting, but this little Wi-Fi hack could help make the waiting a little less boring.

Known for its easily recognizable filters—and coining the hashtag #nofilter—Instagram has long been an app that focused more on photo posting rather than photo editing. Yet today, Instagram released an upgrade for both Android and iOS users that edges the app towards becoming a full-fledged photo editor.

Most days, getting through an eight-hour work shift is a struggle. There are a million places you'd rather be, and none of them include your desk. It's difficult to find the motivation to tackle the growing number of emails in your inbox when your mind is back at home, comfortable in front of your gaming system.

One of the down-sides of international long-haul travel is layovers between flights in unfamiliar places. We have a flight to Europe this year via Guangzhou, China, and I've been putting together my notes on how to make the best use of 7 hours between flights, which I'd like to share.

As the Chromecast becomes more and more popular (it's even available overseas now), the market has seen an avalanche of Chromecast-compatible apps. We can play games, cast TV stations, and even mirror our screens, but today I'm going to show you a multifaceted tool that'll do everything from broadcasting your camera to displaying your documents.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Last week, we covered a new, open-source live wallpaper (LWP) called Muzei, and less than a week later we have no less than twenty beautiful add-on extensions to the app.

No matter how cool my 3D live wallpaper is, or how often my Google Now wallpapers automatically change, I always want more backgrounds. Zedge has made it easy for me to find new ones, and 500 Firepaper helps me keep my background lively with rotating wallpapers—but these aren't enough.

Finally, the much-hyped Xbox One is out, setting the stage for an epic holiday showdown between Microsoft and Sony. While the PS4 was released a full week before the Xbox One, Microsoft's next generation system is fully equipped with the latest games and acts as an all-out media hub.

So, you've got a brand new PlayStation 4, but unfortunately, you've got "No Signal" now, too. You can't really game or watch movies on your new toy if you can't even bring up the PlayStation menu on your TV screen.

It's sad to say, but the chances of a new system launching without any hitches or glitches is just not realistic. If you're one of the lucky few that has gotten their hands on the new PlayStation 4, or if you are waiting in line right now to get one, the first thing you're going to want to do before gaming is update your software to the newest version. This update isn't required, as most single-player games can be played without an Internet connection and without signing into the PlayStation ...

You don't have to be in debt to receive annoying calls from unwanted numbers. You may love your grandma, but if she calls you three times a day to ask how to turn on the television, you might just want to push all of her calls to voicemail.

The NSA's massive internet spying efforts will continue. In President Obama's latest press conference, he went public to (in so many words) say that the NSA's spying efforts will continue uninterrupted. This, coming just weeks after the Amash Amendment which would have defunded the program, was narrowly defeated in the House (you can check if your congressmen voted against it here).

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

I remember how fast my Nexus 7 was the first time I turned it on. Boy, do I miss it. Now my tablet is pretty buggy and crashes happen frequently, and I'm sure that goes for many of your Nexus 7s as well. Even if you upgrade to the new Nexus 7 next week, it will eventually develop similar issues.