Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

International, T-Mobile, and Verizon customers all share something in common—their carriers provide unlocked Wi-Fi tethering for free. Of course, you still pay for the data used, but they don't charge you extra simply for using your Samsung Galaxy S4 as a wireless hotspot.
A single movie download can consume a good ten percent of the storage on your Nexus 7 tablet, unless you went all crazy and opted for the 32GB model. Even then you're bound to run out of space fast, especially if you're like me and have tons of media files you want readily accessible on your tablet.

Not having internet sucks! We do a ton online these days, from working, shopping, studying, and collaborating, to watching fail videos and endlessly clicking through memes.
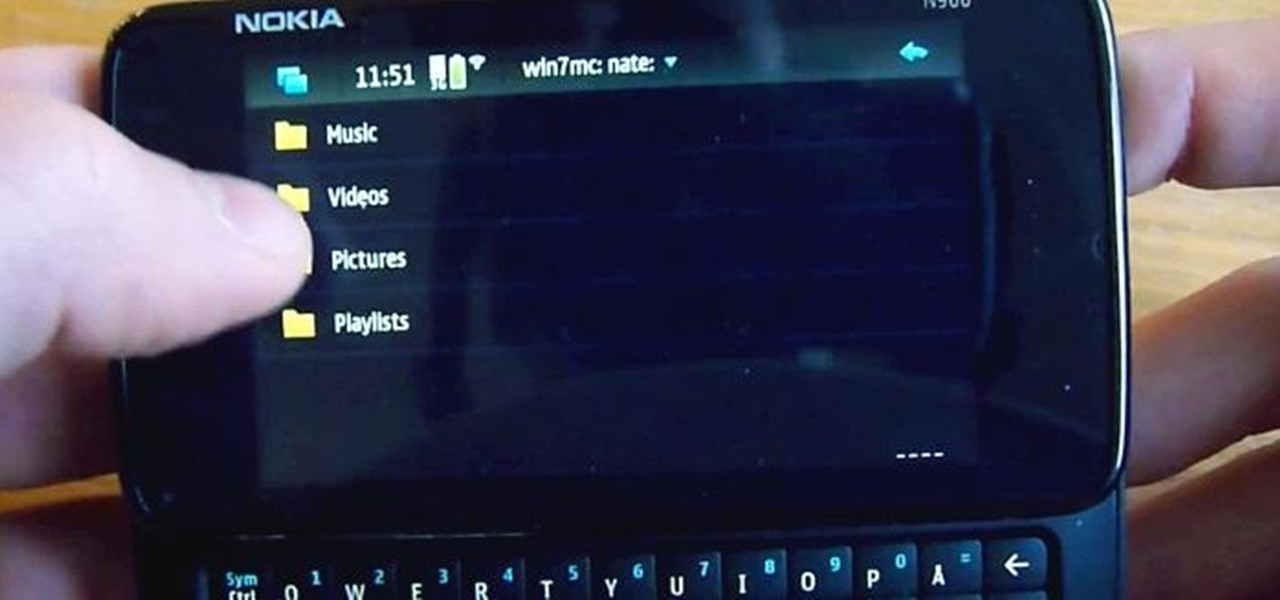
Having access to your computer from your cell phone is an extremely useful feature. Whether you need to edit documents or send files that are on your home desktop, or you simply want to watch movies you have saved on your computer, access is key.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

First off, I would like to say two things. One, this is not for beginners; if you don't feel that you understand this how-to at all, do not try it. Second, never ever install random software or change settings if you do not trust the source.

The cost of movie tickets in North America are currently at an all-time high, but with so many great films coming out, just not going doesn't seem like a probable option. Luckily, there's more than a few resources on the Internet to help you mitigate some of those costs.

This video shows in poor quality how to play Chicken S**t Bingo at Ginny's Little Longhorn Saloon in Austin Texas.

In this video tutorial, viewers will learn how to sweat pipes. The materials required for sauntering the sweat pipes are: M-APP gas, gauge, solder, solder paste, pipe cutter, brillow and copper pipes. Begin by cutting the copper pipe to a desired size. Then brush some plumber flux onto the copper pipe and hold it in place with a clamp. Now use the M-APP gas to move the flame around the pipe to allow it to suck in the solder. This video will benefit those viewers who are interested in plumbing...

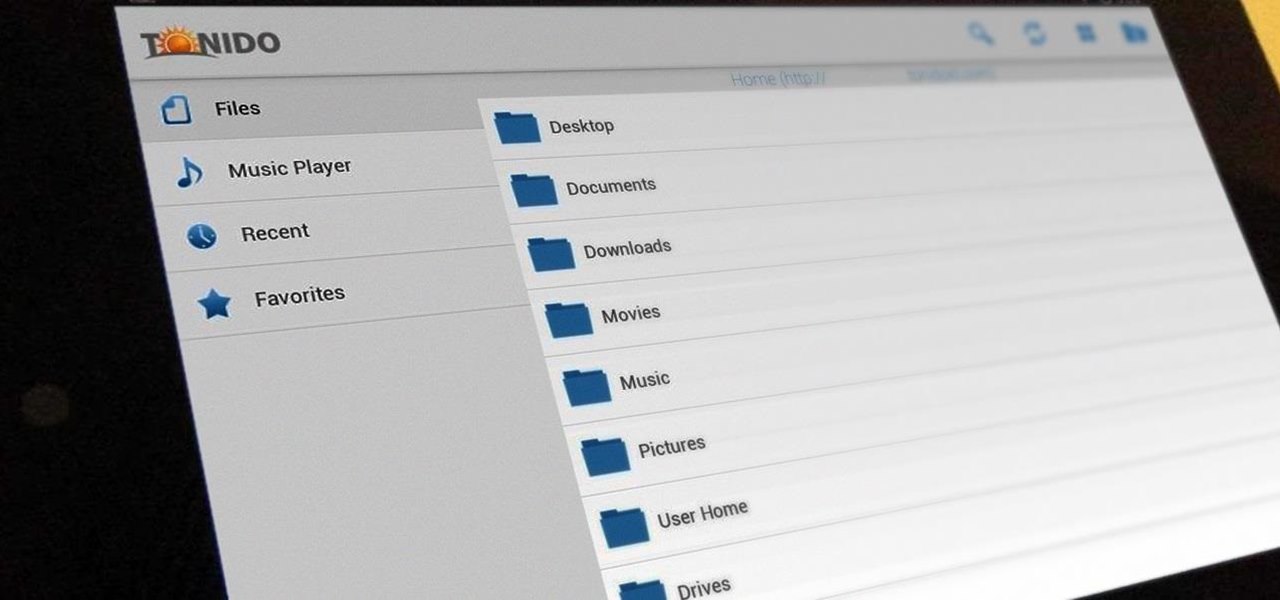
Wouldn't it be great if we could all enjoy the music, photos and movies on our home computers even when we're not home? Some would think it a luxurious feature, but it's totally possible for anyone who has Windows 7 and an internet connection. See how!

Not enough space on your laptop? No problem! Grab a new hard drive from your local office supply store and follow this tutorial to learn how to install it.

There are different theories on if you should clean your grill or not but if you’re on the side that likes to keep your grill clean then Danny Lipford will show you exactly how it should be done. These grills can get pretty dirty .

This video tutorial will show you how to setup your YouTube account in order to enable you to play videos automatically in high quality when available. It only takes a few seconds to setup. It is a very simple process that takes us through the settings and options to enable your default viewing of videos.

Excited about experiencing blazing-fast 5G speeds on your iPhone 12, 12 mini, 12 Pro, or 12 Pro Max? Well, that brand new iPhone you just bought might not actually be using 5G, even when you see that 5G symbol in the top right. Unless you follow these instructions, your iPhone will use regular old 4G LTE more often.

Updating your Galaxy to the latest software version is optional, but you wouldn't know that from the persistent notification and status bar icon that are constantly reminding you to. Thankfully, you're just an app away from hiding these eyesores without the need to update your phone.

The overarching and expanding field of data science and analysis has become virtually inseparable from areas such as programming and development.

Despite Samsung's long running support for Wi-Fi Direct, most users still struggle to transfer files between their devices. Whereas Apple has AirDrop, Samsung's previous solution wasn't so obvious. With the Galaxy S20 and Galaxy Z Flip, Samsung hopes to correct this with "Quick Share," a file transfer system that still uses Wi-Fi Direct but makes it easier to use.

There is so much information in the world that trying to make sense of it all can be daunting. That's where data analytics comes in. By learning how to inspect and model data, you can take large data sets and transform them into highly valuable information that can take any business further.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

Whether you loved or hated the blockbuster hit Joker for its slapdash violence and unflattering portrayal of mental illness, if you have been online lately, you know you can't afford to miss it.

Your phone is loaded with contacts you've collected over the years. They're an asset, and you should use your library of connections outside the confines of your mobile device. Luckily, your Pixel uses a standardized medium to store contacts that can be used by the likes of LinkedIn, Outlook, Hubspot, iCloud, and more.

While the portability of mobile phones makes gaming convenient, it isn't a perfect playing experience. With touch controls, small screens, and limited specs, smartphones lack the comfortability of dedicated gaming devices. But with a few tips, you can enjoy games as if you were playing on the Nintendo Switch.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

Let me paint a picture for you. You're on a long flight home, and while listening to music on your Samsung Galaxy S10, a great song comes on. You want your friend to hear it too, who's also listening to music using a pair of Bluetooth headphones. Thanks to Dual Audio, you can easily share your experience.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.

There are more than a few subscription-based movie streaming apps available for Android and iPhone, each with different benefits and varying pricing plans. Needless to say, it can get expensive fast if you sign up for multiple services because you can't decide on what's best. Hopefully, we can help you out with choosing the right video-on-demand app to spend your hard-earned dollars on.

Applicants looking to attend Magic Leap's first annual L.E.A.P. conference next month in Los Angeles have begun receiving their confirmation invitations, and now we have more detail about some of what will happen at the event.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Looking to inject a little more processing juice into your HoloLens? Unity can fix you up with the Standalone Universal Windows Platform Holographic Emulation.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

Waze is the go-to navigation app for millions of drivers, and it's easy to see why. Benefits such crowd-sourced traffic data, police trap locations, and road work avoidance are just the tip of the iceberg. It can almost be overwhelming, but with these simple tips, you'll master Waze and start navigating like an expert in no time.

Lost among the latest laptops, smart assistants, VR headsets, and Motorola-branded gadgets that it brought to CES 2018, Lenovo has also introduced a new pair of augmented reality smartglasses.

If you or someone you know has younger kids and you're looking for an augmented reality toy, Pai Technology has just the educational option for you.

There may be many third-party file managers for Android to choose from, but until now, Google offered no proprietary option. Enter 'Files Go,' which, while initially anticipated for December, is now available for you to try.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

If we're being honest, very few people go on Tinder to fall in love with someone's personality. Oftentimes, the only reason they'll look at your bio is to make sure there are no red flags.