Remember those Choose Your Own Adventure novels? If your school was anything like mine, they were so popular you were lucky to find one to check out at the library. But there's no worries now, thanks to this handy HTML5 app, which makes it easy to write and share your own 'choose your own adventure' novels. inklewriter is a free tool designed to make writing interactive stories simple. Basically, you start typing and inklewriter helps you organize your story, making it easy to add, remove and...
Video: . » Iran Threatens to Block Tankers in Response to Oil Import Embargo Alex Jones' Infowars: There's a war on for your mind!.

Was Napoleon's death really due to stomach cancer, or was it arsenic poisoning? Some scientist believe the latter. Arsenic poisoning was a deadly weapon in that era, because it was undetectable when administered over a long period of time, making murder seem like natural causes. But if arsenic (As) is poisonous to most multicellular life, then what's with the newest NASA discovery?

Absinthe and caviar have extremely strong, distinctive flavors that many folks can't handle easily on their own, but adrenaline rush connoisseurs will get a kick out of the recipe presented in this video. Combining absinthe with caviar, you'll make a distinctive tasting caviar.
Want to earn coins and easy experience for your Pet Society pet without, you know, actually having to play the game? It's easy. This video guide show you everything you'll need to know to generate unlimited experience and digital cash money.

Fish & chips is the most popular fish meal in the country, & you can make it yourself instead of paying a fortune at your local fish eatery. The special ingredient for these fish and chips… beer.

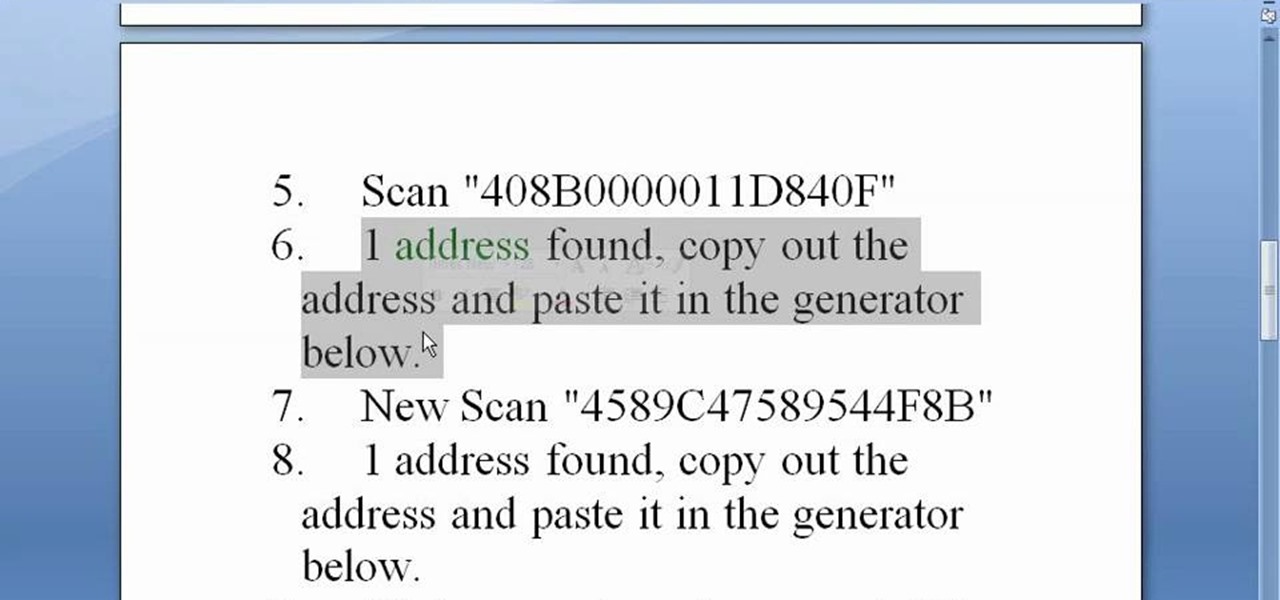
This is a jumprope hack for Pet Society. It's called the Auto Jump + Coin hack, and involves your jumprope, Cheat Engine, and a little code generator.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Have you ever heard of cricket? No, we're not talking Jiminy Cricket or the wireless cell phone service provider. We're talking about CRICKET. The team sport, nicknamed "the gentleman's game," is the popular sport of choice in places like India, Australia, South Africa, Sri Lanka, England, Pakistan and Zimbabwe, though not America. But guess what? It's very similar to the American pastime we all love so much— baseball.

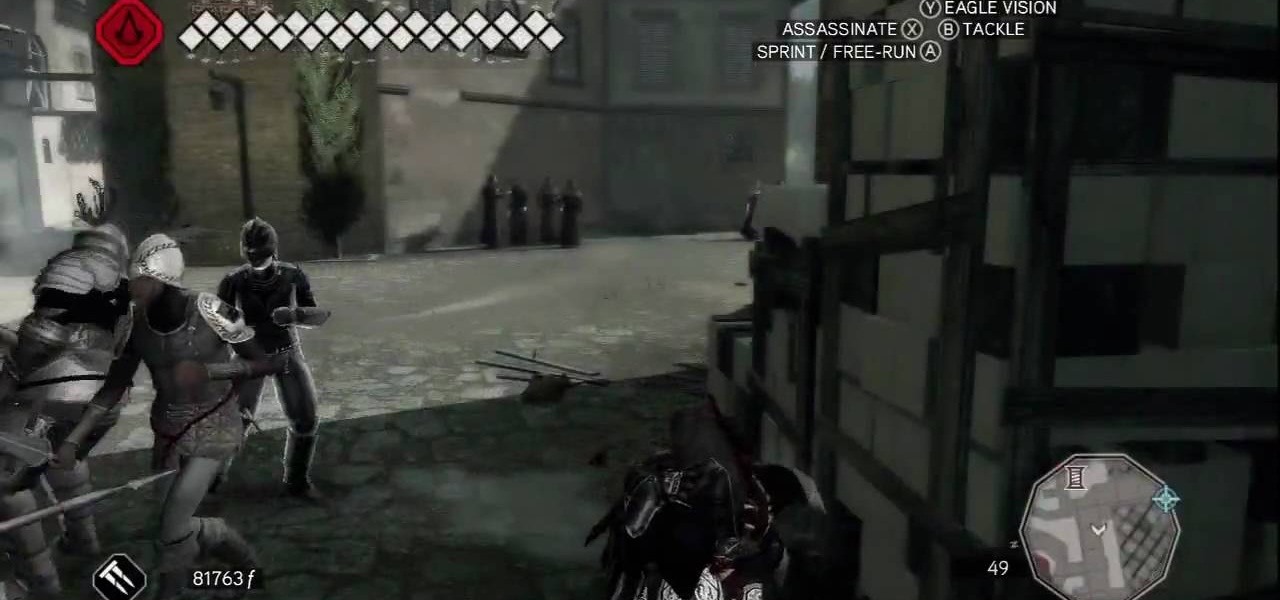
Assassin's Creed 2 was so popular of a game, that it spawned not one, but two downloadable content expansions, for both the Xbox 360 and PlayStation 3 versions. The first DLC was called The Battle of Forlì, and the second, Bonfire of the Vanities. This video game walkthrough focuses on the latter, in 1947 Florence, Italy, where the mass burning of sinful objects is an everyday event.

You’ve cooked on your own now try cooking with a dog companion. This video will show you how to make these popular Japanese snack. They consist of pancakes sandwiched around a whipped cream and sweat red bean paste.

Rumors, gossip, exclusion. Mean girls have a lot of weapons in their repertoire – here's how to combat all that nastiness.

Why buy lanterns for your backyard when you can recycle empty jars into beautiful ones? This video will show you how to make lanterns out of old jars.

Learn how to choose an indoor plant. You don’t need a green thumb to have houseplants that flourish; you just need to know which ones will thrive in your home.

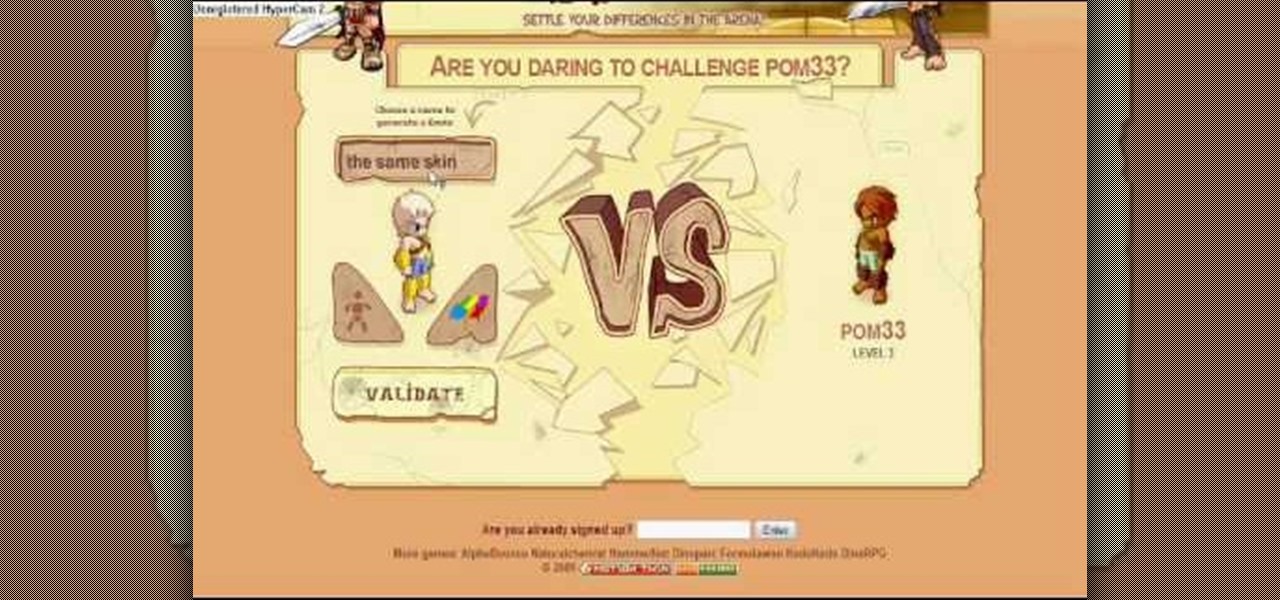
Click the more info tab to see the instruction on how to get a bear on Mybrute.com. This is a tutorial on how to get a Bear on Mybrute.com, An Online RPG Game, It's a very popular game that a lot of people plays everyday, You don't need to do much action with your hands just sit back and enjoy the show. Getting a bear is hard, because it's a extremely hard pet to get on mybrute.com, some sample pets are Dog,Wolf/Panther,Bear. If you can't read what I typed or did on to get a bear here's a lis...

Learn how to crash a wedding. If you have a free Saturday, we have a way for you to score free food, free cocktails, free dancing—and maybe even a hook-up.

Three hundred people die every year from carbon monoxide poisoning. Don't risk being a part of that statistic.

Gamers, anime fans, and those with an interest in Japanese culture are in for an AR treat courtesy of Google.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

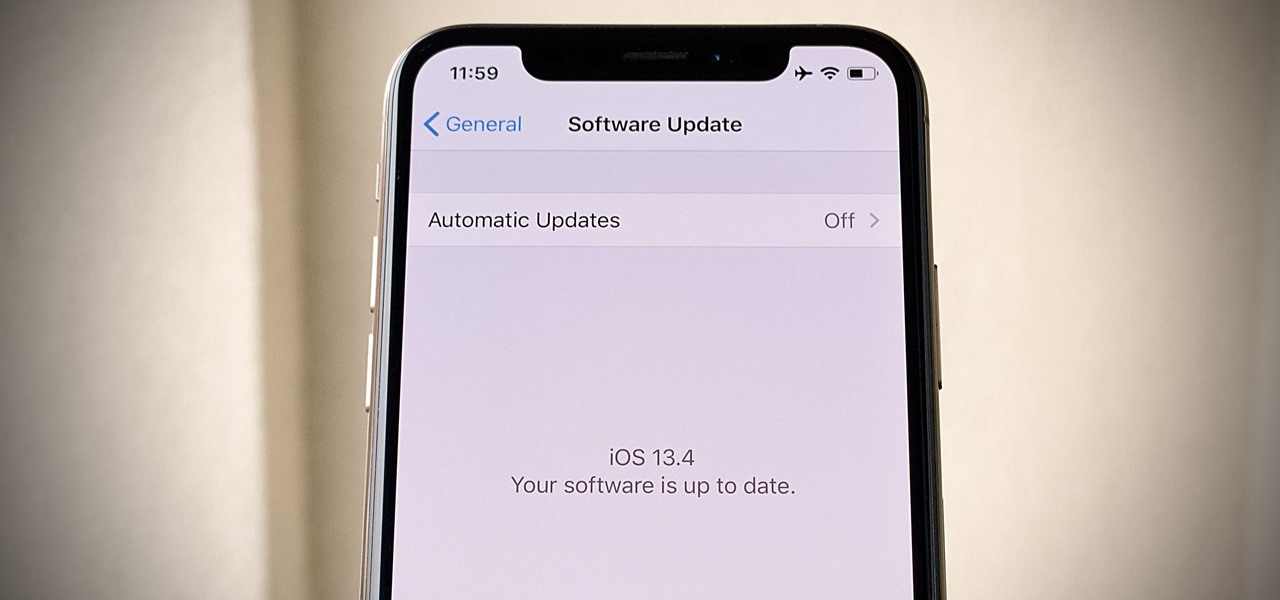
Apple released iOS 13.4 to public beta testers on March 18. The update comes the same day we learned that iOS 13.4 would be made available March 24. The sixth beta is iOS 13.4's GM (golden master), even though Apple refers to it as "beta 6."

Apple released iOS 13.4 to registered developers on March 18. The update comes just hours after news broke that iOS 13.4 would hit all compatible devices on March 24. The update is the GM (golden master), which makes it the same build as the official release we expect to see on March 24, although Apple does refer to it as "beta 6" on the dev site.

When it comes to iOS beta updates, developers get their updates first, and once they do, public testers play the waiting game. Sometimes Apple releases the public version three hours later. Other times it waits 24 hours. It's a roll of the dice almost every time. As for iOS 13.4 public beta 2, it's the latter case, coming exactly one after developer beta 2.

Last week, Apple released the first iOS 13.4 beta with fun and useful new features, such as new Memoji, an upgrade Mail toolbar, and the ability to control your NFC-compatible car via CarKey. To add to that, Apple just released iOS 13.4 developer beta 2, but does the update have any more new changes to be excited about?

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

Many people think antivirus apps are useless — why pay a subscription fee when most malware can be avoided with common sense? But the thing is, there were an estimated 3.5 million malicious Android apps discovered last year, with many of them making their way onto the Play Store. As this number continues to rise, can you truly depend on common sense to protect you?

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

As a former repair tech, I've heard the same reasons over and over as to why people opt not to purchase phone insurance. Some cite the cost—why pay extra every month for insurance when you're careful with your phone? Deductibles are expensive, so why not just spend that money on a repair instead of getting a refurbished phone as a replacement?

Google's new Pixel and Pixel XL flagships are some very powerful smartphones, but as with any high-tech gadget, they're only as capable as the user allows them to be. So if you're a proud new Pixel owner, it's time to bone up on a few new features to help get the most out of your device.

Rice is one of those incredibly versatile pantry essentials that you can make in bulk and then freeze for later use in a quick meal during the week. It keeps well in the fridge and freezer, and there are an endless number of ways that it can be used once thawed—from rice bowls and salads to stir-fry dishes.

I recently wrote about fast food fakeouts you can make at home, but people cannot live off fast food alone. Sometimes you need to step up your game a little and enjoy the fare at a popular chain restaurant with a bit more variety to its menu.

It seems like everything old is new again these days where food is concerned, and that includes the recent renaissance of babka. The name of this rich, rolled yeast bread, with roots in both the Jewish and non-Semitic Eastern European communities, means "little grandmother" in Ukrainian, Russian, and Yiddish.

I've been a fan of potatoes ever since I can remember... but mainly because they weren't a big part of my daily diet (which usually consisted of rice). And because my experience with potatoes was so limited, I only knew of two varieties growing up: big, brown Russets and sinewy sweet potatoes. As for cooking with potatoes—well, I'm embarrassed to admit that the only time I cooked potatoes when I was a kid was with the instant kind.