If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a tiny Arduino Wi-Fi sniffer that saves Wireshark-compatible PCAP files and fits anywhere.

Whether you're in high school or college, you no doubt will have your iPhone in your pocket all day long. To make your iPhone last the whole time and even help you out with your studies, these are the accessories you'll want to get your hands on.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

Just in time for the holiday season, Lenovo has released its Mirage AR head-mounted display with the Star Wars: Jedi Challenges game and accessories. Unfortunately, while its price point is a fraction of most other AR headsets, at the moment, it does have a few issues with the setup process.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting for newbies to get down, and that's where Punchabunch comes in.

We've heard the rumors for months, but it's finally official: The iPhone 7 will not include a traditional 3.5 mm headphone jack. Instead, you'll need to hook your favorite headphones up with a Lightning adapter (or use ones with a Lightning connector built-in) and connect to your phone using the same port that your charger occupies.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

I record close-cropped videos and take macro still shots with my smartphones on a daily basis, so as you would expect, I spend a lot of time cleaning these devices. Over the course of a couple years, I've fine-tuned my cleaning regimen, and at this point, it's down to a near-science.

Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

Sugru is some pretty versatile stuff. The company's slogan is "Hack things better," and for good reason. It sticks to aluminum, steel, ceramics, glass and plastics, it's waterproof and heat-resistant, and it can be molded into any shape you can imagine. Anything from your kitchen cabinets to your bicycle can be improved with some Sugru and a little creativity, and gadgets are no exception. Here are 10 of the coolest hacks to fix or upgrade your smartphone, tablet, or camera.

HP TouchSmart PC is a powerful computer with various features. You can use you PC to connect to other hardware devices like printer, scanner etc. A hardware device might not even work with you computer because the connecting cables might not match. So if you want a printer to connect to your computer you will need a USB connector. If your printer has a normal pin connector, you cannot work with it directly. In this case the other option is to print wireless, provided your printer supports it....

This is an easy guide on how to load a CD in a 2010 Toyota Prius. On units with standard audio system, insert CD into the slot to load. Press eject button on the left to eject. On units with JBL audio systems, press the load button in the right hand side and wait for the light. Next to the CD port to turn amber until solid green. Now you can insert a CD (if you'd like to load all 6 CDs), press and hold the load button and wait until light turns solid green. Now you can insert the next CD and ...

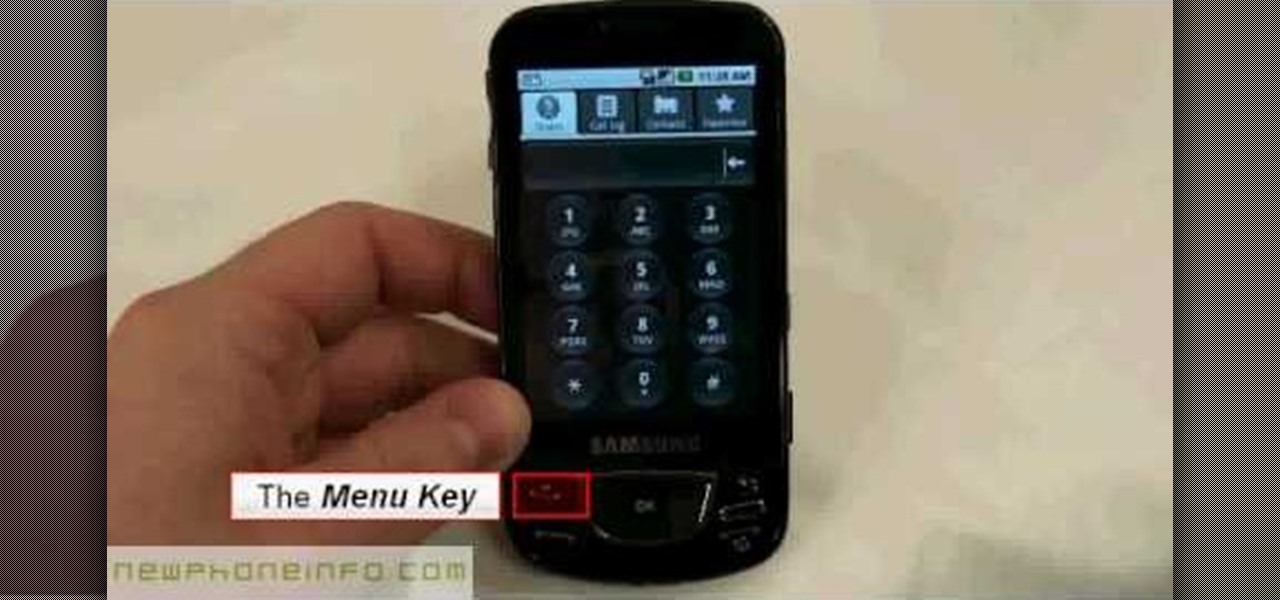
Follow this video to learn some basics on how to use a Samsung Galaxy I7500 mobile phone. Switch on the phone by pressing the power key in the bottom right corner. To navigate around the screen press with your finger on the touch screen and swipe to the left or right. If you want to open a particular application simply press the icon relating to it. Press the menu key to open the home screen with its various options. Press the dial key to open a screen where you can dial in the numbers for a ...

Mission 10 on the Sony PSP takes you through finding the ship for Kyrenia to deliver Alexander's message to the crewmen without being discovered. The path to the Crewman is relatively free of guards if you stick to rooftops as much as possible. Then, leap down to the docks below. The manifest is located on the big ship docked at the Port. Take the ladder down to the deck below and follow your nose to the manifest. With it now in your possession, take it to Alexander. For more info, watch the ...

Prepare to delve into the world of L4D2 and check out the gameplay for Campaign 1: Dead Center - Streets. Stock up and open the safe house door. You should see a bunch of infected milling about here. Kill them and make your way straight up the hill past the port-o-potties. Turn right at the fence and take the street down. Watch out for zombie attacks from the walls to the left and right of you. They will drop down from above. Duck into the building on the right when you reach the fence at the...

Digidesign has transitioned all of their plug-in software copy protection from floppy drive based key disks to copy protection authorizations that reside on the iLok technology provide by PACE. The following is some information about iLok technology.

In this video from AppleGenius0921 he shows us how to connect and set up a Rocport 9CX external hard drive to your Mac. You can connect with 800 or 400 firewire. Take the 800 firewire cord and connect it from the hard drive to the Mac firewire port. Now the Rokport will power up with a blue light and will pop up on the screen. To format it or change any settings, open disk utility, select your hard drive, go to Rocport, click partition, and click apply to settings.

Left 4 Dead 2 has a new add-on campaign, and it's called "The Sacrifice". This DLC for the Xbox 360 is a prequel to "The Passing", which features a meeting with three of the survivors from the original Left 4 Dead video game, where they learn that Bill, the fourth original survivor, sacrificed himself for his fellow comrades.

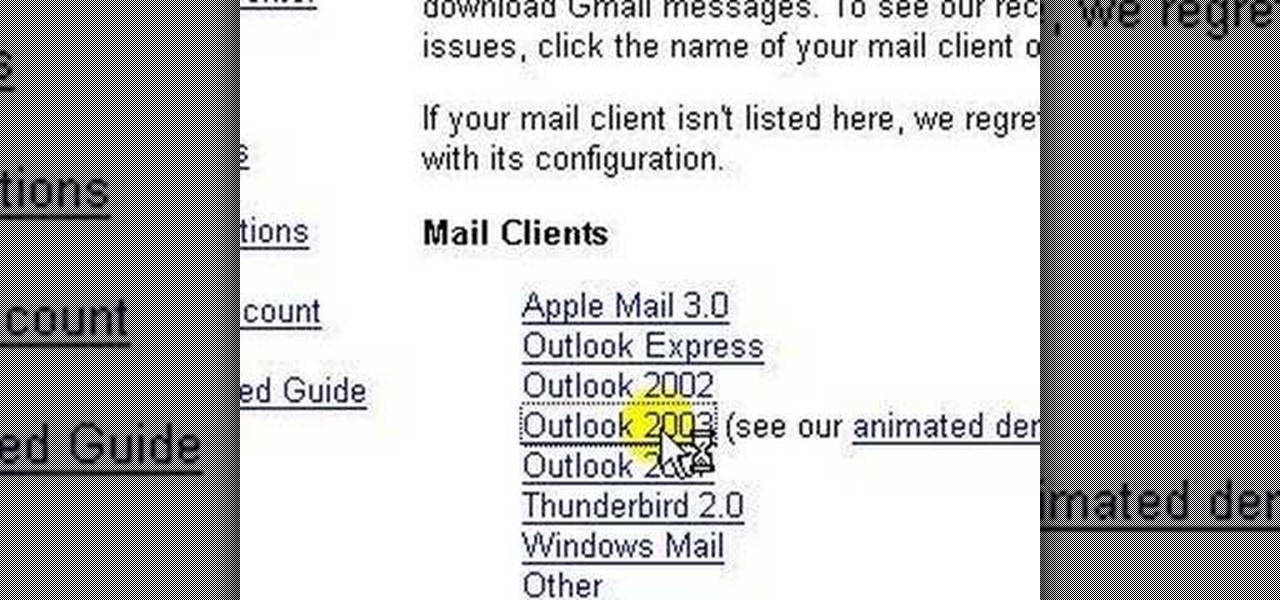
lakercoolman shows us how to set up our gmail account with this quick tutorial. Basically outlook express is a program that helps us to organize our email with added features such as contacts, to do lists and calender entries. Its an offline email client that allows us to work offline and also lets us set up exchange servers aswell. Ohter email servers such as hotmail and yahoo charge for thios service but the advantage of gmail is that IMAP or POP access is free. in ofer to set up, navigate ...

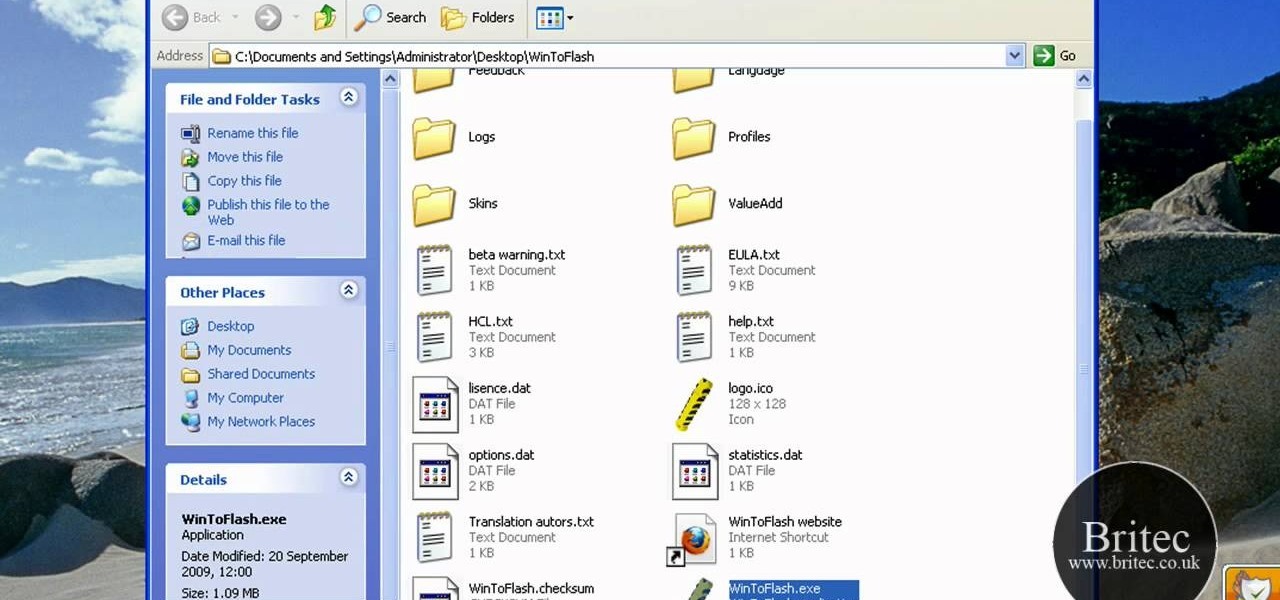
This is a how to video to prepare a bootable USB installer for windows 7/XP using wintoflash. Here are the steps to do.

This video tutorial from iTouchMaster2 shows how to SSH to iPod or iPod Touch using FileZilla application.

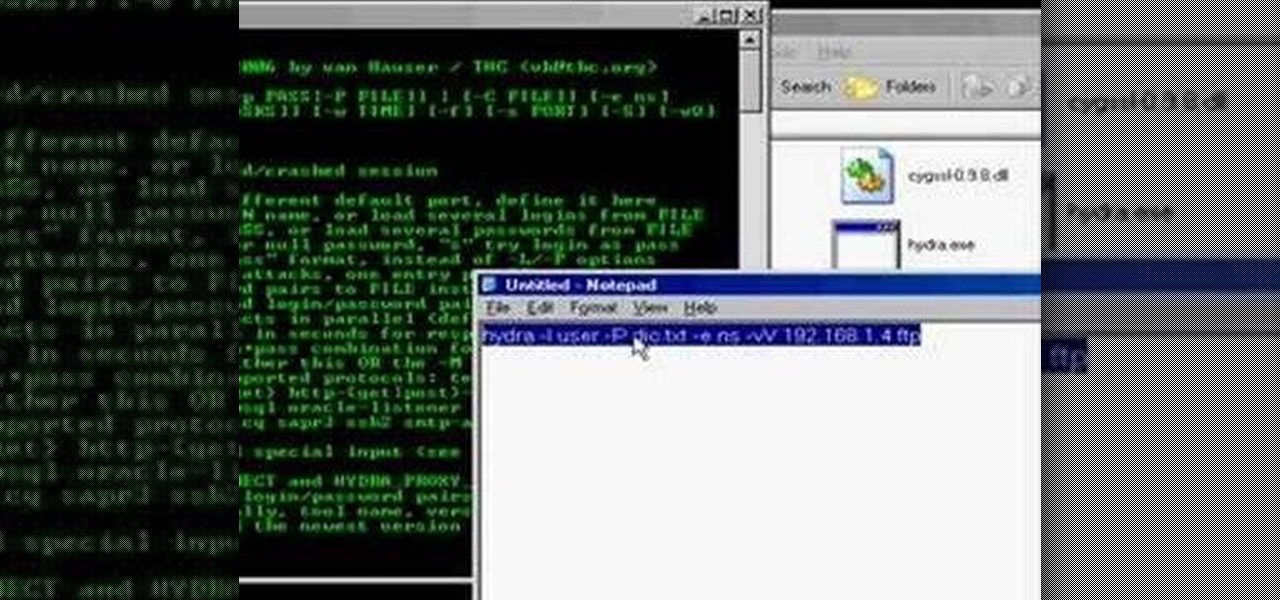
This is a how-to –video on using hydra 5.4 to crack FTP passwords. This video is intended for educational purpose only. It reveals the basics of hacking a FTP server using dictionary search technique. Here are the steps involved.

HighQuality Tutorials demonstrates how to change your iPod Touch alpine default password. Changing the default password is useful when using your iPod Touch in a public setting to make it less vulnerable to hacking. To change the default password, first open up your internet connection and search for Putty. Download the Putty program. Open and run the Putty program. Your host name will be your IP address for your iPod Touch. Select port 22 and SSH and open up the program. Log in as root and c...

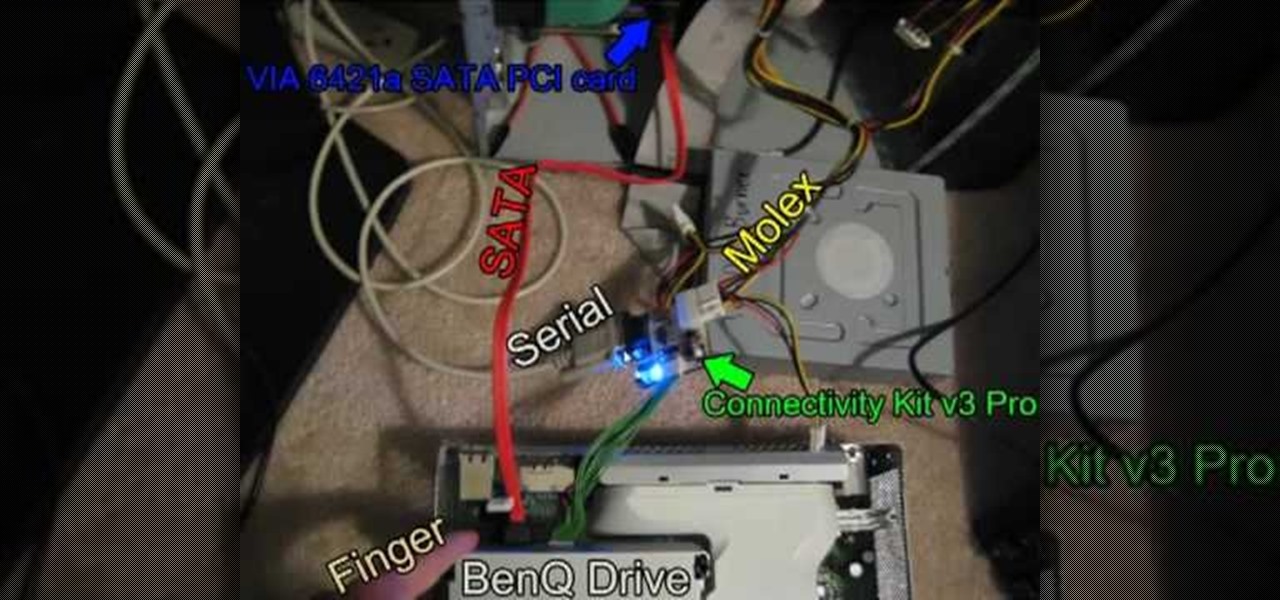
In this Video Games video tutorial you are going to learn how to flash the Benq VAD6038 Xbox 360 DVD drive. This video will show how to do this with the connectivity kit and the jungle flasher. You will need a compatible card for this. VIA 6421a SATA PCI card is probably the best card. Install the VIA card and make the connections as shown in the video. Before you power on the connectivity kit, install the port IO 32 drivers and also the USB drivers for the connectivity kit if you are using U...

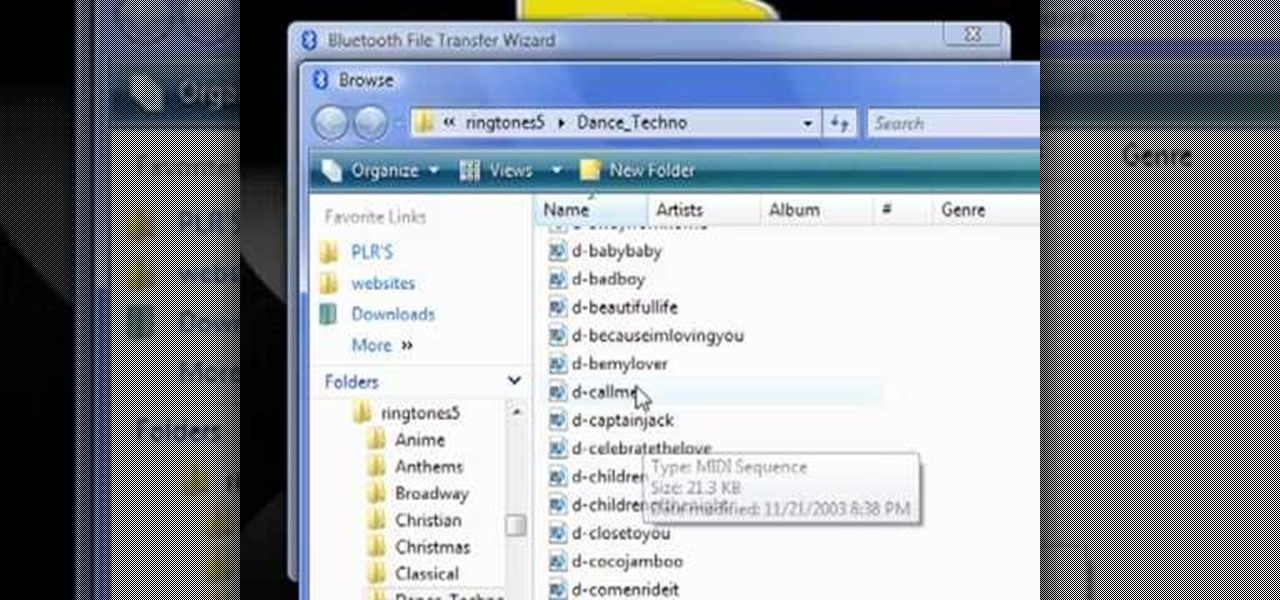
The video demonstrates how to connect your Bluetooth phone to your computer and send/receive files between them through Bluetooth. You need to first switch on Bluetooth in your phone and then click on the icon for Bluetooth connectivity in the computer. Then click on the option called 'Add a Bluetooth Device'. You can see a setup wizard pop up in your computer screen where you have click on the check box and then click on Next button. Once the phone is detected, select it and click on Next. T...

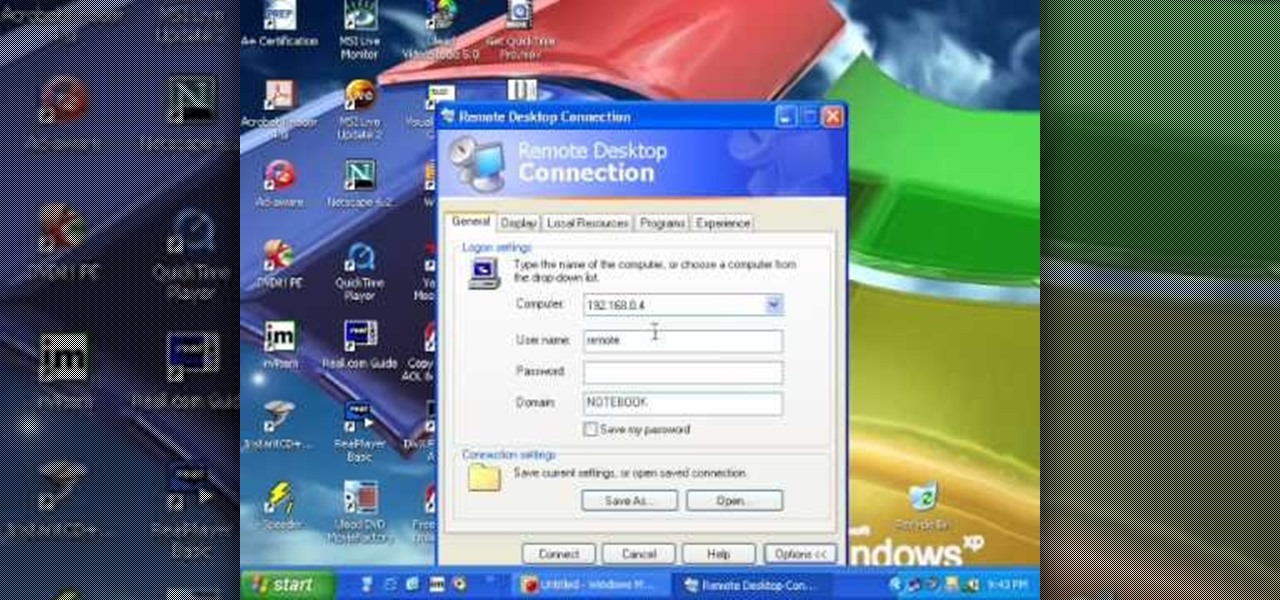
This video from Michael presents how to establish a Remote Desktop connection in Windows XP Professional.This type of connection allows you to access your computer via Internet from any place and manage files, local resources, or perform any other remote activity.To establish Remote Desktop connection click Start button, right click My Computer, from the opened menu select Properties. System Properties window will open. Choose Remote tab. Check Remote Desktop - Allow users to remotely connect...

This video is about how to make uTorrent 2.0 faster. The first step that you will have to do is to open your uTorrent 2.0. Once you have opened uTorrent 2.0, go to "options" then click "Preferences". Once you have clicked "Preferences", go to "Connection" found on the left side of the window. Then beside the random port, change the numbers to "45682". After you have changed it, go to "Bandwidth". Then change the maximum upload rate to "15". Also change the maximum download rate to "1890". You...