
How To: Build a waterfall using retaining wall block
The procedure was adopted to build a waterfall in Oregon Coast Garden Center, Wald-port. 1. A level pad was cut to arrange the first row of blocks


The procedure was adopted to build a waterfall in Oregon Coast Garden Center, Wald-port. 1. A level pad was cut to arrange the first row of blocks

If you don't have a Wi-Fi network, you can still easily SSH into your iPhone. Just follow the steps outlined in this video tutorial. First, you will need a Mac or iPhone along with Fuju. Just download the program. Once you have all of this, click on the Wi-Fi bar and click on Create New Network. As a name, click on iPhone SSH and click Manual. This creates your new network, which you will see on the desktop. Double click on it and then look at your iPhone. Go to iPhone. Connect to the network...

Learn how to access the PS3 secret recovery menu by following this tutorial. You will need a PS3, PS3 remote, and a USB charger cable. Hold the power button on your system. Listen for three beeps (as you keep your finger on the power button). The third beep will turn your system off. Repeat this process, but this time, you will hear only two beeps (one beep followed by a quick double beep). Turn your TV on and it will tell you to connect your controller to the PSP. Connect your USB cable to t...

In this video, Chris Kimball of America's Test Kitchen appears on CBS to show us how to make full proof pepper-crusted fillet mignon. America's Test Kitchen made this recipe 40 or 50 times to make sure it's the perfect recipe. You can start with an entire tenderloin and cut out the center cut, which is preferred or you can buy them in the supermarket pre-cut. Next, take 5 tablespoons of peppercorns and crush them with the bottom of a saucepan. This makes it easier to coat the meat. Cook the p...
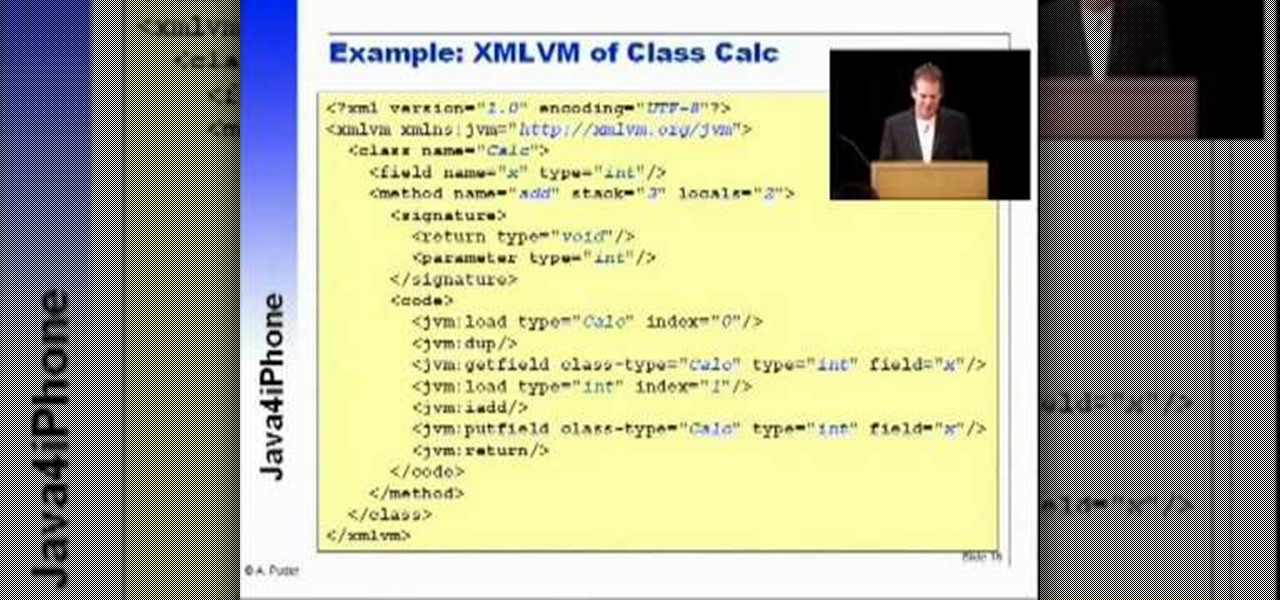
Arno Puder, a master of the XML coding field, gives a great rundown of Apple's new proprietary Java coding. This is especially helpful for Cocoa implementation

Don't jeopardize your memories. Learn how to preserve your old home movies by digitizing your VHS tapes.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install the latest Wine on Ubuntu Linux.

Bet your friends that you can make wine magically go into an upside-down glass, and the next round will be on them.

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to make an LED blink with an AVR microcontroller.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

Ten days after Magic Leap declared that it had selected the winners of its Independent Creators Program, the company has officially released an almost full list of grant recipients.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

China-based virtual reality headset maker ANTVR has decided to enter the augmented reality space, and to do so it's launching its headset on Kickstarter. The company claims that its new Mix AR device has a field of view that surpasses the Meta 2, the HoloLens, and others within a smaller form factor and at a fraction of the price. But there's a catch.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.
Google's Pixel lineup hangs its hat on smooth software and a polished UI. At the core of this experience is the Pixel Launcher, a home screen app that is often imitated, but never perfectly duplicated. That is, until developer AmirZ released the latest version of his Rootless Pixel Launcher port.
The Pixel 2's camera is one of the best you'll find on an Android phone. Among its standout features is the incredible Portrait Mode, which Google accomplished with some impressive software processing. Thanks to a few clever developers, you can now enjoy the Pixel 2's Portrait Mode on your Galaxy S8 or Galaxy Note 8.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.
Rooting has a long and storied history in the Android community. As OEMs push out more refined software, the need to root has diminished — still, the number of incredible things you can do with a rooted phone is enough to tempt many enthusiasts. Luckily, some manufacturers are still putting out root-friendly devices.

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practicing and taking your hacking skills to the next level.

The Galaxy S8 and S8+ haven't even hit shelves yet, but some of the stock apps from Samsung's latest flagships have already been leaked. The biggest one so far is the new Samsung Experience Launcher, which replaces TouchWiz Home, and is quite a bit different from anything you'll find on previous Galaxy models.
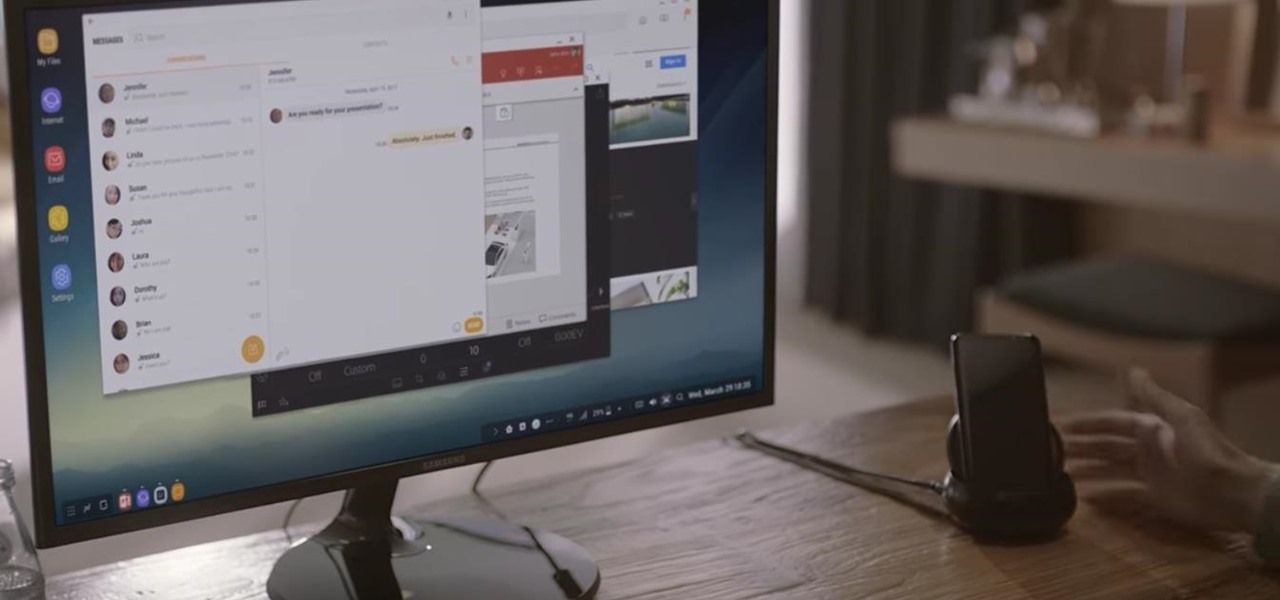
Samsung's new Galaxy S8 can turn into a PC with its DeX dock, but while that may sound like the future of mobile computing on the surface, there are definitely a few issues with the entire setup.

Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking.

When you think about consumer VR headsets, you either imagine a computer-tethered powerhouse like the Oculus Rift and HTC Vive, or something portable yet limited that utilizes your smartphone like Google Cardboard. Somehow, we haven't seen much in-between, but the Idealens aims to fill that gap.

Greetings comrades! Great leader has ordered that we gain intel on a website owned by the opposition. For all general purposes we will be scanning nmap.org because they really don't care if Big Brother decides to perform a whois on their IP. We will be using Dmitry for the scanning.

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!

Although lots of the bigger hotel chains are lessening the restrictions they put on their room TVs, some smaller ones are still taking measures to prevent you from plugging in computers or streaming devices into an HDMI port. However, there are a few steps you can take to bypass these restrictions and watch your own media in a hotel that has restricted TVs.

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.

You're at your friend's house. All you've heard about all day is his new laptop. He's got a brand new top-specced MacBook Pro, and he won't stop going on about it. It particularly annoys you as all you've got is a 4 year old cheap laptop, even if it is running Linux.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

In my last how-to, we built a man-in-the-middle tool. The aforementioned script only established a man-in-the-middle. Today we'll be building a tool to utilize it. We'll be building a DNS packet sniffer. In a nutshell, this listens for DNS queries from the victim and shows them to us. This allows us to track the victims activity and perform some useful recon.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

One of the most feature-packed camera suites out there resides on the Sony Xperia Z2. Along with the regular camera and video modes, it comes with Motiongraph, AR Effect, and Social Live.

If you've got a MacBook, I'm sure you've spent some time messing around with the Photo Booth app. Who would have thought that adding simple effects like Comic Book or Stretch could make a selfie look so hilarious. Photo Booth is available for all Mac OS X computers running 10.4 or higher with an iSight camera, and it's also available on a few of Apple's iOS devices. Actually, it's only for the iPad 2 and all newer iPads since. It is NOT available on the iPhone, don't ask me why.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

Samsung is currently dominating the Android market with their line of Galaxy devices, including the GS3, GS4, Note 2, and Tabs. All of these devices run Samsung's TouchWiz, which is something every softModder should try out eventually. The only thing is that Samsung devices are pretty expensive, and many of you don't actually need (or want) another Android tablet.
There are very few things Android users would want to borrow from Apple's iOS, but let's move beyond the fanboy/girl biases and admit that Apple actually does a few things pretty well. One of those things is looks, and the new iOS 7 looks pretty amazing to me.

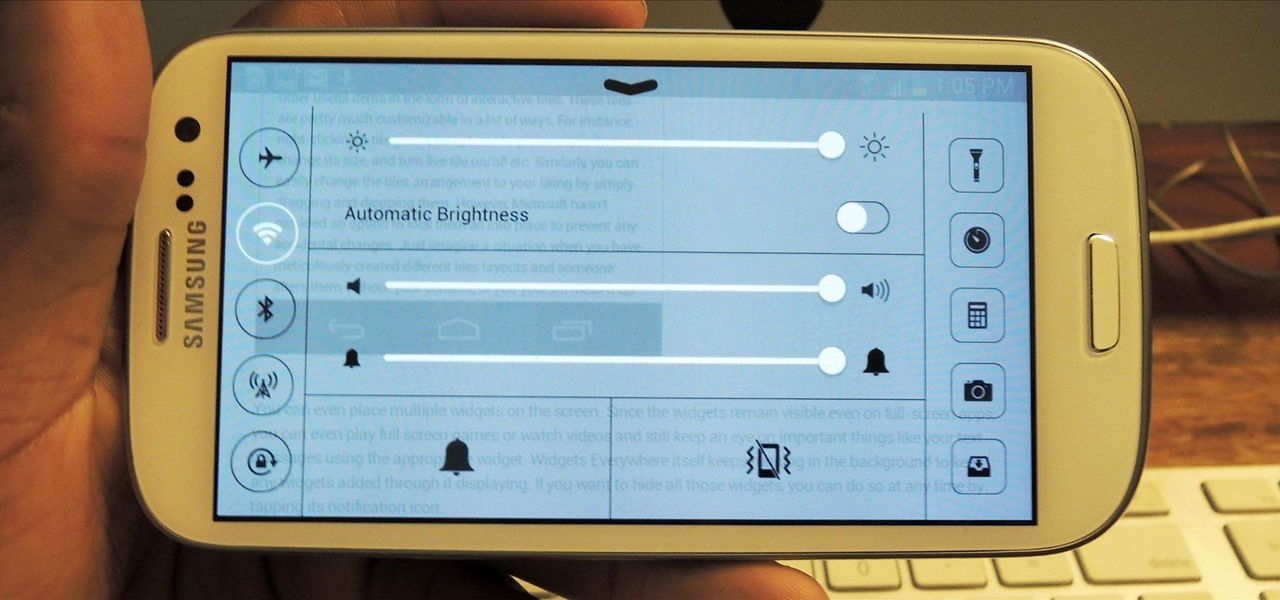
HTC's Sense 4 may be leaner and faster than previous versions, but one thing my EVO 4G LTE sorely lacked was the "Quick Settings" option that Sense 2 and 3 had. Developers were able to port it to Sense 4 for Android 4.0 (Ice Cream Sandwich), but the only way to get this feature was to install a custom ROM. With the update from ICS to Android 4.1 (Jelly Bean), my EVO 4G LTE received the new Sense 4+ version. This new Sense made it possible to add widgets to the Notifications pull-down menu, so...

I spend practically all day surfing the web and writing on my laptop, and just as much time texting and checking emails on my smartphone. So, it's only natural for me to charge my iPhone using the USB port on my MacBook Pro.