
How To: Make a Simple UDP_Flooder in C pt1.
Alright, this will be my first tutorial in C. Note that this guide is written for Linux.


Alright, this will be my first tutorial in C. Note that this guide is written for Linux.

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.
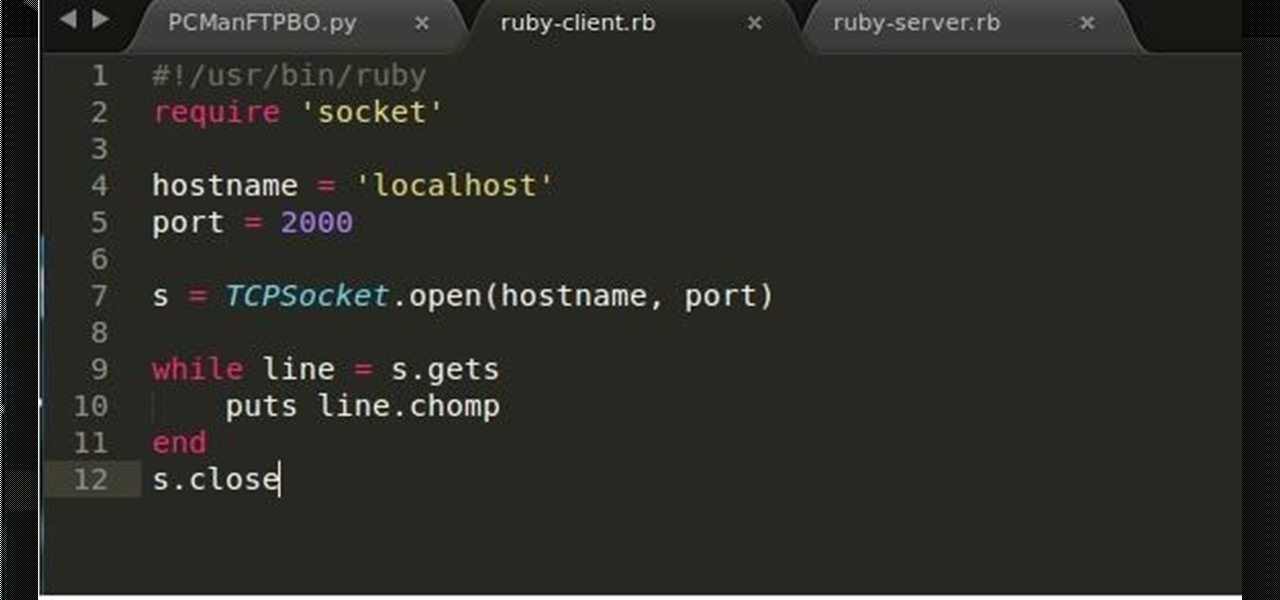
Recently, I've been learning Ruby as a second scripting language. But one topic I never covered with the many lessons online were sockets. So I did some research and came up with a very simple client/server connection that sends a string over the socket.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

This video instructs you on how to clean the trackball on the Blackberry Bold 9000. Begin by turning off your Blackberry and removing the battery. Using a torque T5 screwdriver, remove the 6 screws around the edge that hold on the cover. Remember that doing this will void your warranty. Once the cover is removed, use your screwdriver to lift off the circuit board. Be aware that the USB port can get stuck. If that happens just push the port down slightly and you should be able to remove the ci...
This video shows you how to control your computer from your iPod touch. 1. Go to UVNC. Click on Installation. This will take you to download options. Download the latest stable version. 2. Install Hamachi, which helps you find your computer's IP address. Click on Download Here link, fill in the registration information, and click submit. 3. Install a VNC listener on your iPod so it can connect to your desktop. Jailbreak your iPod, and open the installer. Click All Programs; scroll down until ...

After many years of rumors, the second-generation iPhone SE is here. At $399, it is the most inexpensive iPhone Apple has sold since the original iPhone SE came out. And while the new SE comes with Apple's typical five-watt power adapter, the smartphone supports fast charging — you just need to get a fast charger separately.
Samsung put some of the industry's most advanced camera tech in the Galaxy S20 series. However, their image processing still lags behind the Google Camera app found on Pixel phones, so the end result is good but not great. Luckily, you can install a mod to pair that beastly hardware with arguably the best camera software.

The $35 Raspberry Pi is an amazingly useful single-board computer (SBC) with a good balance of price, performance, and connectivity options. But for some projects, it just isn't enough. Whether you need more computing power, a smaller size, or better machine-learning capabilities, there are other options available.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.

Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring....

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

Are you a "Tron" fanatic? Then this laptop case will blow your mind. Styled after the streamlined, glow-in-the-dark "Tron" cinematography, this laptop bag looks like a "Tron" suit and will shine even at night.

Microsoft has behaved pretty douchily as far as managing the hard disc drive (HDD) sizes it made available for the XBox 360. The 20GB drive included in most models of the system is woefully inadequate, and many have been convinced to give Microsoft even more money to get a larger one. That's not necessary. This video will teach you how to upgrade the XBox 360's hard drive yourself, putting in any large-capacity SATA drive you wish and massively increasing the storage capacity of your XBox 360...

With all the little gadgets people carry around these days, those little cigarette lighter outlets just don't cut it for in-car power sources anymore. Unfortunately, that's often the only option our cars and trucks come with.

We all know that September 19th is National Talking Like A Pirate Day, but did you know that even your Facebook page can join in the festivities? At the top of you Facebook page, click "Settings". From the page that comes up, click on the "Languages" tab. On the next page you will see a drop down menu of all of the languages that Facebook makes available to its users. Scroll down within this drop down menu until you see "English (Pirate)", and select this option. When the page reloads, your "...
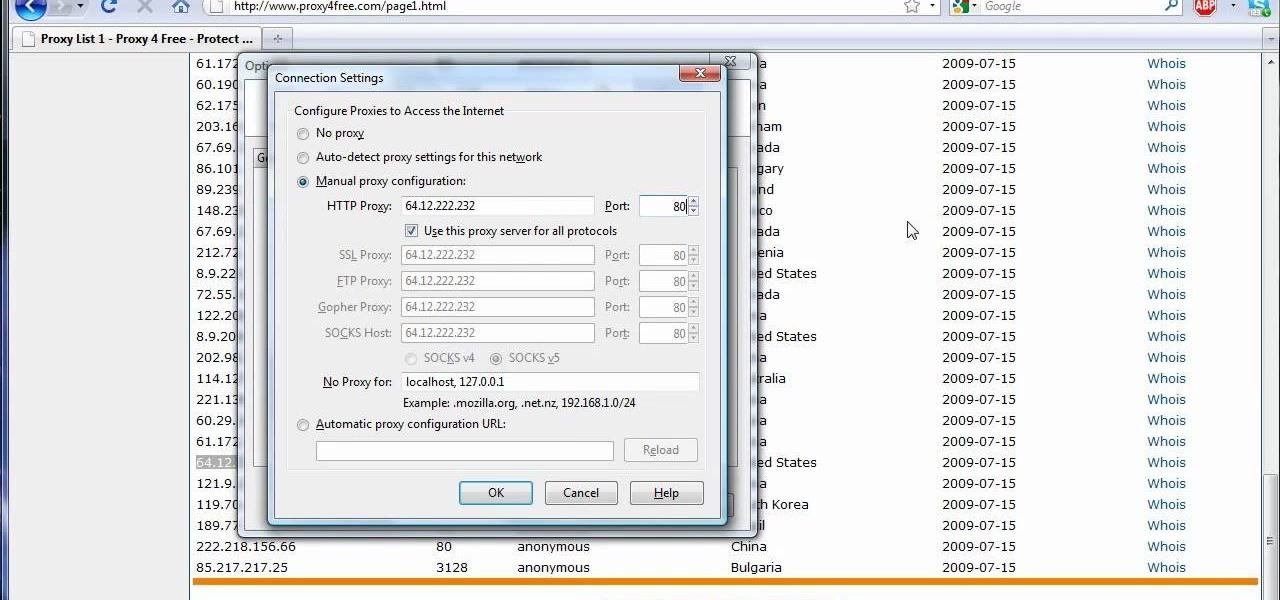
The video shows us how to use a proxy server with Firefox to hide your IP address. you can actually use this to avoid the hacking and various things that are blocking you from websites. Firefox is one of the easiest way to do this and for doing this you need to Google search the free proxylist and then you can select a proxy from the one which is related to the country you are residing in. Then copy that proxy server and then go to tools and click on options and under advanced tab click on ne...

Mike Agerbo explains the benefits from listening to one's music through AppleTV, however it seems that one cannot listen to any music or other audio files unless he/she is using iTunes media. Agerbo explains how you can use Apple TV with other types of media, using a program called ATV Flash. Agerbo believes ATV Flash to be an easy and inexpensive tool to upgrade one's Apple Television so it can use the USB port and download and use other media content. One can also create a Boxee account to ...
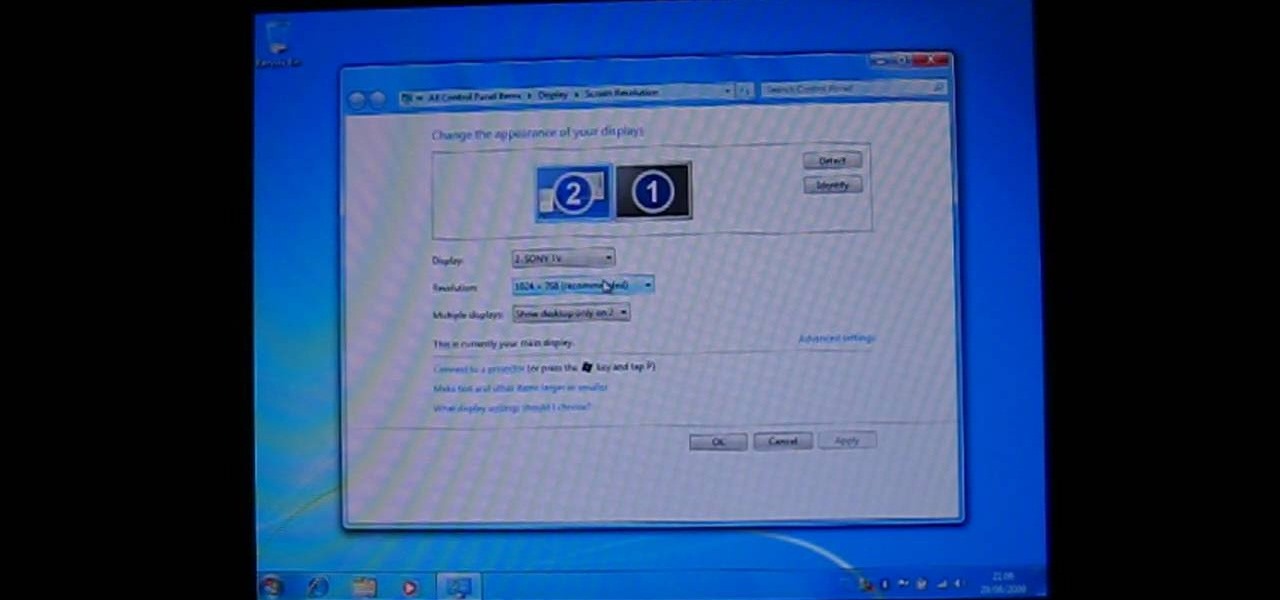
This Windows tutorial demonstrates how to connect a laptop with an Intel graphics card to a TV using the VGA port output in the laptop and a VGA cable.

If you're not into pork, you probably won't like this particular recipe, and if you're not into raw meat, you may want to avoid this, too. Because this video recipe covers a meal that requires Parma ham, which is ham that is eaten uncooked. You could always dive in and try it out anyway, because it's well worth the experimenting! Plus, there's prawns, fresh salad and lemon juice.

First, you will need a surfboard cable modem. You will need a wireless router with an unscrewed antenna and a power cord. Make sure you have two ethernet cord and a computer. First, take the surfboard and screw the cable into it; make sure it is completely tight. Next, take the router and one ethernet cord. Look for the spot that reads WAN; plug the ethernet cable into this spot. Take the other end of the ethernet cable and plug it into the port on the surfboard.

Isn't it annoying when you want to check your Facebook or MySpace but you are at school and hit a big giant Websense blocker? Well, if you are stuck in a library or somewhere else where there are filters on your surf-ability, check out this tutorial for a useful hack.

If you're looking for a new recipe to try, why not try making some lamb shanks. The instructions are easy to follow and you'll be sure to wow your guests. Ingredients: 3 tbsp olive oil, 2, 4 or 6 lamb shanks, 2 stalks celery, 2 whole carrots, 1 large onion, 1.5 cups port wine, 1 cup red wine, 2 cups chicken broth, 2 cups beef broth, 5 garlic cloves, 28 oz can of tomatoes, 1 sprig rosemary, 4 or 5 sprigs thyme. Instructions: Trim the fat and the silver skin off the lamb shanks (optional). Salt...
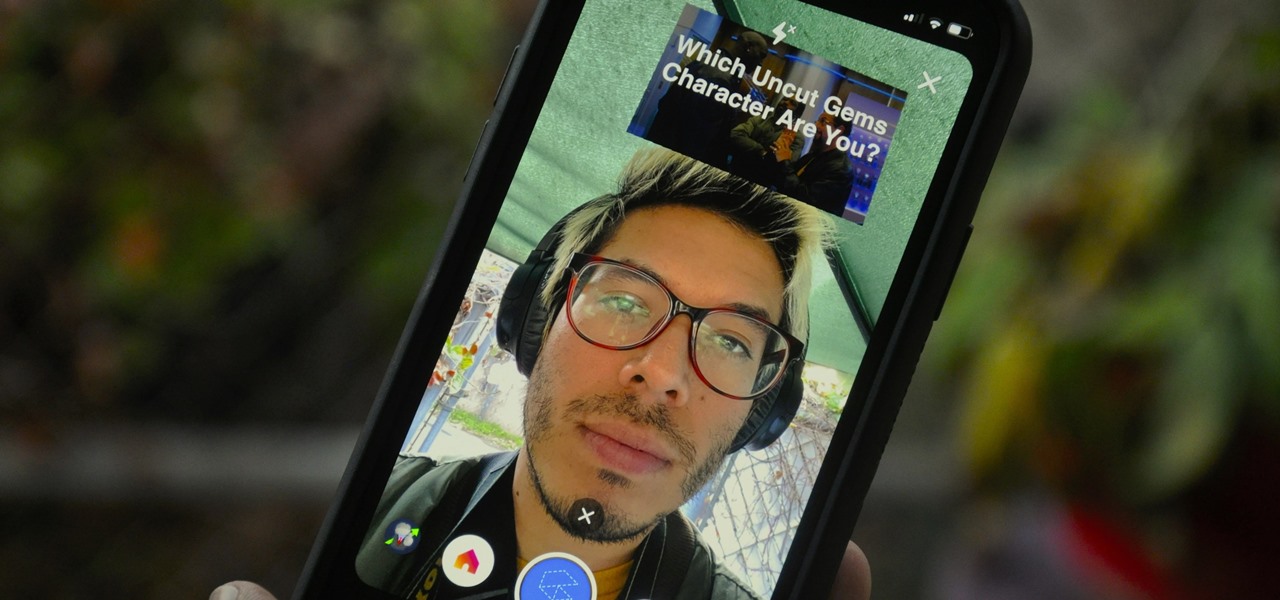
There's a new trend on Instagram Stories: People are making viral AR filters where images of popular characters from TV shows, movies, and other mediums shuffle above your head until one sticks. The filters range from Disney and Pokémon characters to Harry Potter and Friends, but you're not limited to just that because you can create your own "which are you?" filter.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

It wouldn't be iPhone season without a new controversy. Chargegate, Apple's latest PR nightmare, is the name being used for charging issues on some iPhone XS and XS Max devices. If you plug in your iPhone at night — or whenever — then wake up or come back later and see that your iPhone has even less battery power, you're affected. But there is a fix you can implement right now.

Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this saga has Apple outright disabling the Lightning port.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

Hand made air conditioner made of a foam lunch box, 5 volt DC fan, 4 AAA rechargeable batteries, and some ice. This homemade AC can run on batteries and you can plug directly into any USB port.

In order to get your "five a day," or five a day of fruits and vegetables, you should incorporate these foods into everything you make to eat. So for instance, adding a cup of spinach into your turkey and swiss sandwich is one serving of vegetables that you won't even notice, while this recipe, which incorporates figs, gives you yet another serving.

Hak5 is at it again, with a plethora of somewhat accessible solutions to your technological problems. If you've ever needed to get through your school's firewall, or secure traffic tunneling, or try out applications in a fast, efficient manner? This video has it all and more.