If you just got a new iPhone, chances are you picked up the iPhone 11, successor to the iPhone XR, the most popular device in Apple's 2018 series. Since the XR did so well, it was predicted that the iPhone 11 would too, and so far, it has lived up to that prediction, beating the 11 Pro and 11 Pro Max in sales in 2019.

The Pixel is the phone to beat when it comes to cameras, and it's largely due to software. While its hardware is solid, Google's machine learning prowess and general coding wizardry are the biggest reasons the Pixel is so good with taking photos and recording video. What this means is that if you can get the Pixel's camera software, you can replicate the Pixel camera experience on other phones.

With the rapid demise of the 3.5 mm headphone jack, Bluetooth is fast becoming our best option for universal audio. The problem is, with over a decade of it being a standard component, many of us still own a reliable pair of wired headphones that we don't want to gather dust. Well with one tool, you can have your cake and eat it, too.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

Google just released Android 9.0 Pie, but the Android community is already working its magic. Developer Quinny899 quickly ported the updated Pixel Launcher from the new build, so you can try it out on other phones right now.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

On May 25th, 1977 a small movie with a $13,000,000 budget came out. At the time, the executives involved had no faith that this film would make any money. To the surprise of many in the industry, not only did that film set records, it led to a number of other movies, video games, books, toys, cartoons and so much more. This film we know as Star Wars became a long lasting hit that is still setting records 40 years later.

Just days after the first Android O preview build was released, the development community had already started bringing some of the exclusive features over to older Android versions. For instance, the Pixel Launcher received an update in Android O, and developer linuxct quickly ported the new version to work on devices running Marshmallow or higher, and even managed to do so without requiring root.

We recently covered a set of ported apps from the new cloud-based smartphone, the Nextbit Robin. These ported APKs brought two of the Robin's slick new stock apps—Camera and Gallery—to any other device, but the launcher was conspicuously absent.

Welcome back everyone! It's been awhile hasn't it? Sorry for being so quiet, but my CCNA courses have really picked up recently. In the last article we covered how to import modules and how we can use them. In this article, we'll actually be covering a module that is essential to the hacking aspect of Python, sockets.

Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow.

A few lines of code in the iOS 9.1 library cache found by Chase Fromm (@uloshe) indicate that Apple could be working on making iPhones that are Li-Fi compatible.

OK, In my last Tutorial we made a Server for sending Instructions to a Client. This time we will build the Client. Fire up your favourite Python environment and get the Code here.

When they were purchased by Google back in 2011, Motorola underwent a sweeping change in software philosophy. All throughout the UI on their flagship devices, edgy design patterns were replaced by clean, minimalist interfaces akin to vanilla Android. This philosophy has continued on as Motorola's signature, even though they have since been sold to Lenovo.

Hello My Fellow Hackerzz.. This is my first How-to and i'll be updating the “Hacking Android Using Kali” to msfvenom and some FAQ about known problems from comments. So Here we GO!!

If you've been watching the latest USA TV Series Mr Robot, you will have seen the Raspberry Pi used by Fsoeciety to control the HVAC system. OTW covers this very well here with his take on setup they may of used.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Bad news, guys. The shelf life for liquor leftovers does not apply to your two-buck chuck. While an opened bottle of your favorite whiskey will stay respectable for ages thanks to its high ABV (which makes it inhospitable to outside elements), an opened bottle of merlot will sour quickly. However, it turns out that red and white wines have different life spans once they're opened—for reasons which we'll cover below.

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.

Whether you've been fully converted or just want a little Apple with your Android, adding your iCloud email to your Galaxy Note 3 is a fairly simple task. Usually, Apple and Android don't play nice, but your iCloud address can be added to your stock email app just like any other email account.

So, you've got a brand new PlayStation 4, but unfortunately, you've got "No Signal" now, too. You can't really game or watch movies on your new toy if you can't even bring up the PlayStation menu on your TV screen.

Welcome to this short and easy tutorial on hacking and DDosing (is that even a word I don't know) anyways lets get started

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

Don't know much about the dinner table? You know the basics: you eat from a plate, you use silverware to shovel it in and you drink from glassware. But what about if you're at a fancy dinner? Would you be able to distinguish a juice cup from a champagne glass? A white wine glass from a martini glass? If not, these two videos will show you which ones are which.

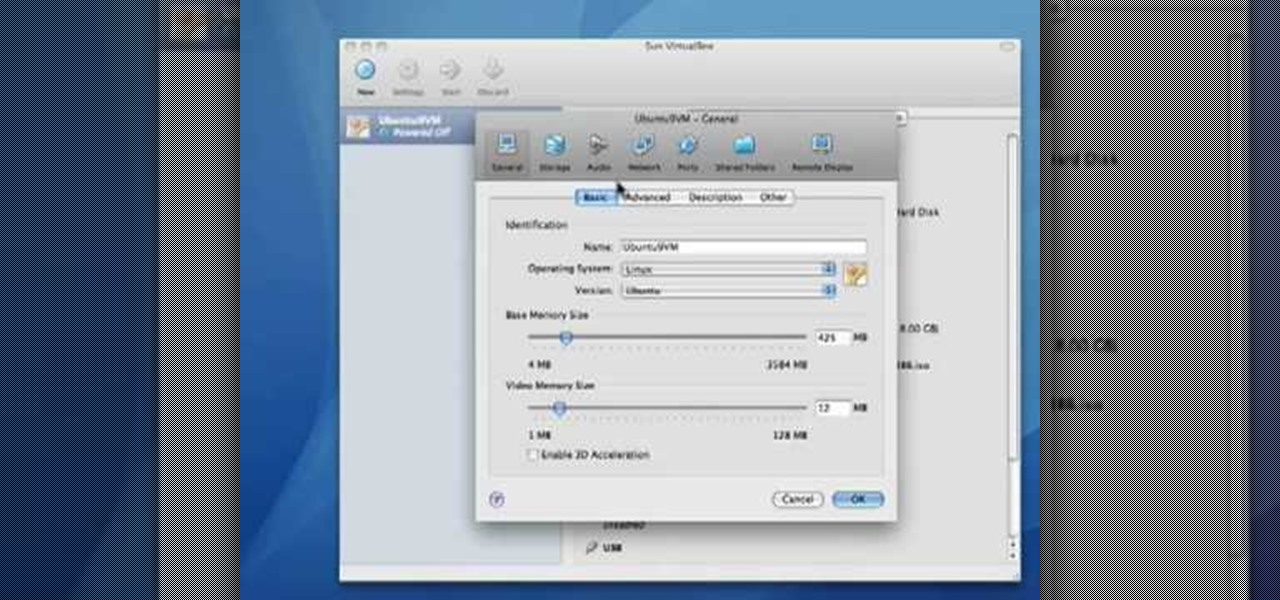
Before you can alter the settings of a virtual machine, you must first have the machine powered off. Load VirtualBox on your Mac desktop and make sure it is powered off on the left hand panel. Double-click General and a window should pop up allowing the changing of several settings. For example, you can include a description to keep many virtual machines separate, or adjust the size of the drive. You can even add virtual devices through ports if they are connected to the physical machine. The...

This video shows you how to assign a letter to your USB flash drive (or memory stick) or how to change it in Windows.First of all, connect the flash drive in the computer's USB port. Click on the start button, then right click on My Computer and choose manage. Once the window opens, go to Disk Management. There, you should be able to see the USB drive as "USB DISK". Right click on it and choose "Change drive letter and paths...". Now click on change and select the desired letter for the drive...

Learn how to operate the latest Blackberry 8330 in simple steps. Follow the steps below to overview the Blackberry 8330: 1. First switch on your Blackberry by pressing the power button on its top. 2. Use the 'Trackball' to navigate around the menu options and press it to select an option. 3. The 'Send' can be used to call a contact, the 'Menu' key opens a list of options, then the 'Escape' key is used to end an application and the 'End' key is used to end a call. 4. You can find on the left s...

This easy-to-follow video tutorial walks you through steps of converting old VHS tapes to DVD. Roxio Easy VHS to DVD is a combination of software and hardware that allows you to easily and quickly digitize old analog recordings. You simply attach the included hardware to a free USB 2.0 port on your computer, then capture from virtually any analog video or audio source.

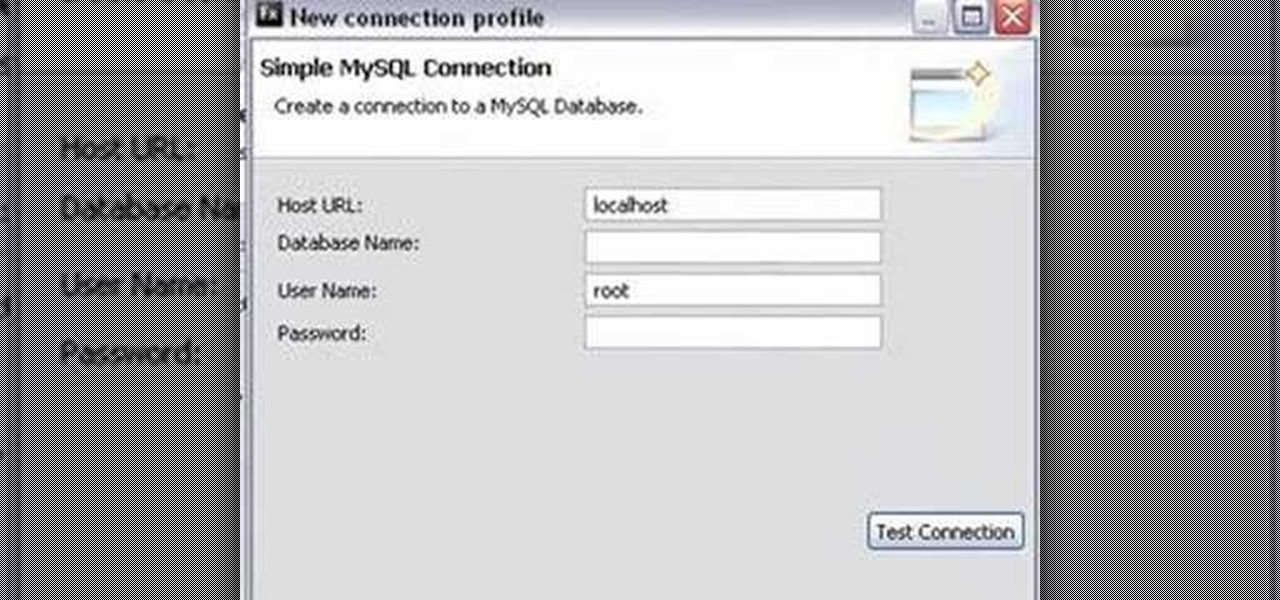
This tutorial demonstrates how to create what is called a complete client-server web application which consist of a Web Application, PHP, and MySQL. The tutorial shows how to automatically generate the PHP necessary to talk to a MySQL database using Adobe Flex Builder 3.

This is a short tutorial on how to use your iPhone as a remote control for your eeePC. First download touchpad from installer.app, as well as install VNSea if you don't have it.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

The fifth annual Amazon Prime Day is upon us. Starting July 15, Amazon will offer thousands of deals on products across its site, kicking off at 3 a.m. EDT. This year, it will only run for 48 hours, so you have even less time to act. To save you some of that time, we made a list of the best deals for smartphone accessories.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

Everyone's been raving about the Pixel's top-notch camera, and the acclaim is well-deserved. The main difference between Google's new camera software on their Pixel phones and the older software on their Nexus devices is that the Pixel has almost no perceptible lag between tapping the shutter button and the image being captured—even with HDR+ mode enabled.

Hello people, I'm back for Part-3. In this part, as promised, we are going to create a client program and then we are going to test it with our server program made in Part-2.