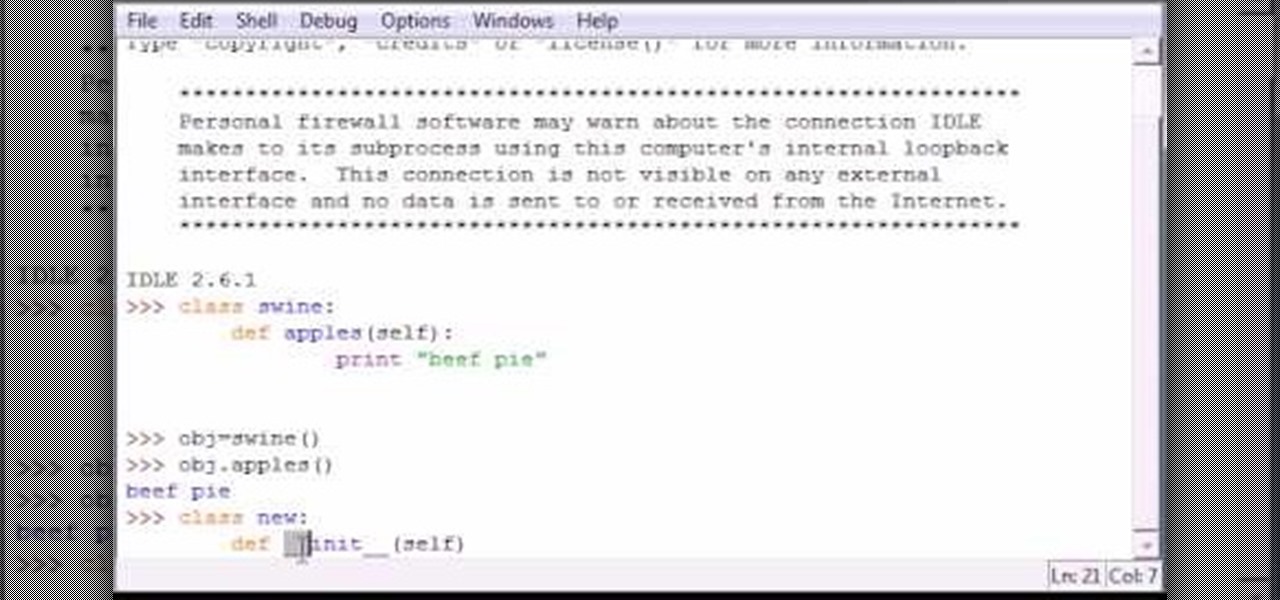
Bucky from The New Boston serves up this Python video tutorial on how to create and program constructors in Python. This is the program you use to write all of your Python code down. Learn how to create constructors and what they do!
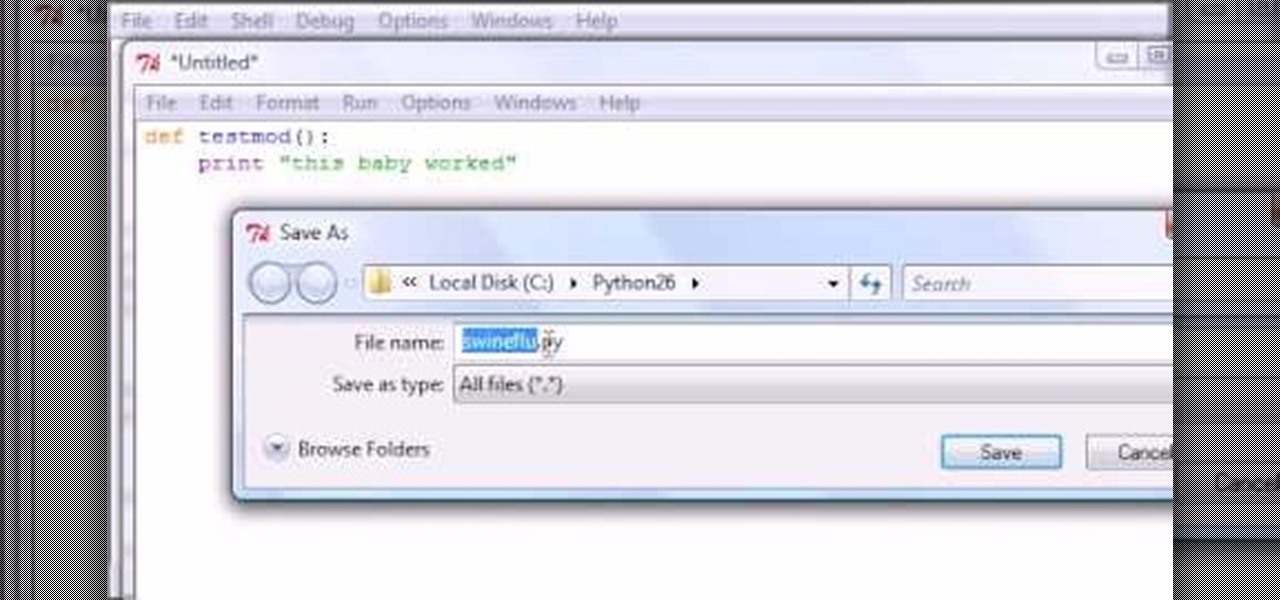
Bucky from The New Boston serves up this Python video tutorial on how to import modules into IDLE in Python. This is the program you use to write all of your Python code down. Fun with importing modules!
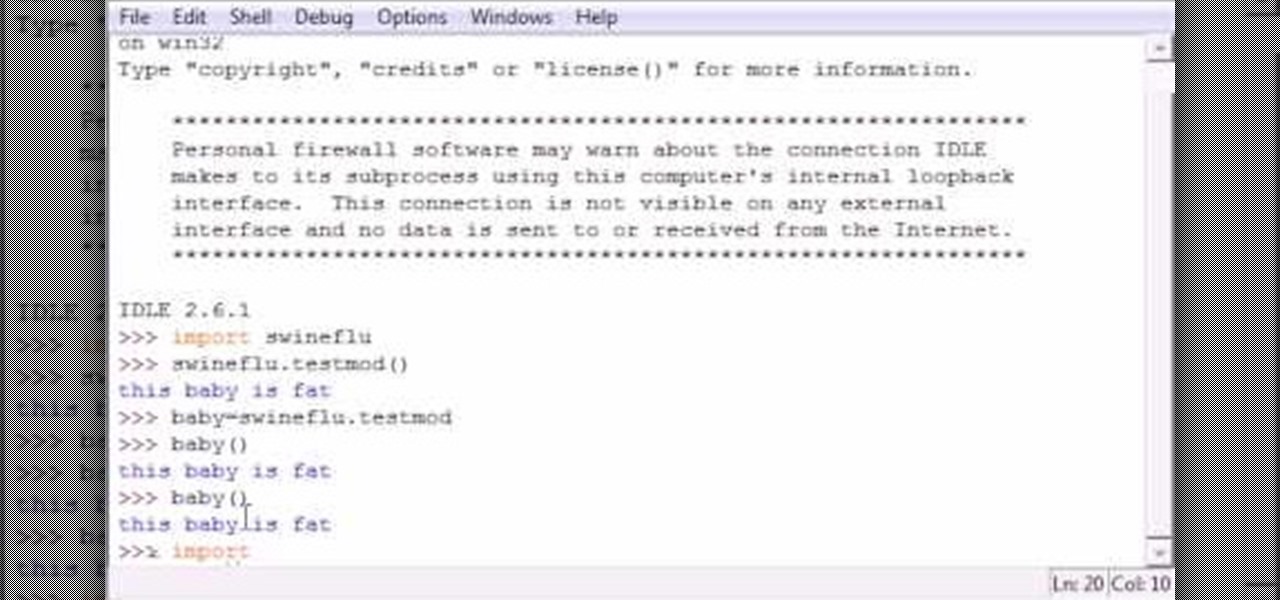
Bucky from The New Boston serves up this Python video tutorial on how to reload modules in Python. This is the program you use to write all of your Python code down. Learn how to reload modules once your source file has been edited!
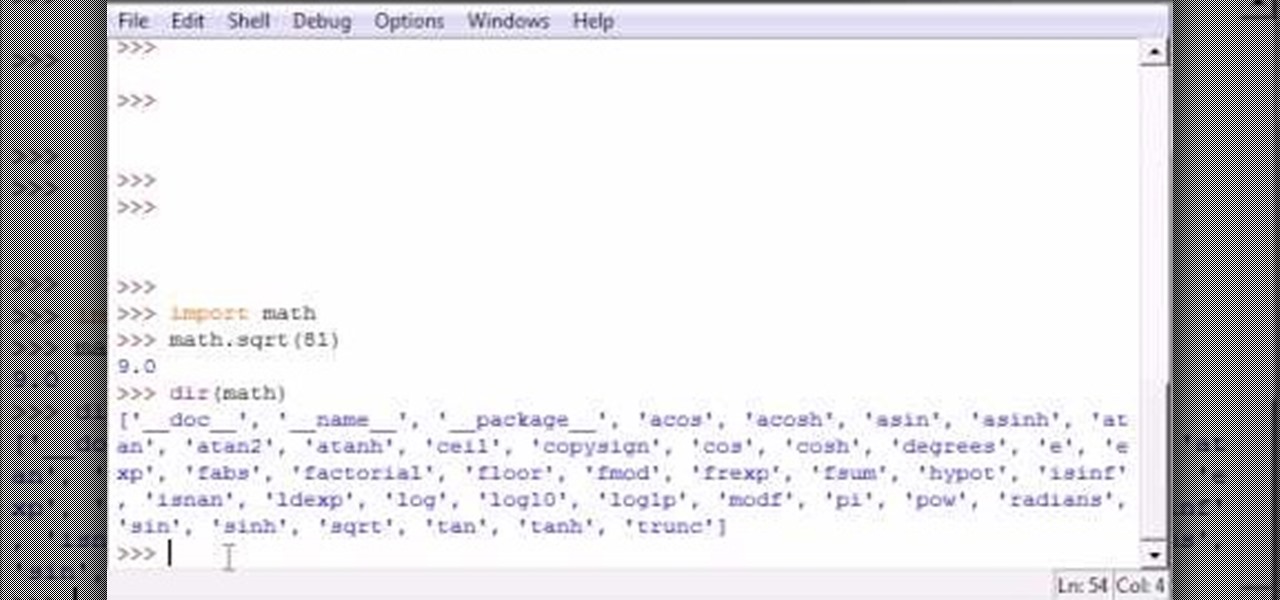
Bucky from The New Boston serves up this Python video tutorial on how to get module information in Python. This is the program you use to write all of your Python code down. Learn how to get extra info from outside modules!

Bucky from The New Boston serves up this Python video tutorial on how to work with files in Python. This is the program you use to write all of your Python code down. Fun with files!

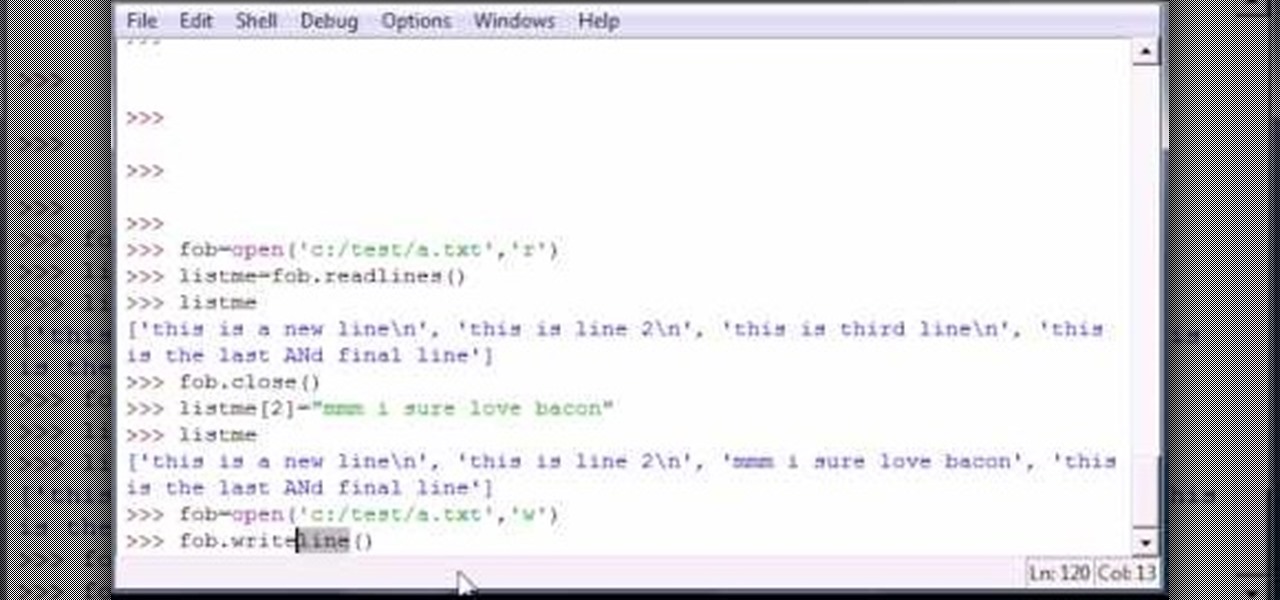
Bucky from The New Boston serves up this Python video tutorial on how to read and write lines in files in Python. This is the program you use to write all of your Python code down. Fun with reading and writing lines into a file!

Bucky from The New Boston serves up this Python video tutorial on how to program and write lines in files in Python. This is the program you use to write all of your Python code down. Fun with writing lines into a file!

Bucky from The New Boston serves up this Python video tutorial on how to download and install wxPython for Python. This is the program you use to write all of your Python code down. Learn how to install the GUI (graphical user interface) toolkit.

Bucky from The New Boston serves up this Python video tutorial on how to program methods in Python. This is the program you use to write all of your Python code down. Fun with methods! Learn what methods are and how to use them.

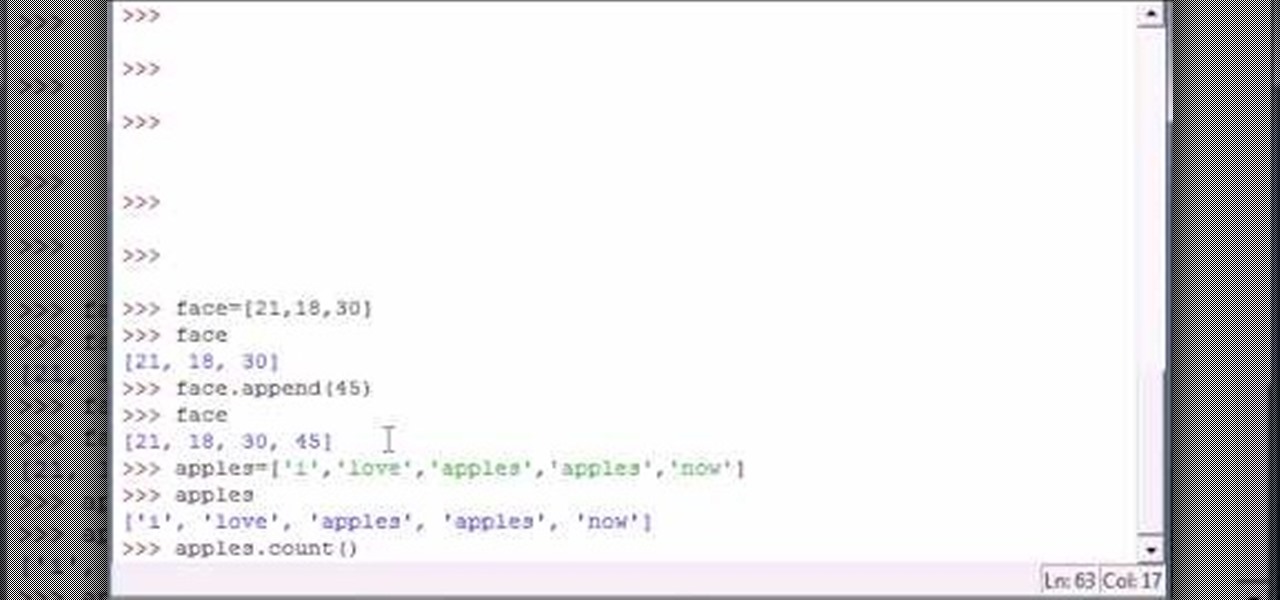
Bucky from The New Boston serves up this Python video tutorial on how to program slice lists in Python. This is the program you use to write all of your Python code down. Slice Python!

Bucky from The New Boston serves up this Python video tutorial on how to program lists functions in Python. This is the program you use to write all of your Python code down. Fun with list functions!

Bucky from The New Boston serves up this Python video tutorial on how to program slices in Python. This is the program you use to write all of your Python code down. Slice Python!

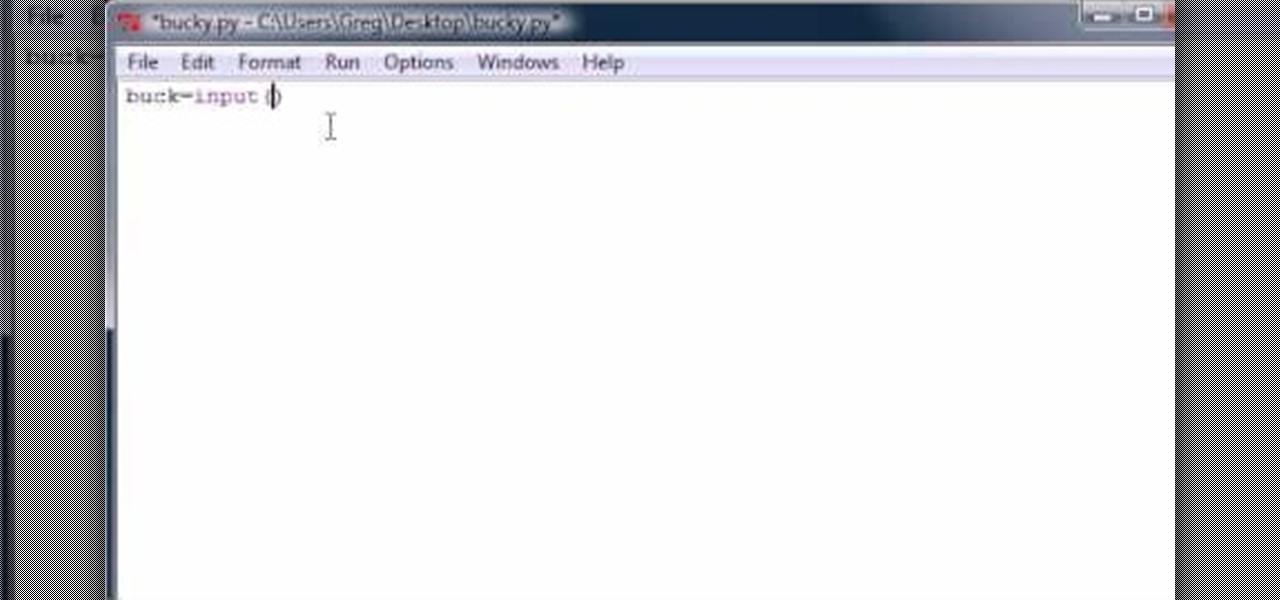
Bucky from The New Boston serves up this Python video tutorial on how to program raw input in Python. This is the program you use to write all of your Python code down. Fun with input versus raw input!

Bucky from The New Boston serves up this Python video tutorial on how to save and execute your programs in Python. This is the program you use to write all of your Python code down. Fun with saving programs!

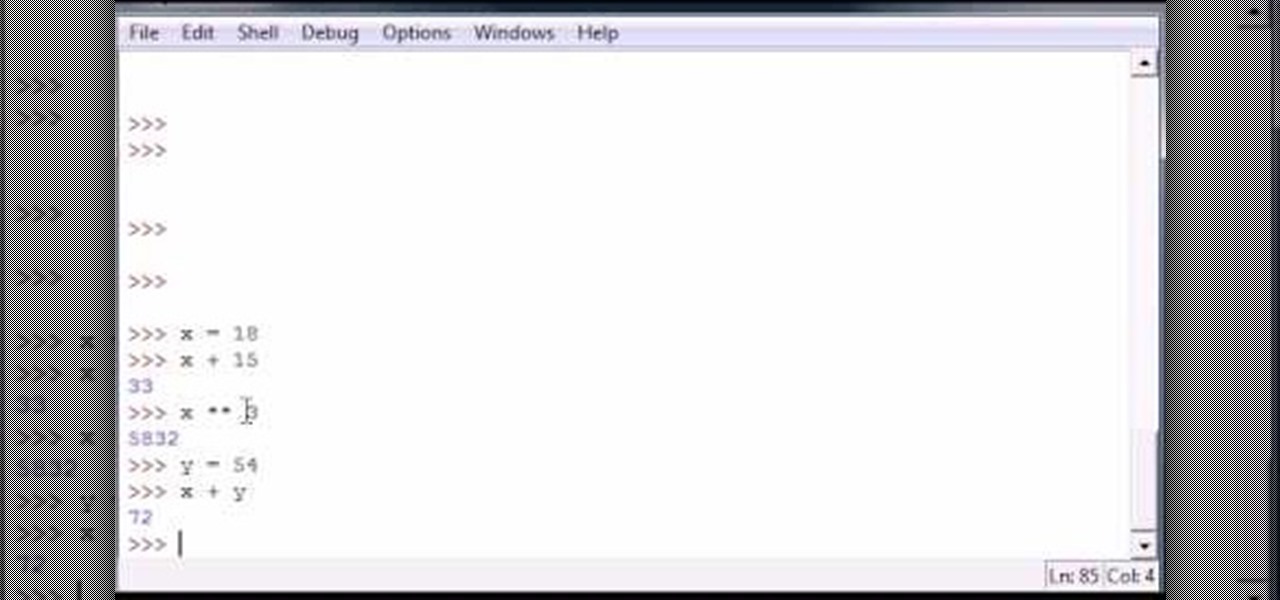
Bucky from The New Boston serves up this Python video tutorial on how to program variables in Python. This is the program you use to write all of your Python code down. Fun with variables!

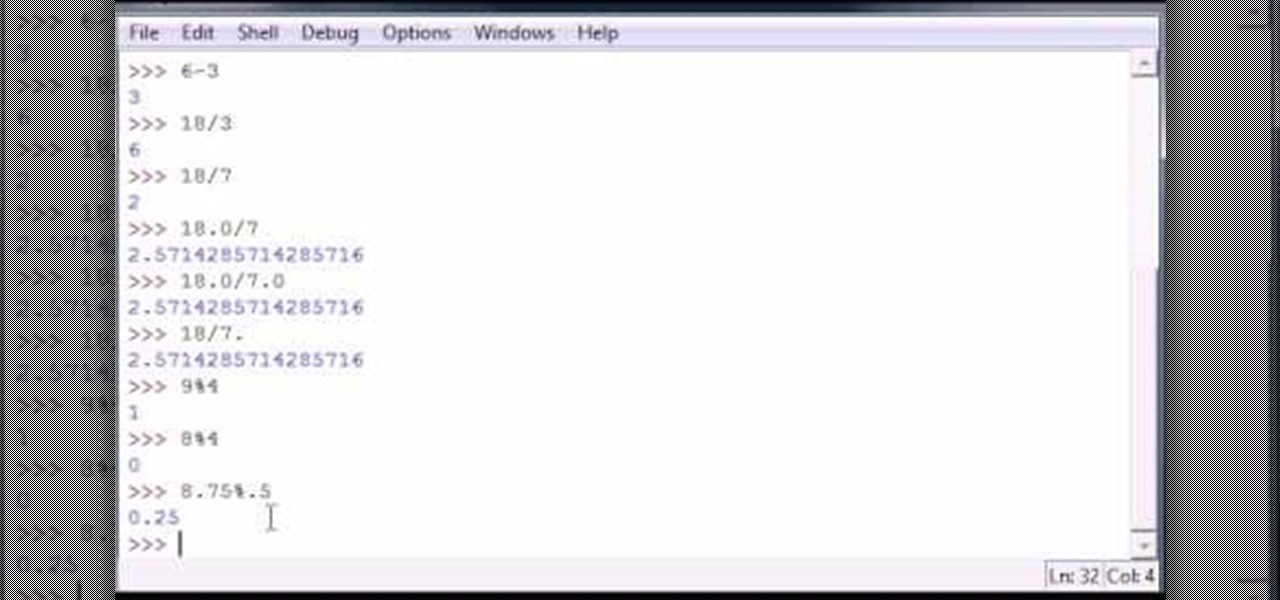
Bucky from The New Boston serves up this Python video tutorial on how to use simple numbers and math calculations in Python. This is the program you use to write all of your Python code down. Fun with numbers!

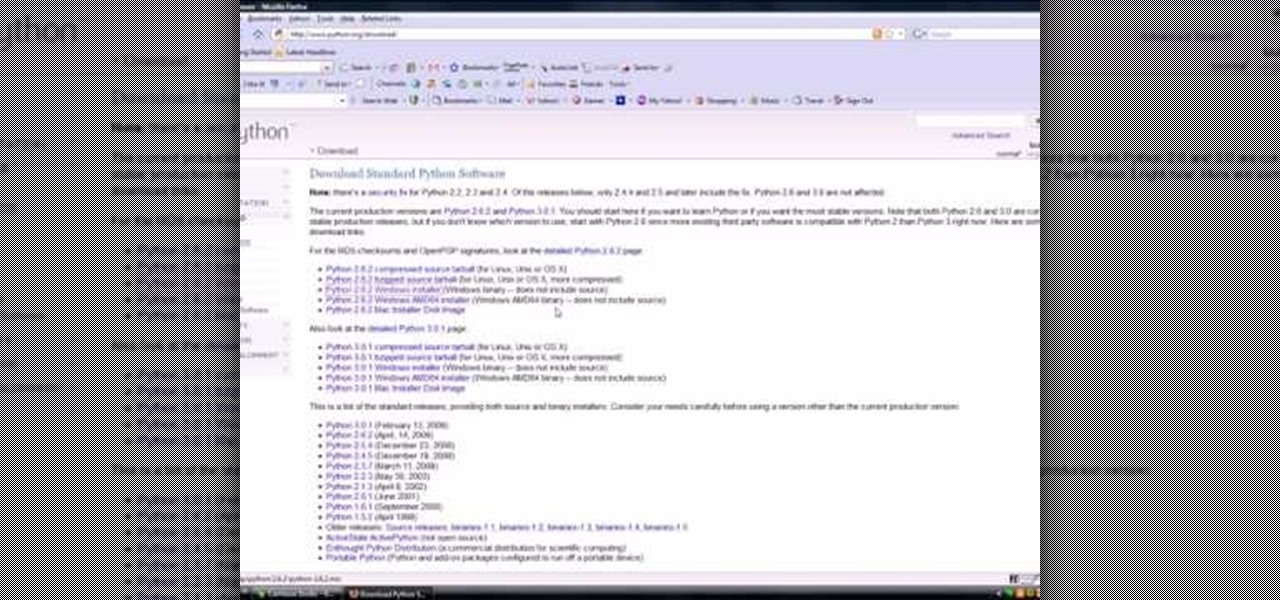
Bucky from The New Boston serves up this Python video tutorial on how to download and install Python. This is the program you use to write all of your Python code down.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to backup Wii games to SD to play in HD.

With the help of a program called TItunes & standard earbuds (and adapter) we can listen to music played by a TI84! Mod you calculator to play music. This only works on a TI84, not a TI83.

One day, your car may break down and you won't be able to afford to hire a mechanic, so what do you do... you look on the web for some how-to vehicle repair videos and become your own car mechanic, that's what. You don't need any advanced training to perform repairs and simple maintenance on your automobile, but you may need a few tools. Invest in the basic tools and you'll be prepared for just about any car malfunction you can think of. These tutorials will help get you on your way, as long ...

Studying to be a nurse? Then here is a nursing how-to video that teaches you how to do a central venous access. Every nurse should know the basics of this technique, follow along and see how easy it is to draw blood from a central line. These medical tips are sure to help you pass your nursing exam with flying colors. Remember when performing a central venous access, all caps must be replaced each time blood is drawn. You must swab the port for 1 min prior to withdrawal. Follow your hospital'...

This is a video tutorial on how to make a USB aquarium powered by a under-gravel LED bulb that is powered by a USB port. With a bit of simple engineering, build a circuit to provide elegant lighting to your aquarium. Connect the wiring to the air pump for a cool lighted bubble effect. Plus, it's powered by your computer! Don't use expensive fish, or those which are sensitive to DC Currents. Don't do this project in a saline water tank, because salt conducts more electricity.

This travel tutorial video explains the visa procedure for a tourist visa into Ghana. The process is simple. Visa costs include the following:

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Tired of squinting over your laptop? There are several ways to turn a big-screen TV into your new computer monitor and enjoy video games, web content, and photos like never before.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

In this video from iPT2gGeec we learn how to control an iPhone from your computer. You need a jailbroken iPhone to do this and use a program called Veency. Open Cydia. Search for Veency. Install it. That is all you need to do with your iPhone.

Coming soon to an Android device near you: Diminished Reality! What's Diminished Reality? A lot like Augmented Reality, really, but with one big difference: Where AR giveth, insinuating virtual elements into a live representation of the real world, Diminished Reality taketh away, hiding actually-existing objects within a live feed.

If you're sick and tired of you laptop dying all the time, then the answer may be right in front of you— power management. In Windows 7, it's easy to control your power settings to help you laptop's battery last longer. Watch and learn from none other than Microsoft.

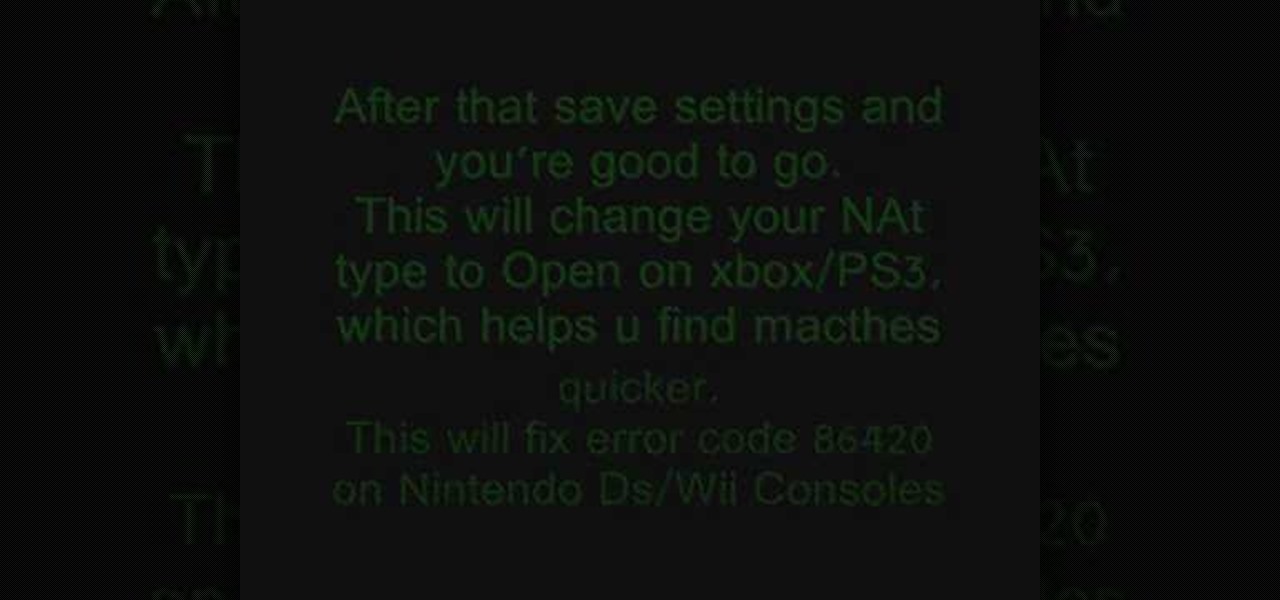
In this tutorial, we learn how to fix error code 86420 and change your NAT type to open. First, go to the website to change the settings for your Linksys router. Next, go to the applications tab that says "applications and gaming". After this, go to port range forwarding, then write in a name next to where it says "application name". Under "start" write the number 1 and under "end" write 6553, then keep "both" marked under protocol. Next, enter in the last 3 digits of your console's IP addres...

In this tutorial, we learn how to set up a Wi-Fi network with a Linksys router. First, go to your cable modem and remove the yellow Ethernet cable. After this, plug the Ethernet cable into the very first port of the router and plug the other end into your computer. After this, connect any other electronics you have with cables, then plug the router into the wall to give it power. Next, turn the power to the modem and router back on. When finished, you should see a new Wi-Fi network appear in ...

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

A modern iPhone is capable of running sophisticated, exquisitely-rendered games that rival titles on current-generation consoles. However, there is some value in classic video game titles, whether you grew up playing games on the Atari 2600, Nintendo Entertainment System, and Sega Genesis or not.

For anyone interested in using cheap, Wi-Fi-connected microcontrollers like the ESP8266, the Arduino programming language can be a barrier to entry. Based on C++, Arduino requires knowledge of more computer science than languages like Python. Fortunately for beginners, setting up MicroPython on an ESP8266 allows anyone to write Python on affordable microcontrollers in a matter of minutes.

The Files app received a big update in iOS 13. Before, it was limited to local and cloud-based files, but now you can access data from external storage devices, including SD cards and USB drives. But before you try to connect your favorite card or drive to your iPhone, there are a few things you need to know.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

A while back, we told you about NoChromo, a no-root ad-blocking browser based on Google Chrome's open source code base, Chromium. That browser was wildly successful, as it offered an identical interface to regular Chrome, but without any ads. Sadly, the developer abandoned NoChromo, but a new ad-blocking Chromium port called Bromite has been released to fill its void.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.