
How To: Networking Basics for the Aspiring Hacker, Part One: IP Addresses
Recently, there have been some questions regarding networking popping up and we have decided to put together this series to try and cover this gap.


Recently, there have been some questions regarding networking popping up and we have decided to put together this series to try and cover this gap.

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.
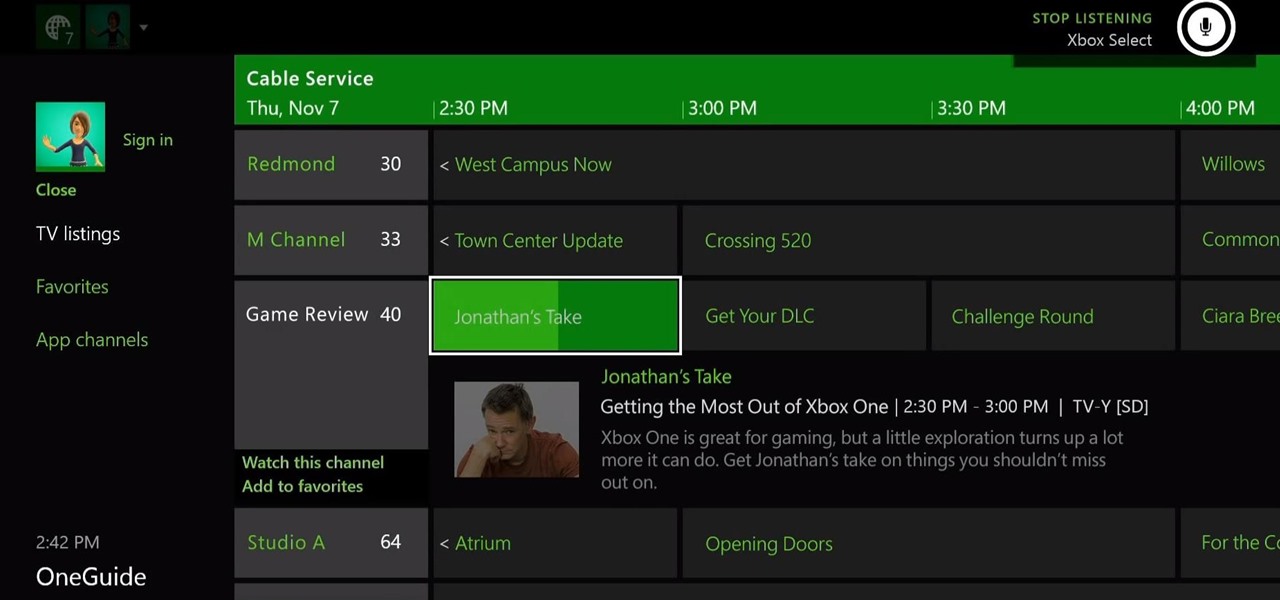
The Xbox One is the quintessential jack of all trades. It can be your browser, music player, gaming system, and cable box, but in order to benefit from all of these goodies, you're going to have to set it all up.
With CyanogenMod 10.2 recently released and the Samsung Galaxy S4 still waiting on Android 4.3, it only makes sense that the coveted features from both firmwares are highly desired by Android owners all over. We've already brought you a feature from each firmware—the cLock home/lock screen widget from CyanogenMod and the Google Play Edition Camera and Gallery from Android 4.3. Now we're bringing you another in the form of an updated text messaging application, ported from both Android 4.3 and...

PRL, or Preferred Roaming List, basically tells your phone which towers to connect to first. Changing PRLs can improve reception and data speeds, and in some cases even give you access to corporate/test towers.

It's no secret that most people who got an iPhone 5 (or upgraded their old iPhone to iOS 6) have been sorely disappointed with Apple Maps. We may all miss Google Maps, but the Google says they aren't even working on an app for iOS 6 yet. Even worse, Google exec Eric Schmidt says they're waiting on an invitation from Apple, and if we know Apple, that could be a while. Users who didn't get an iPhone 5 have had an even worse time of things—Apple disabled 3D maps and turn-by-turn directions on ol...

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.
While the Galaxy S10 is a beautiful phone, its software isn't for everyone. One UI makes huge strides toward undoing the mess known as TouchWiz, but for purists, it's still not quite on par with stock Android. Fortunately, the beauty of Android is you can change this with a few apps.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

For years, PuTTy has reigned supreme as the way to establish a Secure Shell (SSH) connection. However, those days are numbered with the addition of the OpenSSH server and client in the Windows 10 Fall Creators Update, which brings Windows up to par with macOS and Linux's ability to use SSH natively.

Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a simple cable. If you don't have a power source, you can also power your Linux distro over the cable at the same time.

Clumsiness is the great equalizer when it comes to smartphones — it makes no distinction between the most expensive flagship handset and cheaper mid-range models. A hard drop onto pavement will usually result in a shattered screen, regardless of how pricey your device is. And with a smartphone breaking every two seconds, we're truly our own handset's ultimate nemesis.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

I had the opportunity to speak with the COO of Osterhout Design Group, Pete Jameson, shortly before the announcement of the company's R-8 and R-9 smartglasses models at CES in January. And while I sadly could not make it to CES to test the smart specs out right away, ODG invited me to do just that while I was in San Francisco for the Game Developers Conference.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

When attempting to gain access to a server, there may come a point when you need to get around file upload restrictions to upload something. If we can find a way to get around the restrictions, then we can upload anything we want to the server, effectively compromising it. That is what we'll be doing here today, so let's get started!

Learn how to port forward on the GT724WGR Wireless DSL Modem. You'll see the easy steps on how to enable BASIC port forwarding on the GT724WGR Wireless DSL Modem from Actiontec Electronics.
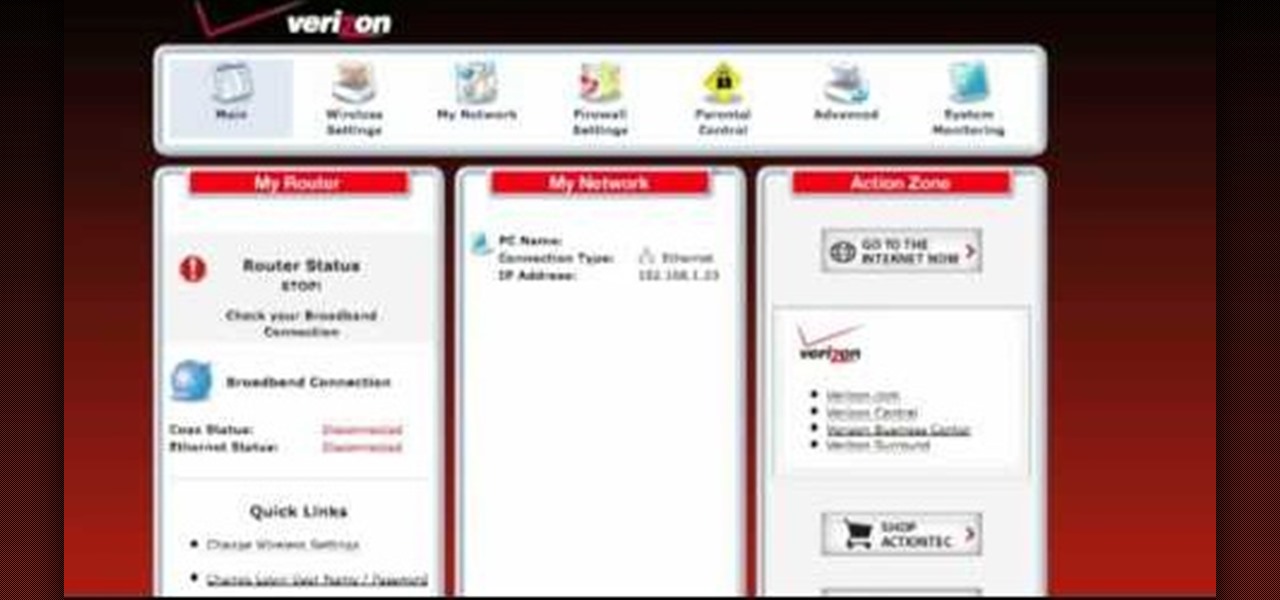
This video explains how to set up port forwarding on the Verizon MI424WR router. See how to setup basic port forwarding for a Verizon FiOS Router.

This video will explain how to set up advanced port forwarding on the Verizon MI424WR router. See how to configure advanced port forwarding on a MI424WR Router.

This scooter engine modification tutorial gives you some tips on tools and methods for making the cylinder ports smoother in a Honda Elite DIO scooter engine. If you are modifying your scooter engine or doing major engine customization, you may want to port the cylinders as shown in this video.
Okay, just because the new Verizon Wireless Droid X comes with an HDMI-out port doesn't mean you're limited to just that. Motorola has made it possible for you to play video, music, and pictures to your television without any wires at all. With the Droid X's DLNA media sharing application, you can easily stream to an PS3 or Xbox, send pics to your PC, and stream videos to your TV. Check out this video walkthrough to learn how to use the DLNA services to connect your Droid X to the PlayStation 3!

Breathing oxygen is an extremely important component of staying alive, right? Well, the same goes for running. If you're not breathing properly, you're running is going to suffer.

In this "super" video tutorial, you'll learn how to convert a Super Nintendo controller to PC controller. Now, dig deep into your garage and pull out those old SNES pads (or controllers) and get ready for some "super" modding!

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

When you want to post a breathtaking landscape or picture-perfect portrait that you just took with your DSLR camera to Instagram, Facebook, or some other social platform, there's an easy way to do so — even if you don't have a computer handy, which is typical when you're out and about.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house.

This how to video is a step by step demonstration on how to make a delicious raisin pie with port wine.

In this Cooking With Kai video, we learn how to make Thai Drunken Noodles. Add 2 TBSP. of cooking oil to coat the bottom of a fry pan. When oil is hot, add 1 clove of garlic and shallot and stir for about 10 seconds. Add 1/4 lb. ground port, beef, chicken or shrimp and stir together for about 2-3 minutes, until done.
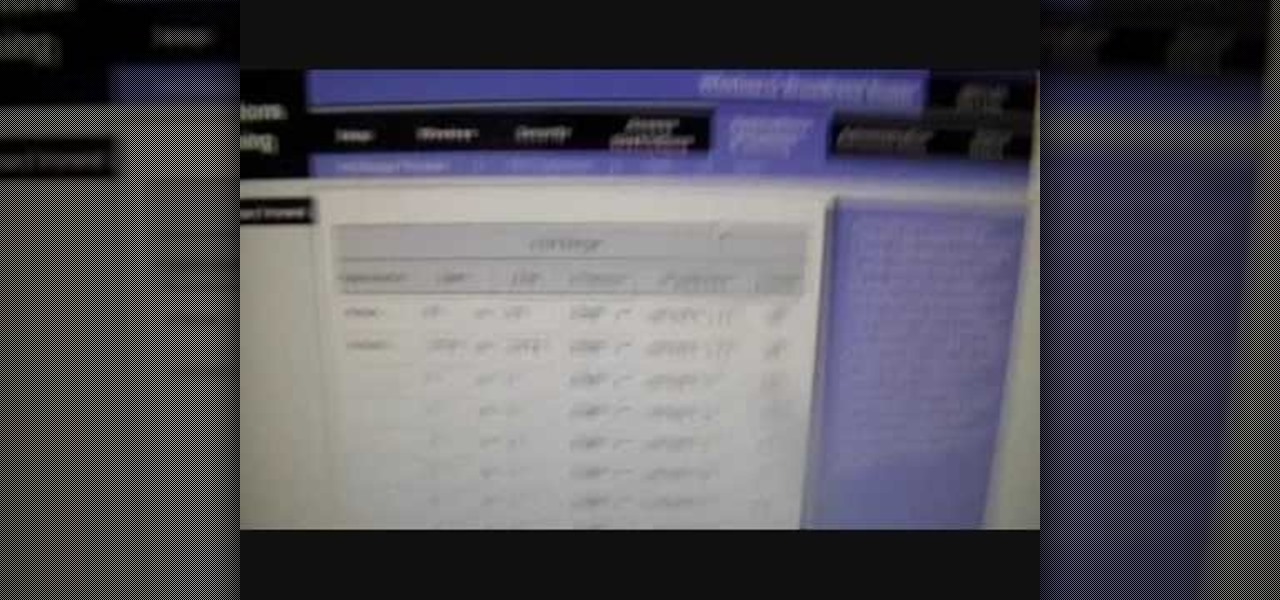
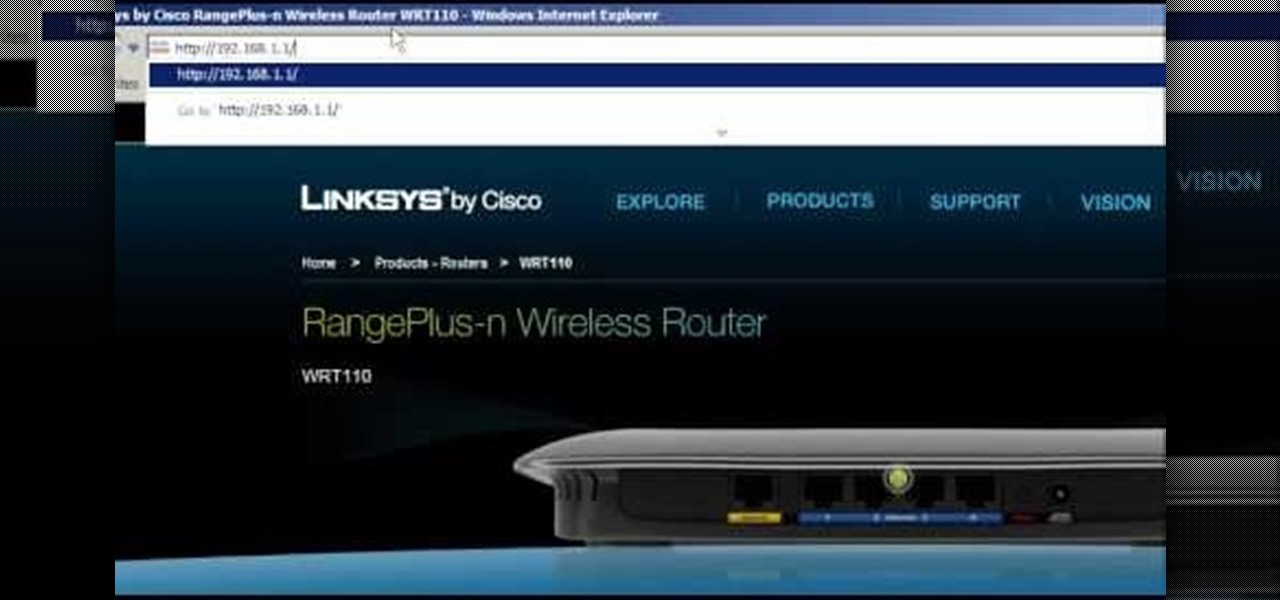
This is a Computers & Programming video tutorial where you will learn how to change your NAT to OPEN with a Linksys router. Go to your browser and type in 192. 168. 1. 1 and that will take you to the basic set up. The authentication dialog box comes up. Type in ‘admin’ for the username as well as the password. These are default settings. In the Linksys page, go to ‘applications and gaming’ and on the Port Range page fed in these information. Your application you can name anything. Start 80, E...
Wrestling with the whys are wherefores of WiFi? Can't figure out how to secure your network? Take heart: This remarkably thorough, seven-part home networking tutorial will get you up and running faster than you can say `Wireless G.'
Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Whether you're trying to become an influencer or just want to share better photos and videos, the best camera to start with is your smartphone. It is likely the only camera you always have on you and it's probably capable of excellent pictures and video capture. But with a little help, it could definitely be better.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

When shooting video on your phone, you have two cameras at your disposal, the rear camera and the selfie camera, and you can switch freely between the two. As for microphones, you may have more than one but, unlike with the cameras, it's not easy to switch between them. Filmic Pro solves this problem by isolating the mics so you can choose the best option for the audio track.