As a lover of food, I'm often asked, “If you could only have one food the rest of your life, what would it be?” My answer is always the same: sourdough bread. (Okay, it's not always the same... I usually cheat and say sourdough, fancy cheese, and a good beer.) Admittedly, I'm biased by my own sentimentality. My mother is an expert bread baker, with a major in making sourdough. Her sourdough starter is older than I am, and in all honesty, she's made thousands of loaves, each better than the ne...

It's never too early to start planning for the best holiday of the year, right? We've already shown you how to make chillingly creepy cocktails, shrunken heads out of apples and potatoes, and a slew of DIY costumes, whether you want to go as Groot or an emoji. Now it's time to think about the most important part of any good Halloween party: the food. If you need inspiration for some spookily tasty Halloween hors d'oeuvres, just read on.

Eating healthy poses a challenge nowadays with so many options that taste great but aren't really good for you. Nutritionists have made it their life's work to understand what actually does a body good. Here's how you can follow their example.

Just like Leslie Knope, I love waffles. Unlike that imaginary character, I don't require that my waffles come from JJ's Diner. I have a deep affinity for frozen waffles as well as the homemade ones. They're so convenient! A few moments in the toaster, and you have a great foundation for a sweet or savory topping, or just a big fat slab of butter and a little syrup. Turns out there's a great big world of frozen waffle innovation out there that I had never dreamed existed. And remember, frozen ...

One of my favorite things is finding an easy way to make what is normally a complex dish. Case in point: pasta sauce. Usually its depth of flavor is the result of fresh herbs, shallots, tomatoes, seasonings, olive oil, and a touch of dairy being cooked and added in stages. Long simmering mellows out each component's inherent character and turns pasta sauce into something that is far greater than the sum of its parts.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

One feature of Samsung devices that's less useful than I had expected is S Voice, the voice assistant that ships with all new Galaxy devices. The voice is annoying, the features are lacking, and it's an all around subpar product. With Google Now, Siri, and now Microsoft's Cortana, Samsung needs to really step up their game—even on the new Galaxy S5.

Most recipes don't specify what type they mean when they call for onions. While using whatever kind you already have won't necessarily ruin a dish, using the best one for what you're cooking will definitely make your food taste better.

Welcome back My sleepless army of young hackers, Everyone uses internet, right? So for this tutorial, i'll start with the basics and slowly we'll get to the UPD Protocol.

Following the Dalton incident, the stripper deck rapidly fell out of favor with poker cheats, but remains popular to this day with magicians. The deck looks perfectly normal but has tapered edges on all the cards. The goal of the magician in using a stripped deck is to have a person choose a card, then replace it in the deck facing the opposite direction, so that the tapered or stripped edge of the card stands out from the smooth edge of all the other cards.

One of the oldest electronic musical instruments is the theremin, a synthesizer that generates sound based on hand gestures, as featured in the classic "Good Vibrations" by the Beach Boys.

If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed.

There's something extremely satisfying about hunting down your online adversaries and knocking them out with a well-placed shot, which probably explains why shooting games are still one some of the most popular time killers for iOS and Android.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

When hacking Wi-Fi networks, having the right wireless adapter is essential. But hunting online for one can be a frustrating experience. To see how the handful of Kali-compatible adapters on the market measure up, I ran a series of tests to benchmark and compare their range, signal strength, and ability to enter monitor mode and perform packet injection. This should help you determine which adapter is right for your own hacking needs.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

There are all kinds of theories—many supported by science—about what causes Alzheimer's disease. Tangles of protein called ß-amyloid (pronounced beta amyloid) plaques are prominently on the list of possible causes or, at least, contributors. An emerging theory of the disease suggests that those plaques aren't the problem, but are actually our brains' defenders. They show up to help fight an infection, and decades later, they become the problem.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.
Welcome back Hackers\Newbies!

Samsung has just announced the Galaxy Note 10 and 10+. These are the latest and greatest from the largest smartphone OEM in the world. Plenty of numbers and specs have been thrown your way to showcase how good the Galaxy Note 10 is, but we wanted to simplify all this for you and key in on the most important things.

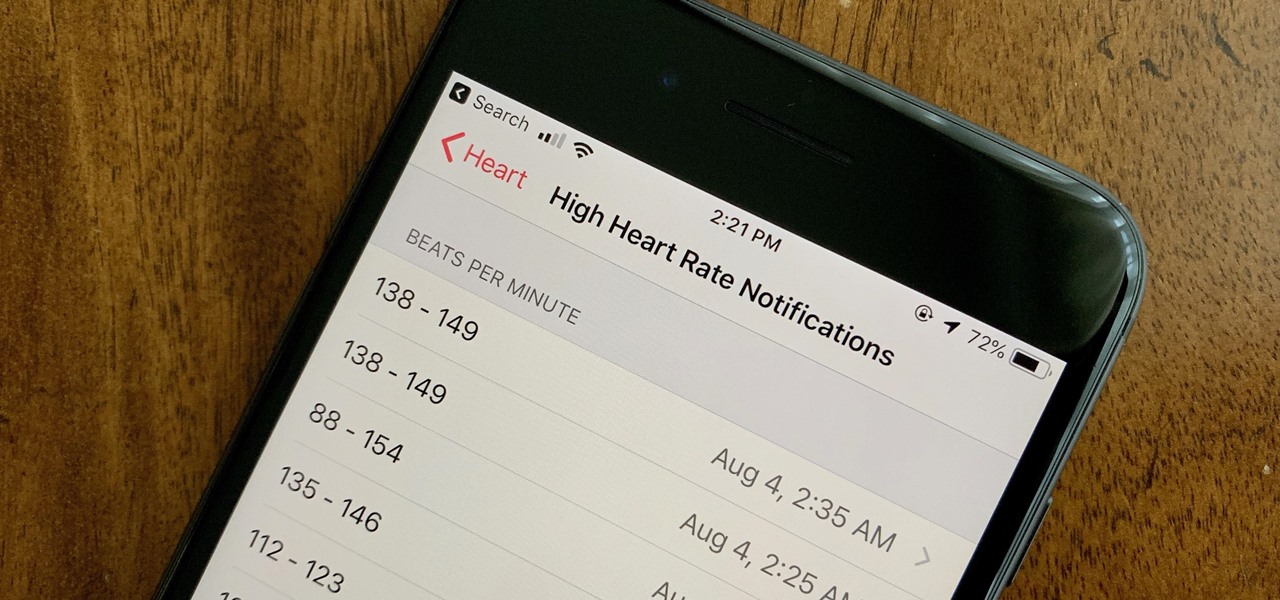
Your Apple Watch sends you notifications from friends, family, and the apps that are important to you. Occasionally, however, the watch may scare the heck out of you with a notification warning of an abnormal, elevated heart rate. If you have no history of heart conditions, this alert might come as a shock. Why do you have a high heart rate, and what are you to do with the information?

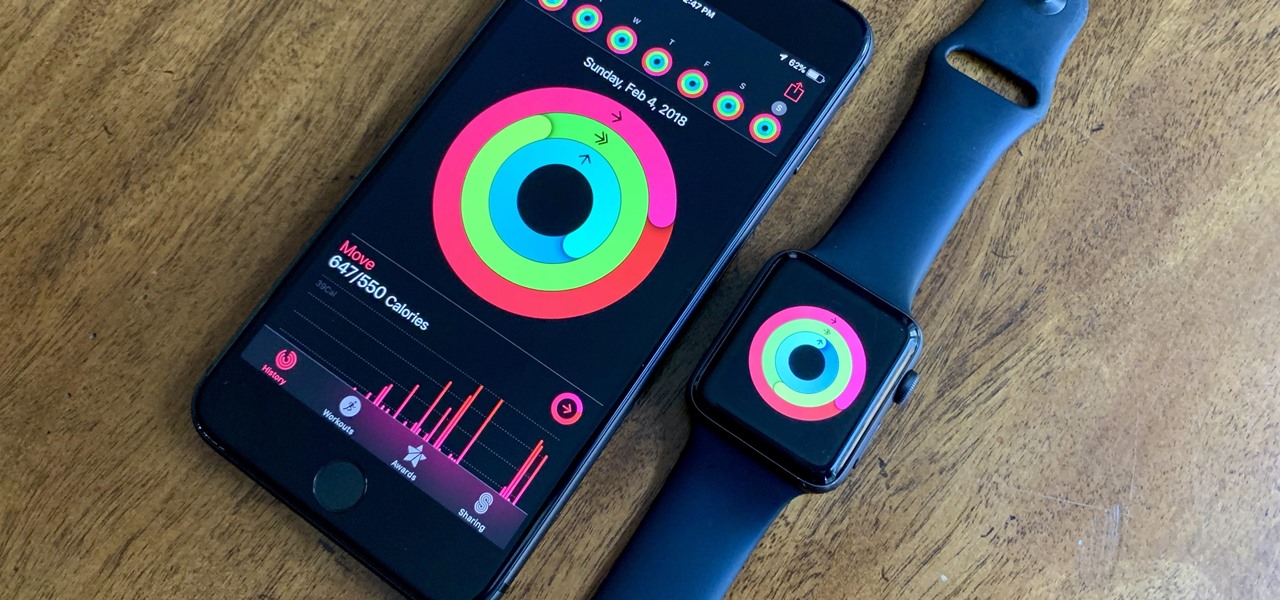
Apple Watch owners know the struggle — it's the end of the day, and those rings aren't met. Whether you forgot your watch before hitting the gym, let the battery run out, or just didn't move enough, you could feel the sting of fitness failure. But it doesn't have to be this way. You can actually close your Activity rings yourself; it just takes a little know-how.

One of the first steps in reconnaissance is determining the open ports on a system. Nmap is widely considered the undisputed king of port scanning, but certain situations call for different tools. Metasploit makes it easy to conduct port scanning from directly inside the framework, and we'll show you three types of port scans: TCP, SYN, and XMAS.

Continuing our series on building a dynamic user interface for the HoloLens, this guide will show how to rotate the objects that we already created and moved and scaled in previous lessons.

Every industry has its own jargon, acronyms, initializations, and terminology that serve as shorthand to make communication more efficient among veteran members of that particular space. But while handy for insiders, those same terms can often create a learning curve for novices entering a particular field. The same holds true for the augmented reality (also known as "AR") business.

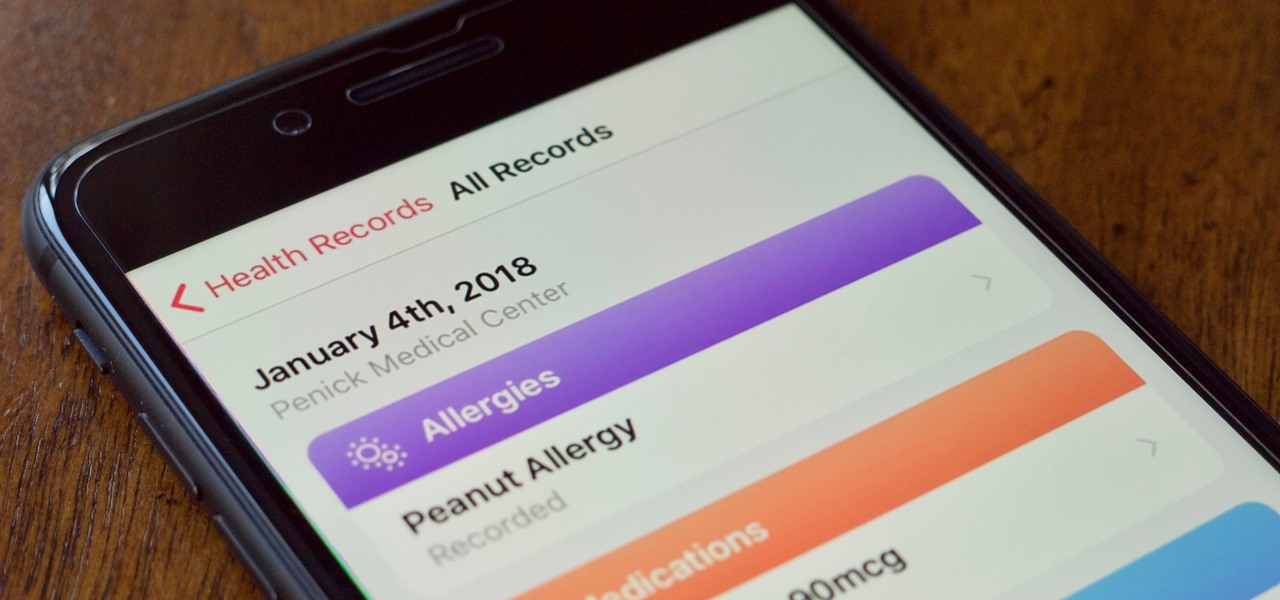
Mobile phones are not only essential for work and communication, they're quickly becoming an integral asset to our health. Your iPhone can store valuable data about fitness, nutrition, heart health, and so much more. And since iOS 11.3, your iPhone can even import a list of allergies, medications, immunizations, hospital visits, and other health information from your doctor or hospital.

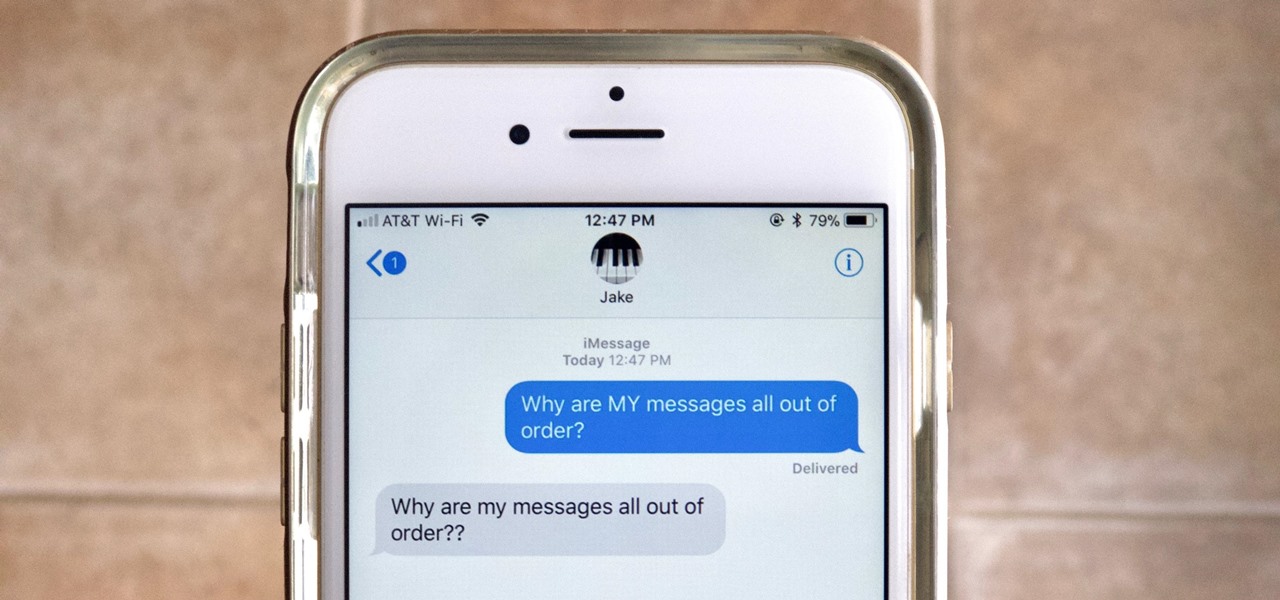
One of Apple's best products is iMessage, which allows for quick, creative, and free messaging between iOS and Mac devices. However, users are reporting that conversation threads in the Messages app are occasionally out of order, which is equal parts confusing and annoying. Luckily, we have some ideas on how to fix the problem.

Whether your palate runs to domestic or imported, a piece of cheese can be a real treat for the senses. Its smell, taste, and texture are all parts of its appeal. A big part of what makes that savory wonderfulness comes from the microbes in and on the cheese. Thanks to a team of researchers dedicated to studying those microbes, we have a better understanding of their importance to cheese and us.

It seems like everyone is getting in shape these days (or at least trying to improve their fitness), and as a result, there's an endless supply of fitness trackers and smartwatches hitting the market. This is all very wonderful, unless of course, you're broke and can barely afford a decent pair of running shoes.

Fast food is a guilty pleasure in which we all indulge. When you're short on time and long on hunger, being able to whiz through the drive-thru or run 'in and out' of a fast food joint can be a real lifesaver.

"It just ticked me off," he said. In March 2011, Neil Singh paid $50 to back the Hanfree iPad stand on Kickstarter. The project was funded at $35,000, but production stalled, and the delivery estimates kept getting pushed back.

Even if you haven't heard of ube (pronounced "OO-beh"), you've probably seen pictures of desserts made with this brilliant purple yam.

Biting into a perfectly ripened piece of fruit is enough to convince you to give up baked goods and plant your own garden. The combination of flavor, juice, and sweetness in a ripe mango, apple, plum, or berry is the stuff of life itself.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

Ever since the much-lauded effects of the Mediterranean diet became widely known, people have been buying olive oil by the gallon. A diet that prevents heart disease, is based on fresh, seasonal foods, and includes a tasty as hell fat like olive oil? Duh—that's a no-brainer.

It's easy to take the food we eat for granted, but the truth is, there are a lot of bizarre, wonderful, and just plain weird things about what we eat and drink, the effects it has on our bodies, and vice-versa. Read on to learn how bugs provide food dye, the Japanese grow square watermelons, and more.

Glow sticks, a popular favor at parties and outdoor events, and a must-have on Halloween, can be traced back to the United States Navy in the mid-1960s. The military desired improved visibility during night operations, and glow sticks, with their small-size portability and lack of batteries, were a perfect tactical solution.

These days, you can find a digital version of almost any form of entertainment. Being able to download or stream content is convenient for a lot of reasons—you can avoid going to the store and you never have to worry about late fees on rentals.

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.