Helping to prove that science is way awesome, an 18-year old electrical engineering student has successfully made a light bulb float. His name is Chris Rieger, and he's been working on his "LevLight" project for about six months now, with pretty amazing results. This feat of ingenuity was accomplished by using magnetic levitation, although that over-simplification masks how considerably difficult this undertaking was.

Cameras can be pretty pricey, but this one only costs a buck, though it's pretty limited in its functionality. That's because it's no ordinary camera, but an origami one made using nothing but a dollar bill.

Step1. Make sure you get your facts straight. Note down the dates, names, and numbers, what was said etc while talking over the phone. It is also essential that when you present your letter of complaint that it is chalked full of facts so that when it reaches a decision maker you may get justice properly. Do not write a novel that is 30 pages. Keep it short and write in bullets. Remember that they are interested in facts only.
This is a very lengthy explanation on BTD playing. There's a lot to actually know about the strategy of Bloons Tower Defense.

Check out this video tutorial on how to make cheap dragon wings, controlled by body posture. You can do this project for $18 if you use plastic garbage bags and Scotch tape for the membranes. You'll see how to make very light and strong costume wings. How strong? That strong.

No one wants or needs a flat tire. If you do get one, however, don't get all flustered — changing a tire is as easy as buying groceries or going to the gym.

If you have a Jtagged XBox 360, the sky is really the limit as far as what you can do with it. This video will teach you how to install Xexmenu, a custom dashboard application, and an FTP client your XBox 360, allowing you to do all sorts of nefarious things.

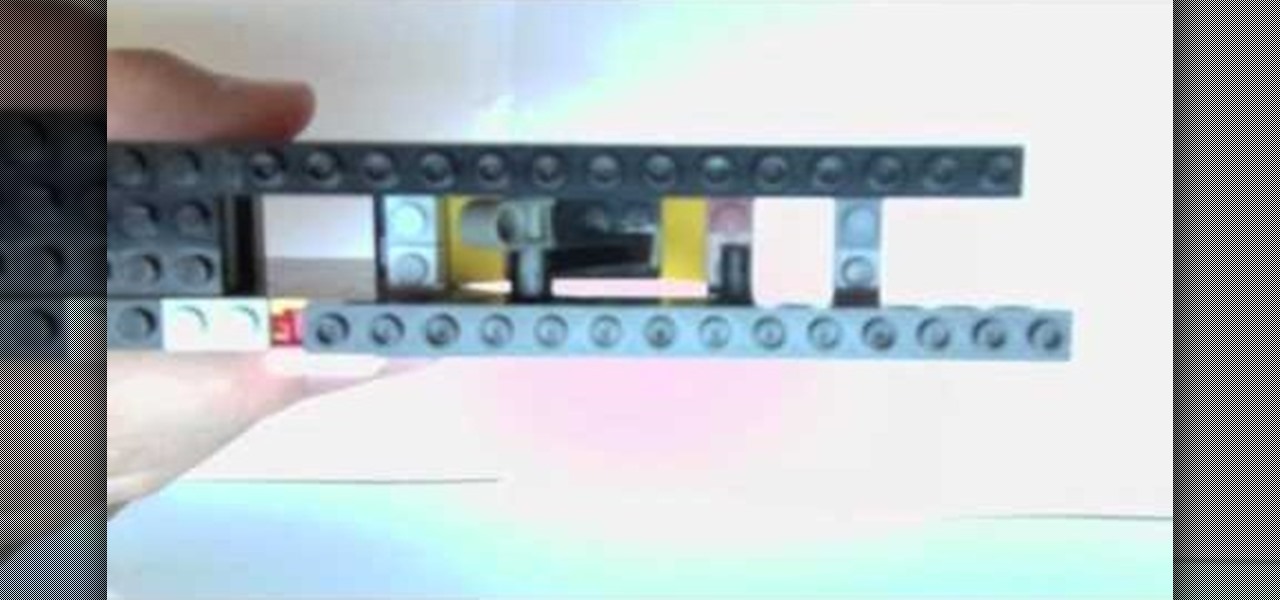
There is truly no limit to what you can make with Lego blocks. This video is a step-by-step pictorial demonstration of how to make a replica of a Glock 18c pistol (a fully automatic version at that) that will shoot rubber bands. Make sure you already have some freestyle Lego skills, as the video moves pretty fast and has no audio, but the final product looks very polished and should help you annoy your friends and siblings for years to come!

We all love the relaxing quality and lovely smell a burning candle adds to a room but it is frustrating when candles burn through too quickly. By taking into consideration the placement and properly prepping the candle you’ll give it a longer life.

Learn how to make your videos well under the 100mb limit using virtual dub and learn to break the video into pieces if the video is much too long. Learn from the master of humdrum tutorials!

Watch this video to learn how to stud your leather jacket. See the finished product in chapter two. Also, learn how to get 100 studs for free from studsandspikes.com (for a limited time)!

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.

We are now in the age of 5G. Carriers worldwide are upgrading their networks to the newest standard for mobile, which will dramatically improve your phone experience. How? By giving it download speeds and latency that surpass Wi-Fi. But before you upgrade, there are few things you should know first.

We're glued to the news now more than ever, but our "free press" isn't necessarily free of charge. Cable news outlets like CNN and MSNBC are locked behind expensive cable TV packages and cord-cutting streaming subscriptions such as Sling TV and Hulu + Live TV. Luckily, there are plenty of alternatives to get your TV news fix, free of any payment, account, or commitment.

When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you even more protection against online threats.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

The Files app received a big update in iOS 13. Before, it was limited to local and cloud-based files, but now you can access data from external storage devices, including SD cards and USB drives. But before you try to connect your favorite card or drive to your iPhone, there are a few things you need to know.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

While photography usually gets all the love, our phones have gotten really good at capturing video. Think about it — when was the last time you needed a camcorder for a vacation? With mobile cameras getting better each year, we're now at a point where smartphones can be used for pro-level videography.

After reviewing the international plans for major US wireless carriers, it became obvious they're all pretty bad. Your data is heavily restricted, requiring a daily fee which can cost an extra $100+ on a seven-day vacation. That's when I learned about Google Fi, and how for most travelers, it's the best option.

With the best selling phone on Amazon in 2018, Lenovo had big shoes to fill when making the successor of the Moto G6. Fortunately, Lenovo was up to the task. The Moto G7 continues to provide a high performance-to-price ratio, offering a worthwhile upgrade for G6 users while remaining budget friendly.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

It's that time of year again. No, not Thanksgiving. Black Friday. There are a lot deals available this holiday weekend, many of which include flagship Android devices. Whether you are thinking of buying a phone for yourself or looking for a gift for someone else, you can find a little savings to shop smart during the holidays.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

Battery drain is a major pain point for Android users, though that promises to change thanks to Android Pie's new Adaptive Battery feature. But Google hasn't said much about the inner workings of this feature, only publicly stating that it uses AI to boost battery life. So we dug in to find out what's really going on under the hood.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

For most carriers, "unlimited" data plans aren't really unlimited, and they still cost more than data limited plans. So while subscribing to music streaming services and storing your own music library in the cloud may be more convenient, it may eat your data up like candy. To keep that from happening, try downloading tracks from Apple Music for offline playback.

Before you go ahead and delete your Facebook — don't lie, you've been thinking about it — consider this. Facebook offers users a wide variety of privacy options to mess with, which can help you find a little control over your information. We're not saying this solves Facebook's privacy crisis, but it might be a more reasonable option than throwing in the towel entirely.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Hulu used to be simple — just a site with all the latest clips and episodes from your favorite shows. Watch some ads, watch some free TV. Easy, right? Not so much anymore. Hulu is no longer free, and on top of that, offers different pricing plans and add-ons.

I've been a diehard Chrome user since its inception, and even more so since Android was released. The ability to sync bookmarks, passwords, and web history across all of my devices made the switch a no-brainer, but what really made me fall in love was the amount of extensions available for it.

It seems like custom Google Now commands are a dime a dozen these days. With Commandr for Google Now giving non-rooted users their first taste of custom voice commands just a couple weeks ago, you may wonder why we're covering this subject again.

There's definitely a lot of new things to get used to in iOS 6, with over 200 added features, but which ones stand out about the rest? Well, it all depends on what device you're using. Some features will only work on newer models, but most of the hidden features are accessible to all.

Ten verses are in this level of the Xbox 360 game Bayonetta. In Chapter 9 - Paradiso - A Remembrance of Time, get ready to fight Golem. From the floating clock face you can jump to the yellow floating disk. Follow the path of floating objects to the floating courtyard garden.

Learn how to choose an indoor plant. You don’t need a green thumb to have houseplants that flourish; you just need to know which ones will thrive in your home.

Watch this video tutorial to learn how to pick up a girl at a stoplight. Tired of the dating scene? Try meeting someone at a stoplight. If you don’t get arrested for stalking, you just might get a date.

Learn how to do single medicine ball on the shelf crunches. Presented by Real Jock Gay Fitness Health & Life.

This is a cheap way to Keep your desk organized, especially if you have so many things and your space is limited. Find out how by watching this video. A simple dish rack is a great storage unit, as well as a way to dry out your dishes. Watch this video housekeeping tutorial and learn how to keep a desk organized.

For those doll makers out there who want to expand into the art show and markets scene, sculpting one of a kind pieces may be too time consuming. This video will hopefully help these artists will to stretch their expertise into making limited edition dolls. Watch this video doll-making tutorial and learn how to sculpt a push mold doll out of polymer clay.