For the longest time, Instagram didn't have a native collage feature. If you wanted to post a story with an assortment of photos, you'd need to use the company's Layout app or a third-party collage maker. Thankfully, that is no longer the case since Instagram now bakes Layout directly into the story camera.

WhatsApp is the go-to messaging app for millions worldwide and its easy to see why. The app can be considered the Swiss Army Knife of texting thanks to numerous features like Group Chats and Status Stories, in addition to striking a great balance between ease of access and overall security.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

If preorder delays are any indication, the iPhone X certainly has some buzz. But does the X have the quality to support that buzz in the long run? After all, a $1,000 (or more) iPhone feels more like an investment than a smartphone purchase. The question on any prospective buyer's mind should be, "Is this thing worth it?"

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

I don't know about you, but I'm tired of hearing some of the same old jargon from people online who claim that all you need to make it on Instagram is to take good pictures and post consistently. Yes, for sure, but do you really think it's that easy?

Every year, tech companies use April 1st as a means to prove that they have a sense of humor. Sometimes their jokes are good for a chuckle, other times the gags backfire disastrously. For the most part, however, we'd be better off without the bulk of these annual antics.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Instagram introduced Photo Maps back in 2012, a feature allowing users to showcase where they've taken photos and explore where others have been, all through an interactive map.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

This year, like every year before it, Black Friday sales are starting earlier than ever. A lot of stores will be opening their doors as early as 5pm on Thanksgiving to get a head start on the madness (and it really is madness). As we've discussed in the past, one of the keys to emerging victorious on Black Friday is to plan, plan, plan. So, we've compiled some of the best deals in tech, gadgets and appliances to help you prepare for battle.

Below are the official rules and guidelines for submitting content to WonderHowTo. Please look over them before publishing any articles. Ignoring the rules could result in deletion of your article or being flagged as a spammer. Most of these rules apply to comments as well.

This 3D software modeling tutorial series shows you step by step how to create a suitable model for Google Earth within SketchUp. The series will start by showing you how to export data from Google Earth to use for reference, how to build and optimize the modle, texture it in Photoshop or Picasa and export and load it to Google Earth.

In this Disaster Preparation video tutorial you will learn how to make a candy stripe bar. The candy stripe bar is a slick way to create a strap of slanted lines. One of the many tying techniques used to create friendship bracelets, the bar can be modified to create stripes meeting at an angle. The line used in the video is a 450 test, 1/8” nylon parachute cord. To attach the cords to the ring, hang the ring on a hook, take two different colored cords and tie the cow hitch. For this, pass a...

Safety is important. If you are going to be riding a bike at night, make sure you are wearing light colored clothing and that you have lights. Lights help cars and other cyclists see you in the dark so you stay safe.

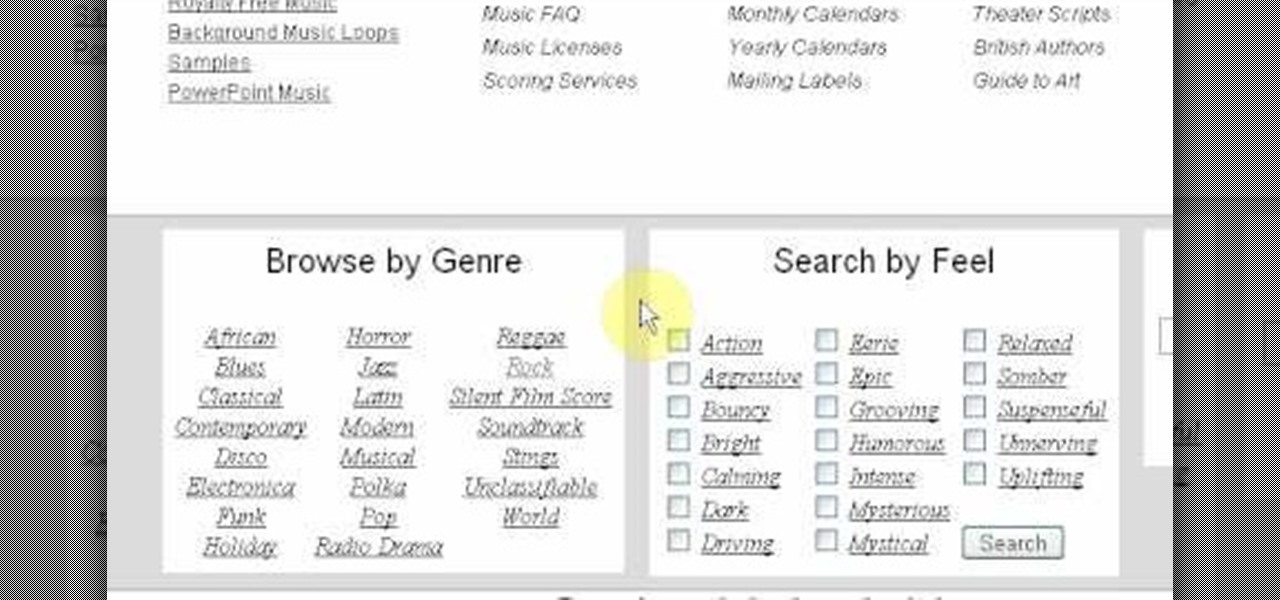
Insert music into your videos knowing that the music won't be removed when posted due to copyright issues. Go to incompetech.com/m/c/royalty-free and you will be able to find a massive collection of royalty free music that you can use to your heart's content with having to worry. There is music from many genres such as Jazz or Modern. Songs can previewed before you download them to find out if it is worth the effort to download it. These songs can be used as many times as needed unless an att...

Watch to learn how to replace the HEPA filter on a Dyson DC04 upright cleaner. You'll remove and replace the Pre Motor Filter and the Post Motor HEPA Filter on a Dyson DC04 vacuum cleaner. It is important to change the filter regularly as part of regular vacuum maintenance and to prevent loss of suction.

Watch to learn how to replace the HEPA filter on a Vax VEC04 vacuum cleaner. See how to remove and replace the central HEPA filter and the post motor anti-bacterial filter on a Vax VEC04 vacuum cleaner. It is important to change the filter as part of regular vacuum maintenance and to prevent loss of suction.

Although mainly demonstrational, this video shows you how to play "Tennessee Blues" on guitar. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your guitar learning:

Although mainly demonstrational, this video shows you how to play "Key to the Highway" on guitar. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your guitar learning:

Although mainly demonstrational, this video shows you how to play "The Little Beggarman" on the banjo. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your banjo learning:

Although mainly demonstrational, this video shows you how to play the "Fingerbuster" on guitar. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your guitar learning:

Although mainly demonstrational, this video shows you how to play a song "Summertime" in D minor on guitar. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your guitar learning:

Although mainly demonstrational, this video shows you how to play a song "The Japanese Sandman" on guitar. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your guitar learning:

Although mainly demonstrational, this video shows you how to play "Doctor Jazz" by Joe "King" Oliver on guitar. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your guitar learning:

Although mainly demonstrational, this video shows you how to play "Stealin'" by Will Shade on guitar. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your guitar learning:

Although mainly demonstrational, this video shows you how to play "Strolling Down the Highway" by Bert Jansch on guitar. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your guitar learning:

In this instructional video, our expert will explain and demonstrate a variety of BMX bike tricks. He will focus on quarter pipe and lip tricks, like the Disaster, Tail Tap, and Fufanu, giving step-by-step instructions for each and then performing the trick. You'll also learn how to do a Double Peg trick, and an Abubaca trick on your BMX bike. So grab your bike and get ready to ride, and as always, wear a helmet and follow proper safety instructions before trying any BMX bike trick.

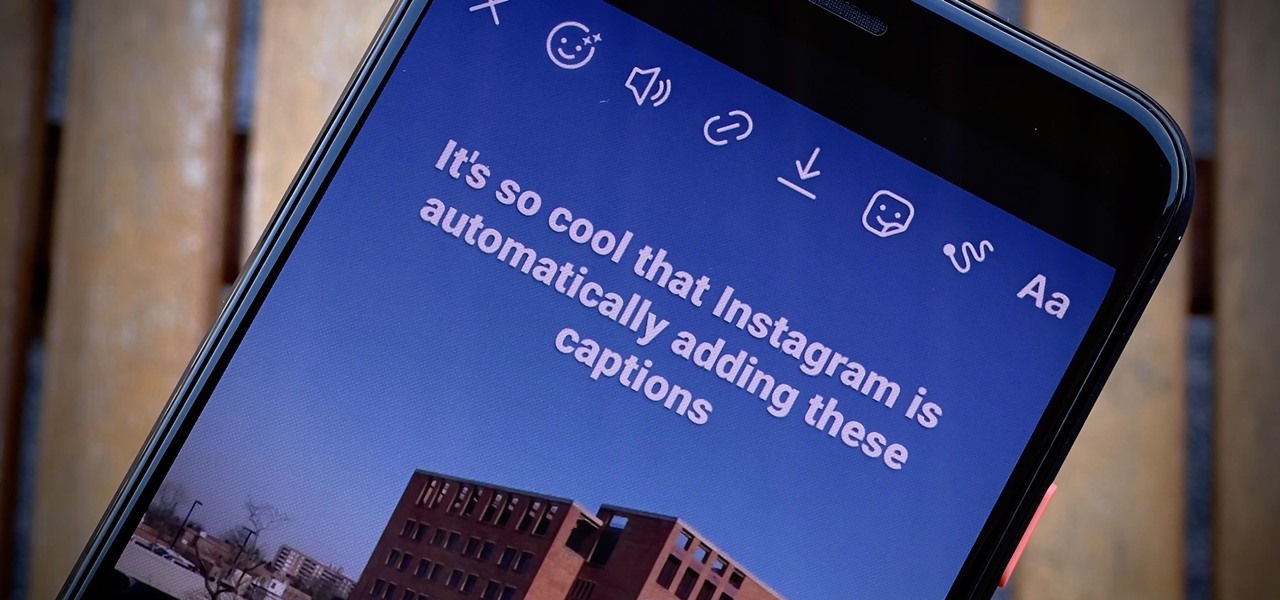
When creating video content for social media, such as a story on Instagram, it's common practice to add captions or subtitles to the post so that people can watch it wherever they are on silent. Doing this by hand is time-consuming and frustrating, but Instagram has a solution: a feature to add automatically-generated captions to any story you make from your iPhone or Android phone.

Anyone looking to have a complete set of design tools at their fingertips needs to look no further than Adobe's Creative Cloud. This suite of applications is the go-to platform for creative software and is, in many ways, a must-know in fields like graphic design, video editing, and photography.

As soon as you try recording a video in the Camera app on your iPhone, any music playing on your device comes to a halt. Apple Music. Spotify. Pandora. Tidal. Deezer. No matter what you're listening to, as soon as you switch to "Video" in the Camera app, the music will stop. However, if you want background music in your movie files, there's a workaround to avoid having to add an audio track in post.

With Avatar, Facebook's personalized stickers for use on its social and messaging platforms, those who aren't on Facebook or have otherwise dumped the social network may feel left out.

Over the past few months, Google has prioritized the development of its video communications products as the demand for social distancing solutions continues to increase in response to the COVID-19 pandemic.

For the last three years, Apple has hosted its Worldwide Developers Conference at the San Jose Convention Center, but thanks to the COVID-19 pandemic, WWDC 2020 is now an online-only event. So what can you expect from the new virtual format and when and how can you watch the keynote and developer sessions?