Everybody wants to build an app, but no one wants to start it from scratch. Building a full-blown application — or any other digital product for that matter — from the ground up entails some tedious work, which is why frameworks exist. Django, a Python-based framework, happens to be one of the best

The frustration of searching for the perfect image can be overwhelming. Then there's the issue of copyrights: Can you use it? Do you have to give credit? Are you allowed to manipulate the image?

It is a scary time to be alive. As states start to ease back shelter-in-place restrictions, the new world you're entering is still unsafe. With a vaccine months away, your best bet is to follow CDC guidelines and use the tools at your disposal.

5G is undoubtedly the future of mobile networks, and there's a good chance your next phone will have it. But just like with 4G, as carriers race to get the best 5G coverage, the ones running behind are abusing marketing terms to make themselves seem further ahead than they actually are.

Snapchat popularized personalized stickers for social media and messaging with Bitmoji, followed by walled-garden versions from Apple with Memojis and Samsung with AR Emojis. Even Google has gotten into the game, integrating an emoji generator for Gboard.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

With many office workers in the US being asked to work from home if their job allows, Magic Leap's customary updates for the Lumin OS and Lumin SDK brings some help to keep distributed workforces connected.

Whether you call it the foot shake or foot dance, videos of people tapping their feet together have been and still are blowing up all over TikTok. If you want to get in on the action but can't follow along with all of the fast-paced TikToks, we'll slow it down a bit for you and a friend.

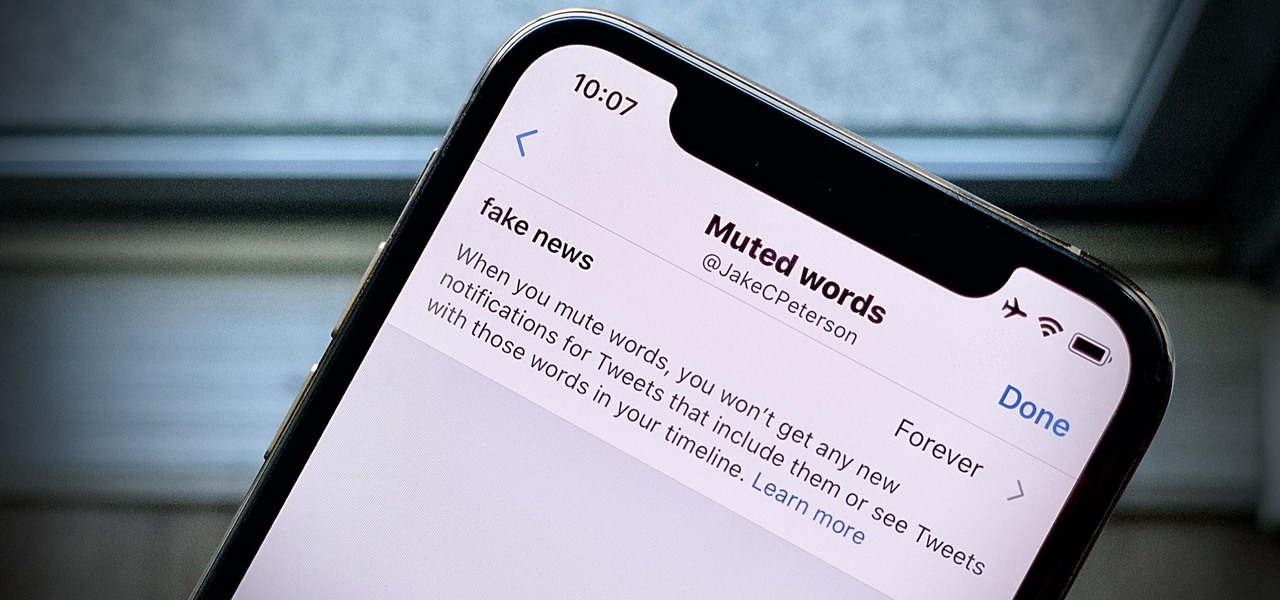
Twitter can be a wonderful place for people to express their emotions and chat with each other in brief. However, it can also be a breeding ground for hateful comments, foul language, and a whole lot of political talk.

If you don't want to be found on Twitter, there are several ways to do that without making your account private. For instance, you can choose an obscure username, omit your real name, or pick a random avatar. But there are lesser-known features deep in your settings that can also protect your privacy online, including preventing photo tags.

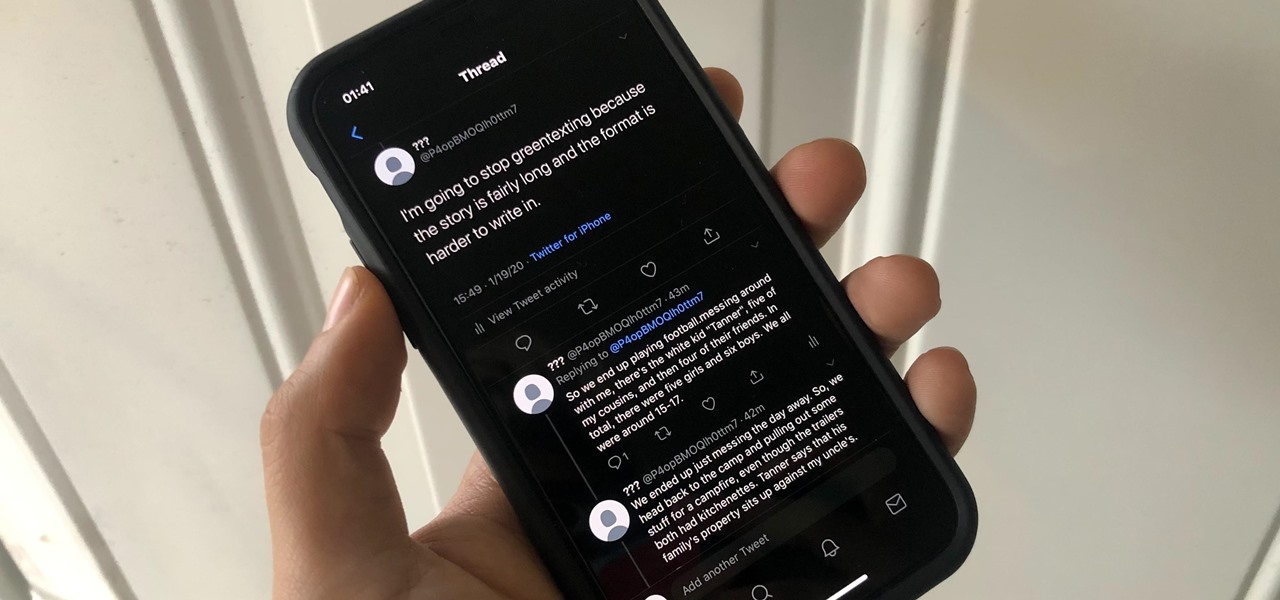
The 280-character limit for tweets on Twitter is double what it used to be back in the day, but it's still not enough to express in-depth thoughts, ideas, commentary, rants, blogs, stories, and the like. These tweetstorms, as they're called, are the reason why Twitter created its threads feature.

It looks like Pokémon GO players may get a surprise gift from the game's developer, Niantic, this holiday season.

Apple's ARKit has built a considerable lead in terms of features over Google's ARCore, but Google's latest update to ARCore adds a capability that makes the platform a bit more competitive with ARKit.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

While its competitors are concentrating on building out AR cloud platforms to give advanced AR capabilities to mobile apps, Ubiquity6 is taking a step in a different direction.

Semi-untethered jailbreaks are here to stay, as evidenced by iOS 11's Electra method, Chimera for iOS 12, and even the new bootrom-based Checkra1n tool for iOS 13. While not as convenient as fully untethered, re-enabling a semi-untethered jailbreak is still pretty easy once you get used to the steps involved.

Is the augmented reality magic fading down in Plantation, Florida? That's the first question some may be asking following a casual revelation over the weekend that Magic Leap, the maker of the Magic Leap One, has assigned much of its patent portfolio over to JP Morgan Chase as collateral.

Just like Apple and Google, Facebook has been working to develop computer vision shortcuts designed to give mobile apps augmented reality superpowers.

Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate copied apps independently, thus giving it an unprecedented layer of privacy and freedom within your handset.

The streaming content vision from Magic Leap recently underwent a quiet but major update, courtesy of AT&T.

Before smartglasses makers can dream of taking smartglasses to mainstream consumers, they must first determine the right mix of form, function, and price that will drive customers to buy into what they're hoping to sell.

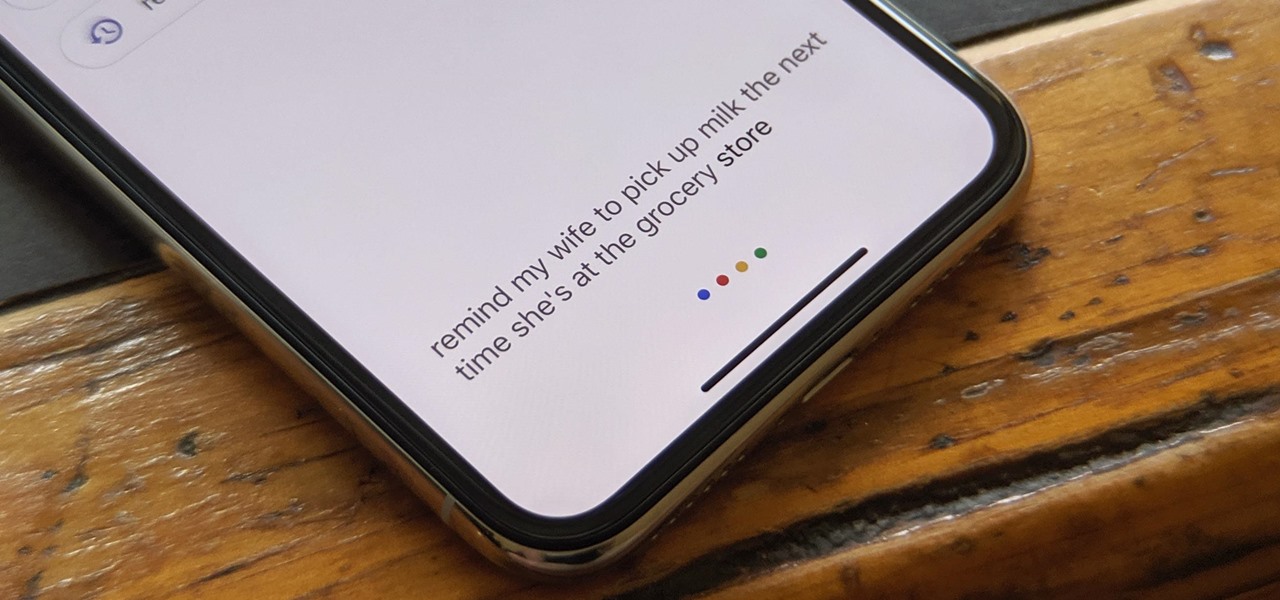
The Google Assistant is available almost everywhere. It powers smart speakers like the Google Home, it's built into Android phones, and it can even be installed on iPhones and iPads. So when Google adds a feature like the ability to send reminders to other people's Assistants, it's far reaching.

Developers and enterprise customers chomping at the bit to get their hands on HoloLens 2 may not have to wait much longer, as Microsoft passed one of the remaining hurdles needed to release their new tech into the wild.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

Some of the Pixel 3's coolest features are software related, which means you can get many of them on non-Pixel devices. "Flip to Shhh" is a perfect example of this. It lets you quickly put your phone into do not disturb mode by placing it face down, and this can be replicated on other Android phones with the help of a simple app.

Long before the HoloLens or the Magic Leap One, a California-based team of independent filmmakers envisioned what the future of augmented reality might look like.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

You finally did it! You've combined all your knowledge about photography and angle to take the perfect selfie. It looks stunning, and you cannot wait to post that bad boy to Instagram. But wait, what's this? Your skin looks so uneven and — is that a zit!? I guess the selfie gods were not in favor of your skin when you snapped it. Luckily, you can fix all of those minor flaws with the help of Photoshop Express.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

Imagine an Instagram feed filled with a wild array of vivid color. Beautiful right? But when you look at the photos in your iPhone or Android phone's albums, they're all just too dull to pull off that dynamic look. There's no doubt that colorful images are more eye-catching than dull ones, so how do you get your photos to overflow with vibrant color? The answer: Add it in post.

If there is a major blind spot in the AR space in 2019, it's the impact that blockchain technology will eventually have on the software distributed in AR clouds.

Anyone who has been within a block of any wireless brick and mortar store or tech conference in the last couple of years has no doubt seen banners, posters, and videos promoting 5G high-speed wireless services on the way.

It's difficult to find that perfect lighting when you're taking a photo. You won't always have studio lights — or at all — and you're not always out during golden hour. So how can you combat lighting issues without waiting around for a well-lit condition? Do it in post. Adobe's Photoshop Express makes it easy to fix and even customize the lighting in your photos using the right adjustments.

The era of AT&T and Magic Leap has quietly entered a new phase that ramps up the mainstreaming of the cutting edge augmented reality device.

In recent months, the Magic Leap One has frequently tied promotions to groundbreaking entertainment properties, but the latest may be the startup's biggest coup yet.

While Magic Leap turned heads at the Game Developers Conference with AR experiences at the Unity and Unreal Engine booths, news broke that the company was the winning bidder for ODG's patents.

As Microsoft continues to bask in the glow of its HoloLens 2 unveiling and begins ramping up the hype to launch, Nreal and Vuzix are carving out their own niches in the AR hardware landscape.

Current-generation mobile augmented reality apps offer users numerous opportunities to punch up photos and videos with 3D content, but there's surprisingly few options for users to express themselves using virtual characters.