In this video tutorial, Chris Pels will show how information can be passed from one page to another using a query string. First, see how to construct a query string including variable names and values from information on a data entry form. Next, see how to access the query string information when the page is posted including how multiple query string variables are handled. As part of the server side processing of query string information, see how to implement validation for existence of query...

Lisa shows us how to clean up spilled candle wax using an iron and a paper towel, a trick from Japanese Urawaza.

This how to video shows us how to clean up spilled egg yolk using salt. Avoid a slippery sticky mess with these great cleaning tips.

Joy and Gracie show us how to make a newborn infant stop crying and sleep in peace using a wine tasting secret. This is a Japanese Urawaza trick that uses the white noise of a gurgle to ease a baby's cry.

This how to video shows us how to fix a scratched cd or dvd using toothpaste. Don't throw out that scratched cd or dvd, just fix it with this DIY home project.

This video uses a skull modeled in other Zbrush lessons by Jason Walsh to discuss ideas and ways to think about presenting compositions, render passes and posting work for others to see, and for job applications. You don't need to have the skull built to follow this video. This theories should be applied to each sculpt after you've finished modeling.

Notice: This is probably not new to many people. This *IS* new for some people however, and meant for them! Post interesting cameras you find.

As promised for nearly the whole school year now, I have finally explained how to do two simple pen tricks. There are many such videos on YouTube and elsewhere, but many (students) have requested me to explain it too, so here it is.

In this episode, we dive into the expensive, or, at the least, tedious realm of camera stabilization equipment. This ranges from the all-powerful, all-knowing fluid tripod head, to the much used and often abused dolly. We don't own and operate an actual Steadicam or a jib or a crane, but hey, we'll mention them, too.

Before I built the mechanics for my laser cutter I was planning on using the etch a sketch since the pulleys where already there. I accidentally cut the wires while taking it apart, so I made it from scratch (much bigger too). But I figured I'd post this in case you want a small laser cutter and need to learn how to take apart an etch a sketch. It was a bit tricky. The tought part was trying to take off the case. What you need to do is to pry the red off of the black, not the other way around.

This is how my version of an origami Christmas tree turned out based on the instructions I posted awhile back. Cory also made a version from white glossy paper, which looks great. I opted for the green and brown look, but it wasn't easy.

Are you the one scraping sticky marshmallowed yams and congealed gravy off the dishes every Thanksgiving? Shame someone else into doing it this year. Avoid doing the Thanksgiving dishes.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

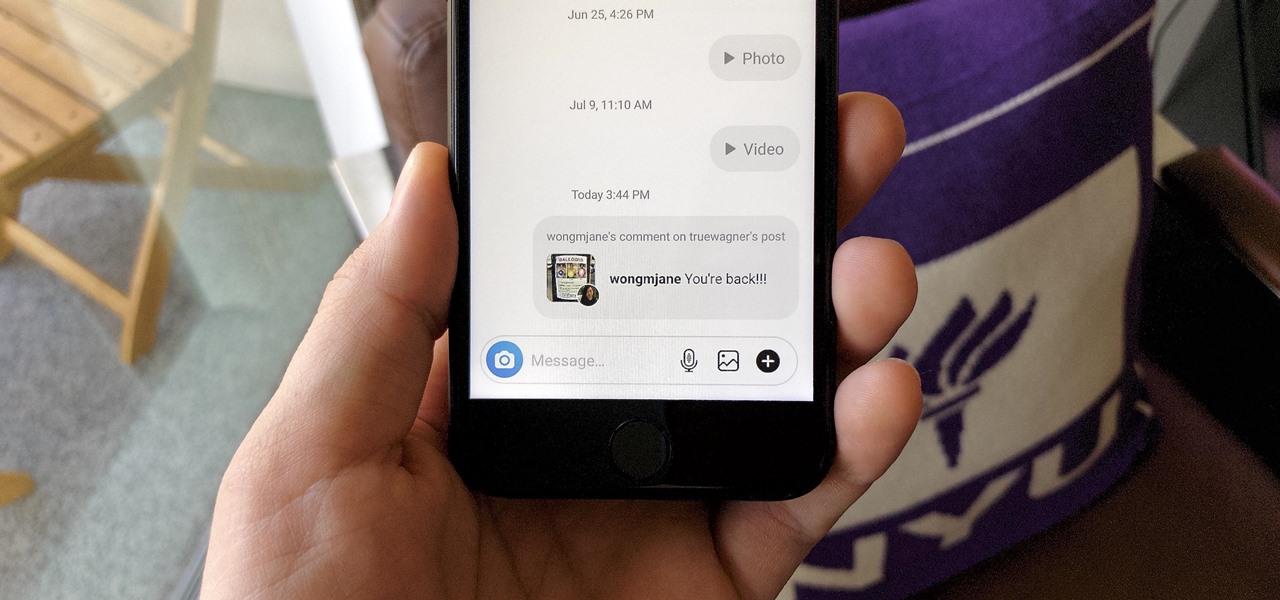
Sometimes, you'll see a comment on Instagram that you really need to share. Maybe it's something funny, possibly offensive. Whatever the case, the only thing to do is screenshot it and share that, right? Hopefully, not for long. Instagram is currently testing a feature that would allow you to share comments with others via a direct message and maybe even to stories and other apps.

In a way, Twitter is the town square of our era, where people can share and discuss ideas on a wide variety of topics. While the tech giant has its own app for Android, it's pretty bare-bones when it comes to features. This has paved the way for third-party clients that are rich with customization options.

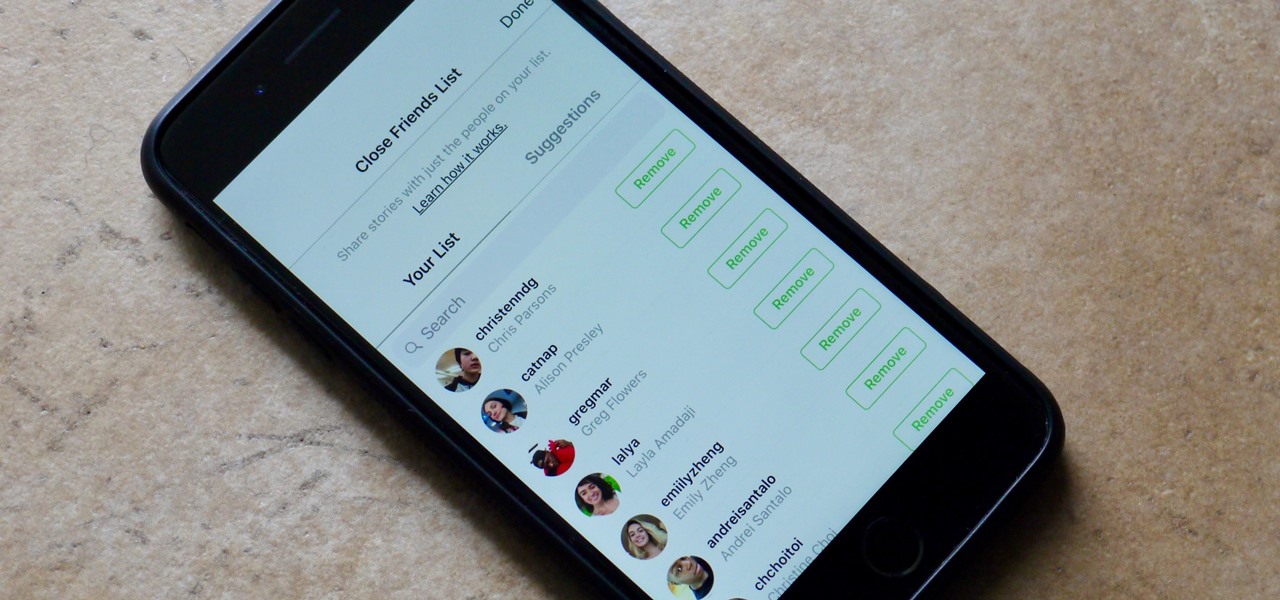
Stories make sharing your day-to-day highlights fun on Instagram. However, other than choosing who to hide stories from, by default, stories don't have much privacy control, especially if your Instagram account happens to be public. Instagram recognizes this flaw, which is what its "Close Friends List" is all about.

Instagram has long-resisted easily resharing content. While it's been testing a "regram" feature for a long time, it still lags behind apps such as Twitter and Facebook when it comes to resharing content. But while Instagram is a bastion of original material, there is a feature in place for you to reshare stories from those you follow. Your friends can reshare your stories too.

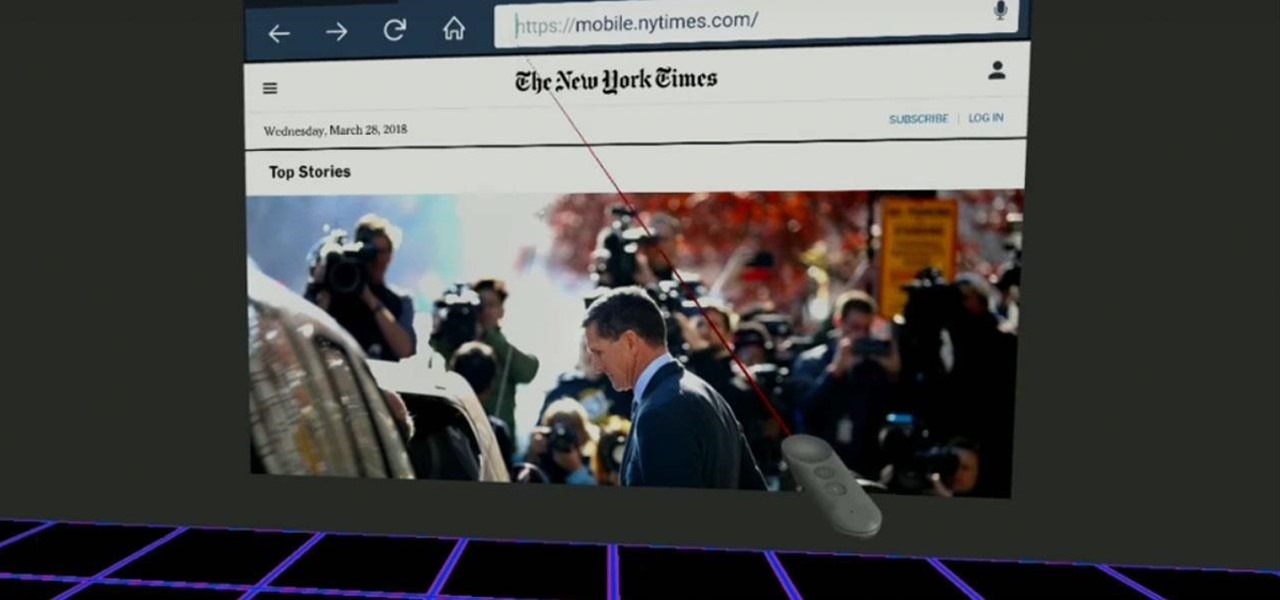
Before Google Chrome entered the scene and subsequently dominated the market, Firefox trailed only Internet Explorer as the most popular web browser. Now, Mozilla has its sights set on a new opportunity to revive its browser for immersive experiences.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

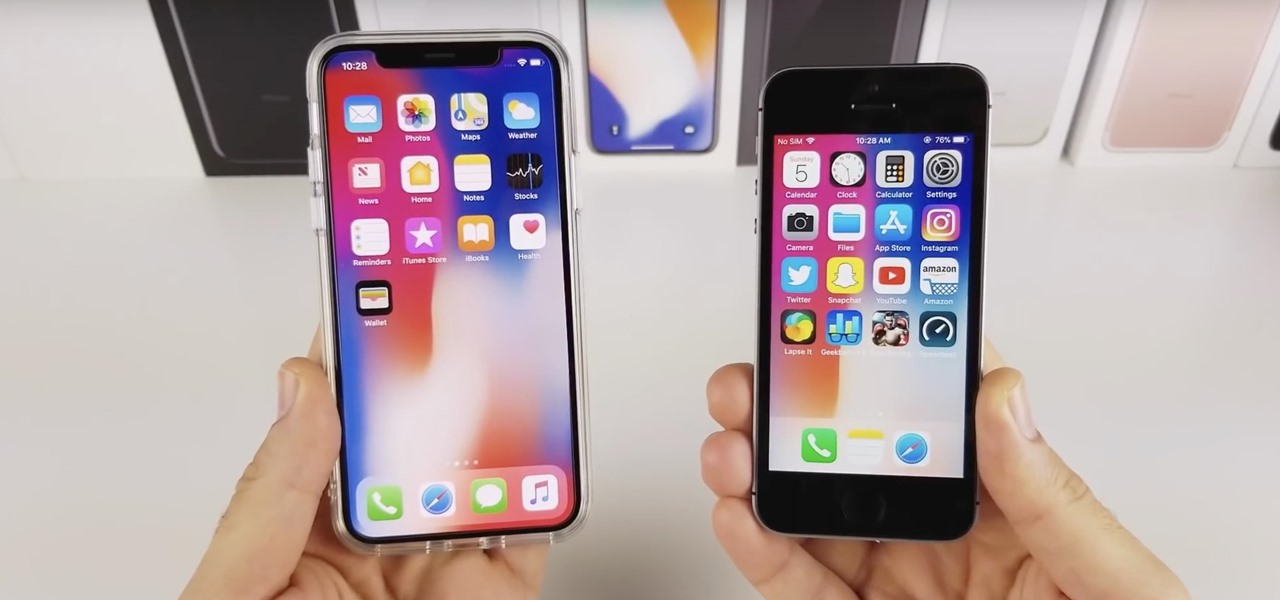
When first released, the iPhone SE was nearly identical to its iPhone 6S counterparts in all but form factor. While the rumored SE 2 (if it even happens) is expected to follow suit with the iPhone 8 models, that hasn't stopped people from wondering what it would look like with an iPhone X-like bezel-less display.

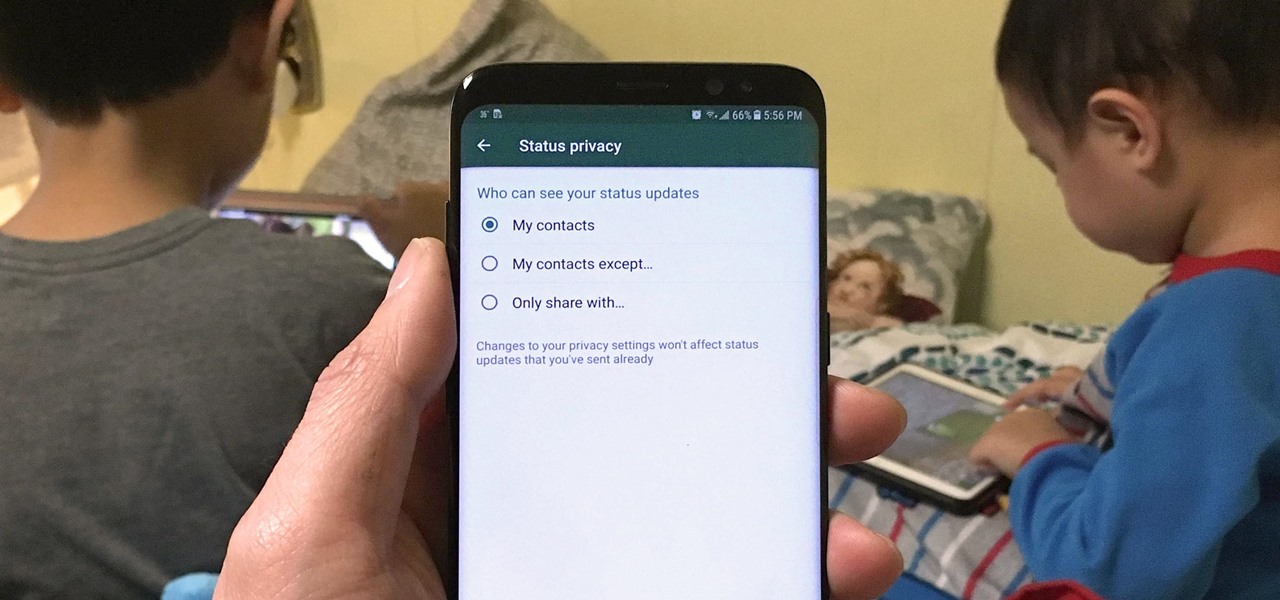
Sharing Stories via WhatsApp Status grants your friends access to your daily adventures in the form of GIFs, photos, videos, or simple texts. Like Snapchat, stories you share with your contacts disappear after 24 hours, giving you an extra layer of privacy since anything you post will not be permanent. And if you want to limit who can see your private stories, WhatsApp also has you covered.

As awesome as the 2017 Galaxy lineup may be, few can forget the monstrous disaster that was the Note 7's exploding battery. Needless to say, the last thing Samsung wanted was another news story about a problem with the Note 8's battery. Unfortunately, that's exactly where we find ourselves today.

After multiple leaked references in Samsung apps, the Oreo Beta Program for the Galaxy S8 and S8+ is official. Yesterday, we posted a full changelog from users that obtained the beta a day early. The update brings many new features from Oreo to the S8, including notification channels and autofill API support. If you're quick, you can enroll your Galaxy S8 in the beta today.

The creative possibilities are part of what makes Apple's ARKit so exciting. We've seen new camera effects, painting, and new ways to tell stories through ARKit. Now, the app developer studio "Orb" has created an app to let you create scenes with 3D objects of your choosing.

You'd better start watching where you're stepping because there are portals opening up everywhere thanks to Apple's ARKit.

Following the most recent election, some argue that increasing political polarization is dividing Americans. A new app, called Read Across the Aisle, is aiming to combat this by encouraging users to read news from media outlets on both sides of the political spectrum.

Making a custom location on Instagram is one of the best ways to generate traffic to your account. It gives you that extra uniqueness when it comes to standing out amongst other companies. It also allows people to check in at the same location, further promoting your account across other platforms.

Update 6/20/17: Olixar, a smartphone case manufacturer, has released images of an iPhone 8 case design. While at first glance this might seem to confirm the iPhone 8's final design, 9to5 Mac reports that Olixar admits they produced these renders based on "information and schematics they've acquired through their factories and contacts in the far east."

Uber resumed its pilot program for driverless cars after one of its autonomous vehicles crashed in Tempe, Arizona last weekend.

A proof of concept for an overhead crane training simulator is in the works. Using Microsoft HoloLens and an industrial-style controller, trainees can pick up holographic loads and transport them throughout a warehouse setting.

The Last Supper, or L'Ultima Cena, is a mural painted by Leonardo da Vinci in 1498. It is considered one of the greatest paintings of all time, and if you live in the San Antonio, Texas area, or are willing to travel, you can get it shaved into the back of your head.

The winter holidays are right around the corner and that can only mean one thing—dessert. Leave it to the French pastry chefs to come up with something totally unique, like this glittery, chocolate Slinky by Amaury Guichon of Jean Philippe Patisserie inside the ARIA Resort and Casino in Las Vegas.

If you want to become a food Instagram star, you may want to consider having babies. Well, to be more specific, you might need Mike Chau's two adorable children, Matthew and Samantha.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

With over a billion monthly active users, it seems that Facebook is nowhere close to being dethroned as the most popular social media service in the world (sorry, Ello). While their stats may be impressive, it doesn't mean that Facebook is as good as it can be.

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.

There are certain foods and beverages that can actually brighten your smile or improve your dental health when you chew or sip them. Once you understand their chemical properties or textures, you can look to items you already have in your cupboards or refrigerator to help keep your teeth looking and feeling their best.

Spotlight is awesome for finding items in the stock Apple apps, but what if you want to search through the rest of the apps on your iPhone?