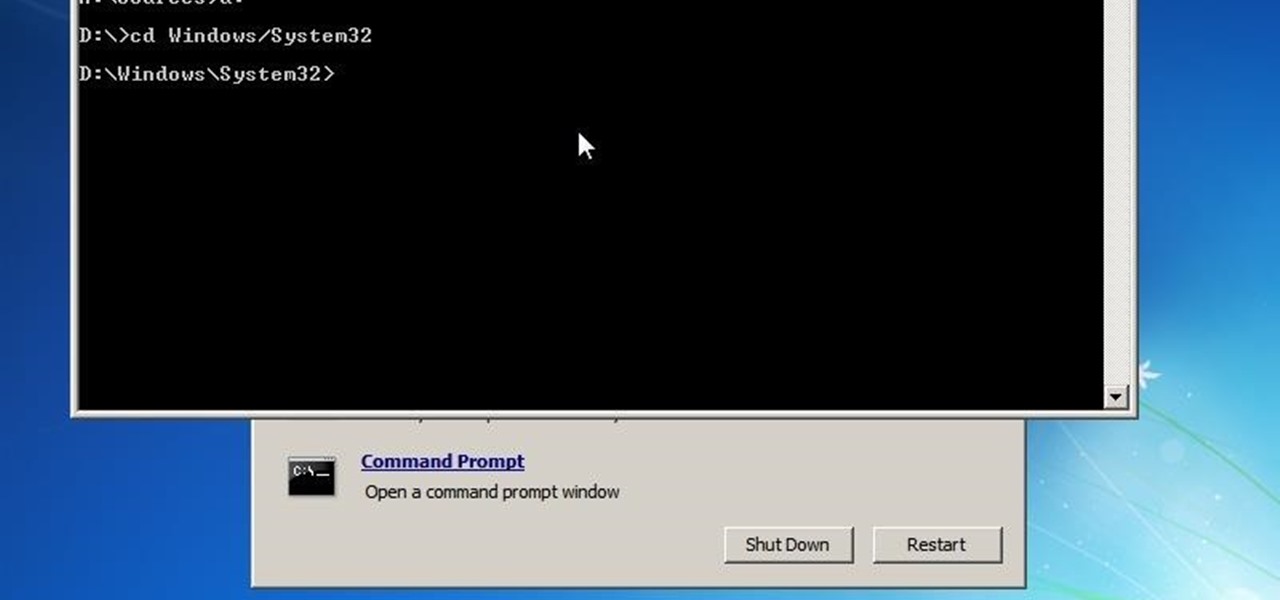
This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.
First and foremost, let me once again apologize for that bug, which I failed to notice in time. Alright, alright... Enough sulking, oaktree. Get to it!

Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey, as long as it's there, people can always go off to research themselves and eventually understand. So here is my contribution to the gradual and inevitable progression of Null Byte!

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

For me, shredded coconut is something that is eaten several times a week in a variety of ways—and that includes in savory dishes. It can be added to just about anything, and this is a good thing if you enjoy having some variety in your diet. Because I get tired of eating the same foods all the time, over the last few weeks I've tried some pretty interesting and simple ways to use coconut flakes in order to keep my finicky palate satisfied.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.

In my last post I introduced how to use ncat to connect to your Pi remotely, but what's the point to if you can't actually hack? This tutorial I'm gonna show you how to use very simple tools for a much bigger purpose. With that said, boot up our Pi and lets wreck havoc.

Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

Welcome back Java programmers! In this tutorial we'll being going over Variables/DataTypes and Type-casting

If Android is all about options, then iOS is all about new features. Every year without fail, Apple announces a cool software component that brings something new to the table, and this year was no different.

I'm no coupon-cutter (I just don't have the patience for it, sadly), but I do love buying things in bulk to save a buck or two. And one of the staples on my bulk-buy list is chicken; I cook with chicken so often that trying to save money on it is a no-brainer.

Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

If you read my previous post, "How to Hack into a Mac Without the Password", you know that it is very easy to break into someone's Mac if you have physical access to the computer. Now the question that lies is, how do we protect ourselves from this happening to us? Well, here is a way that guarantees that no one will be able to change your password through OS X Recovery.

Welcome back to another C tutorial, this post covering the first part of control structures, if statements. Let's get right into it.

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

BlackBerry has yet to find a home amongst the iPhone and popular Android phones, with sales plummeting over the last couple years, but this might be a thing of the past thanks to their latest device, the BlackBerry Priv. It has decent numbers so far and was even sold out on Amazon shortly after its initial release.

This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me.

Hello everyone! I'm glad to post my first tutorial and hope you will appreciate it.

When it comes to news, updates, and arbitrary nonsense, it's hard to find a better source than Twitter. And for some of us, the best way to consume Twitter is through the web (versus a mobile app). But as much as I prefer the standard browser version, it's easy to make it better, faster, and more convenient using a few Chrome extensions—and here are my favorites.

Editor's Note: The research described in the article below has been criticized and any conclusions based off this research should be examined with a skeptical eye. The article has been edited to reflect these issues.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

Boxed brownie mixes advertise their convenience compared to homemade brownies—with only a few ingredients, they promise a moist, chocolatey crumb. However, these "instant" mixes still require fresh ingredients and a baking time that matches that of homemade brownies. When you're craving a chocolate fix but you're coming up short on eggs, oil, and time, don't despair: you can still make brownies using a can of soda. Two Different Methods, One Soda Required

Video: . Being one of the most popular DIY/maker projects around, Musical Floppy Drives are nothing new. However, myFloppyDriveOrchestra includes a few unique features, which separate it from the crowd.

Windows 10 marks a new era for Microsoft with the return of the Start menu, the demise of Internet Explorer, and the introduction of the remodeled Windows Store.

When I finally saved up some cash and got my first good chef's knife, I vowed to do everything by the book: clean it properly, hone it regularly, sharpen it faithfully, stand by it in sickness and in health, blah blah blabbity blah.

Aren't the weekends extra special when they include a bacon, egg, and pancake breakfast? We call it "Lazy Sunday" for a reason. Actually, who needs it to be a weekend? Monday it is!

If you've updated your iPhone 4S or iPad 2 to a version of iOS 7, iOS 8, or even iOS 9, you've probably noticed that its performance is a little more sluggish than it was back when it had iOS 6 and lower on it.

Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring....

As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.
Hello, Hackers/Viewers! My name is nullf0x, and I have 4 years of experience as a hacker. You might see everyday that one of your friends or acquaintances get a new virus in their computer. You might think, How cool would it be if I made a virus? or How cool would I be if i could remove viruses from others computers for money or free?

With all the stress that goes into booking flights and lodging, packing (and not forgetting) everything you'll need, finding pet sitters, and everything else that goes with a trip overseas, there's the added stress of staying connected while abroad.

Relentless in its fury, the iOS text messaging exploit that exploded onto the scene late last week seems to do more damage than initially reported.

With just a Phillips head screwdriver and this walk-through, you can open and close any bObi robot vacuum. So long as you have a replacement wheel, follow these steps to install it yourself.

Hi there, Crackers, Welcome to my 7th post (Part-1), this tutorial will explain about the basics of Batch Scripting.

Smartphones don't generally play nice with tripods, so videos taken with our handheld devices make terrible source material for time-lapse photography.

bObi has four floor detection sensors on her underside that warn her not to drive over ledges and stop her from falling down stairs.