
GIVEAWAY ALERT: AWE Is Here & We Are Giving Away Free Passes!
The Augmented World Expo (AWE) is upon us, and that means it's time to get excited about all the awesome next reality things to come.


The Augmented World Expo (AWE) is upon us, and that means it's time to get excited about all the awesome next reality things to come.

Instagram just added another nail in the coffin for Snapchat. It looks like it's the AR platforms final hurrah as IG has snapped up the app's last good feature: its AR selfie filters.

Firefox Focus has been out for iOS for a while now, so it's about time Mozilla began porting the app over to Android. It's an amazingly private browser that protects you from trackers and ads when you're surfing the web. It blocks a wide range of online trackers, erases your browsing history, hides passwords, and deletes cookies. This essentially means ads won't be able to follow you around, in the sense that you won't see ads related to your last ten searches on Google.

In a series of news about the OnePlus 5, the company posted its first teaser of the upcoming device on its Weibo account. According to GSM Arena, the teaser doesn't show us any sneak peaks of what the phone might look like — co-founder Carl Pei took care of that — though, we are greeted with the caption "Hey Summer! Give me five!"

A new technological movement without the technology itself is just an idea sitting and waiting. Once the technology is present in the equation, movement forward can begin. This is how many of us see the head-mounted displays (HMDs) and smartglasses that have recently entered the augmented and mixed reality market — or are coming out in the next few months. This is a movement that will sweep over the world, changing everything in its path, and these are some of the people behind it.

Last week, the internet was ablaze with talk about the Galaxy S8's home button, because it subtly changes positions without the phone alerting you. This feature was included to stop burn-in issues with the screen, and the general consensus from tech sites was the screens would not experience any burn-in at all.
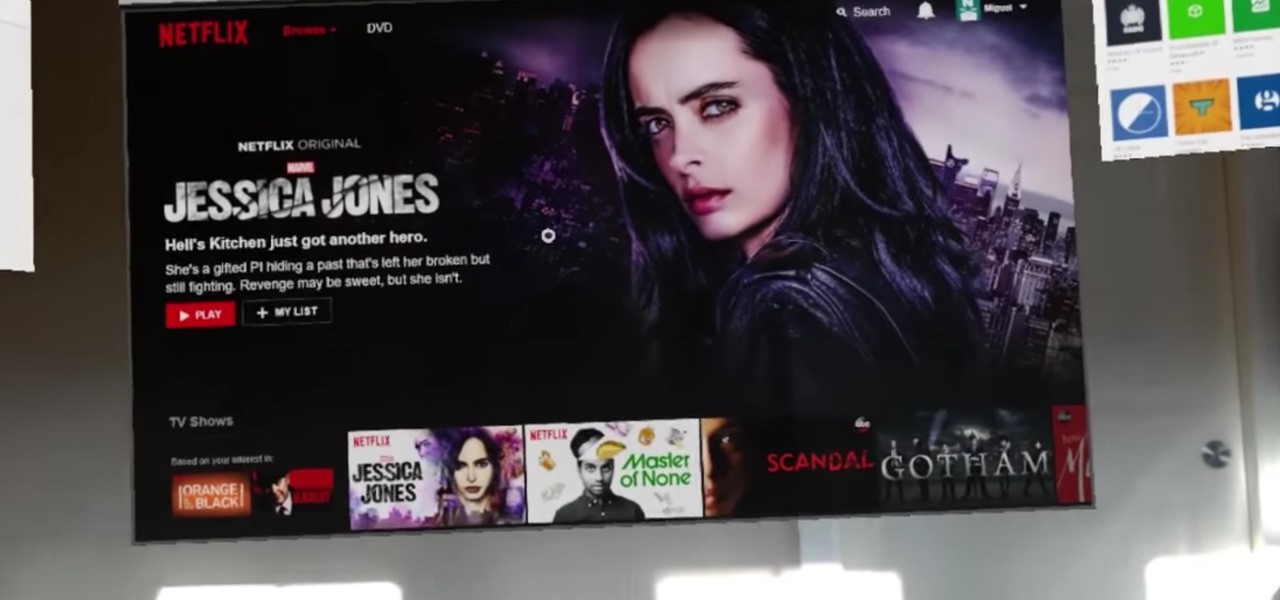
Alright, fellow HoloLens code wranglers, load up your word processor because it's time to spruce up your résumés. According to a report by Variety, Netflix is looking to hire a new Senior Software Engineer — and Windows and HoloLens were mentioned as an end point.
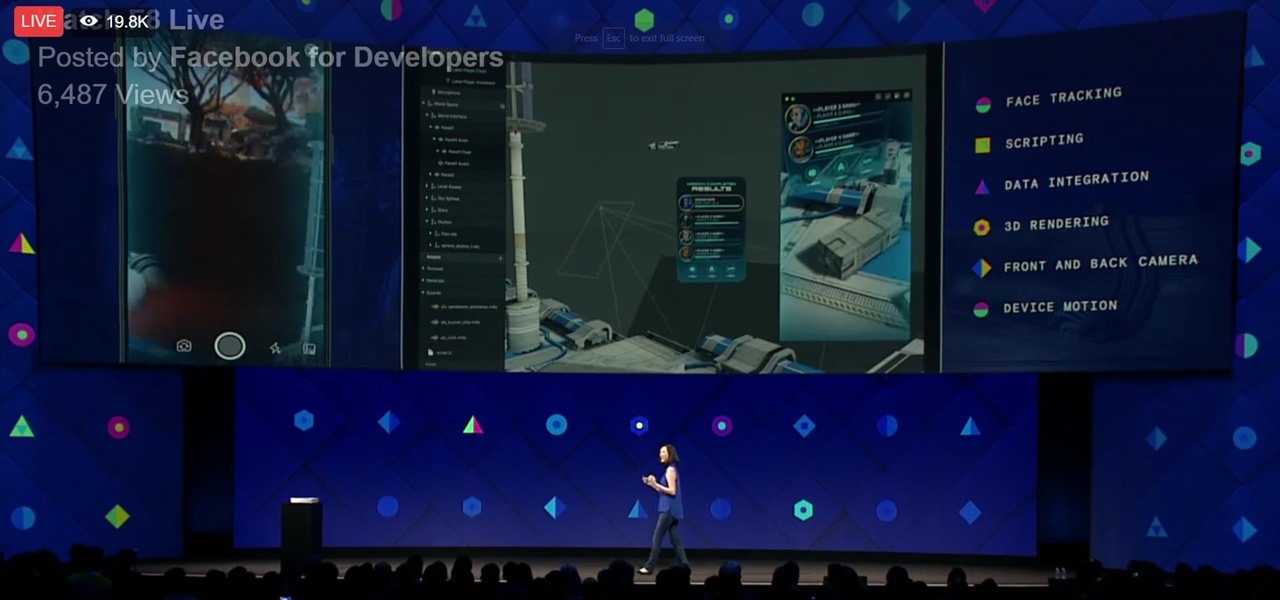
During his opening address on April 18 at F8, Facebook's developer conference, CEO Mark Zuckerberg launched the company's augmented reality platform centered on artificial intelligence-powered cameras.

Microsoft's augmented reality headset, the HoloLens, is getting a taste of the classroom with Lifeliqe's new mixed reality apps for kids.

During the last few months, WhatsApp's Google Play Store ratings have been tanking—all the way down to an average of 3.4 stars from the instant messenger's usual average of 4.1. Within the last week, though, WhatsApp has received thousands of seemingly fake 5-star reviews that have bumped up the company's overall average to a 4.4.

It's official — the newest version of Google's mobile operating system is called Android 8.0 Oreo, and it's in the process of rolling out to many different devices. Oreo has plenty of changes in store, ranging from revamped looks to under-the-hood improvements, so there's tons of cool new stuff to explore.

This morning, in an early morning session at GDC 2017, Brandon Bray, a senior program manager lead at Microsoft, revealed a mixed reality headset made in collaboration with Acer—a different headset than the one we saw from Acer at CES 2017 earlier this year. Also at the event, the name for Microsoft's holographic system seems to have changed from Windows Holographic to Windows Mixed Reality.

With the Game Developers Conference (GDC) in San Fransisco just a few weeks away, Microsoft Senior Program Manager Vlad Kolesnikov has announced via Channel9 (Microsoft's developer news outlet) that not only will new low-cost virtual reality headsets be coming in March to developers, but that they will be at GDC, too.

Android's notification system is quite robust, especially now that Google added bundled notifications and quick reply features to Android 7.0 Nougat. However, things can still get quite cluttered when you have several unread messages, which fills your status bar with icons and makes your notification tray take up half of the screen by itself.

Leave it to some lazy college kids to attempt to figure out a way to brew a pot of coffee without leaving the couch.
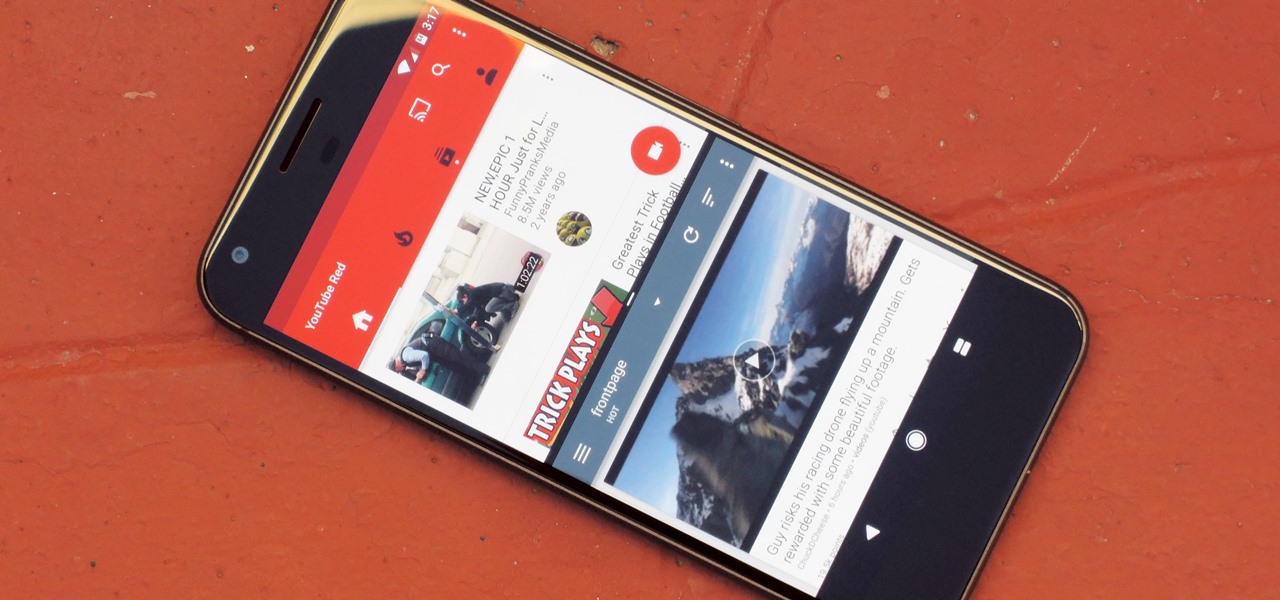
Android 7.0 Nougat brought a lot of multitasking improvements along with it, but the most notable addition is a unified multi-window mode (which shines bright in Google's Pixel phones). This means that every Android device can now use the same split-screen interface, and the days of software fragmentation caused by differing multi-window implementations by LG and Samsung are now over.

The Snapdragon 820 and 821 were met with praise last year, receiving almost no complaints compared to their overheating predecessor, the Snapdragon 810. But now, all eyes are on Qualcomm to see what goodies they have in store for us this year, as their new SoC, the Snapdragon 835, will be revealed this week at CES 2017.

Frosty the Snowman is a fairy tale they say, but this microscopic snowman is very real and just broke the record for the world's smallest snowman. (Though, it's not Guinness-official yet.)

If you really want to play Gran Turismo or Castlevania on the go, Sony's PlayStation Portable is a great way to do it. But it gets harder and harder to justify carrying around a PSP handheld gaming console when you've got an equally powerful Android phone in your pocket already. The PSP had a good 10 years before being discontinued, and your Android can pick up the slack now.

Windows Insiders running Build 14971 of Windows 10 in the Fast Ring can now look for the "Windows Holographic First Run" app to check to see if their PCs are up to the task of running Windows Holographic. It won't detect your VR headset yet, but at least you'll be able to see if your computer will be compatible.
Immigration and immigration policy are some of the biggest discussions happening in international and domestic politics right now. From building walls to opening borders, a definitive plan has not been made about how to deal with the large number of people who are fleeing their home countries in hopes of a different life.

Visualization is one of the obvious commercial applications for technology such as Microsoft's HoloLens. The ability to see the assets of a project in different scales—from micro to larger-than-life—with a quick air tap will play a large part in the coming augmented reality revolution. Whether the assets are art for a game, interior design, raw financial data, or architecture, data visualization will play an important role in the future. This is due, in part, to our ability to absorb informat...

When it comes to hacking guides, most are written from the perspective of a Linux user. There are a few outliers, but it's mainly Linux, which leads to the idea that Linux is the only OS that's viable for hacking. This couldn't be further from the truth. A properly set up Apple machine can do quite a bit of heavy lifting.

Verizon customers who use the Samsung Galaxy S7, beware: a recent update installs new bloatware over your existing bloatware that installs new bloatware. Confused or pissed off? You should be, as this app can install new apps onto your phone without you knowing.
I've been doing tutorials on Rasberry Pi and I would like to thank everyone that have both read the tutorials and gave me feedback on how well I'm doing. But now I've decided to take a small break and start a mini series that I'm hoping to be at least five tutorials. This doesn't mean I'm gonna stop posting Raspberry Pi tutorials, but since I'm learning so much at the same time I've decided to share some of that knowledge. Hence this tutorial. Please sit back, relax and read on.

This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. OTW made a brilliant article, but only touched on the surface of the possibilities. I hope this article will both show you many the possibilities and also allow you to start causing havoc, but I'm planning on making this ...
Kim Kardashian and Kanye West have fittingly named their second child "Saint," but I'm sure you don't care about that—and neither do I. Unfortunately, regardless of our pop culture interests, we're forced to know these types of stupid facts because the internet is so densely populated with Kardashian-related content that it's impossible to avoid. It's enough to make you puke.
How to do an NMAP scan on Armitage to find IPs within a certain range. Armitage is a gui interface of Metasploit, and advanced hacking/exploiting program. It can be downloaded from http://metasploit.com/ and http://fastandeasyhacking.com/ and you will need NMAP. http://www.nmap.org/

!!!WARNING!!! !!!Because of misleading informations please wait for the new post about this same argument instead of reading this post!!!

Hello My Fellow Hackerzz.. This is my first How-to and i'll be updating the “Hacking Android Using Kali” to msfvenom and some FAQ about known problems from comments. So Here we GO!!

You must have read news about hackers dumping the data online, recent one was Ashely Madison. It's only the big companies' data, which gets noticed once it is out. There are many other small leaks which don't even get a mention. So this article is the first one of my series which will help you to find hacked accounts. Some of you must already know about this, but this post is intended for the new learners. This also serves as an example of my learning how a good service can be used in other w...

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my original script can download files, upload files, make changes to registry, create user accounts and more. I'm sure you could do it on your own too.

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

MagicTree is often the go-to tool for data collection and reporting for many pentesters. It organizes data in nodes in a tree-structure which is very efficient at managing host and network data. Reports can be completely customized to meet the user's needs. Also, MagicTree allows you to import XML data and has XSLT transforms for Nessus, Nmap, OpenVas, Burp, Nikto. MagicTree comes pre-installed in Kali.
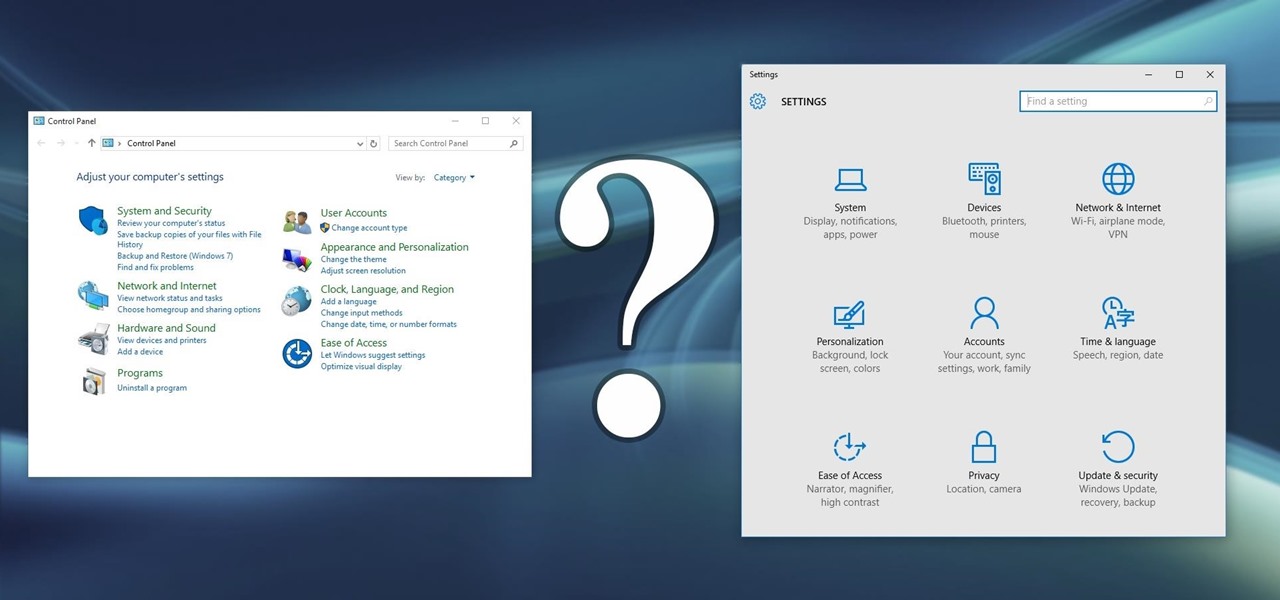
Slowly but surely, Microsoft is pushing more and more options out of the Control Panel and into a new menu simply called Settings. This new Settings menu debuted with Windows 8 and mainly focused on touchscreen-related options, but starting with Windows 10, you'll find quite a few general options residing here as well.

In an attempt to increase advertising revenues, Snapchat introduced Discover back in January of this year, a feature that brought a handful of prominent media partners, such as CNN, ESPN, and Vice to your feed, along with their tailored news stories and videos.

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock:
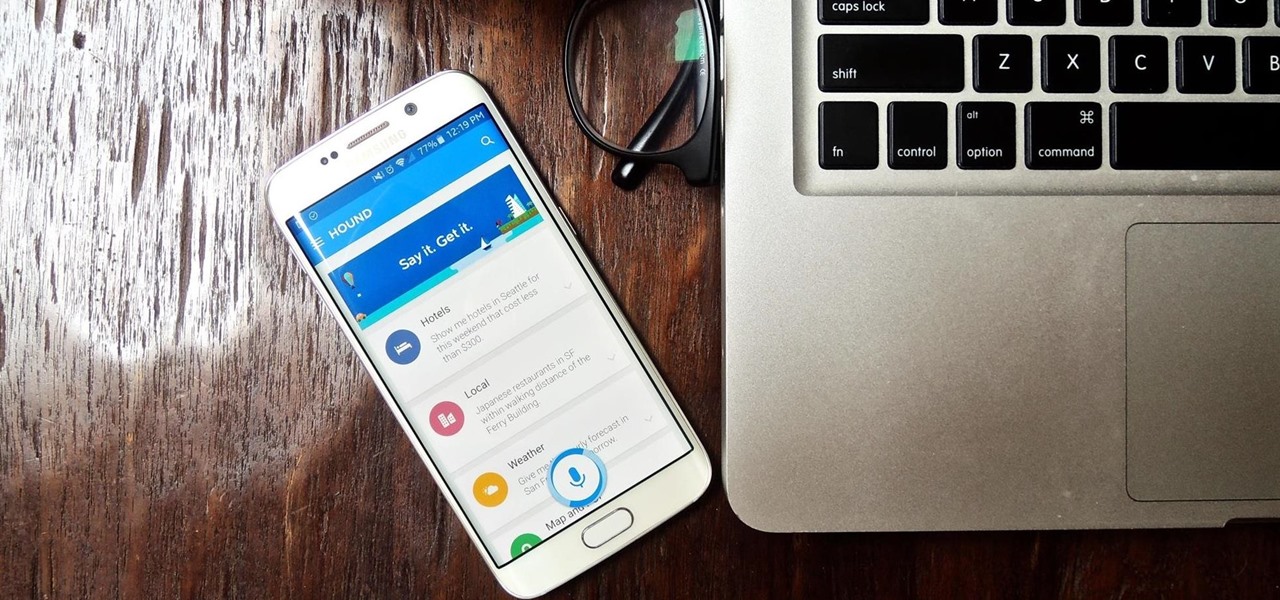
SoundHound's new virtual assistant application, Hound, is gaining a lot of buzz in the tech world—especially after a demo video showed just how awesome it works (it has amassed over 1.6 million views in under a week).