This process requires XBox2 live with vision camera. We are going to create a character. First, you go to multiplayer mode, options and then choose character creation. If you haven't created a character, you will start from scratch here. If you have created a character previously, you will make some adjustments to the character for this presentation. Now, go to player information and then service record. As the program already has a character, we are going to change the appearance of the char...
Okay, just because the new Verizon Wireless Droid X comes with an HDMI-out port doesn't mean you're limited to just that. Motorola has made it possible for you to play video, music, and pictures to your television without any wires at all. With the Droid X's DLNA media sharing application, you can easily stream to an PS3 or Xbox, send pics to your PC, and stream videos to your TV. Check out this video walkthrough to learn how to use the DLNA services to connect your Droid X to the PlayStation 3!
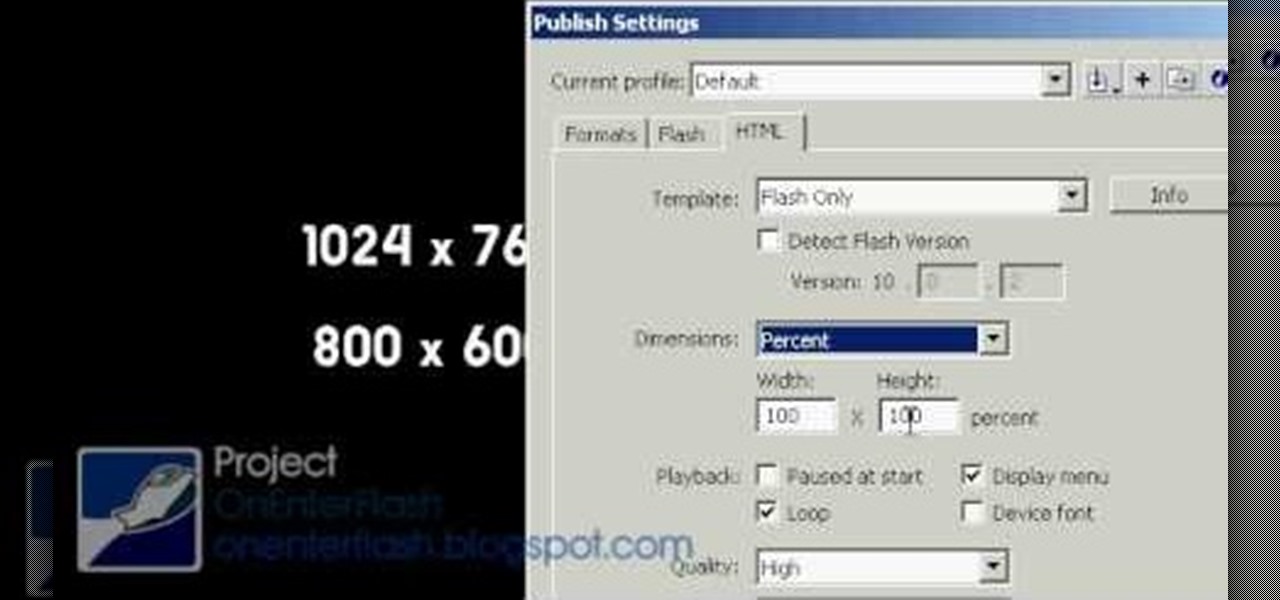
Creating a website from scratch is one of the most productive and most challenging things that you can do on a computer, whether the site promotes your own services and interests or you're being paid to make it for someone else. This nine-part video will walk you through the entire process of making a website using Flash CS4. It is very complete, and if you have the patience to watch all nine parts you should be well on your way to creating a really cool, high-traffic site.

So, you've just got yourself an Apple iPad, but it already needs fixed, or you want to check the innards out for yourself, you're going to have to know how to open that sucker up. This video tutorial will show you how to do just that.
Check out this informative video tutorial from Apple on how to organize your Mail in Mac OS X's Mail. See how to sort messages with rules, create smart mailboxes, and comlpletely organize your mail. Mac OS X. It's what makes a Mac a Mac.
Check out this informative video tutorial from Apple on how to use the basics of Mac OS X Mail. See how to set up mail with your email accounts, compose messages, add attachments, view attachments with Quick Look, and search through Mail. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to use Mac OS X Mail to its fullest. See how to filter out junk mail, use data detectors, and view RSS feeds in Mail. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to add a blog to your website in iWeb '09.

Check out this informative video tutorial from Apple on how to add a photo album in iWeb '09.

Check out this informative video tutorial from Apple on how to add a movie to your website in iWeb '09.

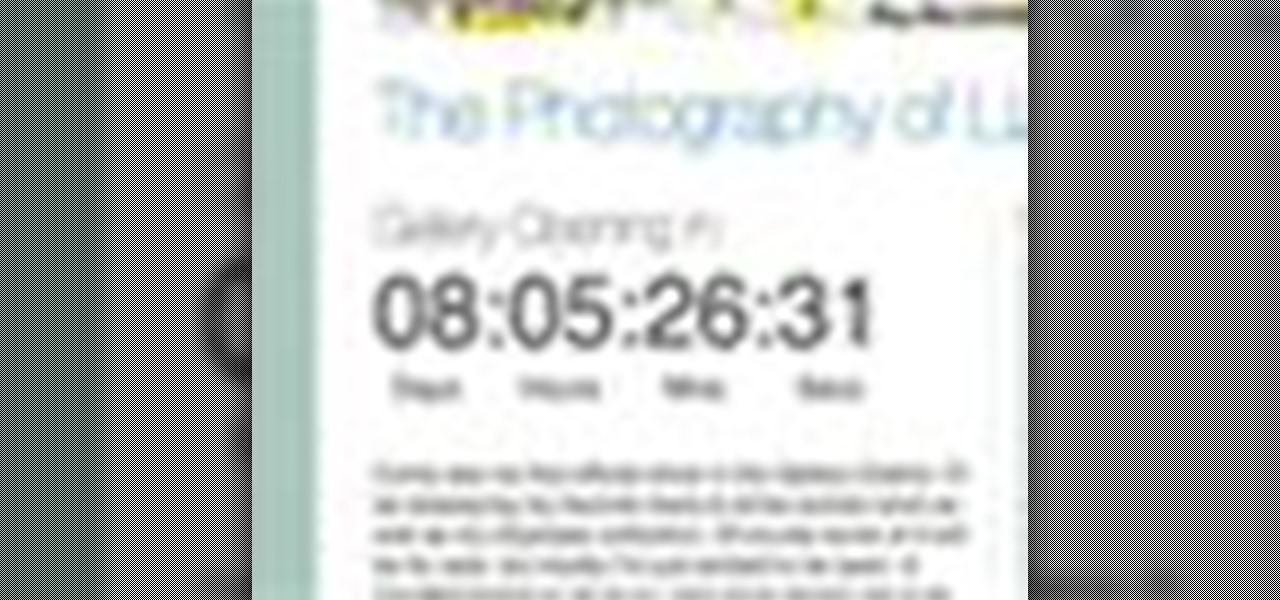
Check out this informative video tutorial from Apple on how to add a countdown clock in iWeb '09.

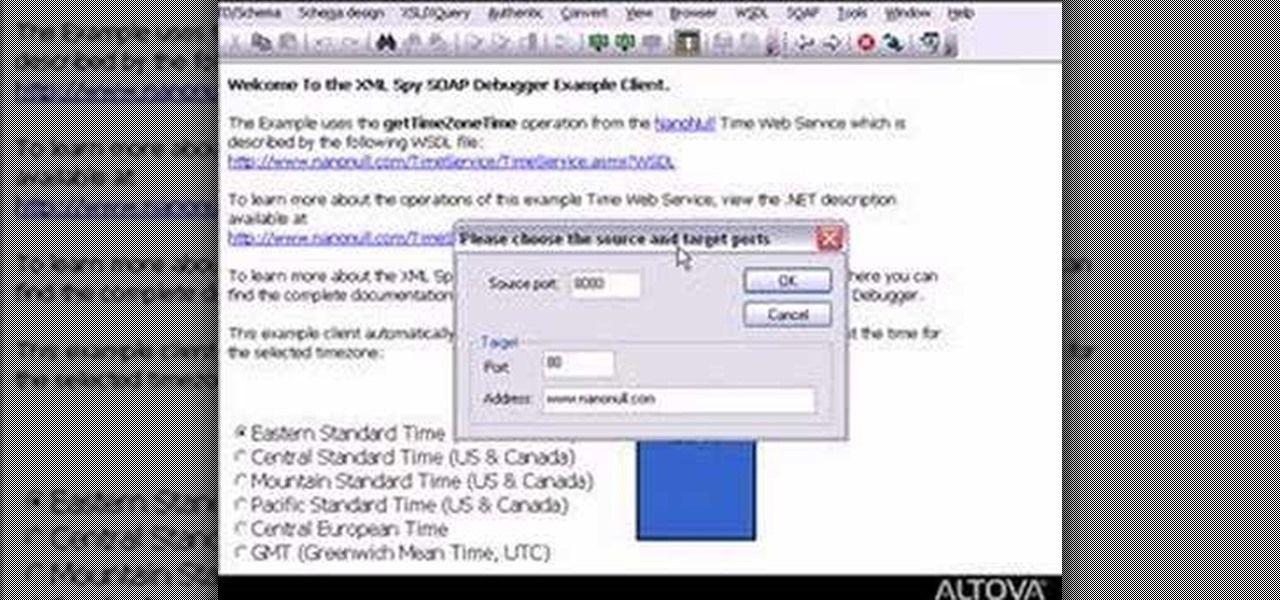
Need to debug some exisiting net services? Well, check this video out for how to do some basic XML editing in XMLSpy.

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

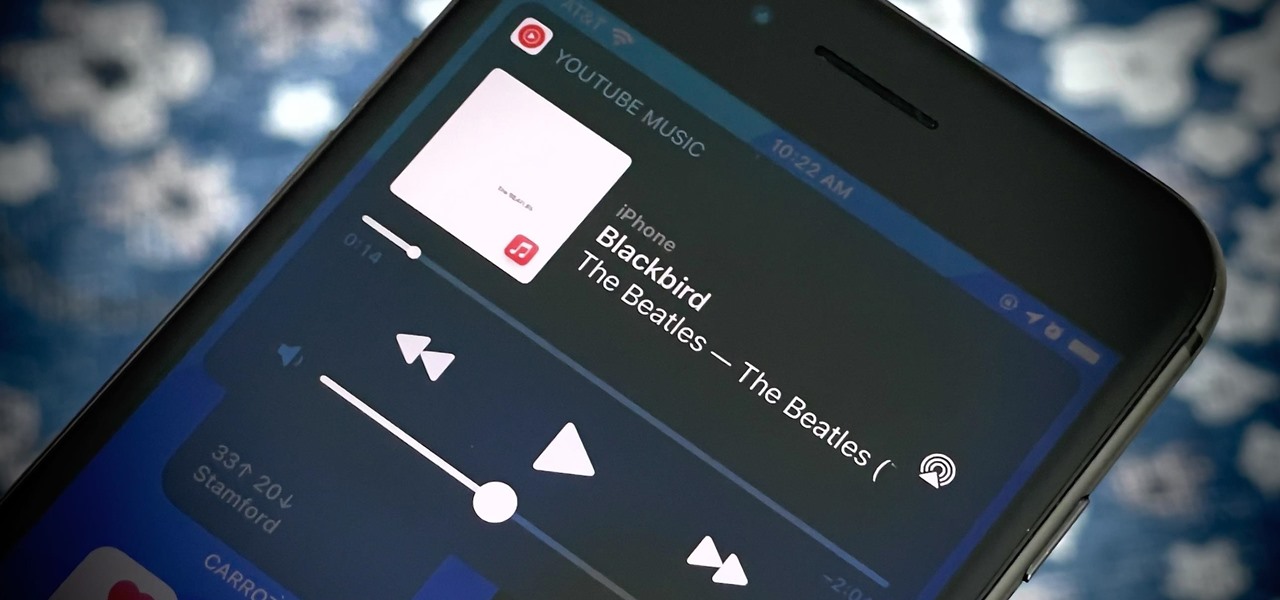
A new feature in iOS 14.5 lets you change your preferred music player for Siri requests. So if you primarily use YouTube Music over Apple Music and other services, Siri will learn so that you never have to tell the virtual assistant to play a song, artist, or album "on YouTube Music" again.

Now that 3D display maker Looking Glass Factory is closing in on $2.2 million raised in its crowdfunding campaign for the consumer-grade Looking Glass Portrait device, the company now has a 3D content generator to go with it.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

While much of the world is currently in some form of quarantine due to the COVID-19 pandemic, augmented reality (AR) gives us all the opportunity to see virtual content while stuck in our homes.

By now, you've probably been inundated with enough Baby Yoda memes to last you a lifetime. But if you don't have the new Disney Plus streaming service on your TV, you're probably wondering where all this is coming from. Well, lucky for you, just in time for the holiday season, we're here to guide you to the best ways to take part in all the streaming fun when you're not glued to your mobile devices.

For those with small hands, smartphones have gotten out of control as of late. Nearly every flagship phone is over six inches in length, so many are forced to use phones that are too big for them and hope they don't fall. Well, thanks to one developer, using these phones can be a lot easier.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.

Every photo you take is brimming with metadata such as iPhone model, date and time, shooting modes, focal length, shutter speed, flash use, and geolocation information. Share these pictures with friends, family, or acquaintances via texts, emails, or another direct share method, and you unwittingly share your location data. Even sharing via apps and social media sites can compromise your privacy.

In case you hadn't heard, Google is now a legit cell service provider. Google Fi has its pluses and minuses, but the biggest upside is in the pricing. Depending on how much data you typically use, there's a good chance you could save a lot of money without sacrificing coverage by switching to Fi.

If you've ever been on the receiving end of a threatening phone call, you'll immediately know the value in being able to record phone conversations on your iPhone. Beyond that extreme example, however, recording calls is still an extremely useful feature to have for important conversations like business meetings and verbal agreements, and it's totally doable with a third-party app.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

With Gboard, Google created a keyboard with more functionality than just inputting words. The app includes features such as GIF search and live text translation, but it gets even better when you let it learn more about you. With this data, Gboard grows from a good keyboard to one that can complete your sentences.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Your iPhone has a lot of personal information contained within it, so of course you want your device to be secure. You don't want that information getting into the wrong hands — or any hands other than your own, for that matter.

Coverage for the 88th Academy Awards, aka the Oscars, will air live this Sunday, February 28th at 4 p.m. PT (7 p.m. ET). The ceremony itself, hosted by Chris Rock, is set to begin at 5:30 p.m. PT (8:30 p.m. ET).

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.
Welcome back Hackers\Newbies!

Keeping data private is vital in the days of smartphones and the free-floating information they carry. Justin wrote a guide on many of the deeply hidden and sometimes concerning privacy settings in iOS 7. Now we're back to cover some of the new (and old) privacy settings in iOS 8 that you need to address right now.

There's a 2800mAh battery powering the Samsung Galaxy S5, but even it's no match for the constant day-to-day torture you put it through. Taking photos, watching videos, and playing games can make your fully charged S5 powerless in no time.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

Attention all veterans and active-duty military personnel—this coming Tuesday, November 11th, is Veterans Day, that time of year where the whole country thanks us for our service. For the most part, a simple thanks will do, but some folks like to go above and beyond and give us veterans free or discounted meals and discounts on merchandise in stores.

In order to access blocked videos and websites, you will need to set up a proxy service in the U.S., if you are trying to use Hulu. Go to a list site.

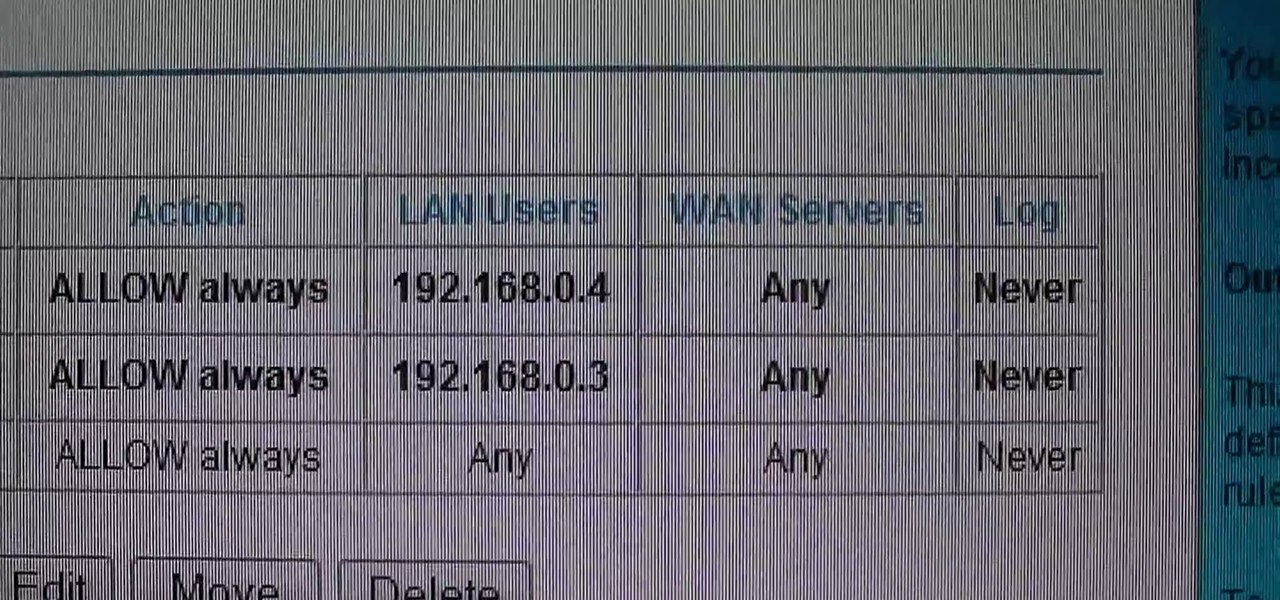
This video shows how to change the NAT type on a PS3. Go to connection settings>network settings>internet connection settings>OK>custom>wired connection>auto detect>manual. Choose an IP address that is different from your router, any other consoles, etc. Click right>automatic>do not use>enable. Press x to save settings, and test your connection. In this example, NAT type is 2. Now go to your PC and open IE. In the address bar, input router IP address, username and password. Go to Firewall Rul...

If you don't have room for a full-scale compost heap, you can always employ the services of some worms. In this handy vermiculture how-to, you'll learn how to build your very own wormery.

With all the documents ready, we need to fill our wallet with money for the travel. This video discusses various ways of filling the pocket. That is how to prepare the money for international travel. Over the years credit cards have been widely used by many travelers, which is safer than carrying cash. In this case we need to contact the credit card provider well in advance and notify them about the travel. Also we need to learn about the various fees applicable to international purchases. Th...