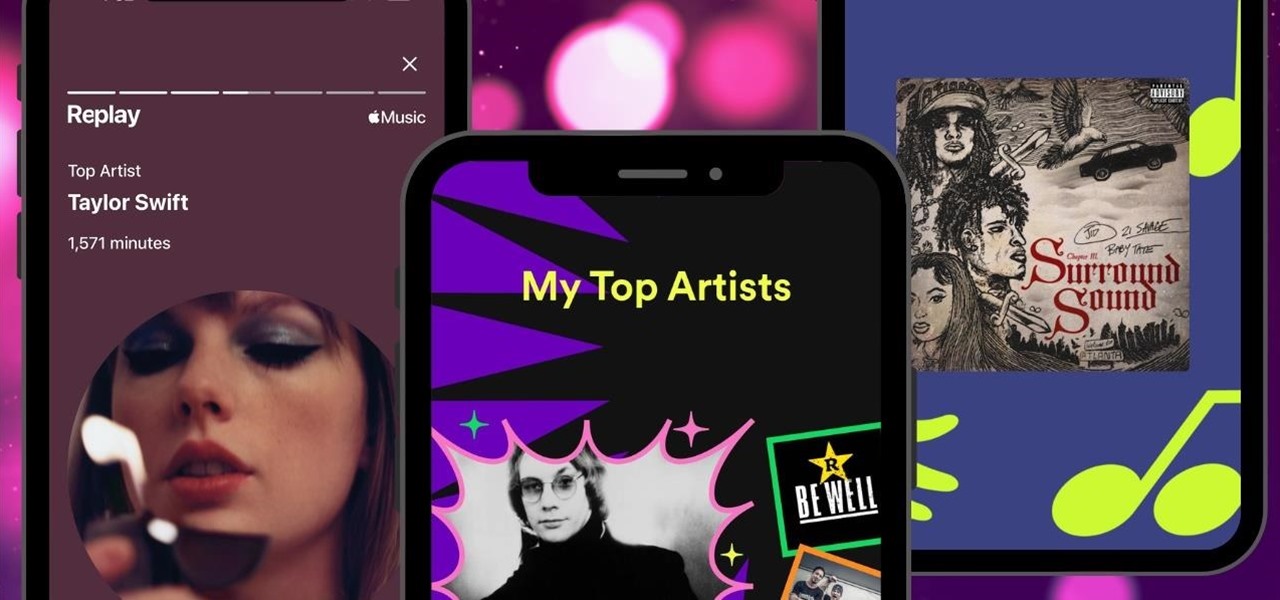
It's that time of year again. No, not the holiday season … the "share your year in music listening" season. And no matter which music streaming service you use, there's a way to find and share (or not share) your activity from 2022.
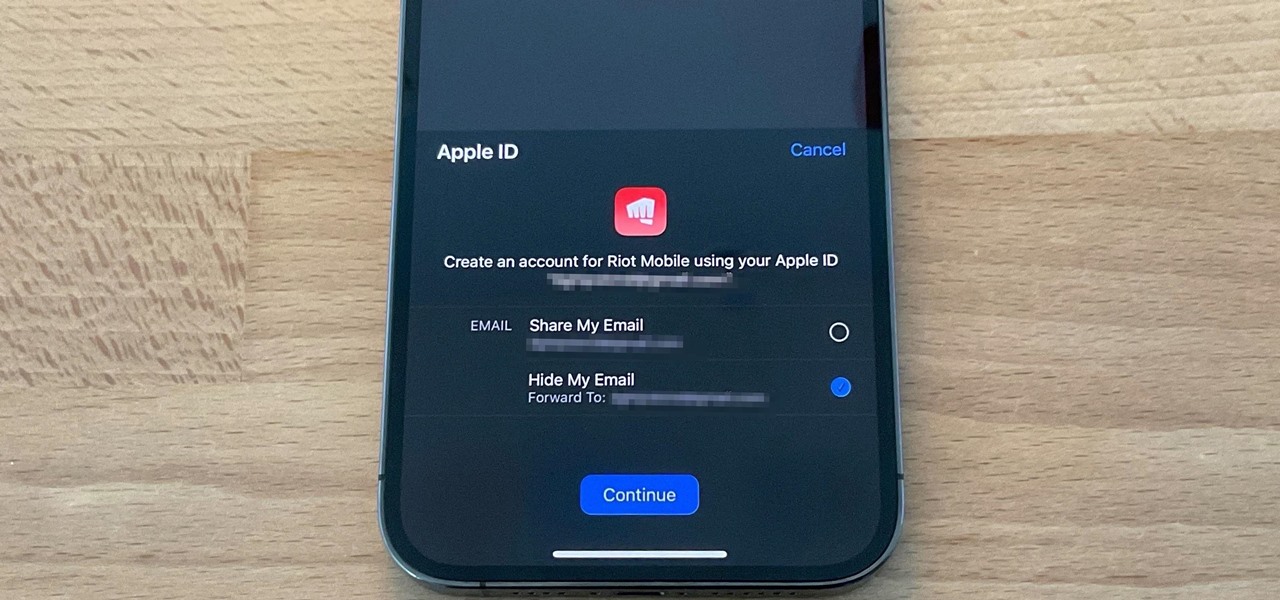
The "Sign in with Apple" service lets you create accounts with third-party apps and websites more easily using your Apple ID. More importantly, it can hide your personal email address using auto-generated disposable email addresses. However, it's easy to lose track of the accounts you use with Sign in with Apple, as well as any throwaway email addresses you used to hide your actual address.

Amazon really wants to make itself at home in your home. Like, everywhere in your home, from your doorstep to your kitchen, your kids' rooms, and everywhere in between.

If you like to listen to popular songs from huge musicians and hard-to-find music from obscure indie artists, SoundCloud is for you — and you don't have to pay a dime. When you find a song you really love and want to play it back even when you're not connected to the internet, SoundCloud has offline listening, but there is a way to download your favorite tracks onto your iPhone for longevity.
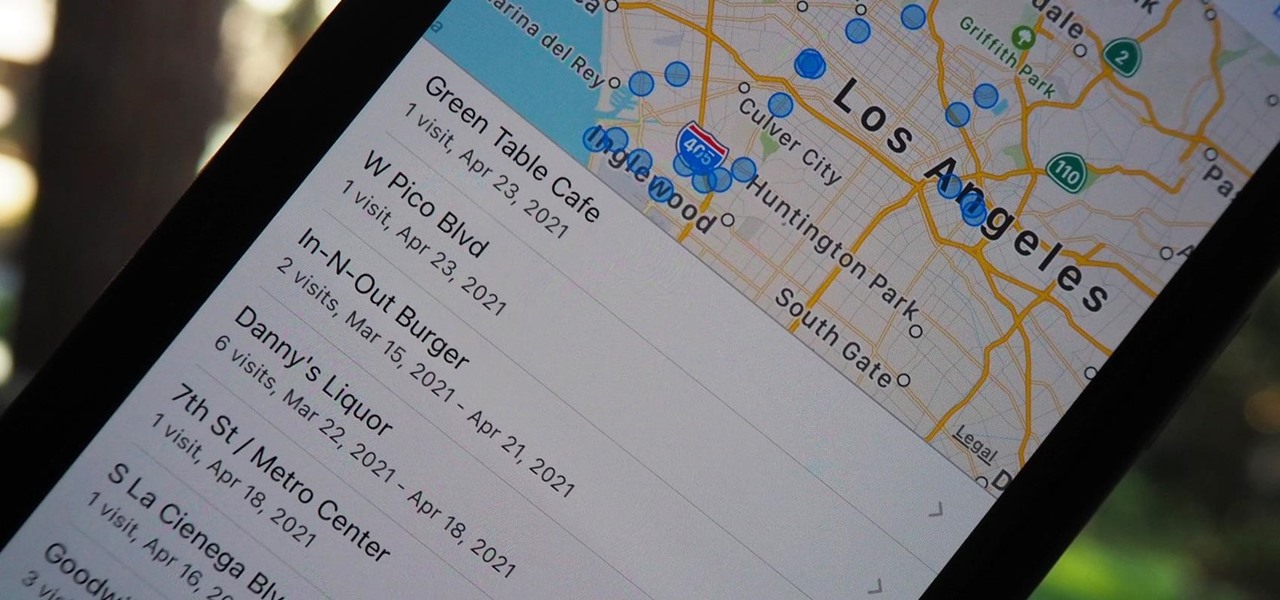
Your iPhone keeps track of every single place you go, especially those you frequent most often, and syncs those locations across all your iCloud-connected devices. People who gain access or already have access to your iPhone, iPad, iPod touch, or Mac may be able to view all of these locations to see where you've been and where you might be. If this worries you, there are things you can do.

Ah, subscriptions. Whether you love or hate them, they are now a fundamental part of our increasingly digital lives. If you have some essential subs on your iPad, iPhone, or Mac, like Apple Arcade, Apple Music, Apple News+, Bumble, Pandora, Tinder, or YouTube Premium, there are three key issues you need to know about that could unexpectedly stop your membership from renewing.

The COVID-19 pandemic forced many businesses into remote work models, whether they were ready or not, making Zoom a household (or home office) name for its video conferencing service.

After a slow phase-out, Google Play Music was shut down in December 2020. The songs you uploaded or purchased are still on Google's servers, but even those will be deleted on Feb. 24, 2021.

Countless third-party apps and services exist that can convert the videos on your iPhone into GIFs. With so many options available, the problem becomes which one to choose. Do you install something on the App Store that provides good quality but costs money, or should you use a shady online service where you have to jump through hoops to get the GIF? Your best option may be neither.

Standard notifications on Android are pretty intuitive, but the little popup toast messages that appear at the bottom of the screen can be a bit elusive. They come and they go, and that's about it. You can't long-press them to change their settings or even tell which app displayed them in the first place.

What does it mean when a software company obsessively focused on innovating the way we use our mobile devices to see and communicate with the world adds virtual voice agents? Possibly e-commerce magic, with a powerful layer of augmented reality.

As we've seen with other tools and utilities, administrators typically use certain things to do their job more efficiently, and those things are often abused by attackers for exploitation. After all, hacking is just the process of getting a computer to do things in unexpected ways. Today, we will be covering various methods to perform banner grabbing to learn more about the target system.

The Music app for iPhone underwent a significant update back in iOS 8.4 when the Apple Music subscription service was incorporated into the user interface. It then had another transformation in iOS 10 that improved the UI for everyone. But things can still feel a little cluttered in Music, even in iOS 14, especially if you don't or never will subscribe to Apple Music.

If you're on a cellular plan with a low data allotment, being thrifty with your data can help you avoid a higher bill. But even if you have an affordable unlimited plan from wireless carriers such as T-Mobile or Verizon, going over a certain amount of data may throttle your connection, leaving you with slow web speeds. One way to prevent hitting these thresholds is to keep certain apps in check.

Waking up to buzzing alarm clock is so 20th century. Wouldn't it better if the first sound you heard in the morning was your favorite song? Whether it's a track to get you motivated or something to put a smile on your face, a song can do wonders for your mood and help you start the day right.

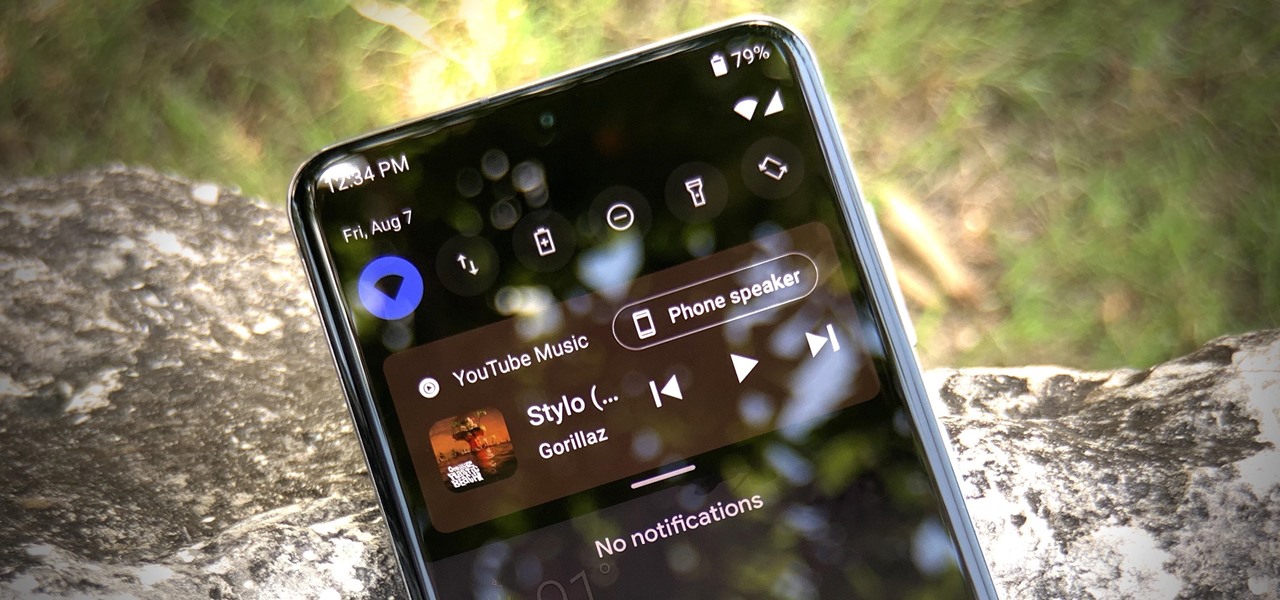
In Android 11, music player controls have been moved from the notification tray to the Quick Settings. The change frees up space for the new Conversations notification section. It also adds media output controls, making it possible to switch from your phone speakers to a Bluetooth device with only two taps.

Instead of using a single APK, YouTube Vanced recently started being distributed as a bundle that requires a third-party app to install. Some fans found this too difficult, so the Vanced developers decide to make the process easier.

If you've jumped on board HBO Max to watch more than just HBO's content, such as DC films, Looney Tunes, Turner Classic Movies, Cartoon Network, and movies from Warner Bros., there is a downside to HBO's improved service. Namely, you cannot use it on all of your devices yet. The most notable omission is Roku players and TVs. But there are workarounds you can use until an official app comes out.

With every new Galaxy flagship release comes the age-old dilemma: do I choose great hardware or great software? For years, Samsung has given users the best components available on any smartphone. The problem is the software is an acquired taste. But there is something you can do about it.

So far, iOS 13's major point updates have all been pretty exciting for iPhone. We've seen iOS 13.1, 13.2, and 13.3 come and go, offering more than 60 new features and changes combined to that very first version of iOS 13. While iOS 13.3.1 was a minor update, its successor, iOS 13.4, is a return to form.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

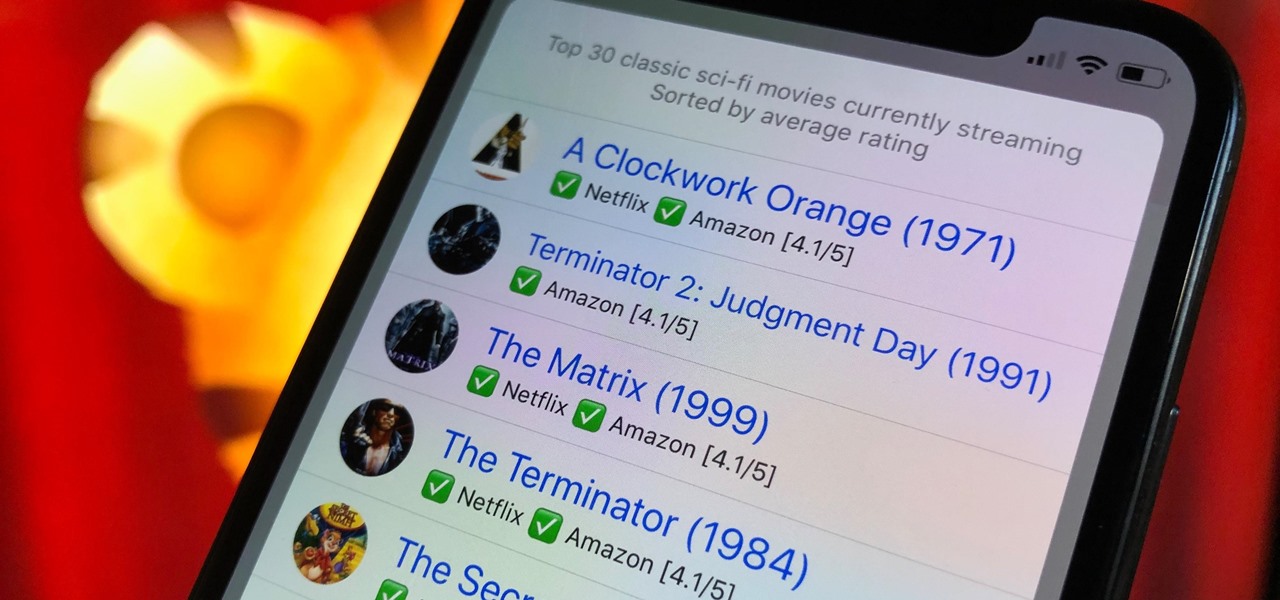
Choosing a movie to watch at home can be incredibly difficult when you don't already have one in mind. But there's a shortcut for your iPhone that can make it easier to browse your streaming media services for something good to play. More specifically, it lets you browse Netflix and Amazon Prime at the same time.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.

Apple released iOS 12.3, the latest version iOS 12 for iPhone, on May 13. Great features to know about include Apple TV Channels such as HBO and Showtime that you can subscribe to in the TV app, support for audio, image, and video streaming to AirPlay 2-enabled TVs, and the ability to use Apple Pay to pay for content and subscriptions inside Apple's own apps.

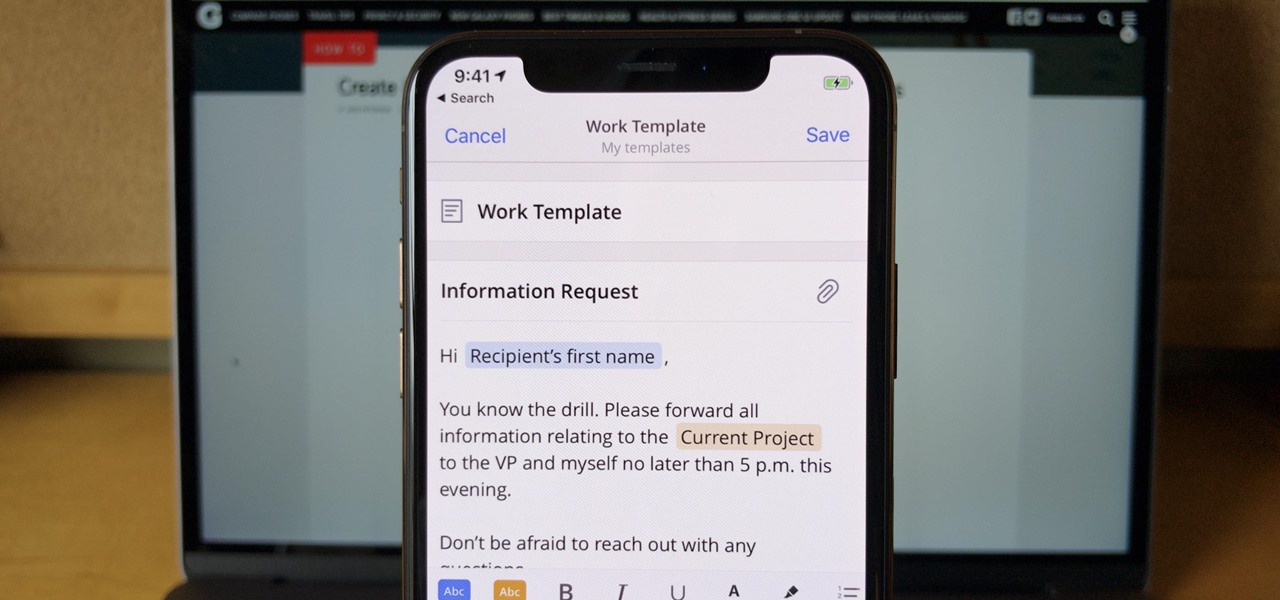
If you find yourself emailing the same email over and over again with just a few changes such as new addressees, or if you're constantly replying to messages with the same response, typing it out every time is, well, a waste of time. Spark, a third-party email client for mobile devices, takes all the work out of this — no matter which email account you need it for.

Planning a vacation overseas can sometimes feel overwhelming with the number of things you need to remember before heading out. Since smartphones keep us connected at all times, it's essential that you have everything you need here as well. Unexpected events can arise while on your trip, and you should be prepared for anything like a survival expert.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

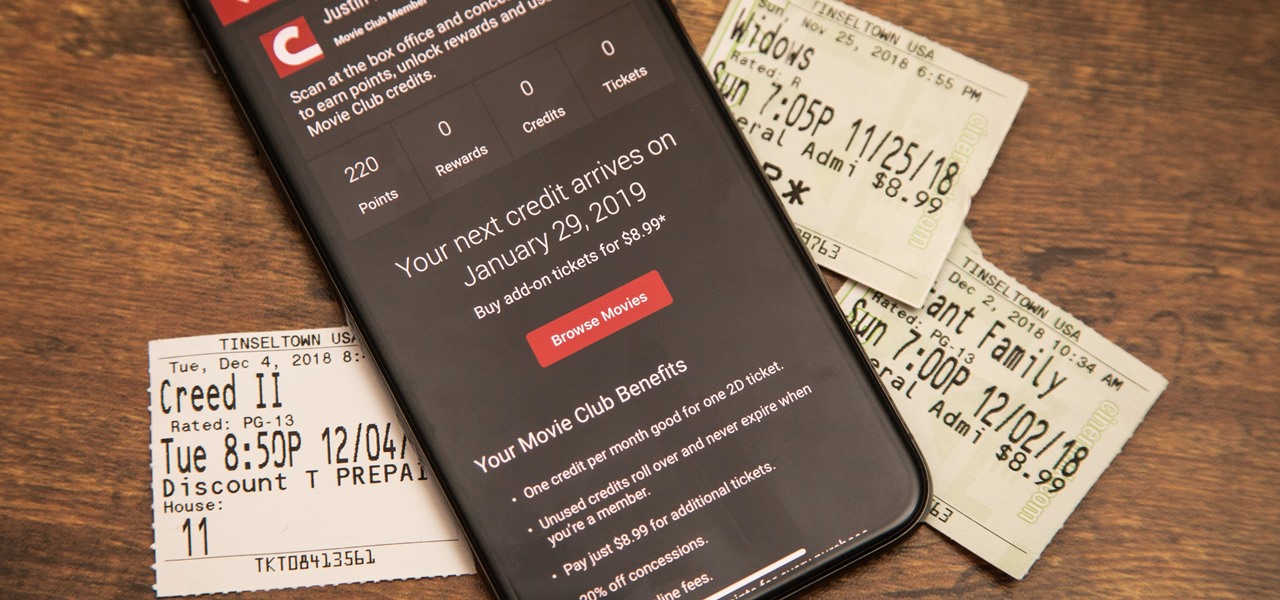
Cinemark may not be as big as AMC Theatres, but it also has a subscription if you want cheaper access to movie tickets. There aren't as many theaters, but if there's no AMC around you, there will likely be a Cinemark to save the day. But is the price of its Movie Club plan worth it?

You might think you need to buy a thousand dollar phone to get a great experience while streaming movies and TV shows from services like Netflix, Hulu, and YouTube, but that's just not true anymore. While phone prices keep rising and the midrange segment now ranges from $300–$500, there are still cost-effective options that come with top-notch displays and media features.

The idea of a perfect phone is a myth. There are lots of pros when it comes to OnePlus devices, but there are also a few things that could be better. And even if there were a phone without flaw, there are still things that you might want to customize for personal preference. That's why we set out to find the very best tweaks for OnePlus phones, and to make it easier for you to apply them.

It's that time of year again. No, not Thanksgiving. Black Friday. There are a lot deals available this holiday weekend, many of which include flagship Android devices. Whether you are thinking of buying a phone for yourself or looking for a gift for someone else, you can find a little savings to shop smart during the holidays.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.