The Holy Grail of chicken has just been found by an unsuspecting reporter of the Chicago Tribune. Yes, that's right: The secret 11 herbs and spices in Colonel Sanders' Original Recipe chicken has finally been revealed, and it looks legit as hell.

If all things go well, you'll only have to take your road test once. That's the goal: to ace your test on the first try and then start driving on your own. Granted, it's a nerve-racking experience, but keep in mind that the California Department of Motor Vehicles wants you to pass. So much so, they give you the examination answers ahead of time! All you have to do is study.

So... This is a prank on a prank. The first prank involves everyone getting drunk one night and drugging the "victim" (say a friend of a friend, because any jackass member would know it's a prank) to the point of unconsciousness, tearing portions of their clothes and leaving them covered in fake blood in the middle of the forest surrounded by fake dead animals (humans preferably). Thick Werewolf type hair could be stuck to the blood against their skin to imply that they were turned on that fu...

For those who were creeped out by the Knoxville mannequin, well now i've outdone myself! Just like Jackass has taken their game to a whole new level with 3D, i've taken mine to a new level...the Jeff Tremaine sex doll! Though I can't take full credit for this doozy, because Mr. Julien Nitzberg(genius behind The Wild Whites of West Virginia) came up with the idea. He suggested I make one, and he would hand deliver it to Mr. Knoxville himself(for reasons only to be kept secret).

We've all been there before: We're in a hurry to get somewhere (often in bad weather), so we get in the car, turn the key in the ignition and.....WHUH! WHUH! WHUH! The darned battery is dead! After a stream of choice expletives (that is, if you're anything like me....;o)), we open the trunk and take out the jumper cables - but what if we don't know how to use them? Even if we do, we can often forget such things in crisis situations when we're pressed for time.

Etching your own circuit boards is tons of fun, but etching requires strong chemicals to dissolve the copper plating on blank circuit boards. The normal ferric chloride solution works well, but can be expensive and leaves permanent stains. Luckily, we can whip up our own etchant at home with everyday chemicals! Better yet, our new etchant will turn an eerie green color rather than the dull brown of ferric chloride.

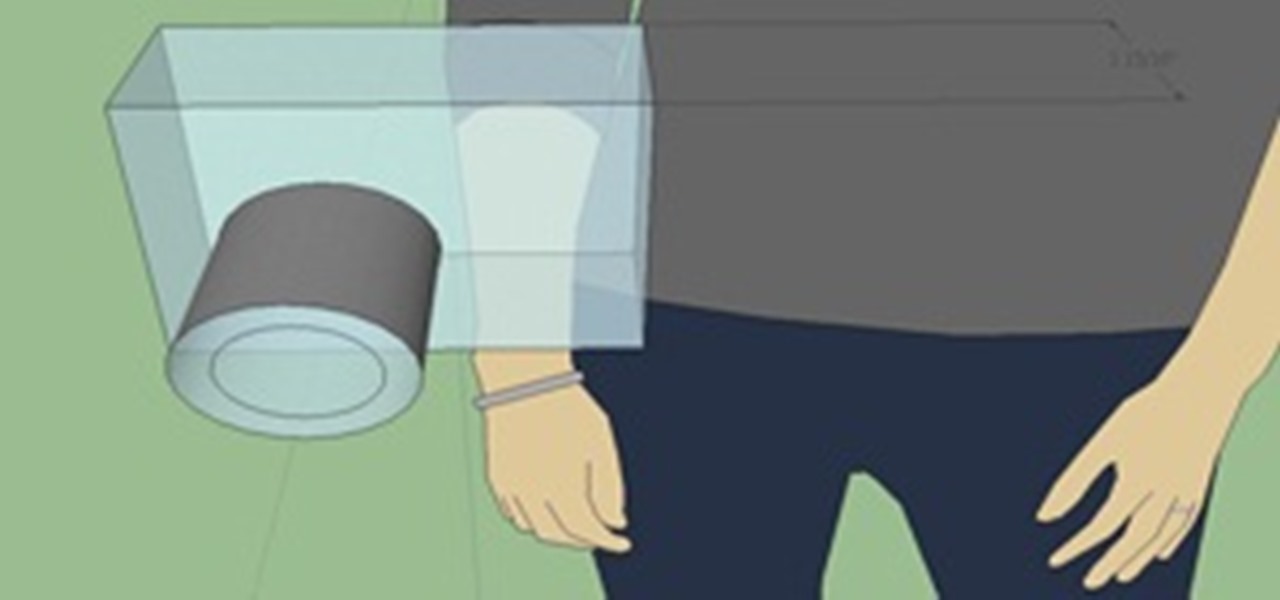
Creating any object you want is as simple as point and click if you have a 3D printer at home. If you don't have one handy, there are a few companies that offer printing services online. But to help services realize your design in extruded plastic, you have to make a 3D computer model for the printing machine. For beginners, the free Google SketchUp application is the best choice of software. Using only a few tool bar buttons and a scroll wheel computer mouse, you can model literally any obje...

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Need help getting started on this week's WTFoto Challenge? Look no further! In this tutorial, I will teach you how to create simple chalk symbols and writing in Photoshop. So read through this post and try it out yourself—or I'll tell your cousin what you said when you were drunk that one time. Keep in mind that the steps are similar for other programs, such as GIMP.

The agents of empire do not always arrive with warning. When you are besieged, surrounded, and infiltrated, imagination is often your best weapon against the oppressors. If all you have at hand is some duct tape and a disposable camera, fear not, you have the makings of a powerful taser!

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

Since the internet is becoming more and more important all the time in regards to overall marketing plans for many companies, it’s imperative that the company website be up to the task of attracting visitors and converting them into customers. There are many methods and techniques to do this and for that reason it’s usually preferable to hire a company that focuses on online marketing or search engine optimization (SEO) to do this work.

This article is all about creating content. This is a very important concept to grasp because the content that you will learn how to create is going to be the basis for how you will advertise and promote your website. Content, meaning articles, videos, and even podcasts. Content is now really the new advertising. Instead of traditional types of advertising and instead of the traditional separation between editorial content and advertising, that has gone the way of the dinosaur.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Part 5 in Minecraft World's Ultimate Survival Guide is, for me, the longest article to write. Since I squeezed out a lot of information from other areas to put into survivability, its going to be a fairly long read. Of course, you can just skip to your topic of choice.

Skyrim is an enormous RPG recently released by Bethesda. After many long years of waiting (I had 1000's of hours clocked into its predecessor, Oblivion, way back in 8th grade) the game is finally out and it surpasses everyone's expectations—save for removing custom spell crafting... Why, Bethesda?

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. UPDATE: Minecraft 1.9.6 has been leaked!

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. While mining is a basic aspect of Minecraft, it is often overlooked. Every adventure requires iron and diamonds and other ore and if you're playing in hardcore mode then you need all the help you can get.

PVC isn't something you want to send to the landfill. It's not going to do anything good for the ground when it's buried. It is also something you really, REALLY don't want to send to an incinerator. When burned, PVC releases some really nasty chemicals, including hydrochloric acid and dioxin.

I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

If you're interested in bypassing Windows and Linux passwords, there is a great tool from the good people at Kryptoslogic. Have you ever forgotten your administrator password? Have you ever bought a used computer with a password on it? Well, Kryptoslogic have created a boot-disc call 'Kon-Boot', which allows you to bypass any Windows 32 or 64 bit OS, as well as Linux passwords. There is both a paid and freeware version available.

Culinary collective Studiofeast is known for thinking outside the box, especially when it comes to food. They've hosted inventive and spectacular events like the L Train Lunch, where a high-end meal was served to guests on a moving train, and the Datalicious Last Supper, where results from a survey of people's desired "last meals" informed the menu.

If you've gained entry into Google+, one of the first things you should do is adjust your Google account settings. Your settings will now look quite different, and you can adjust your notifications, password retrieval methods, and more. There are many settings that you may not have been aware of before.

It's no secret that Apple has retail stores in China, along with a large amount of Premium and Authorized Resellers. But a recent post by blogger BirdAbroad has caused quite a commotion in the world of all things Apple, claiming that in her home city of Kunming, there is another breed of Apple Store locations... "Un"Authorized ones.

The relationship between developers and publishers in the video game industry has always been awkward. Many great game developers such as Bizzare Creations, Clover Studio, and Bullfrog Productions have been disbanded due to corporate shenanigans involving their publishers and owners. The indie game movement has risen largely as a response to this.

Introduction to the Basics of Off-Camera Flash

It's never too late--in fiction or in life--to revise - Nancy Thayer, author
Long-Term Strategies for FrontierVilleWhen you first start to play FrontierVille, after you’ve cleared a bunch of trees and brush and started to build a schoolhouse or a barn and you’ve added a few neighbors, you look up at the people around Level 90 or Level 100, and wonder how they play the game and how they got that far.There’s a book (or a series of four books) you may notice – FrontierVille Tycoon Guide – that promises to tell you the secrets of the high level players. You can buy it on ...

Making your way into an online community can be really exciting. Some life-long friendships and lasting romances begin in humble chat rooms and message boards. But for the novice internet user, one of the biggest hurdles can be trying to figure out just what people are saying to one another.

Business owners and marketeers are diverting from traditional marketing techniques, including billboards, radio and TV advertising, brochures, and any other outdoor promotions, to cheaper but effective Internet marketing strategies. Under the new arrangement, business owners reach out to the final consumers through advertising on the World Wide Web.

Have you ever noticed that whenever you setup your voicemail account after getting a new cell phone number, it asks you to create a security pin to access your voicemail from other phone lines?

These easiest way to create contact pages for your WordPress blog is with a plugin. Not fuss needed. These two videos attempt to tell you how you can create contact forms in your WordPress blog with the Contact Form 7 plugin. The "contact us" page made easy!

With careful wording you can avoid lying and still avoid going to something that you just don’t want to attend. Even without a good excuse you can politely decline without hurting anyone’s feelings or ending up in an embarrassing situation.

Although mainly demonstrational, this video shows you how to play the song "Whistling Rufus" by Kerry Mills on guitar. This video is aimed more towards advanced players who learn easily by watching or listening. Read the useful tips posted below:

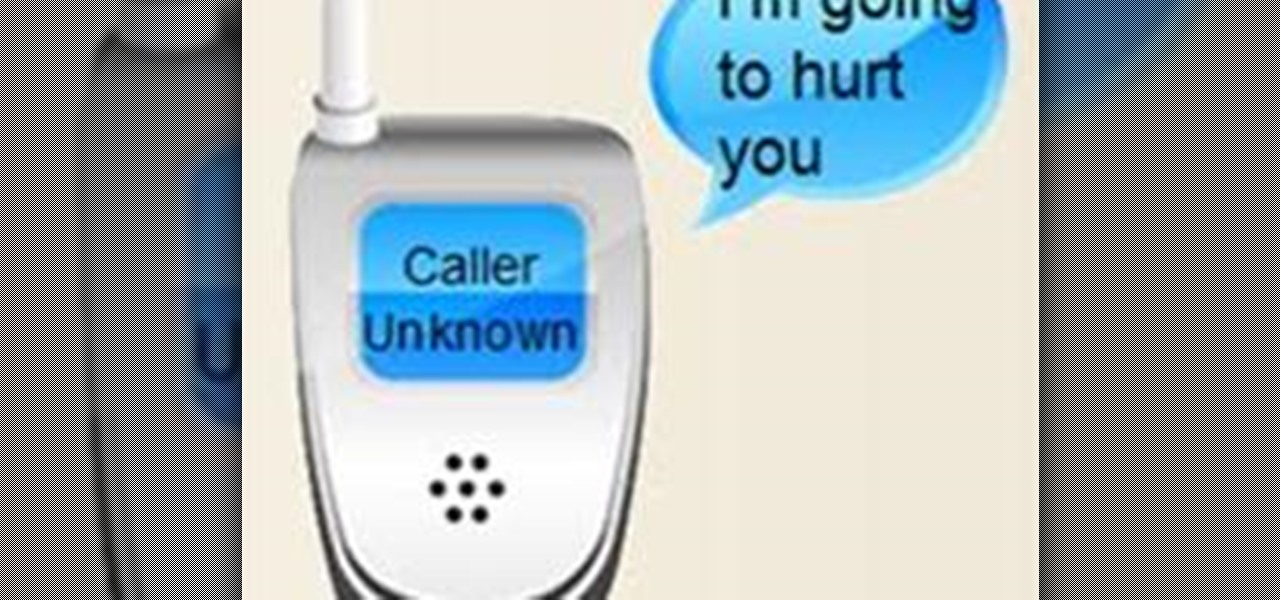
Prank Calls, Masked NumbersWho is calling your phone or your child's? Pranksters use a lot of tricks to make sure they can get on your nerves. Being able to trace prank calls is important because you're not going to learn much from your Caller ID, since most prank callers use an unlisted number - such as, a cell phone number. Many also use special code *67 to mask the number so your Caller ID will show "Blocked Number" or "Private Number". There are a lot of mild cases of so-called phone bull...

The last few months of WikiLeaks controversy has surely peaked your interest, but when viewing the WikiLeaks site, finding what you want is quite a hard task.

The key to this skit is to get someone incredibly drunk to the point that you can move them without their knowledge. As soon as they pass out, dress them in an orange jumpsuit and take them to a prison or a studio made to look like a prison. The cell-mate (actor) needs to be someone who looks like a big old biker, and is named “Sweetheart,” who makes a lot of references to the victim’s ass hole. When your victim wakes up, they will be in the jail cell completely confused. Sweetheart will say ...

If you don't want to be found on Twitter, there are several ways to do that without making your account private. For instance, you can choose an obscure username, omit your real name, or pick a random avatar. But there are lesser-known features deep in your settings that can also protect your privacy online, including preventing photo tags.

Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate copied apps independently, thus giving it an unprecedented layer of privacy and freedom within your handset.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.