The sprouts, they're alive! Alive, I tell you—aaaaaaliiiiiive! (Cue dramatic music.) It's true: sprouts are a living food, and they're packed with more nutritional benefits than some raw vegetables. It's easy and fun to grow your own sprouts from seeds, legumes, and grains. Plus, watching them grow is incredibly satisfying—you're bringing new life into the world (and onto your plate)!

Hello Guys, Today I have made a script for ddosing sites with VBScript! And I don't know how you guys do it, but I've made a script that refreshes the page in a chosen amout of milliseconds. And if you want it a number of times or if you want it to go on and on. And this is a script to run it on your botnet. But again I don't know if this works on your botnet too.

Why, for the love of God, do people keep inventing ridiculous devices that make the simplest things more complicated in the name of convenience? This may be a rhetorical question that will forever go unanswered—because these crazy gadgets just keep rolling out, one after the other.

Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up for a ransom.

There are countless recipes for mug cakes (and breads) on the internet, but not all of them are good. Mug cakes promise a warm, moist, and fluffy cake after a few minutes and with minimal work... but sometimes, all you end up with is a chewy, rubbery mess.

Greetings, fellow NBers! Welcome to my sixth iteration of my sorting series. Today, we'll be discussing a personal favorite: Quicksort, or Quick Sort.

Creamer, milk (whole or skim), sugar, or even butter—you've probably added at least one of these to your coffee to improve its taste at some point. If you're looking for something different, though, try a new twist with a dash of cinnamon. This sweet, sharp spice can do so much more than improve coffee's taste, and I've got 10 examples for you to consider.

Local cafés and food bloggers are catching onto a gourmet toast trend that makes bread and butter look like movies before color TV was invented.

Valentine's Day is upon us, and it's the perfect time to show those you love (or like) how you feel about them by making them a homemade sweet treat.

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

Greetings my fellow hackers.

Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

The sheer variety of Android devices on the market is staggering—one report suggests there are well over 24,000 distinct phones and tablets floating around out there. When you consider that each manufacturer adds a few tweaks to the Android code base here and there, that makes for a lot of software variations, which in turn means there needs to be many different root methods to match this variety.

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

The start of a new year is generally thought of as a chance to start over, a time to improve or "fix" things in your life. Yet most people who set stringent New Year's resolutions find themselves failing within weeks—or even days—of setting their lofty goals.

Switching your favorite facial cleanser isn't an easy choice. Since everyone's skin type can range from dry, to oily, to some complicated combination of both... well, let's just say that the conventional wisdom is to stick to what you know works.

Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, skills and a whole lot more that comes out as a result of pursuing hacking. What we mean by hacking on this forum is White hat Hacking and OTW has great articles on it and I don't need to explain myself on that one.

This is my first How-To on Null-Byte, so I hope it's not too complicated written, because I am not a native english speaker. I don't use pictures, but this Tutorial is a good supplement for my updated Tutorial here.

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

Hello again, reader! In this post, we are going to cover some data types and how to declare variables. It shouldn't be too hard so just sit back, relax, grab some popcorn and enjoy the ride (while you still can!).

During my time living in dorm rooms and small apartments, I would find myself in need of many different appliances—a food processor for making hummus, a blender for vegetable smoothies, or even a mortar and pestle for muddling mojito-bound mint leaves. Luckily, there was one tiny, inconspicuous tool that solved all of these problems: the coffee grinder.

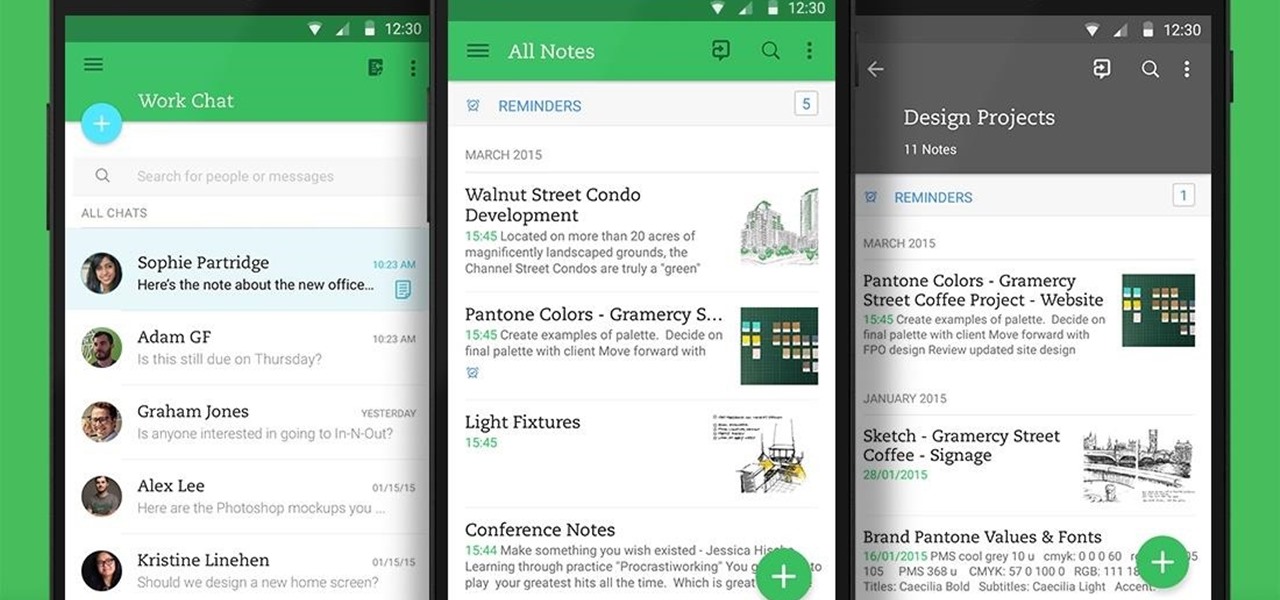
Not many people use their phone exclusively for making calls or sending messages today. If you're an Android user, the chances are high that you're using your phone or tablet for work-related activities. However, the basic set of apps and services your device was shipped with won't satisfy most users. The good thing is that Google Play Store has a nice selection of productivity apps for every task. Below you'll find a list of apps that will help you gradually optimize and organize your digita...

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

Reddit, the self-proclaimed "front page of the internet," continues to take a big bite of my free time each and every day, as well as millions of its other users'. The clicking and scrolling through page after page never gets old, but you could speed things up with a few browser extensions and double your Reddit knowledge in half the time. Here are my favorite extensions you can try out for the Chrome, Firefox, and Safari web browsers.
Welcome back Hackers\Newbies!

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

In case you didn't know, Android has an awesome hidden settings menu called "Developer options" that contains a lot of advanced and unique features. If you've ever come across this menu before, chances are you just dipped in for a minute so that you could enable USB debugging and use ADB features.

There are many hacks for increasing productivity, but so many depend on tricking your own mind or behavior. When it comes to motivation in the workplace, though, sometimes the space within which you work dictates how you behave and the work you produce. So if you want to increase your ability to get more done in a single workday while doing a better job, consider changing your surroundings in the following ways.

In the world of breakfast, a great trench of injustice divides French toast and pancakes. Just look at the average brunch menu. While pancakes are treated to a wealth of variety (chocolate chip, silver dollar, blueberry, banana, and even some with pop culture references), French toast is often regarded with a one-size-fits-all attitude.

Cortana, Microsoft's voice-activated personal assistant, originally launch on Windows Phone, but is now built directly into Windows 10 complete with "Hey Cortana" voice search (take that, Apple). It can help you locate files, set up reminders, control music.

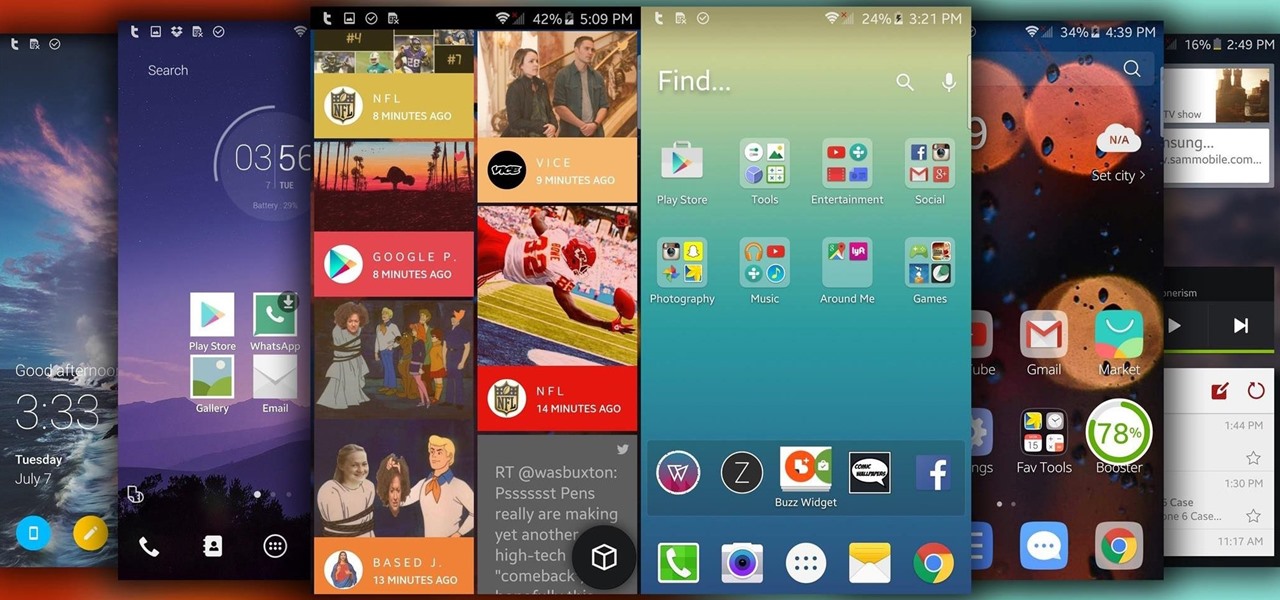
I'm often reluctant to use a home screen launcher other than the stock one on my Android. Once you're well acclimated with something, complacency sets in, welcoming change with much resistance. Well, my friends, I have seen the error of my ways...

Protein powder is a fad in the same way that Justin Bieber's music is: you either love it, or you hate it. Everyone I know has a strong opinion about protein powder, ranging from "daily necessity" to "utterly useless."

For most of us, the primary reason we capture videos on our iPhones is to post on one of the various social media platforms out there, like Facebook, Instagram, Snapchat, or Twitter, providing instant gratification by receiving a proverbial nod from our followers.

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

When it comes to smartphones, the biggest complaint voiced by most users is battery life. Sure, it's unrealistic to expect your Android device to run for weeks without a recharge, but many folks struggle to even make it through the day without having to top off their battery.

At last, what you all finally waited for! Hi! Fire Crackers,