
How To: Make straight lines
Learn how to make a simple device out of stuff you can find around the house (including a bubble tape container). You'll have straight lines each time you use this device.


Learn how to make a simple device out of stuff you can find around the house (including a bubble tape container). You'll have straight lines each time you use this device.
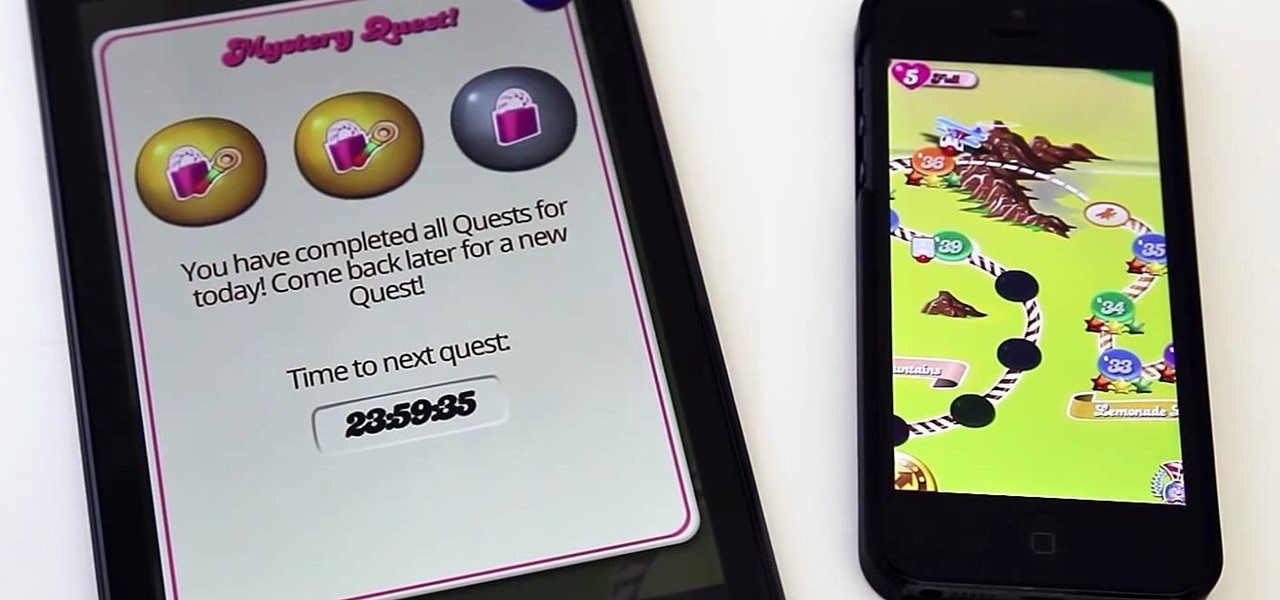
There's an easy time hack available for Candy Crush Saga that let's you bypass the time restrictions to you can play more games faster, and this video guide from KiboshGaming will walk you through it on both Android and iOS devices.

Today's the big day for all Apple fans to start updating their devices to the new iOS 5, which has many improved features compared to its iOS 4 predecessor.

One of iCloud's most exciting features is automatic download. It means that when you download something from the App Store on one device, it downloads onto all of your devices. No more going back and forth between iPad and iPhone, all of your music, movies, and ebooks in the same place.
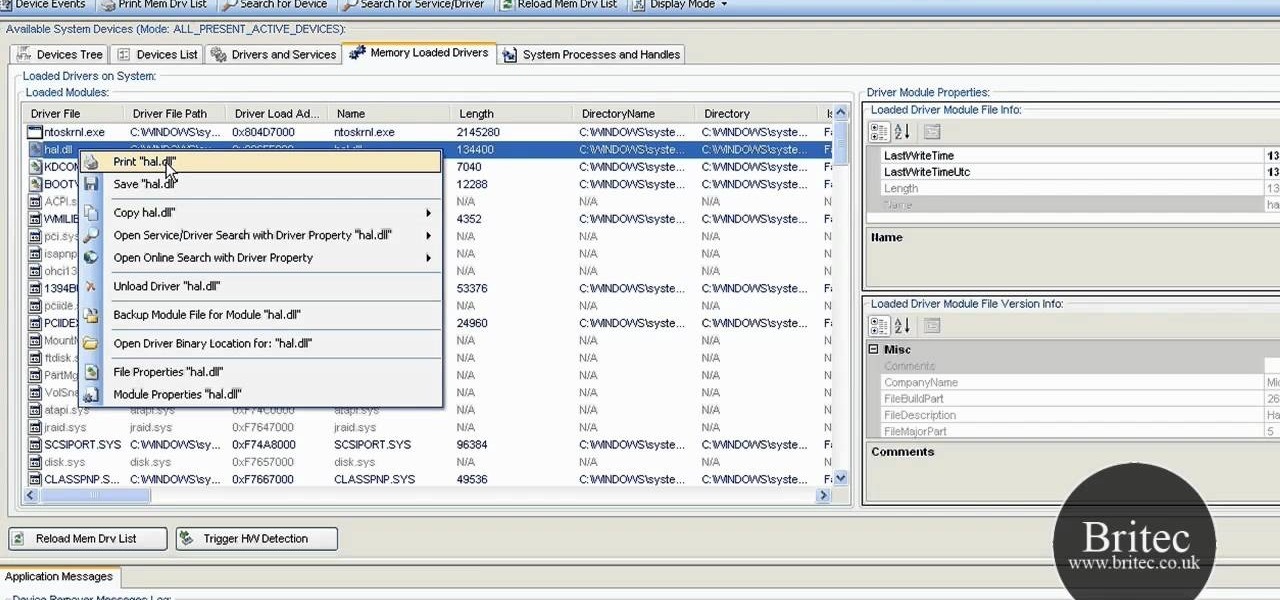
Looking for a solid alternative to MS Windows' default Device Manager? This clip will teach you everything you'll need to know. It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over six minutes. For more information, including detailed, step-by-step instructions, take a look.
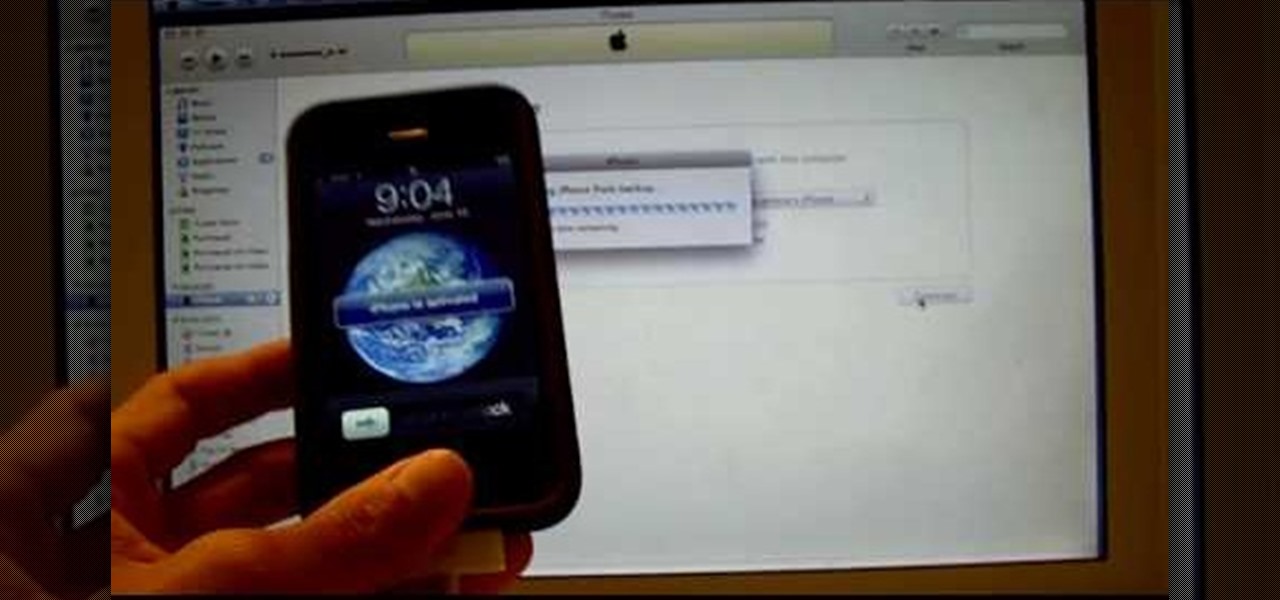
In this Electronics video tutorial you will learn how to update your iPhone and iPod Touch firmware 3.0. You will need iTunes 8.2 and the firmware from Deposit Files. Go to the website and download the firmware. This will take some time. Use Firefox browser for the download. Now make sure your device is clean, i.e., it is not jailbroken and connect it to the computer. Then open up iTunes on the device for this hold down ‘power’ and ‘home’ until the device switches off and then powers on. Once...
If you are sick of hearing that recorded robotic voice on your GPS device, check out this tutorial. In it, you will learn how to record your very own voice (or that of a friend or loved one) and have it give you directions instead! This can make for a pretty cool prank on someone as well. So, check it out, it's super easy and all you need is a PC with Windows and a small download.
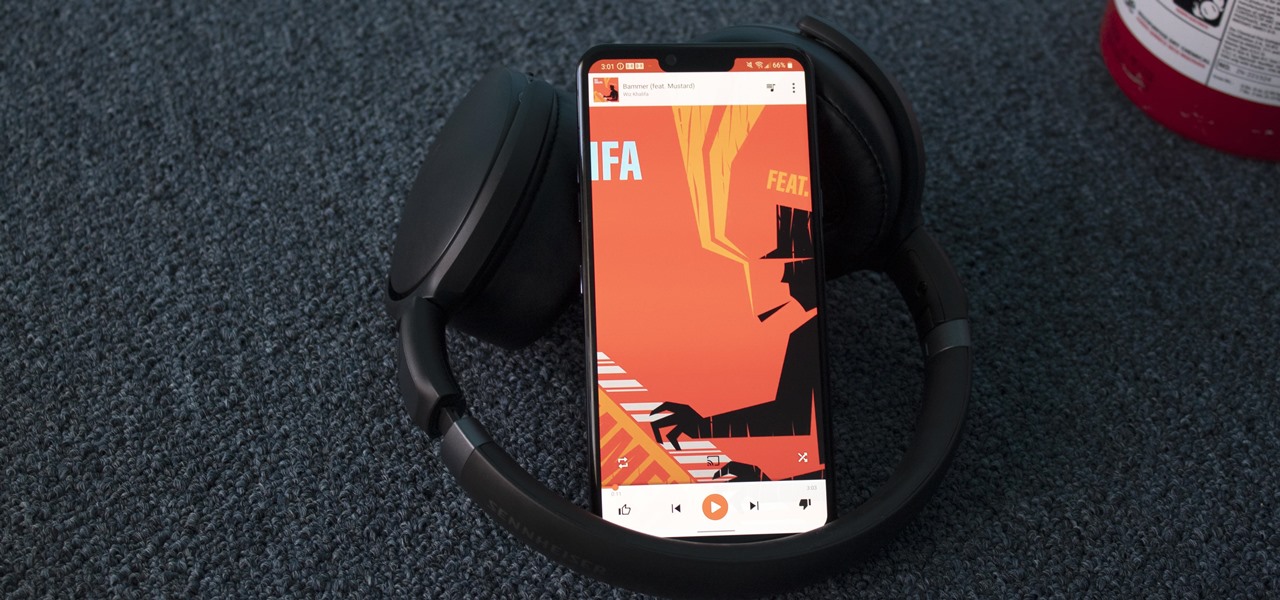
For audiophiles, few smartphones come close to LG flagship devices. With either the latest G series or V series phone, you can be sure you're getting the best audio experience of any smartphone thanks to Quad DACs and headphone jacks. And with some tinkering, you can make this experience even better.

Part of the fallout from the canceled Mobile World Congress is that a range of products, ideas, and designs slated for reveal in Barcelona are now being showcased without the framing and context of the massive tech gathering.
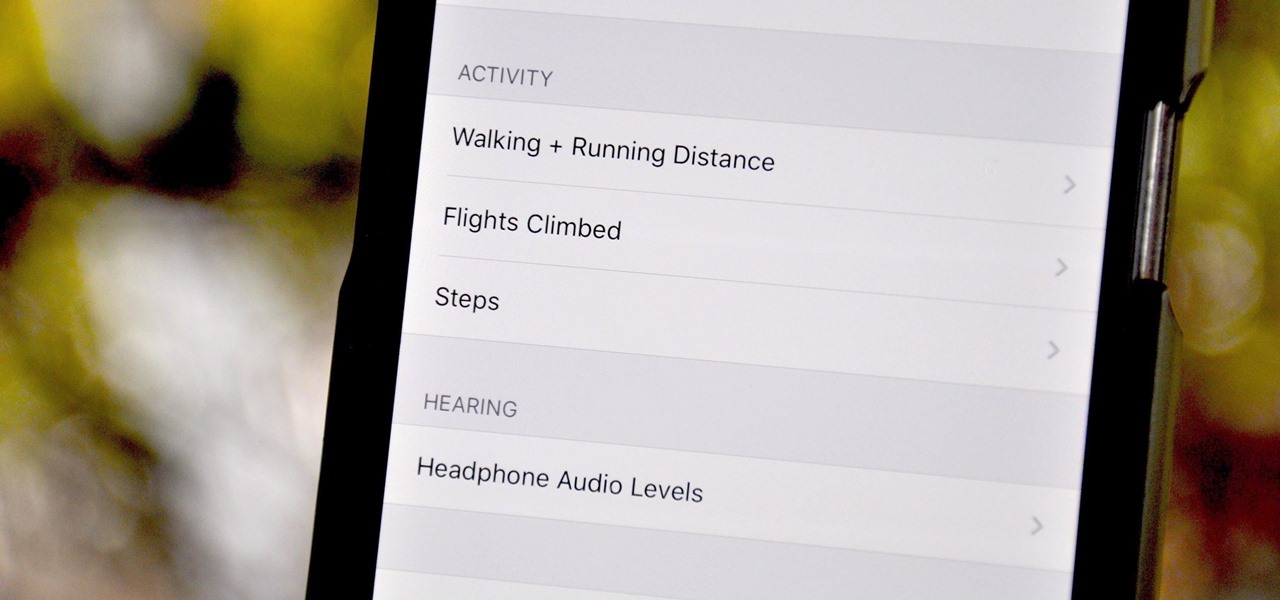
Your iPhone tracks how many steps you take, how far you walk, and how many stairs you climb each day. That may seem a bit frightening, but it's all for a good reason: the Health app stores this data so you can view your progress in one place. But interestingly, opening the Health app isn't the easiest way to view this info.

Let me paint a picture for you. You're on a long flight home, and while listening to music on your Samsung Galaxy S10, a great song comes on. You want your friend to hear it too, who's also listening to music using a pair of Bluetooth headphones. Thanks to Dual Audio, you can easily share your experience.

In the technology space, there are certain brands you grow to depend on. Whether it's due to a long, multi-decade track record of success, or new innovations that blow you away, some tech names accrue a rare kind of brand equity with users that's difficult to earn.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

Traditionally, if you were looking for end-to-end encrypted messaging, you'd stick with something like iMessage, WhatsApp, or Signal. However, if you already use Facebook Messenger, you have all you need for truly private chats with its built-in E2E encryption. It's available to all users, on Android and iOS — you just need to know where to look.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.
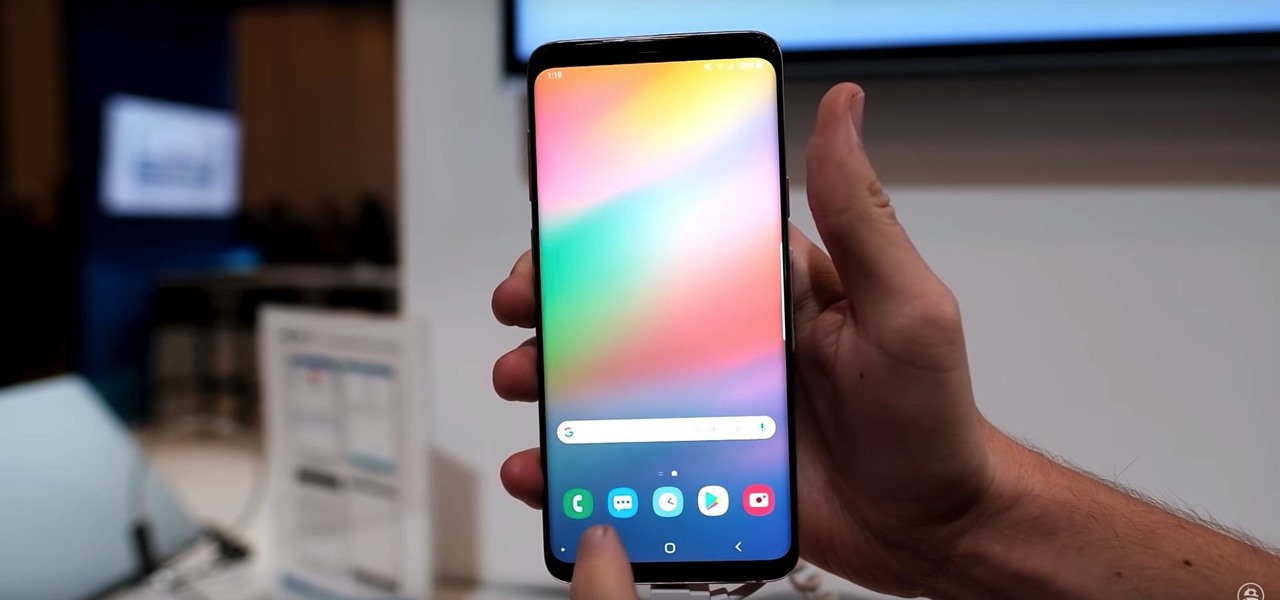
Who doesn't love a refresh? Samsung's upcoming One UI makes it easier to use your device with one hand and adds a fresh coat of paint to the formally "Samsung Experience" skin. While you're probably looking forward to installing One UI on your phone, not all Galaxies are equal — your device could be one of the first to receive the update, or it could never see One UI at all.

One of the main reasons Authy was able to top our list of the best two-factor authentications apps was its ability to transfer access to a new device. This feature ensures that whenever you get a new phone, you don't lose all your tokens. However, if the process is done incorrectly, you can leave your account vulnerable.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

Although the Magic Leap One: Creators Edition is currently officially available in only six US cities, those living outside of Magic Leap's designed US cities now have a roundabout way to order the device.

In recent days, I've twice talked about brining the Magic Leap One out into the world with me to test its mobile capabilities. But you may have been wondering how I carried the device with me. Did I just stuff my brand new $2,300, hard to obtain device in a backpack and hit the road? Hardly.

The roster of handsets supporting Google's augmented reality toolkit now includes 46 Android models as well as support for ARKit-compatible iPhones and iPads.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

On Wednesday, June 6, the people at Magic Leap finally (FINALLY) decided to give the public a dedicated, slow, feature-by-feature walkthrough of the Magic Leap One: Creator Edition. How was it? About as good as it gets without actually getting to see what images look like through the device when wearing it.
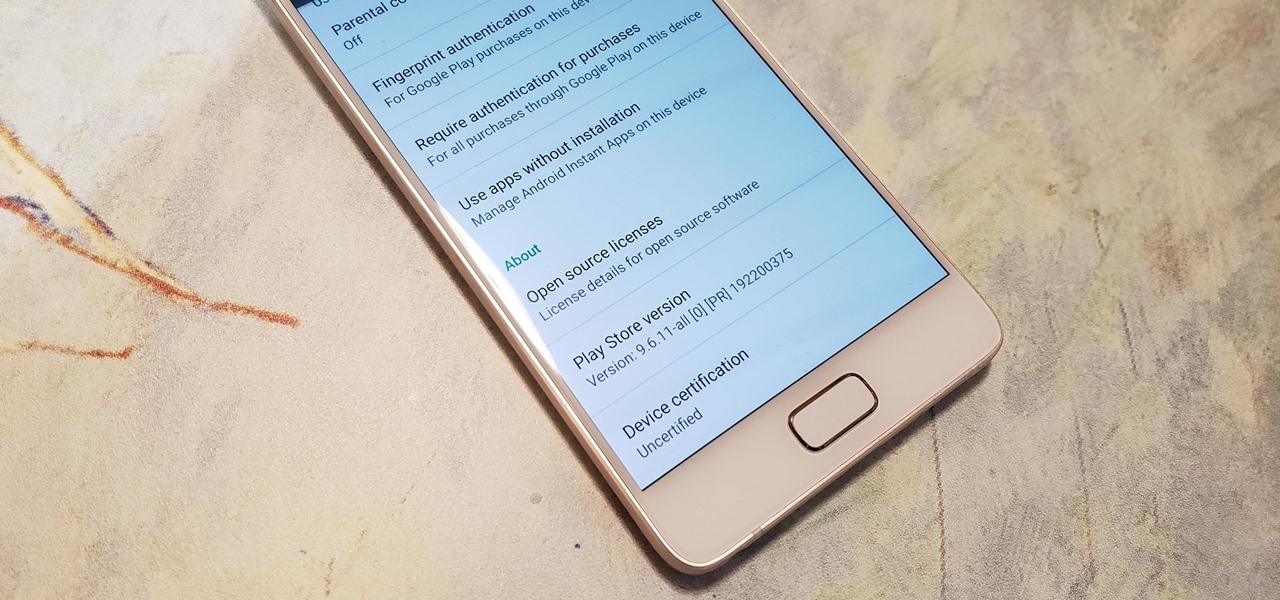
Google has started blocking certain devices from accessing the Google Play Store and other Google services. This is part of an effort to clamp down on OEMs that skirt its certification requirements, but now millions of phones have been uncertified to download or update Google apps. Fortunately, there are a few workarounds.
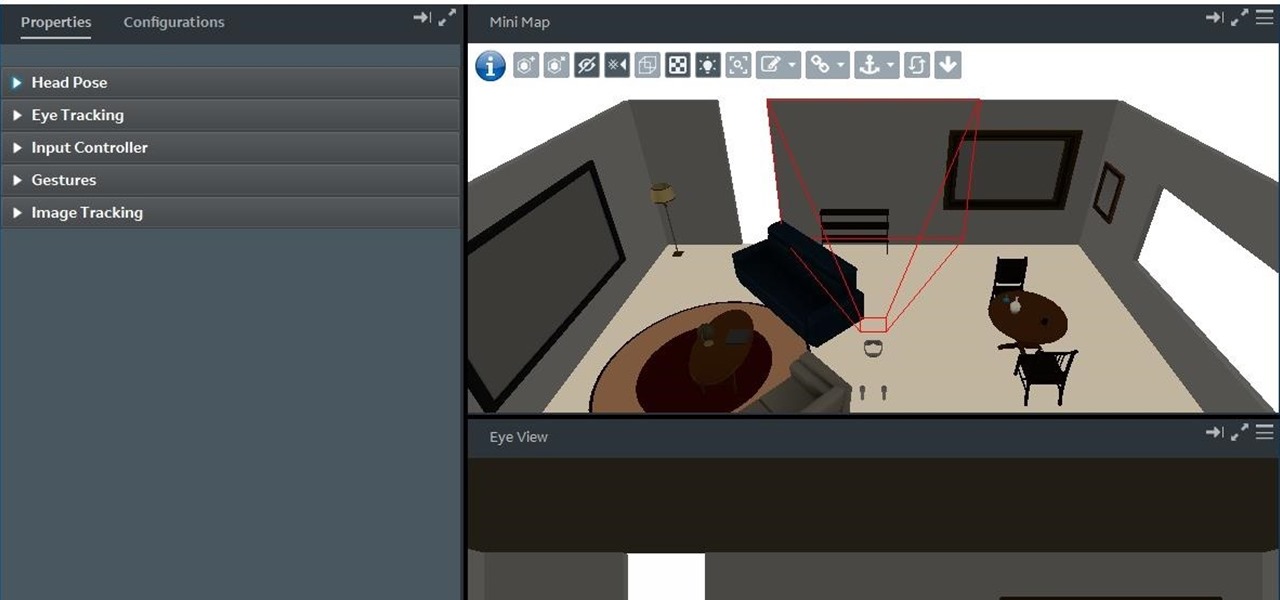
With the reveal of Magic Leap's developer documentation last week, many questions have been answered—and several new ones have been raised as well. But since the Magic Leap One (ML1) isn't simply called the "Leap One," these are questions that the company probably has no interest (at least for now) in answering. Understandably, Magic Leap wants to keep some of the "magic" under wraps.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

After recently being in the news for collecting PII (personally identifiable information) for analytics and after-sales support, OnePlus has another security problem. An individual going by the name Elliot Alderson discovered an app in OnePlus devices that can enable root access with one command.

When it comes to Hi-Fi music streaming services, Jay-Z's Tidal is one of your only choices. But as you can imagine, true High Fidelity audio requires faster download speeds than your average music service. So the question becomes, how do you listen to Hi-Fi tracks on Tidal when a speedy internet connection isn't available? Offline music is the answer.

On the surface, iOS 10.2 might look the same as iOS 10.3, but there's one big difference between the two versions: iOS 10.2 can now be jailbroken! Jailbreaking your iPhone means gaining access to thousands of tweaks and mods which greatly enhance the iOS experience, so this is great news for the power users out there.
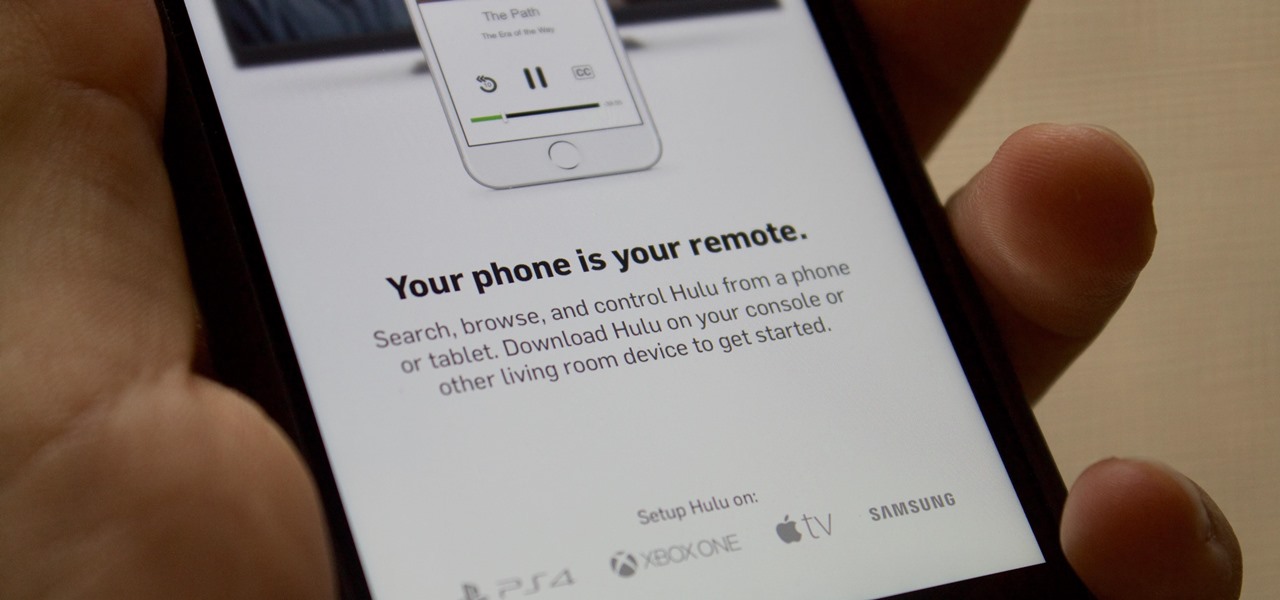
Your smartphone is the perfect place to watch Hulu on the go. Whether you're looking to catch up on your shows in a hotel, or your phone is the only screen available, mobile streaming can be a lifesaver. But what about when you have access to a TV? Wouldn't you rather watch your favorite Hulu Original on the big screen than on your comparatively tiny smartphone?

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.
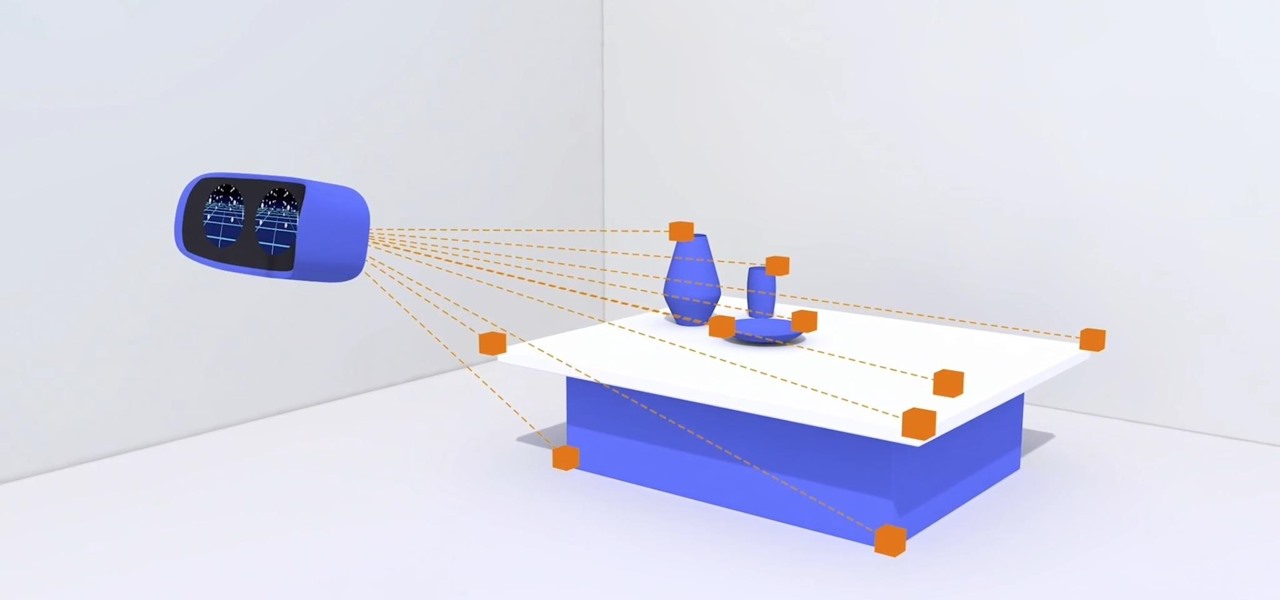
Google announced several new devices (as well as updates to existing devices) that will take advantage of the company's augmented and virtual reality platforms.
Smartphones have been around for nearly a decade now, so we've had plenty of time to develop preconceptions and bias. People that have never owned an iPhone will tell you that Apple devices are restrictive and bland, while others might say that stock Android is boring compared to manufacturer skins like HTC's Sense, despite never having owned a Nexus or Pixel.

Several Samsung phones have a feature that turns the screen black and white when the battery is getting low. This takes advantage of the AMOLED display in these devices, because unlike red, green, and blue pixels, no battery power is used to display black pixels on this type of screen.

The Stagefright exploit, which allowed for malicious code to be embedded in files on your device, is now very real in the form of Metaphor. Developed by software research company NorthBit, Metaphor is their implementation of exploits to the Stagefright library, and when executed, can access and control data on your device.

Out of nowhere, Google released a preview build of the upcoming Android N release back in March—a full two months early. As if that weren't enough excitement for one day, they topped themselves by following up that announcement with the debut of a new "Android Beta" program that allows users with eligible devices receive preview builds as a regular OTA update, meaning no losing data or manual installation.

The sheer variety of Android devices on the market is staggering—one report suggests there are well over 24,000 distinct phones and tablets floating around out there. When you consider that each manufacturer adds a few tweaks to the Android code base here and there, that makes for a lot of software variations, which in turn means there needs to be many different root methods to match this variety.
Hi guys. Hope you all had a good Christmas , today i have a tutorial for you.

Starting a few months back, you might have noticed that some text messages you received from certain friends or family members had blank or missing characters. This was because Apple included all of the new Unicode 8.0 emojis in an update to their iPhones, but Android devices didn't have some of these just yet, so they weren't capable of displaying them.

Android Marshmallow was recently released, and as we've grown to expect, a root method was quickly made available to devices running the brand new operating system. Legendary root developer Chainfire has stated that he's working his way towards retiring from the scene, but he still had enough left in the tank to quickly publish an update to his popular SuperSU root method.