Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

It's that time of the year, y'all—when the air becomes crisp, the nights grow long, and people crave hearty, warm soups and stews. And of all the season's offerings, my hands-down favorite has to be chili: It's versatile, meaty, and above all else, it's damn easy to make. (Thank you, Lord, for the slow cooker. Amen.)

Dinner is meant to be enjoyed after a long day away from home—it shouldn't cause stress or fuss. But for many, that's exactly what a home-cooked meal represents, especially on a work night. The prep work, the steps involved in following the recipe, the numerous amount of bowls, pots, and pans you use, and... worst of all, a sink full of dishes to clean.

The world of spices can be bewildering. They promise to make your food more flavorful if you know how to make the most of them. Unless you know a couple of essential tricks, however, it just seems like you're adding bits of colored powder to your food.

Many of the beauty products you buy at drug and department stores are loaded with potentially toxic ingredients like parabens, while their active ingredients are made of things like glycolic, lactic, malic, and alpha hydroxy acids and retinoids, which are all derived from foods.

Even as someone with super pale skin that burns instead of tanning, I don't use sunscreen nearly as often as I should. Or, uh...ever. My skin cancer prevention routine mostly involves hiding from the sun as much as humanly possible. If you're like me and hate the greasy feeling of sunscreen, there are other ways you can protect your skin by increasing your sun tolerance. Your diet actually has a lot to do with how easily you burn, so by getting enough of a few key nutrients, you can decrease ...

While most established media brands are satisfied with copying Pokémon GO to jump into augmented reality gaming, at least one property is taking a slightly different approach.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

Because timing is everything, the latest entry in the location-based augmented reality gaming sweepstakes, Ghostbusters World, has arrived just in time for Halloween.

With the announcement of ARKit 2.0 at WWDC 2018, Apple is bringing some powerful new capabilities to mobile augmented reality apps this fall.

The LG G7 ThinQ will likely be lambasted for its notch and awkward name, but one thing they seem to have gotten right is the new display. The G7 ThinQ will give many a first look at a new type of panel with lots of promise. While it was previously limited to TVs, from what we know, it should really shine on a smaller screen.

Cocktail rims are an easy way to add extra fun and pizzazz to your favorite drink; Most cocktail rims only take a few minutes to put together, and are a great way to add a burst of flavor to compliment what you're drinking.

Once again, you've found yourself inviting comrades, companions, and compatriots over for beverages on a Friday evening whim... but alas, your alcohol cabinet is looking rather meager, and your skills are lacking. No worries—just utilize these 10 tricks and spice up your at-home mixology game. Your friends will be none the wiser (and swear that you are a cocktail-concocting genius).

Pickles come in all shapes, sizes, and names (gherkins in the UK, cornichons in France). There are even crazy flavors such as koolickles—dill pickles soaked in a mixture of Kool-Aid and brine, an American South favorite. Whatever sort of pickle tickles your fancy, you can count on one thing: there's always leftover juice once they've been eaten and enjoyed.

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

Regardless of where you happen to live in the United States, you can always count on Caesar salad being on a menu nearby. The restaurant may be top dollar or a humble diner, but this ubiquitous salad prevails in every region and at every price point.

Each flavor of sake, the national spirit of Japan, comes with its own fans, not unlike whiskey aficionados here in the States. While sake is often called "rice wine," it is more akin to a malted beverage like beer.

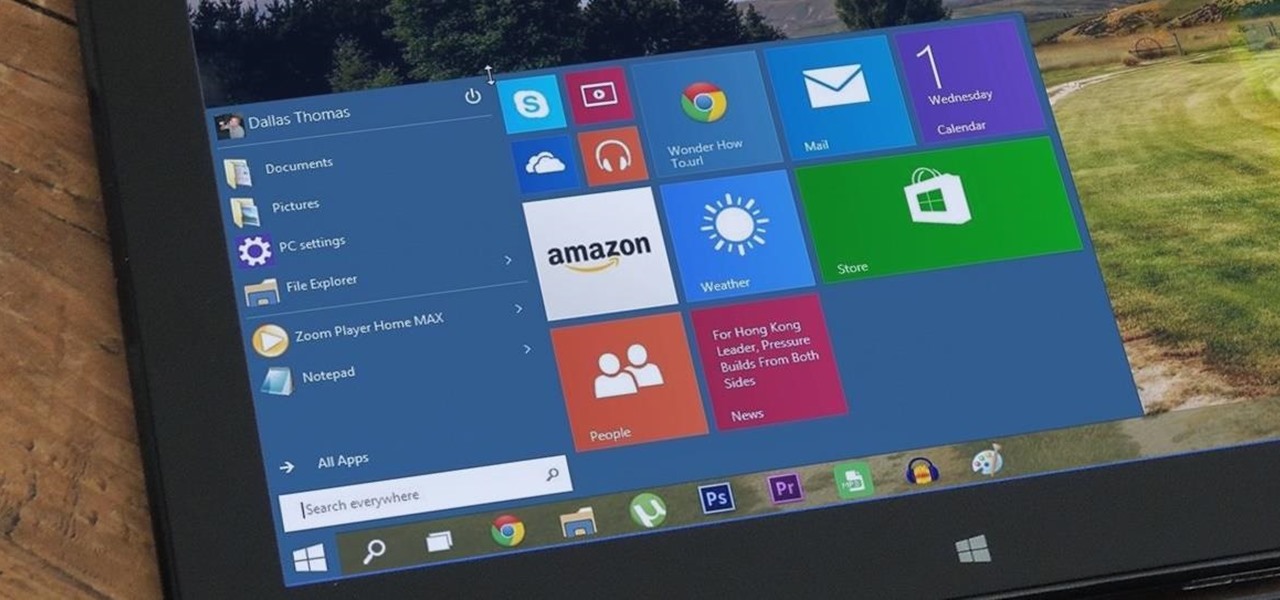
At a closed-door presentation on September 30th, 2014, Microsoft unveiled the latest iteration of its industry-leading operating system. Dubbed Windows 10 (seems as if Redmond isn't too fond of the "9" moniker), this new version brings along with it many UI optimizations and under-the-hood tweaks. With a particular focus on optimizing the interface for traditional mouse and keyboard computers, one of the most noticeable changes is the return of the Start Menu. While touch-optimized devices wi...

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

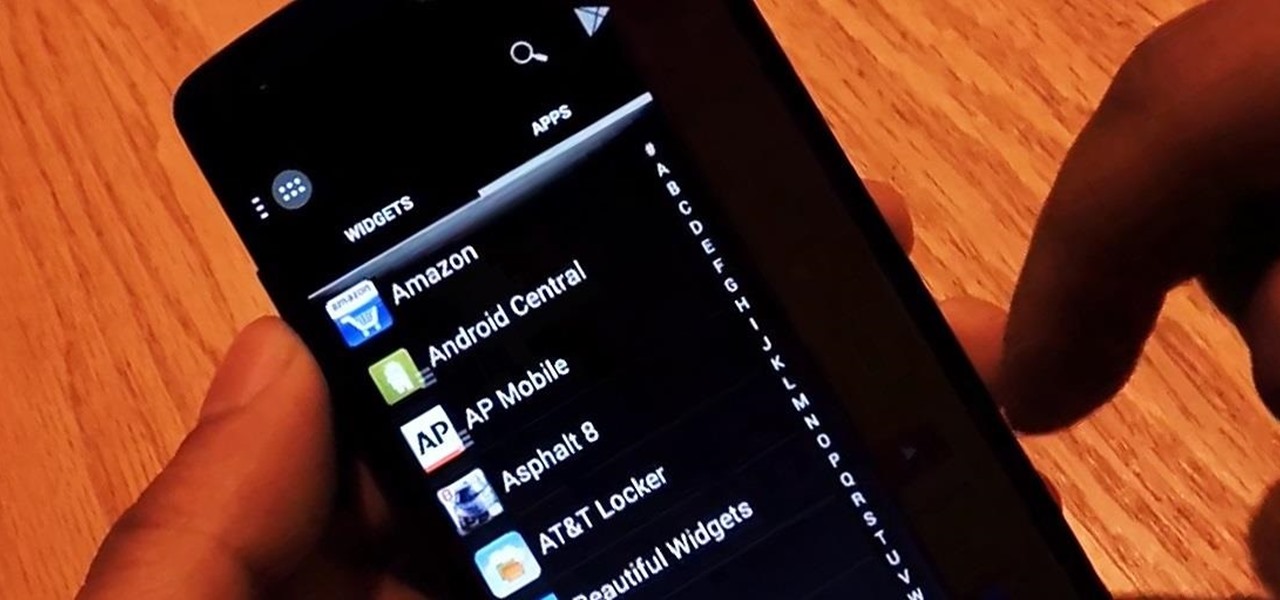
One thing almost every Android launcher has in common, from stocks to skins, is the way they handle organizing and launching apps and widgets. Tap an app icon to open the app. Drag apps together to create a folder. It's simple, it works, and it's what we know.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

I don't know how many of you had this experience in your youth, but when I was a kid, I used to actively think about what would happen if I suddenly woke up in a fantasy land, or were to pass through a portal into another space and time. I knew it wouldn't really happen, but when you're a kid, these can be important issues to you. So I slept with my glasses on every night, just in case. Photo from George Pal's The Time Machine.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

In the last decade, the number of people working remotely in the US has increased dramatically, and so has their need for technology and software to supplement that remote work. Whether you work from home or a coworking office space, the requirement for highly compatible and helpful productivity apps is a must if you want to get things done successfully.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

With the tagline "More Than Meets the Eye," the Transformers franchise was pretty much preordained to have its own augmented reality game, and AR gaming pioneer Niantic has stepped up to fulfill that destiny.

If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed.

Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries.

A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.

While installing the new Android 9.0 Developer Preview is fairly easy if you're using a Windows machine, it's a little trickier if you want to use macOS instead. To help you get the latest Android OS on your Google Pixel phone, we'll break down the whole process so using your Mac can be as simple as Windows.

I don't know about you, but I'm tired of hearing some of the same old jargon from people online who claim that all you need to make it on Instagram is to take good pictures and post consistently. Yes, for sure, but do you really think it's that easy?

Being part of the wild frontier is amazing. It doesn't take much to blow minds of first time mixed reality users — merely placing a canned hologram in the room is enough. However, once that childlike wonder fades, we need to add more substance to create lasting impressions.

After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking tools. There are multiple options to choose from, but Homebrew has a slight advantage.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

Brining is magic. All you have to do is make a mild saline solution, toss in your protein of choice, let it soak, and cook. You end up with incredibly tender, flavorful meat or tofu for very little effort. So why aren't more of us doing it?

Most of us have conducted an investigatory science project without even knowing it, or at least without knowing that's what it was called. Most science experiments performed, from elementary to high school students and all the way up to professional scientists, are investigatory projects.

OnePlus, whose phones always challenge for the title of best spec-to-price ratio, releases two main devices every year. There's the primary flagship in late spring, then an iterative update with the "T" suffix in fall. Typically, there's not much difference between the two, but this year, OnePlus is mixing up the formula a bit.