I know Americans love to hate on the French, but from my standpoint, they've given us a lot of things we should all be thankful for, like French kissing, casual sex, Pepé le Pew, and of course, French fries. Well, maybe not...

The new Samsung Galaxy S4 has something no other phone has ever had before—weather sensors. Older devices like the Galaxy Nexus, S3, Note, and Note 2 do have a atmospheric pressure sensor, aka a barometer. However, they do not have a thermometer or hygrometer like the GS4 does, which measures ambient temperature and humidity.

According to the CDC, less than 33 percent of adults eat the recommended servings of fruit each day in the United States. When it comes to vegetables, Americans are even worse, averaging less than 27 percent. Most adults should consume at least 2 servings of fruit and 3 servings of vegetables each day, depending on age, gender, and level of physical activity. Eating lots of fruits and veggies has been linked to a better immune system, faster weight loss, and way too many other health benefits...

While Siri may be the cream of the crop when it comes to smartphone personal assistants, there is always room to grow bigger and better (that's what she said). Siri, although recently expanded, is still lacking in the amount of commands and actions she can currently perform. While looking up directions and restaurants is fairly easy for Siri, asking her to gain access to third-party programs or browsers is a little more difficult.

Got a Samsung Galaxy Note 2 phablet? Sure, it has its problems like any other mobile device, but it's still one of the hottest phablets on the market right now, because, well... it's awesome, right?

While the majority of America was watching the Super Bowl yesterday, the crew over at the evad3rs was finishing its work on their untethered iOS 6.1 jailbreak called evasi0n. Well, the wait is finally over!

I loved the Gold Rush unit back in third grade. We went up to the American River and panned for gold, and my panning skills balled above all. I got like three tiny pellets. Of course, it was all fool's gold, aka pyrite, but it was still pretty legit. And this was before wearing gold chains was cool—or not.

Finding love is tough. Movies like The Notebook and Twilight have ruined the expectations of love and relationships for us guys. Some women's ideal love situation is being kissed by a glittery sparkling vampire. "I know we only met a few seconds ago, but I'm deeply in love with you."

So many times, you turn on your computer, you open your front door, or you sit down on the couch to watch some well-earned TV, when you think -- Gosh! If only I could do this or this, life could be so much easier! And then, if you were a boring person, you would slouch even further down on the couch and continue to watch those reruns of The Sopranos.

Sprint has announced that it will be the first U.S. carrier to release Jelly Bean 4.1 for the Samsung Galaxy S III. The over-the-air updates have already started, with users receiving a notification on how to update on their phone. The reason Jelly Bean has garnered so much attention is due to several, well-known features like Google Talk, Project Butter and expandable notifications.

While becoming the next Mark Zuckerberg may be out of reach for someone just getting introduced to code, the skill has never been more valuable. Just understanding basic programming language is a great thing to put on your resume, and if you know how to code, you’re golden. Software developers and programmers have been the most resistant to the recession, as jobs in the tech industry continue to grow.

Considering how often many of us fly on commercial airlines, the idea that a hacker could somehow interfere with the plane is a very scary thought. It doesn't help to learn that at Defcon, a researcher found that the Automatic Dependent Surveillance Broadcast (ADS-B), transmissions that planes use to communicate with airport towers are both unencrypted and unauthenticated.

Do you own an HP printer? If so, it may be vulnerable to malware attacks. Researchers at Columbia University discovered that 25% of Hewlett-Packard printers have significant vulnerabilities that put your printer in danger from hackers—even your home. With a budget of just $2,000, researchers Salvatore Stolfo and Ang Cui were able to hack into the printers using remote firmware to install malware, and in some cases even cause the printer to catch on fire. The main issue is with the printer's c...
An amazing amount of news this week; new proposals and new agreements have sprung up. But so has our "need" to spread our presence. The military warns of another war, while 26 congressmen decry the use of drone strikes. Read on:

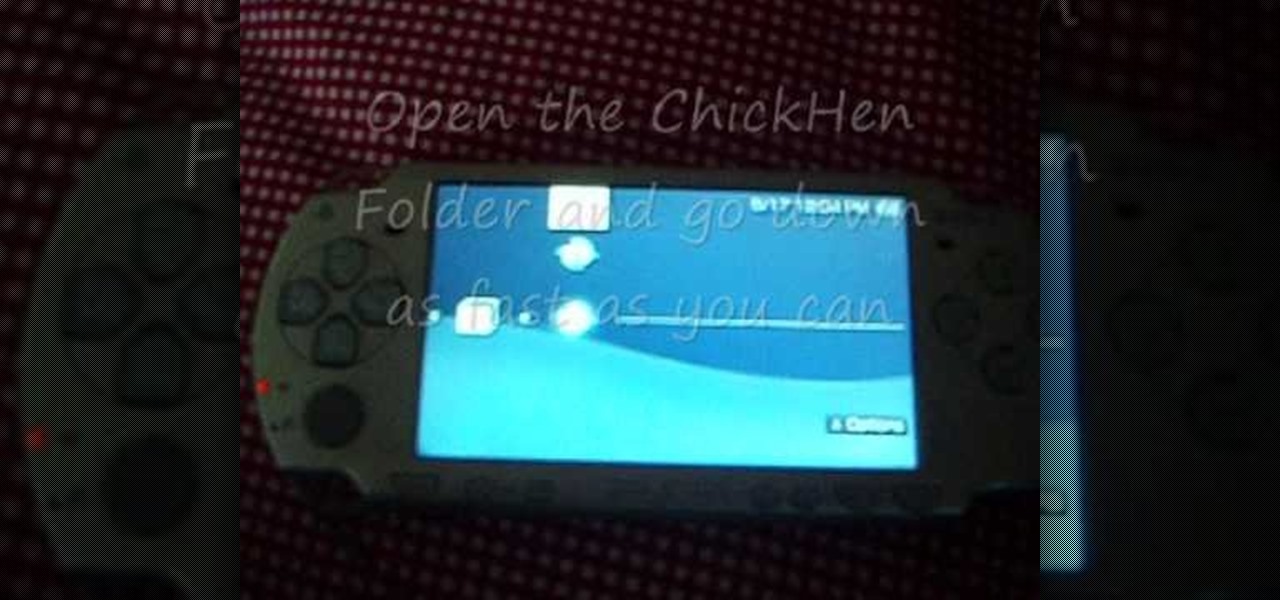
This is part 1 of 2 on how to hack a PSP without a Pandoras Battery using ChickHEN. You will need to ensure that you have firmware version 5.03 ChickHEN R2 in order for this hack to work.

Although mainly demonstrational, this video shows you how to play a song "Summertime" in D minor on guitar. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your guitar learning:

The development of virtual reality at Facebook has been evolving lightspeed in the last few years. But while a relatively small group of VR enthusiasts and gamers are enjoying the social media giant's dedication to immersive headsets, it is the augmented reality space and its potential scale that truly has the tech market enthralled.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

When I first found out about Nreal, back in the spring of 2018, the most interesting thing about the company's story was the founder's background. Chi Xu, the CEO and founder of Nreal, previously worked at Magic Leap as a software engineer.

For many, the stock version of Android is often considered the epitome of what the operating system should look and feel like by default. It's clean and clear of unwanted extra apps that come pre-installed with the system, provides a fluid and fast user experience, and runs on just about any device that has an unlocked bootloader to install a custom ROM with the stock version ready to go.

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

While Microsoft dominated the augmented reality news at this year's Mobile World Congress, a small AR startup we've covered in the past arrived in Barcelona, Spain, to unveil the next phase of its mission.

| Update: ZTE's issues with the US government have finally been resolved. Check out the details below.

Apple has introduced a special edition iPhone 8 and 8 Plus to bring attention to the ongoing worldwide battle against AIDS. As the second iPhones to carry the (PRODUCT)RED name, these rare iPhones may quickly sell out when preorders open up on Tuesday, April 10, at 5:30 a.m. (PDT), so we'll go over some tips to help you secure a red iPhone before it's gone.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Despite their sometimes fluffy reputations and occasionally ethically compromised viewpoints, tech evangelists are important, don't let anyone tell you otherwise. The right passionate voice behind the right technology platform or piece of hardware can sometimes spell the difference between fostering a community of potential users and watching a product die on the vine.

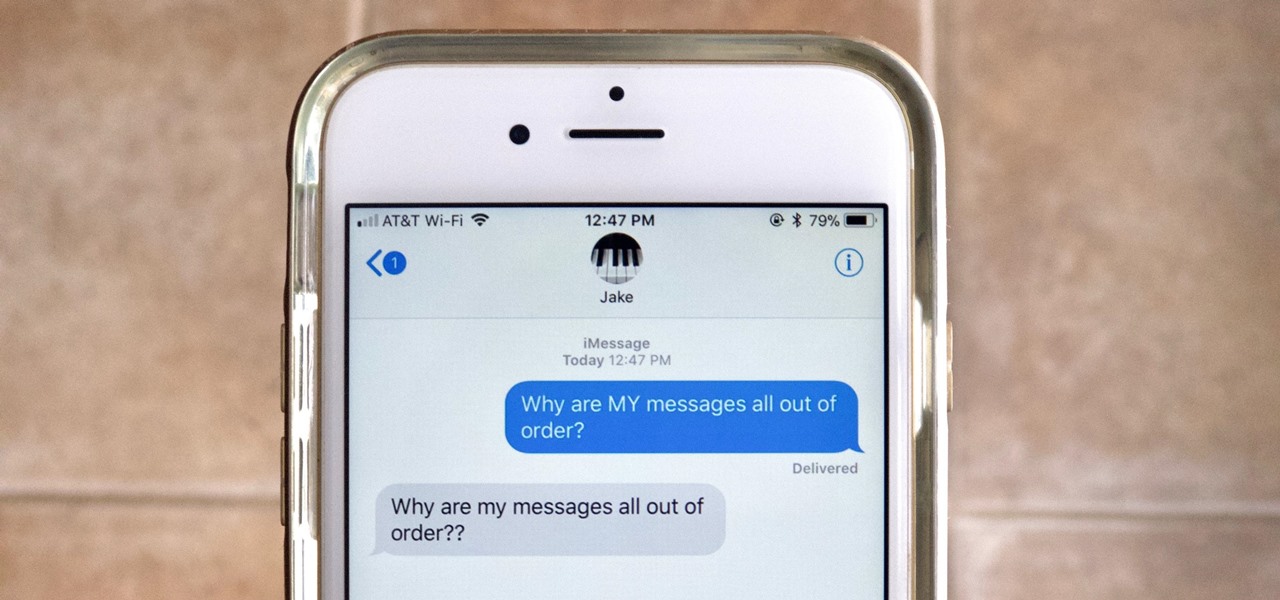
One of Apple's best products is iMessage, which allows for quick, creative, and free messaging between iOS and Mac devices. However, users are reporting that conversation threads in the Messages app are occasionally out of order, which is equal parts confusing and annoying. Luckily, we have some ideas on how to fix the problem.

At this point, we've seen Samsung's vision for Android Oreo on both the Galaxy S8 and Galaxy Note 8. Just last month, Samsung opened its Oreo Beta Program for the S8 to the public. A few days ago, we obtained and detailed a leaked beta build of Oreo for the Note 8. While both of these updates have some compelling new features, there are always tweaks we hoped to see that didn't make the cut.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

Apple demonstrated their continued interest and investment into the awesome world of augmented reality during their Sept. 12 event, highlighting a few new AR games that will appear on iPhones thanks to ARKit. But that's not all you can expect — as long as you have an iPhone with an A9 chip or later, there will be a ton of cool new AR tools, games, and other apps to play around from the App Store.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

So while it is the weekend of San Diego Comic-Con, and it should not be a complete surprise — without a word of warning hitting my feed — the trailer for the upcoming film, Ready Player One was released today. And wow it looks amazing.

Quanergy CEO and founder Louay Eldada is, by any standard of measure, a pioneer in the development of LiDARs for driverless vehicles.

Apple just unveiled a red iPhone and iPhone 7 Plus, dubbed the iPhone 7 (PRODUCT)RED Special Edition, to commemorate the ongoing global fight against AIDS. Apple fans the world over are sure to swarm in and gobble up the initial stock shortly after the new color is released at 8:01 a.m. (PDT) on March 24, 2017, so we'll go over some tips to help you secure a red iPhone before it's sold out.

While its direct-selling model echoes brands like Avon and Tupperware, Indonesia's MindStores gives the approach a modern twist—with augmented reality.

A recent study underscores a connection between climate change and infectious disease, raising concerns about our quickly warming planet.

Google's former Self-Driving Car project, now graduated from Alphabet's X division as Waymo, has found a collaborator and potential new partner in Honda. This is an interesting turn of events given traditional automakers' reluctance to work with driverless-car startups over the years.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.