Humans learn best by doing or through an experience, and so the holographic environments provided in virtual and mixed reality are ripe with educational opportunities. HoloStudy took this to heart and created an educational science app that teaches you with animated models you can explore in your own space.

The Weather Channel, by virtue of its name, has always been tasked with the difficult problem of making the weather interesting. As Mashable notes, they've turned to augmented reality for a solution and can now render a 3D storm in their studio, as well as help us understand how bad a storm might be with 3D forecasts.

Clothespins are pretty innocent-looking, but with a mod here and a hack there, that innocence quickly turns into danger. Well, sort of. In this project, we'll be turning an ordinary spring-action clothespin into powerful matchstick and toothpick shooter that can shoot apples and lob fiery darts over 20 feet.

The holiday season is almost over, bringing the year to an end, and what better way to end it than with some tonsil hockey from the dime across the room on New Year's Eve?

As dedicated bicyclists are well aware, riding can be very dangerous. Now that daylights savings time has ended in the United States, darkness appears quicker, and the night is especially dangerous for cyclists because of the low visibility that drivers have. Not only is darkness a danger, but also fog, blizzards, and heavy rain—all wreaking havoc on the vision. To combat this, bikers attach reflectors: clear front reflectors, red rear reflectors, amber pedal reflectors, and clear side reflec...

Shaun Alexander was an amazingly productive NFL running back. In this video, he takes some time to explain for young running backs how to hold the ball properly, protecting it from the defense and potential fumbles. Proper finger positioning and placing the body between opponents and the ball are both crucial elements.

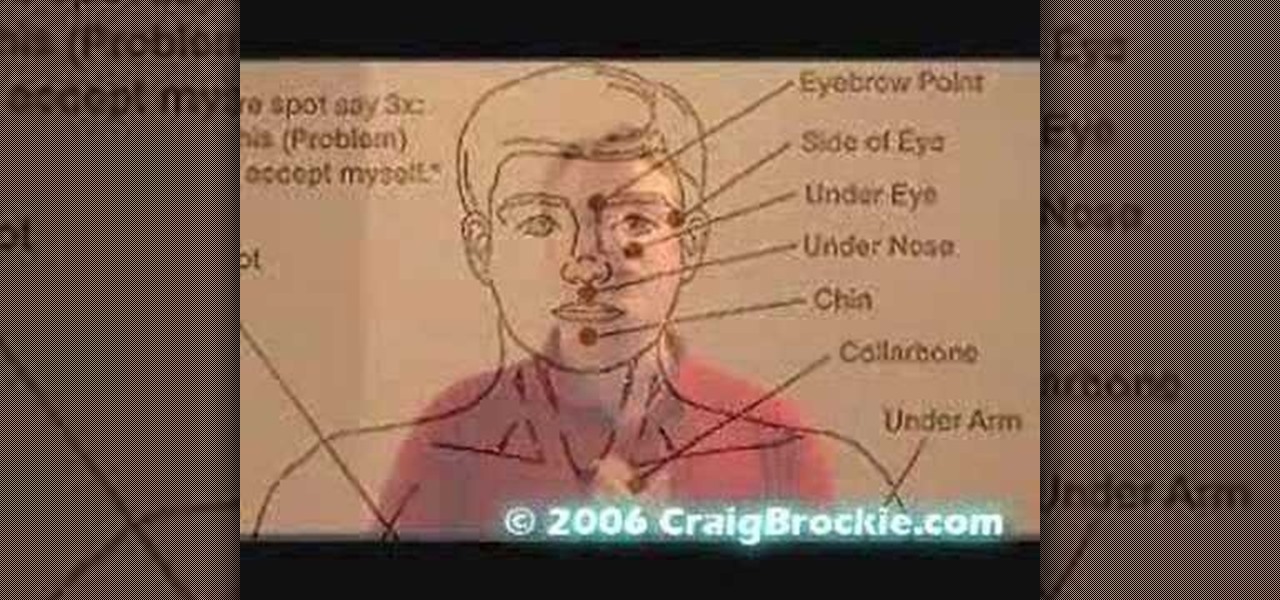
Craig Brockie delivers the goods with a how to video on Emotional Freedom Techniques, or EFT. Learn these powerful techniques to reach your highest potential and reduce stress, increase focus and will, and overall acheive positive results. Watch this tutorial and you will be able to overcome cravings and reduce stress with EFT.

Mr. Shane Benedict describes the delicate balances necessary to hit that perfect boof every danged time.

The video shows you how to calculate capital budgeting with a Texas Instruments BA2+ financial calculator. Capital budgeting will help you determine cash flows for given investments for a certain number of years in the future, thus helping you determine if the investment is worthwhile. The buttons you will use are the CF (cashflows) button, the NPV (net present value) button, and the IRR (internal rate of return) button. The video uses the example of a $10,000 investment that will return $5,0...

Looking at homes is the fun part. But before you go house hunting, make sure you have your financial ducks in a row.

Testing products for a living is a bit more complicated than it sounds. You Will Need

Congratulations! You have the potential for a killer hourglass figure, if you know how to work it. You Will Need

Learn how to read a person just by looking at their hand using the ancient art of palmistry. Step 1

Learn how to attend a wedding alone. Not having a date for a wedding can be a good thing, if you know how to work it.

This video demonstrates Bernoulli's Principle which states that, “For an ideal fluid (low speed air is a good approximation), with no work being performed on the fluid, an increase in velocity occurs simultaneously with decrease in pressure or a change in the fluid's gravitational potential energy..

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

This week's Apple earnings offered a report of solid performance and guarded optimism about future iPhone sales, which may be impacted later this year by issues around the current coronavirus epidemic in China.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

Now that we've had our hands on the Magic Leap One for almost a year and early adopter developers have had the opportunity to publish apps for the AR headset, it's time to see how it stands up against the rigors of a day at the office. We did just that, and we wrote about it!

While Magic Leap turned heads at the Game Developers Conference with AR experiences at the Unity and Unreal Engine booths, news broke that the company was the winning bidder for ODG's patents.

Now that its first developer conference is in the rearview mirror, Magic Leap continues to nurture its content development community, this time with an assist from strategic investor and retail partner AT&T.

This week, we continued our NR30 series highlighting the leaders of augmented reality space by profiling the venture capitalists and strategic corporate investors that sustain the industry.

UPDATE: The ported APK covered below is now obsolete because Fortnite beta is officially available for all Android devices!

If you're a console or PC gamer, you may be quick to ignore the mobile version of Fortnite Battle Royale. The lower graphics and the switch to touchscreen controls may be enough reason to dismiss this version of the game. But don't be so quick to judge — there are actually some clear advantages to playing on mobile.

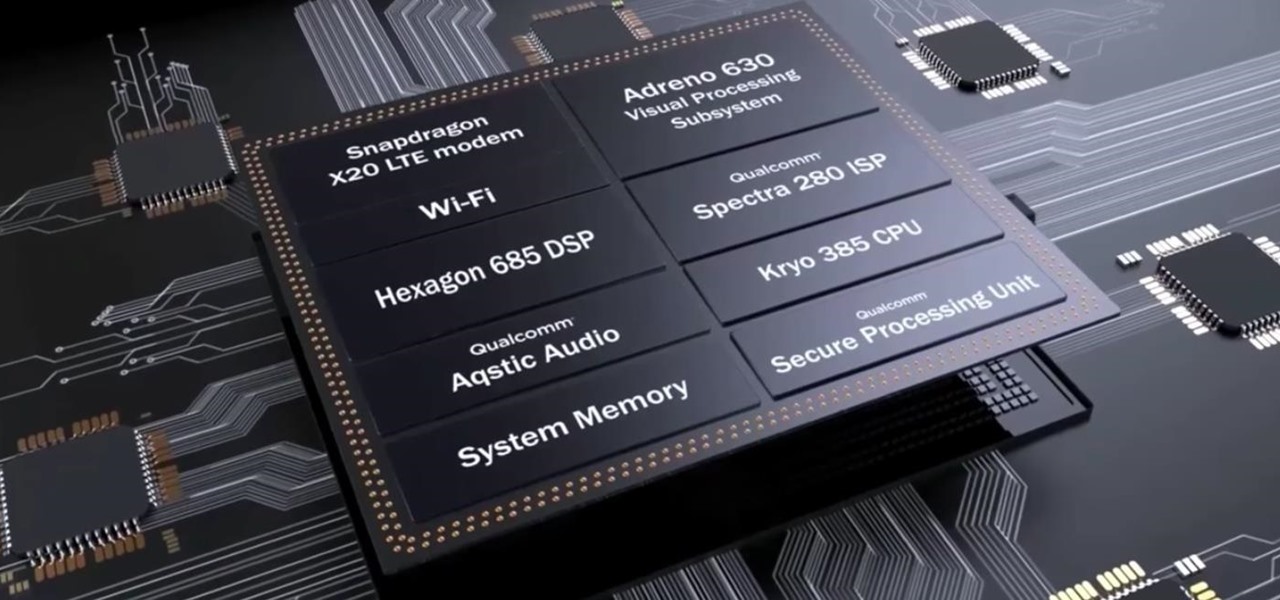
After the success of the Snapdragon 835, Qualcomm now has its eyes set towards the future with the arrival of its next-generation SoC, the Snapdragon 845. Debuting alongside the Samsung Galaxy S9, the 845 is now set to take over the market for flagship Android phones in 2018.

One of the standout features of Nova Launcher is its vast customization options. Not only does it includes numerous tweaks to alter the aesthetics of your home screen, but it even has plenty of features that reduce clutter. One area of our device that has a high potential for disarray is our home screen.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

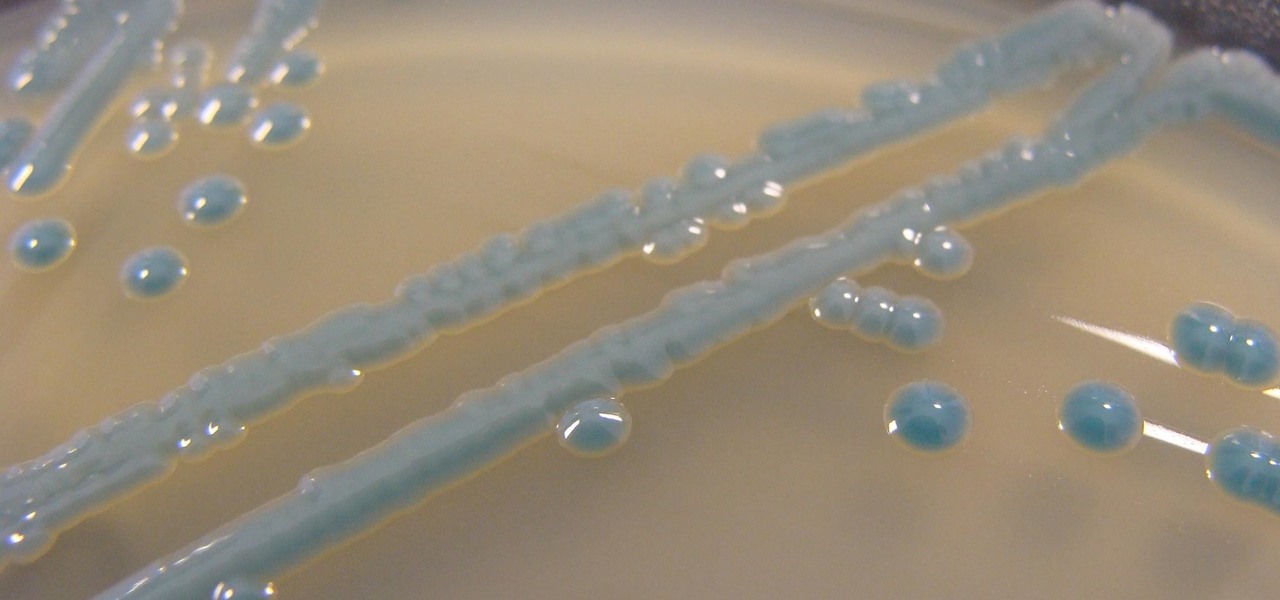
The growing list of dangerous antibiotic resistant organisms has just acquired three new members. Researchers have discovered three new species of Klebsiella bacteria, all of which can cause life-threatening infections and have genes that make them resistant to commonly used antibiotics.

More than one in ten people in the US have type 2 diabetes — that's over 29 million people. It's characterized by excessive sugar (glucose) in the blood due to the development of resistance to insulin, the hormone that normally metabolizes glucose.

For a company more associated with debugging computer programs, Google's parent company, Alphabet, is making a name for itself by taking on the real thing — mosquitoes.

Sex makes the world go 'round, and when it does, so does gonorrhea. Finally some good news on the growing menace of drug-resistant gonorrhea — a large, long-term study shows a vaccine may work in reducing the incidence of an increasingly dangerous infection.

Peach trees and other related plants are susceptible to the devastation caused by fire blight, a contagious bacterial disease. Once contracted, infected trees have to be burned to contain the disease and prevent spread to nearby trees. Increasing resistance to antibiotic treatment has sent scientists in search of alternative ways to deal with the bacteria and prevent its catastrophic damage.

More bad news for patients who have undergone heart surgery in the past five years. A new study suggests about one-third of heater-cooler units used in cardiac procedures remain contaminated with a slow-growing, potentially fatal bacteria.

The search is on to find antibiotics that will work against superbugs — bacteria that are rapidly becoming resistant to many drugs in our antibiotic arsenal.

Despite the threat of superbugs, physicians continue to prescribe antibiotics when they might not be needed, and patients are suffering.

The leading platforms enabling augmented reality technology lead our headlines in Market Reality this week.

The problem with HIV is that it attacks and kills the very cells of the immune system that are supposed to protect us from infections — white blood cells. But a new technique, developed by scientists at The Scripps Research Institute (TSRI) in La Jolla, California, offers a distinct HIV-killing advantage.

An innovative new wound dressing has been developed by a research team at Lodz University of Technology in Poland that uses crustacean shells to create a bandage that packs an antimicrobial punch — and even more potential to help solve a global problem.