This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

There is something so satisfying about dipping your spoon into a perfectly smooth slice of cheesecake. There is something a bit less satisfying about it if the top of the cheesecake is cracked and cratered.
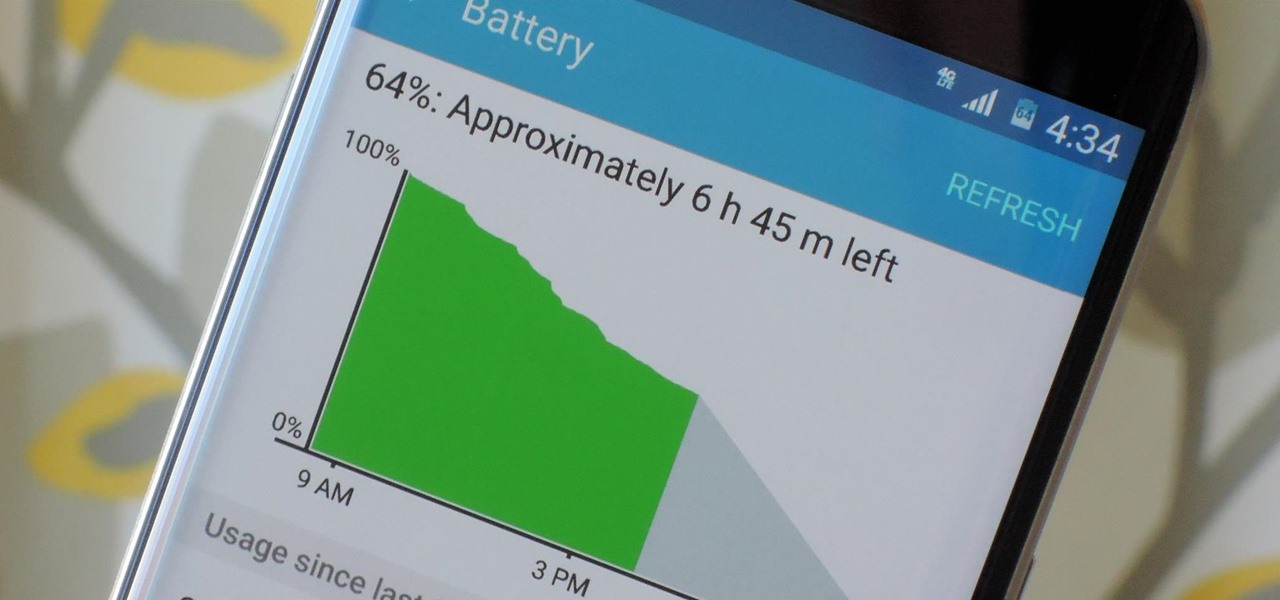
Smartphones have otherworldly specs these days, so it's relatively uncommon that you hear someone complaining about display resolution, build quality, or general speed and performance. At best, these are secondary concerns, with the number 1 issue almost unilaterally being battery life.

When you look at an Italian flag, what do you see? Green, white, and red? Well, I see a Caprese salad. And no, I do not need to have my vision checked. It simply means that I have the eyes of a chef.

The other day I was doing the math on roughly how many eggs I eat each year. I estimated about 500. That's a lot of eggs. And, subsequently, that's a lot of eggshells to throw in the trash.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

Whites are the hardest color to keep looking bright and new after just a few months' time. Your sweat and oils quickly become stains, and colors from other clothes will eventually bleed into the fabric, discoloring your bright whites into something merely whitish. But before you reach for the bleach, the ultimate chemical cleaner, try some a few of these safer, less-toxic DIY solutions out instead.

Hi, dear co-apprentices and wise masters. I've been recently trying to learn the basics to hacking here, and I've read all guides on Wi-Fi hacking and noticed no word is dedicated to this awesome script that comes bundled with Kali!

Most of the time we only use the microwave to reheat or defrost, but you can actually save a lot of time by using it for cooking. These genius recipes make the most of this underused appliance, and also turn out some pretty tasty dishes.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Cooking with animal blood is as old as civilization itself. I promise that your ancient ancestors, no matter where you're from, didn't have the luxury of throwing away any part of the animal, including the very lifeblood that used to run through it. Animal blood, along with everything but the skin, would invariably end up in the stew.

Willpower is a pretty significant word. It's the difference between sticking with a clean eating diet and diving face-first into a plate of brownies. It's what drags you out of bed on Monday mornings and into work rather than letting you stay snuggled under the covers asleep. And, most importantly, it's the kick in the butt we all require to both accomplish goals and make changes.

Welcome back, my novice hackers! This is the third installment of my Python scripting series. If you haven't read the previous two articles, take some time now to go back and read Part 1 and Part 2 before you proceed here.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Dulce de leche is a beautiful, caramel-like spread that you can slather onto bread or use to flavor cakes, cookies, or flan. You can also use it as a drizzle for ice cream, chocolate candies, and pastries. It tastes like heavenly toffee, translates roughly to "milk candy," and is popular all over Latin and South America. A version of the confection is also popular in the Philippines, in Russia, and is known in France as "confiture de lait." The traditional way to make dulce de leche is to slo...

While most people build collections of things with intrinsic value such as coins, stamps, or rare post cards, I collect wine corks—the natural ones, not the plastic kind. Corks are a natural product harvested from the cork oak tree. It takes the better part of 10 to 12 years before a tree can have its bark manually removed for the production of cork. Thankfully, no tree is harmed in the process and in 12 years, the tree bark can be harvested yet again.

We all carry a bit of anxiety around with us. Is our boss still annoyed because we could barely stay awake in yesterday's pre-dawn meeting? Will our friend hate us forever because we forgot to call them back two weeks ago? Whatever worries pop up in your mind, whether they're monumental or insignificant, it can be hard to quiet those nagging voices, but you can shut down your nonstop mind with a bit of relaxation, distraction, and action.

By now, you've stuffed yourself with enough cranberry-soaked turkey to last you until next year. Still, there's a formidable amount of leftovers, and you're kidding yourself if you think you won't be craving them when you wake up tomorrow with a food coma/hangover.

When I was 12, for some mysterious reason, my dad put my little brothers and me in charge of cooking the Thanksgiving turkey. Naturally, my brothers and I spent the rest of the day playing hide-in-seek in the backyard and forgot all about the humble bird defrosting in the sink.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

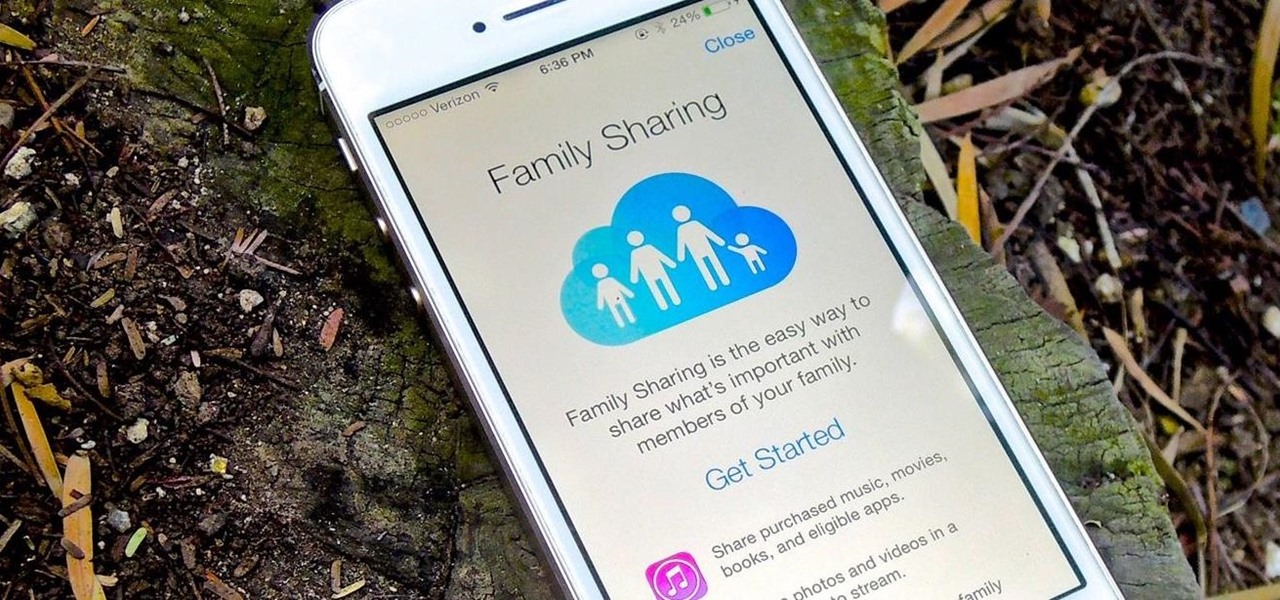
There are a ton of great new features in iOS 8, and one of the most interesting (and perplexing) ones is called "Family Sharing."

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

If you're anything like me, every time you travel you end up in a desperate panic for a decent W-Fi connection. Whether you want to post your photos, research the best beaches, or kill time during an overnight layover, a hotel's Wi-Fi quality is of paramount significance in making a reservation.

Fish is delicious, and as the Harvard School of Public Health points out, incredibly good for you. There are many studies that show regularly consuming a couple of servings of fish per week can help prevent heart disease and may well reduce your chances of stroke, depression, and getting Alzheimer's. After all, there's a reason why fish is called "brain food."

Android enthusiasts have their own opinion as to whether you need antivirus software on an Android device. This debate will never end, provided that Android malware is in existence. This guide is not here to say, "Yes, you need antivirus," or "No, you don't." It's to give you all the facts, so that you can make a decision as to whether or not you need antivirus on your Nexus.

Journals are a great source of hilarity and embarrassment, detailing everything from your elementary school crushes to those super awkward middle school dances. While rereading your old hand-scrawled entries might make you cringe, that old journaling habit could benefit you as an adult.

Humans in general are great at keeping things about themselves private, from feelings to personality traits. While smartphones and social networks are making these secrets more open, narcissists have and always will love being out in the open with everyone's attention on them.

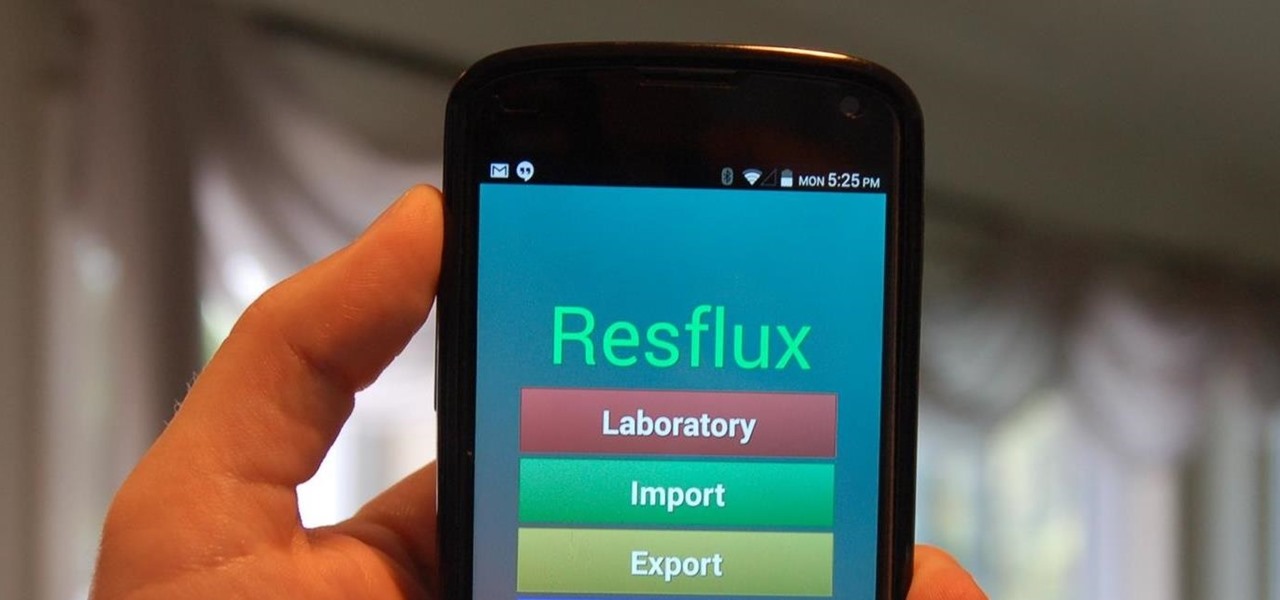
Resflux is an Xposed mod developed by Julian Paolo Dayag, aka WisdomSky, that provides users with a straightforward and functional way to customize and theme almost every aspect of the packages (apps and system components) installed on their Android device.

Jailbreaking gives you root access to the iOS file system, allowing you to install third-party apps and tweaks on your iPhone that aren't available in the App Store. It opens up a whole new realm for what your device can do, but it can also cause instability across the system and can dissuade you from getting future updates from Apple that have important features, bug fixes, and security enhancements.

Boozing it up at work might have been okay back in the days of Mad Men, but today, employers prefer that their workers stay sober. What you and your bosses probably don't know is that a little drinking on the job can actually increase your creative capacity and problem-solving skills. Alcohol Can Enhance Your Creativity at Work

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

LG's arsenal of screen-off and screen-on tap gestures recently expanded into lock screen territory. Dubbed "Knock Code", this feature allows owners of various LG phones, like the G2 and upcoming G3 to unlock their phone with a series of taps on the screen. The most impressive part is that the screen doesn't even need to be on!

You know you've had a long day when you head home with a headache, back pain, and eyes so sore they feel like they might roll out of your head. Turns out your medicine cabinet isn't the only place you can find help—instead of popping painkillers, just open up your wallet for instant pain relief.

Look away from this screen and try to remember the sound of your childhood hero's voice. Did you do it? Do it again, and this time pay attention to your eyes.

Phantom phone vibrations. You might feel them in the pocket of your jeans, or when your handbag is on your shoulder—even when you're holding your phone in your hand. When you do, you immediately wake it up to see who texted or what app just had an update—but there are no alerts.

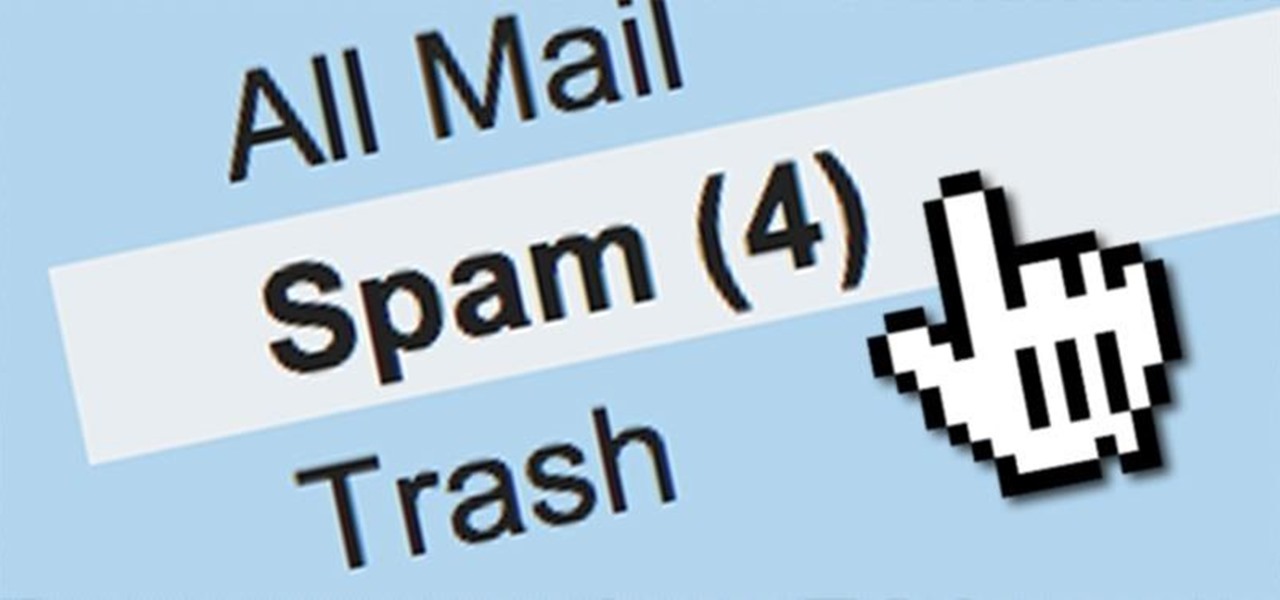
I rarely receive spam mail, but every now and then I’ll get an email from Cat Fancy Magazine. I’ve never read an issue of Cat Fancy Magazine or been to their website. Actually, I’m allergic to cats. So how did they manage to get my information?

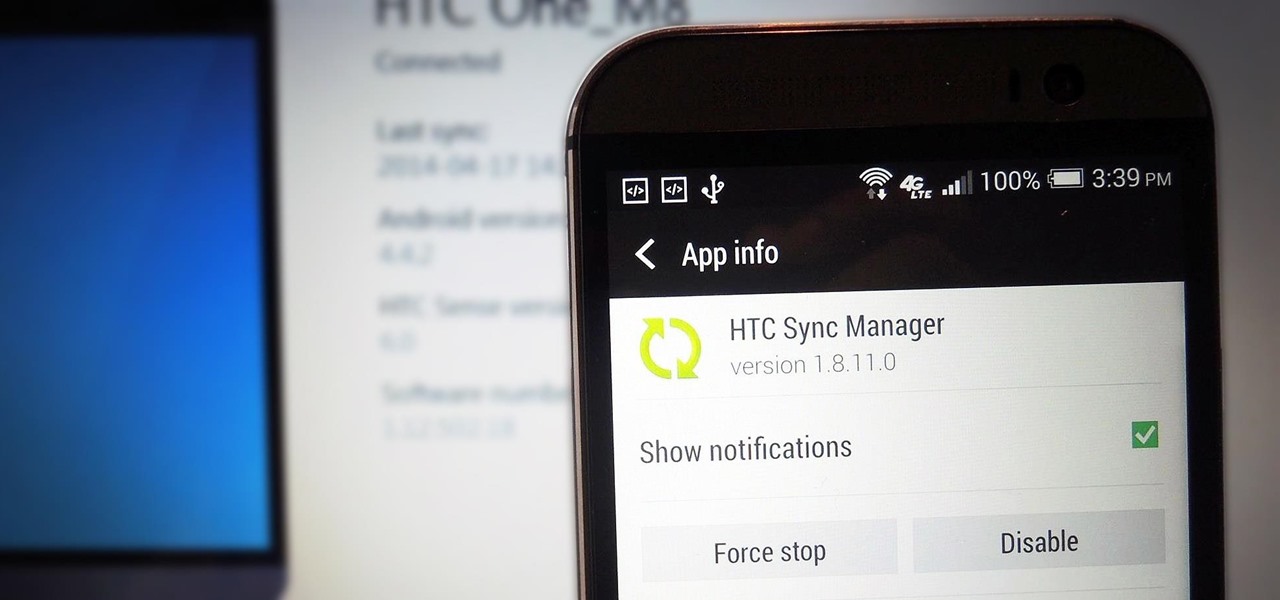
If you've just upgraded to an HTC One M8, chances are you've got some media files you want transferred over from your computer or previous phone. Even after you've done that, there will be times when you want to transfer content back to your computer for safe keeping.

Garlic—it stinks so good! It's one of nature's most wondrous foods, being both delicious and incredibly healthy. What's not to love? Well, it is kind of a pain to prep, whether you're peeling a couple of cloves for a sauce or a whole head and trying to mince it finely. One way to get around the whole peeling and mincing issue every time you want garlic in a dish is by buying pre-made garlic-infused olive oil, except that stuff is pretty pricey. Learn to make it at home and you'll get all the ...

We've all been there. Stranded in a large lot or parking garage, braving the rows upon rows of identical cars in an endless concrete landscape because, for the very life of us, we can't remember where we stashed the very ride that brought us there.

Apps that have no business accessing the internet can share your location, device ID, and other personal information with potentially malicious data snatchers. If you're connected to the internet on your Nexus 7 tablet, you're a potential target for cyber threats.