
Windows 10 : Against Privacy
The title might not be in harmony with the post, but thinking a good title that perfectly matches your post... isn't that easy. Especially for this post.


The title might not be in harmony with the post, but thinking a good title that perfectly matches your post... isn't that easy. Especially for this post.

A recent security risk exposed by software engineer Szymon Sidor has raised a few eyebrows amongst the Android community.
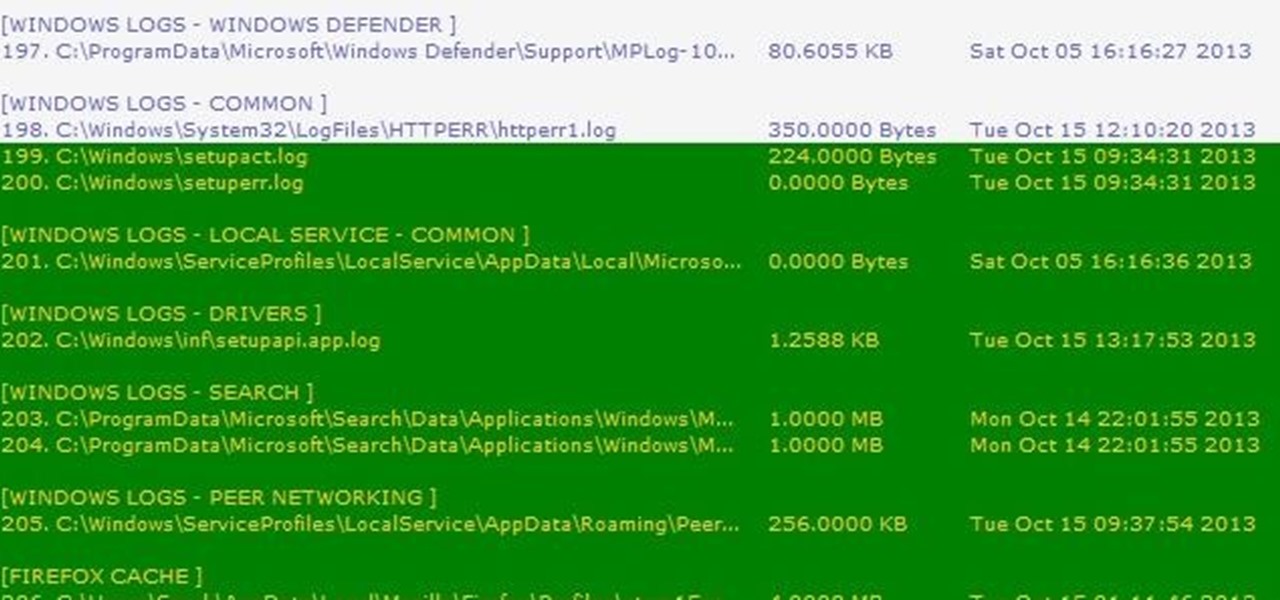
Thousands of history files, cookies, other unwanted files stored in your system as logs and other formats. To manually check each one is difficult. New computers are too fast by processor behavior, after some times of working it comes to slow performance.

When it comes to your smartphone, you don't have to be a cheater to want a little privacy. I don't even like people playing Temple Run on my mobile because I don't want anyone beating the achievements I've been working on getting myself.

The camera system on the iPhone has never been better. Apple's iPhone 11, 11 Pro, and 11 Pro Max sport some of the best shooters on the market. But no level of quality makes up for the fact that shady apps can access your cameras for nefarious reasons. You can take control of the situation, however, and block any app you want from using your rear and front-facing cameras.

The recent Oculus conference in California revealed just a bit more about Facebook's secretive plans to compete in the augmented reality space with its own wearable devices.

Your iPhone has a lot of personal information contained within it, so of course you want your device to be secure. You don't want that information getting into the wrong hands — or any hands other than your own, for that matter.

Facebook really wants us to use Messenger. For the most part, they've succeeded; theirs is one of the most popular messaging apps right now. And with yesterday's announcement of new features, Facebook is only going to make their flagship chat application better.

Windows 10 is the most cloud-oriented version of Windows to date—yet, while this means you get some nifty new features, it also means some of your personal data is being shared with Microsoft's servers.
One of the biggest improvements in Mac OS X Yosemite came to the Spotlight search feature, allowing users to not only search through their applications, but also their emails, text messages, iCloud, and the web.

Former Vice President Dick Cheney was so fearful of attacks, he had his heart defibrillator re-calibrated to block incoming wireless signals so that highly skilled hackers couldn't send him into cardiac arrest.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

Free online dancehall step tutorials every wednesday at 10am for the entire summer! Learn your favorite dancehall steps in the privacy of your own home! This one covers the Nuh Linga steps.

We know that Facebook is a very useful social media sites. This video will help you how to hide friends list on Facebook from others.

Your IP address is what identifies your personal computer while you are online. You may want to change your IP address for privacy, to bypass website settings, to download, or for various other reasons. This tutorial will take you through the steps you need to start surfing more anonymously.

Although it's always been important to safeguard your data and private information in the digital age, privacy has recently taken on an entirely new meaning.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

Mozilla's Firefox has always been a highly praised internet browser. Since it's open-source, users know what they're getting without any secrecy. It's got plenty of features that are unmatched by any of its competitors on mobile. However, speed and performance have always been a pain point for Firefox, but Mozilla went back to the drawing board to solve this problem with the release of Firefox Quantum.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

Keeping data private is vital in the days of smartphones and the free-floating information they carry. Justin wrote a guide on many of the deeply hidden and sometimes concerning privacy settings in iOS 7. Now we're back to cover some of the new (and old) privacy settings in iOS 8 that you need to address right now.

This video explains how to delete cookies in Windows XP, Mozilla Firefox, Internet Explorer and Opera. To delete cookies in Mozilla Firefox, choose the "tools" option from the tool bar, then choose "options", then choose "privacy". Many options will be given under the "privacy" menu, but make sure to choose the following options- "accept cookies from site" and "accept third party cookies", then choose the option "I close Firefox option" under "keep until" then choose "ok" to delete the cookie...

Starting to work at home? With more and more people trying to make a solid living at home, it's important to know the best way to set up a home office – even if you don't have a spare room. Learn how to set-up a solid work environment with tips from this video on how to create the perfect home office.

With social networking systems, YouTube comments chains, chat rooms, bulletins boards, Twitter updates... It seems as if almost everyone has at one time publicly stated an opinion on the Internet. Nearly half of all prospective employers research job applicants online. Make sure that what you’re posting today doesn’t cost you a dream job tomorrow!

Thanks to the Freedom of Information and Privacy acts, we’re all entitled to see what the FBI has on us. Learn how to get your hands on your FBI file.

The Droid Bionic was rooted the same day it came out with the one click method used to root the Droid 3. This tutorial will walk you through the process of rooting Motorola's Android device so that you can unlock the full potential of Verizon Wireless's flagship device.

A recent trend in freshwater fishing is adding a fluorocarbon leader to your braided fishing line. The benefits of this are mainly allowing for some more absorbtion of pull, resulting in less twist and potential tangling. This how-to will show you how to tie this knot yourself, so when you're in the middle of that beautiful pond, and you feel the bite, you'll be able to successfully land that big one with less stress on you or your gear.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

Ahhh! You're locked out of your bedroom, or your bathroom! Well, watch this video and you won't be locked out for long. Fortunately, interior privacy locks are very simple to pick. There are essentially two kinds: one that requires a blade, or knife and the other which requires a long sharp "pin" like object to insert into the handle. Check out this video and never be locked out again! You'll need something like a flat head screw driver for locks with a "slot" in them, and something long and ...
The achievement system and hard drives of modern video game consoles present an as-yet-underutilized potential for crossover content between games. Microsoft has finally taken advantage, and recent Xbox 360 releases World of Keflings, Ilomilo, and Raskulls contain some really awesome crossover content. Watch this video for a guide to accessing and using all of this awesome and visionary content.
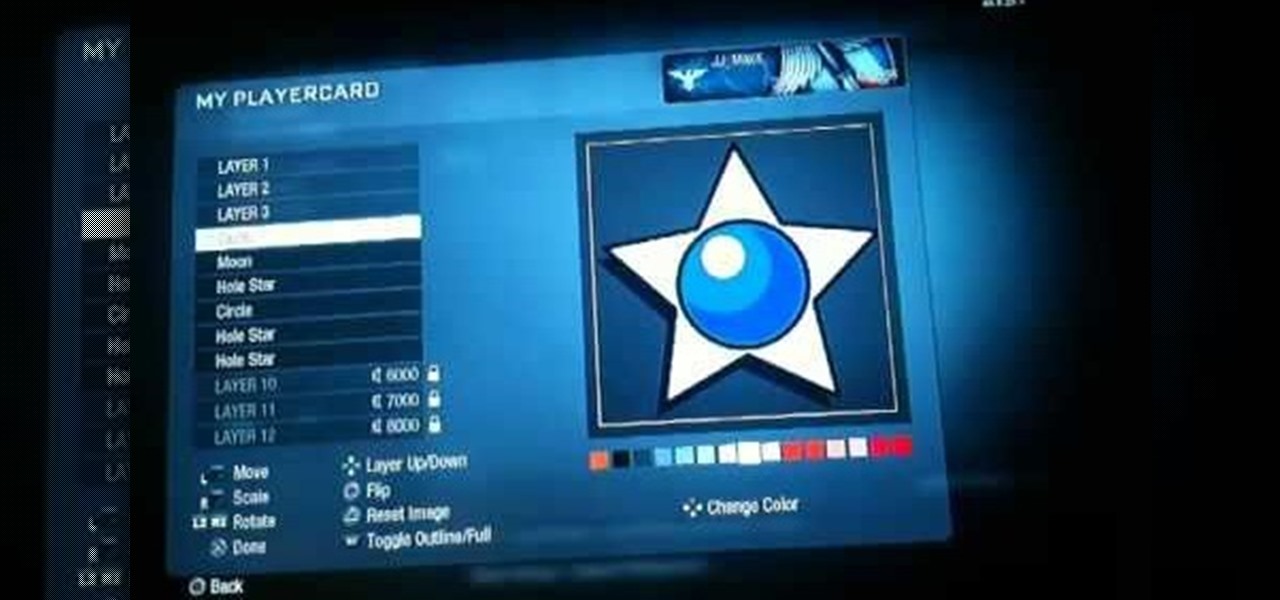
Your Call of Duty Black Ops custom player card / emblem is the first thing that a potential opponent sees about you, and you should be proud of it. This video will give you some great tips that will help you make any emblem you choose to make look sharper, less flat, and overall just plain more badass. The example made in the video is a cool star, so if you wanted a star you're even luckier!

EL wire is known as the Currency of Burning Man, and it's potential to create beautiful light in all sorts of settings is amazing. If you're tired of buying it and want to stock up on some DIY EL wire (which is more in the spirit of Burning Man anyway right?) watch this video to learn how to twist enamel and bare wire together to make your EL wire.

The first Maroon 5 album, Songs About Jane, was an awesomely funky love story, and the songs all sound great on piano and are practically guaranteed to draw potential sexual partners to you. Watch this video to learn how to play the song "Sunday Morning" on piano. It's fairly challenging, so watch out.

The Roland TR-808 drum machine is one of the most important modern instruments, forming the backbone of both hip-hop and electronic music percussion. If you have gotten your hands on one, you're a lucky devil, but you have a long way to go before you can unlock it's true potential. Watch this video to learn how to program an 808 all the way up to a 64-step beat!
Free up space on your hard drive while protecting your privacy by deleting all of the temporary files on your MS Windows desktop computer or laptop. This clip will show you how it's done. It's easy! So easy, in fact, that this handy home-computing how-to from the folks at Tekzilla can present a complete overview of the process in about two minutes' time. For more information, including detailed, step-by-step instructions, take a look.

Looking to make your HTC Evo 4G smartphone even better? Unlock your phone's full computational potential by installing Linux on it! This video guide presents a complete, step-by-step walkthrough of the process. For more information, and to get started installing the Ubuntu Linux distribution on your own Android smart phone (without blowing out your phone's Android installation), take a look!

We all have our reasons for erasing personal data from a phone. Whether you just ended a bad relationship whose face you never want to see again (lots of text messages) or just want to restore your privacy on the cell phone, erasing may be your only option.
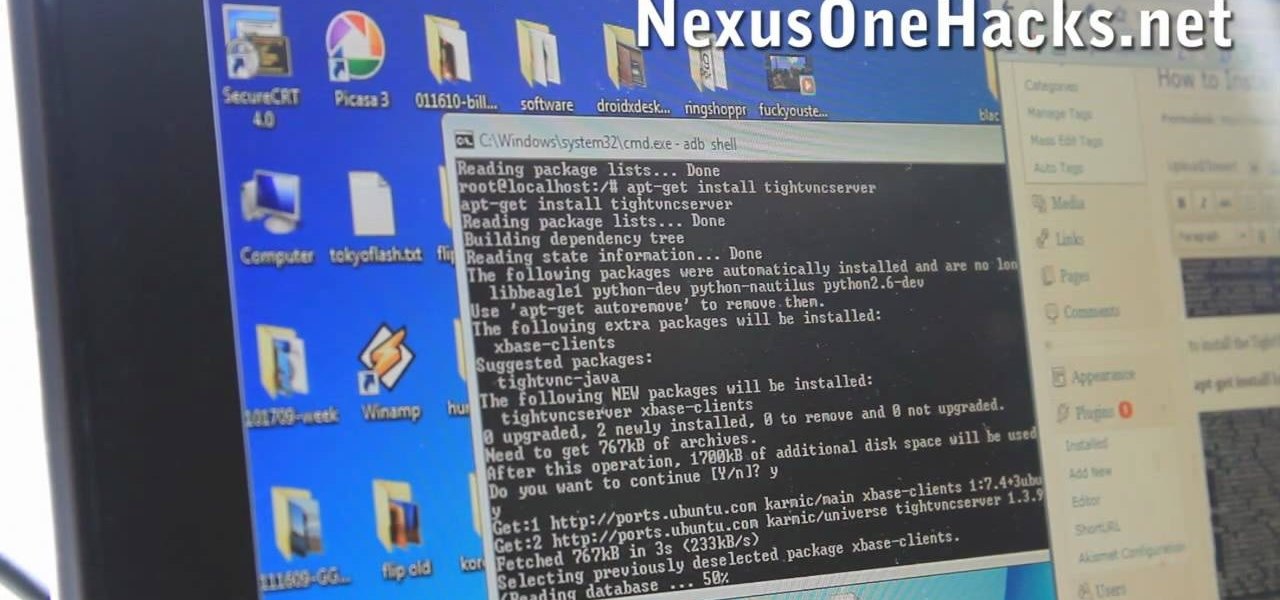
Looking to make your Google Nexus One or HTC Evo smartphone even better? Unlock your phone's full computational potential while following in a tried-and-true geek tradition: Install Linux on it! This video guide presents a complete, step-by-step walkthrough of the process. For more information, and to get started installing the Ubuntu Linux distribution on your own Android smart phone (without blowing out your phone's Android installation), take a look!

If you like your privacy, you probably hate snoopy people, and when it comes to your briefcase, you don't want anyone's paws on it besides your own. To keep their hands off your precious belongings, you need to take some drastic measures…

Waxing should be as painless as possible, which is why girls turn to sugar waxing to remove their hair monthly. But don't shell out wads of cash having someone else rip thick-rooted hair from your hindquarters.