How To: Send a private wall post on Facebook
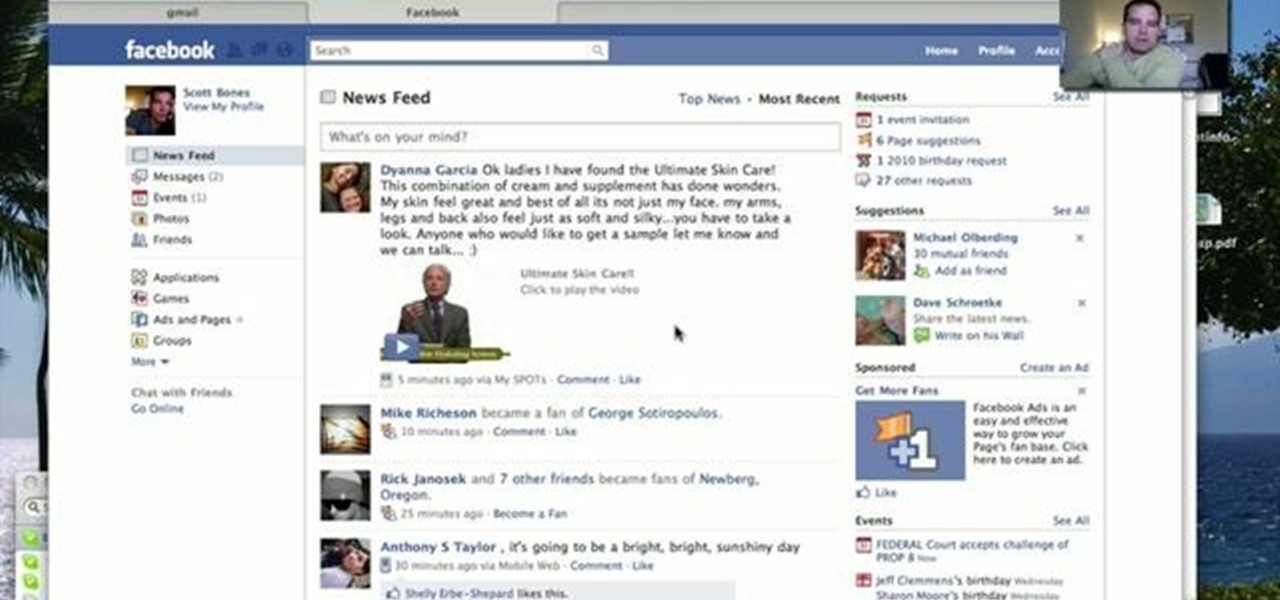
Privacy is important on Facebook, a lot of users don't even realize that their posts are being broadcast to the masses.


Privacy is important on Facebook, a lot of users don't even realize that their posts are being broadcast to the masses.

How to Belly Dance! Okay, so you can shimmy and you can shake, but you ain’t seen nothin’ until you’ve seen a skilled belly dancer strut her stuff. Here are a couple of basic belly-dancing moves to awaken your inner Shakira…

Need to keep people out of your precious room? Tired of all of those "do not disturb" signs not working? Locks just aren't cutting it these days? Safeguard your privacy with your very own electric fence. Remember Jurassic Park, when the kid got zapped by the electric fence? Think that, but in the doorway of your room.

This video won't show you how to crack a safe but it will show you the next best thing: cracking a combination lock or master lock! We do recommend only trying this on a lock you have forgotten the combination to and not other unlawful purposes. Watch this video tutorial and learn how to retrieve the combination from a lock. Hack your own lock or your friends and you have the potential for great practical jokes.

With all the talk about privacy concerns recently, Google's name keeps coming up because they are a very data-driven company. As an Android user, they know basically everything about you based on your device usage. That can easily scare some people off who are worried about their privacy and security. You do have some say in what personal data Google controls, but what if you want total control?

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.
Can you trust every user you come across on TikTok? The answer to that may depend on how use the service, but the real question is — can you trust every user that sees your content? Not everyone on TikTok is someone you want viewing or interacting with your content, and there's a way to prevent them from doing so.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.
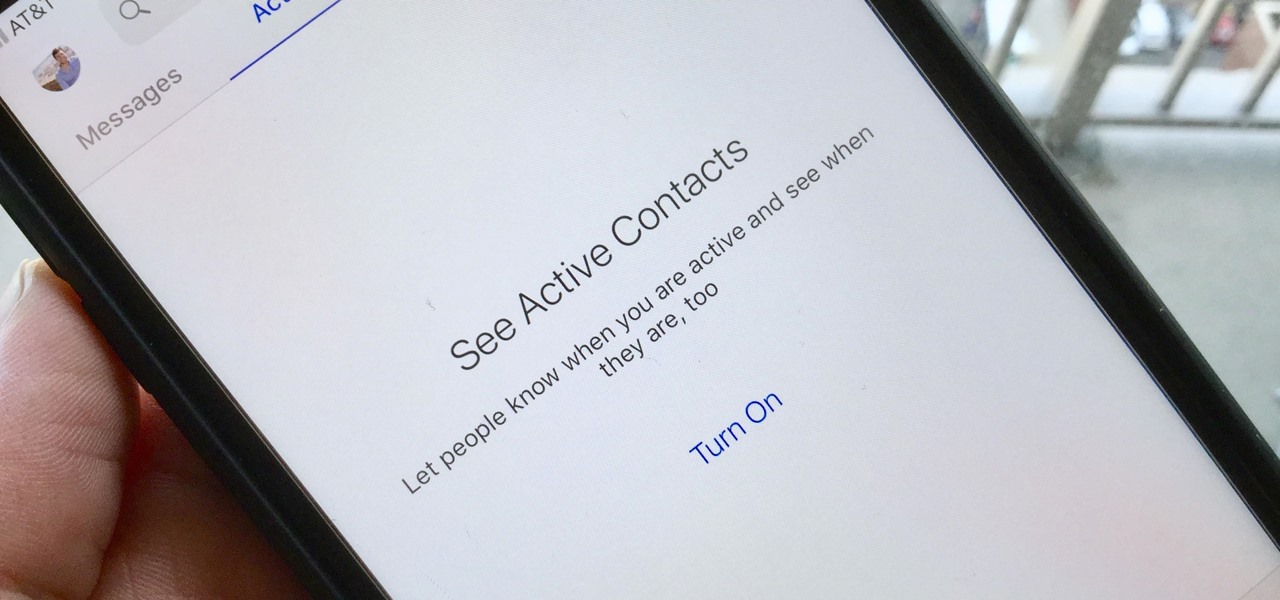
For all of its advantages, Facebook Messenger isn't the best for people who like their privacy. The popular app lets all your Facebook friends know when you're online by default, as well as how long you've been idle, making it impossible to check up with one person without leaving yourself vulnerable to your entire friends list. Luckily, this feature is one you can turn off.

When you visit a website in Safari, it's most likely keeping tabs on your browsing activity. It could be keeping track directly, or its third-party content providers and advertisers can be spying on you. All three could happen simultaneously. This enables them to serve you content that's tailor-made for you, but it can also feel like an invasion of privacy.
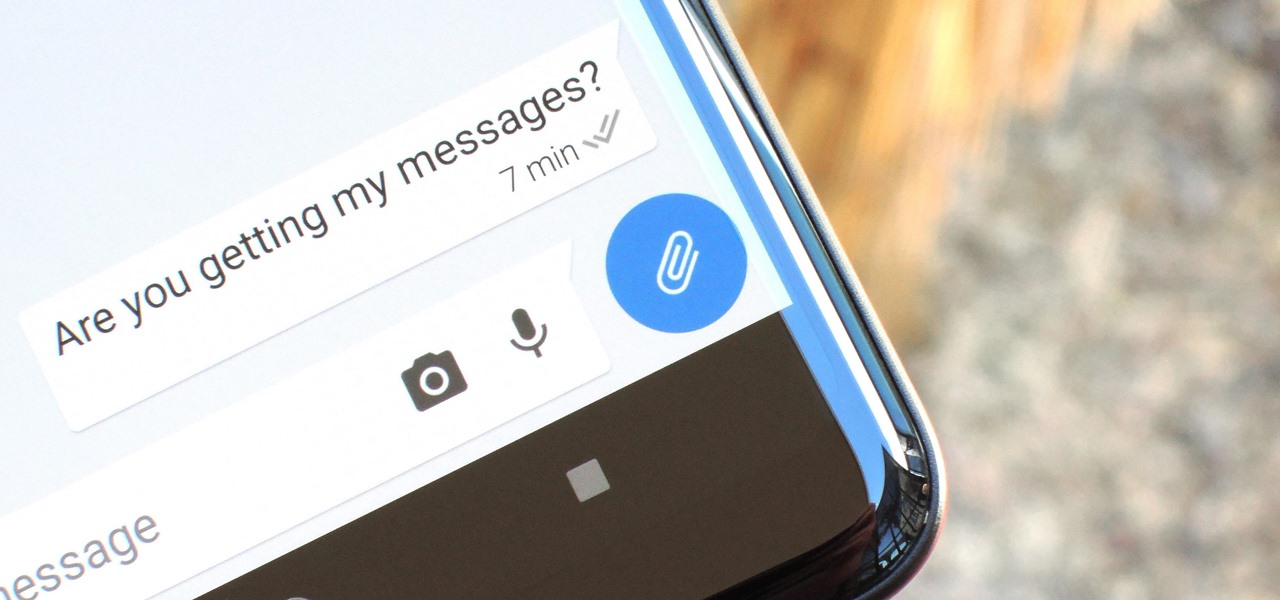
After receiving many requests for the feature, Signal introduced read receipts last year to its mobile apps. However, some users don't like the idea other people knowing when they've read messages. Luckily, Signal lets you disable this feature and reclaim a little privacy.
Most of the free apps you'll find on the Play Store have ads. These ads are personalized — in other words, they're for products and services Google believes you might be interested in. The way Google knows about your interests is by collecting data from your smartphone, including your location and app usage. While personalized ads have their advantages, the collection of data is unsettling.
If you're tired of Google tracking you, but love how Chrome works, CyanogenMod has you covered. Their browser is called Gello, which is based off Chromium, Chrome's open-source counterpart. It's basically a souped-up version of Chrome—without all of the intrusive Google stuff. So if you're uncomfortable with Google displaying personalized ads based on your browsing history, or using your location to bring the "Physical Web" to your phone, you won't have to worry about any of that with Gello.

If you like having Siri available to answer a quick question every now and again but don't want everyone who picks up your iPhone to also have access to your personal assistant, there's an easy way to disable her from working on your iPhone's lock screen. This is also something you can do if you're always activating Siri accidentally in your pocket.

In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent.

Let's just say it's been a pretty bad year for spies and government agencies and an even worse one for the privacy of U.S. citizens. Edward Snowden blew the lid off the NSA's spy program, and the FBI was recently discovered to have the ability to access your webcam any time they want—without triggering the "camera on" light. Yeah, that means those Justin Bieber lip sync videos you recorded weren't just for your private collection.

How much privacy are you getting as an AT&T customer? With the recent leaks confirming the National Security Agency's surveillance on AT&T users, and the ongoing trial of Jewel v. NSA, it seems not much at all.

If you're a frequent Snapchatter like myself, you're probably well aware that Snapchat can't stop you or anyone else from taking a screenshot of a photo received. Instead, they notify the sender that a screenshot was taken—a greatly appreciated fair warning when impetuous photographs are involved. However, there is a loophole to this.

Microsoft's updated web browser, Internet Explorer 10, has only been out for a few days on Windows 8, and there is already a storm of controversy surrounding its launch.

If you've read anything in the news about Skype recently, it probably hasn't been good. First, there was the controversy over the company listening to and recording users' conversations. Now, there's a new spam tool for Skype that can harvest usernames, see whether or not you're online, and even parse your log files. Image by Lloyd Dewolf
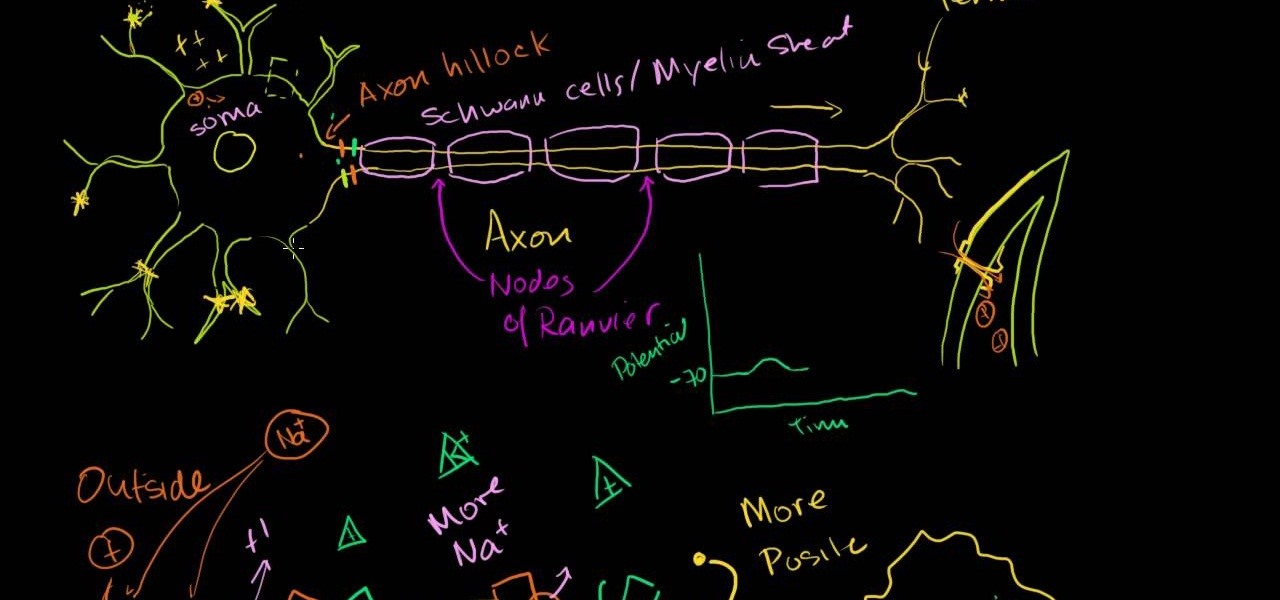
This video is a discourse about saltatory conduction in the neurons. According to the author, it begins with the opening of a gate on the membrane of one of the dendrites of a neuron, and positive charge enters through this gate. The positive charge spreads throughout the cell, and gets dissipated as it spreads, so that, by the time it reaches the Axon hillock of the neuron, it is left with very little potential. However, the potential which results from the simultaneous excitement of many de...

Vanae presents a video about dating a woman who is already married. Monologue to a question presented by a subscriber to her video blog. In her opinion it is not wise or acceptable to date someone who is married or dating already. Reasons to not date a married person and different potential things about what could happen including the block on having a full relationship, the potential karma, and a few other aspects of what this could mean to you.

One thing you should do every time you approach a tool is think of the worst-case scenarios. Its a bit gruesome to let your imagination take you there, but there is a good reason for it. This simple mental exercise not only raises your awareness of the potential dangers, but essentially shows you exactly what you need to do to prevent injury. This how to video walks you through potential dangers in the workshop and how you can avoid each one.

The video begins with a finished fence being shown as an example of what your final product should look like. The first step is to lay out straight lines with string to create the outline of fence parameter. To set the first post you must dig a five inch hole in the ground which the post is placed in. The post will be set along the string line spaced out about four inches evenly along the parameter. the holes must be filled in with rock or cement to set them securely. You must then nail board...
In this clip, you'll learn how to adjust your privacy settings to prevent your friends from sharing your personal information on Facebook. Share pictures with your friends by making photo albums on Facebook. This clip will show you how it's done. Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to perform a particular task on Facebook, you're sure to benefit from this helpful video guide. For more informati...

Want to be as secure as you can while you surf the web? The EFF and the TOR project have brought you HTTPS Everywhere, a Firefox addon that encrypts as many websites as possible. This clip will show you how to use it. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in just over two minutes. For more information, including complete, step-by-step instructions, take a look.
Are you sick of Facebook's ever-changing privacy practices that opt you into anything and everything without even asking you if you care? Watch this video to learn how to delete your Facebook account. Permanently. Make sure you don't log in for 14 days after your account closure. Free yourself from having to check your Facebook status every 5 seconds, from having to be "connected" to everyone you know and from Facebook itself.

If more privacy in your car is what you seek, you may want to consider installing a dark tint to your windows. In this tutorial, Mike Burke of Sunstoppers shows you how car tinting is done right. Mike will show you how to apply a tint just like the professionals do, so that you can get some info on how it's done.
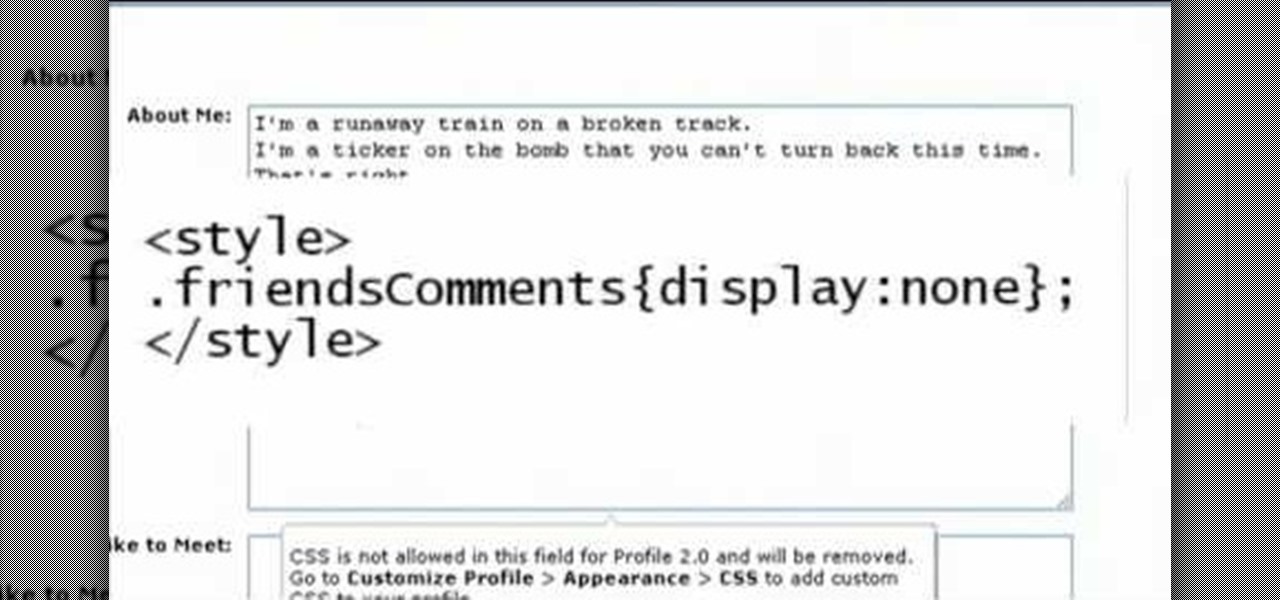
Want a bit more privacy in your MySpace account? Here's how to hide comments in MySpace. After you login, you should see a button that says 'edit profile' near the top. If you have a MySpace 1.0 profile you have to go to the 'About Me' section and at the bottom of it type this exactly like you see it here
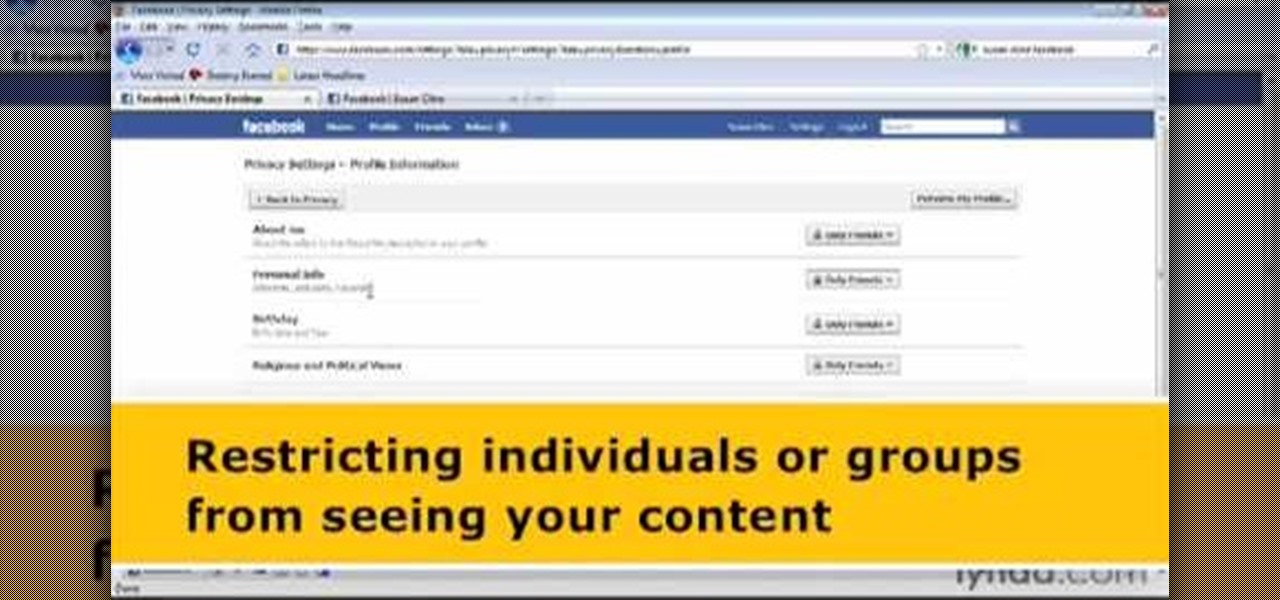
Facebook is one of the most popular social networking sites out there, so make sure you are being safe! Susan Kline shows you in her Facebook Essential Training series how to Restrict certain aspects of your profile. Login to Facebook and view your Privacy Settings. From there you can pick your About Me, Personal information, Wall Post, Photos and more and restrict showing it to people. You can pick everyone, certain friend lists, Networks, and even individualize it down to one person.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.
Uber as a service is great, but using it requires you to hand over your location data to the company. What's worse is that you may be giving them precious access to your GPS even when don't have the Uber app open. This is both a major privacy issue and a drain on your battery. Fortunately, some of you can fix this.
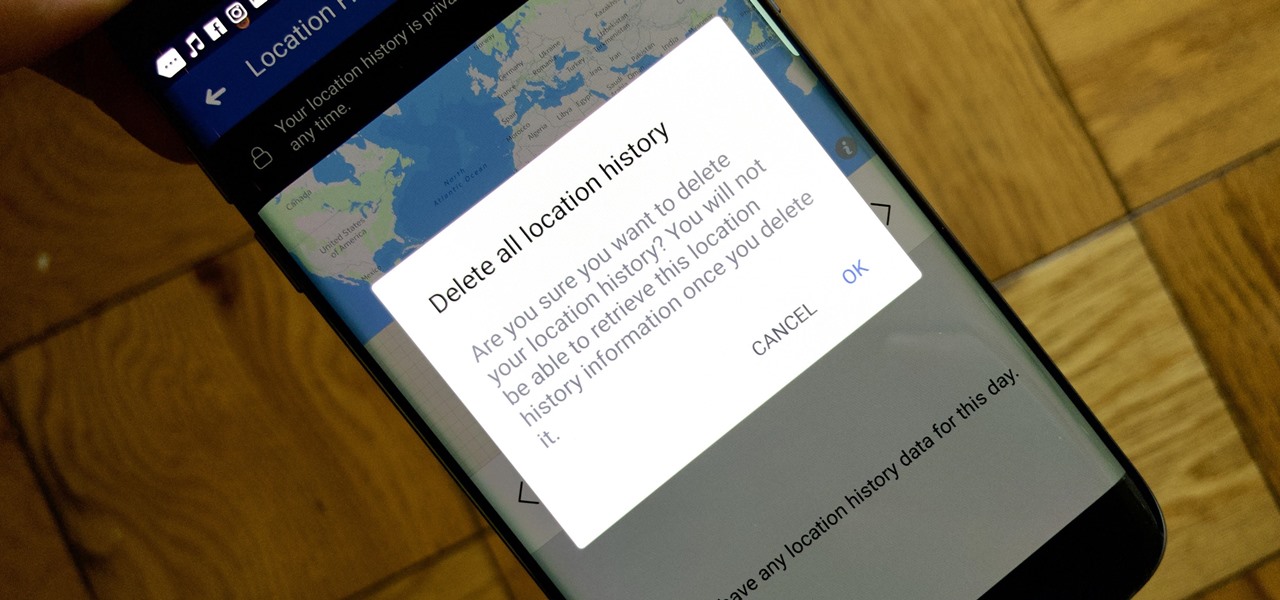
Facebook's shadiness when it comes to user privacy has never been much of a secret. The Cambridge Analytica scandal, however, has thrown the company and its practices into the limelight, with users taking their data more seriously than ever. If you're one of those users, you might want to check your "Location History" to see if and how Facebook's kept tabs on your whereabouts.
WhatsApp comes with a ton of great features that make it the go-to messaging app for millions of people around the world. Among these is the ingeniously simple Read Receipts that let you know your message has been viewed. If you want to read a message without alerting the sender, however, there are simple tricks you can perform to give yourself plausible deniability.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Taking a cue form Snapchat, WhatsApp Status lets you share updates that come in the form of GIFs, photos, videos and good old text. This awesome feature is available for both iPhone and Android users, and it even lets you choose which contacts to share with while disappearing after 24 hours.

WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still!

Your Android phone could be listening to ultrasonic ad beacons behind your back. The unwelcome news comes year after app developer SilverPush promised to quit using its (creepy!) eavesdropping software.

Our future technology has a lot of amazing possibilities, and few have more promise than augmented and mixed reality headsets. But these advancements come with several concerns over privacy, and if we don't understand them, we may lose control of our own data without even knowing.