
How To: Charge a Cell Phone on Train Tracks
If you're ever lost or hurt out in the middle of nowhere with a dead cell phone, you might be able to "flag" down help as long as you're near some railroad tracks.


If you're ever lost or hurt out in the middle of nowhere with a dead cell phone, you might be able to "flag" down help as long as you're near some railroad tracks.

Over the course of the past century or so, media consumption has gone from a few readers enjoying their local print publication to billions of users viewing countless hours of video across the globe each day. This was a gradual evolution at first, but recent advancements in mobile connectivity have sent us into a climb the likes of which we have never seen before.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

Unless you're in law enforcement, you won't usually have a flashlight on hand for those rare moments when you need to sift through the dark. However, it is very likely that you will have your phone on you, so you'll have fast access to a bright light with just a few easy taps.

Every phone has its issues and quirks, and the Nexus 5 is no exception to this rule. One of the most common troubleshooting questions asked by its owners is "Why does my Nexus 5 keep shutting off or restarting?" where the device suddenly decides to reboot or power off randomly on its own.
Ready or not, the USB-C cable is about to take over your electronics. The new industry standard is fully reversible and packed with enough power to serve as a laptop charger or an HDMI cable, so it actually has the potential to replace every cord, wire, and connector in your house. In fact, the conversion has already started: The latest MacBook, Chromebook Pixel, and Nexus phones are sporting USB-C connectors out of the box.

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!

With a slab-style touchscreen device, butt dialing is always going to be a problem. While you're moving about, your phone can unlock itself and give your most recent contact a ring, leading to an awkward one-sided conversation where the other person gets to eavesdrop on everything you're doing or saying at that moment.

Those of you who have been a part of the Null Byte community for even a short while know that I sincerely and firmly believe that hacking is the most important skill set of the future.

When it comes to news, updates, and arbitrary nonsense, it's hard to find a better source than Twitter. And for some of us, the best way to consume Twitter is through the web (versus a mobile app). But as much as I prefer the standard browser version, it's easy to make it better, faster, and more convenient using a few Chrome extensions—and here are my favorites.
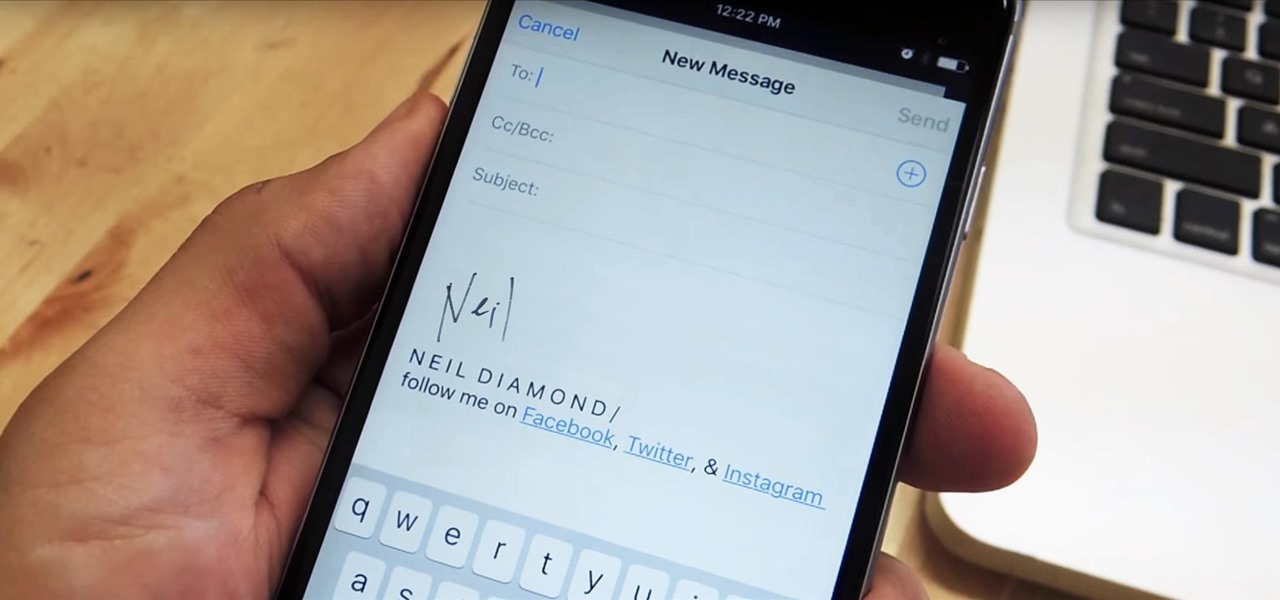
Emails sent from an iPhone, by default, are signed "Sent from my iPhone," which almost seems like a disclaimer in case the email has spelling or formatting errors. If your goal is to look professional while corresponding with coworkers or potential employers, then you're better off removing the signature completely and just typing your name out.

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

In an age where restaurants can charge $20 for eggs Benedict at brunchtime (if you're lucky enough to even get a reservation on a Sunday), many people long for a way to create this classic dish at home. But once you've taken pains to perfectly poach an egg and gently crisp your sourdough, the problem of the hollandaise still lies before you. The key to any good hollandaise sauce is to apply enough heat to cook the egg yolks, but not enough to scramble them. The minute the eggs begin to solidi...

All of those keys on your keyboard can do much more than just help to update your Facebook status or fire off a scathing tweet. By learning all of the keyboard shortcuts for apps on your Mac, you can cut back on mouse or trackpad usage to perform actions faster and more efficiently.

Welcome back, my hacker novitiates!

I have a thing for black foods, whether it's mysterious, lovely black garlic (the secret to its color: fermentation) or adding charcoal powder with its reputed health benefits to cookies, cakes, and breads.

Potato peels are largely misunderstood creatures. They're shucked away from every mashed potato dish like some icky rag that has no business in your kitchen. PS: Quit it. By ditching the peels, you're not only missing out on fiber and large amounts of potassium (even more than a banana), you're tossing the potential for chewy, crunchy finger food. So the next time you're left with a plate of scraps, here are four tasty reasons to hold onto them.

Food waste is a topic near and dear to my heart, but the truth is, no matter how dutiful we are about finding ways to double-down on food scraps, a lot of stuff goes into the trash needlessly.

There are a lot of frustrations when you're dealing with cramped living quarters, but you can do a lot of good cooking in your tiny kitchen if you make the most of your space. These storage hacks will make it easy to cook delicious meals, no matter how limited your square footage.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Eye contact is key in conversations, job interviews, and honesty, and it can help you access others' thoughts and spot heavy drinkers. Locking eyes with someone can even help you fall in love, whether you know them or not.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

Starting with the original HTC One and now present on the new Nexus 6, dual speakers allow for smartphones to pump out true stereo sound. OnePlus, however, kept their speakers on the bottom of the device and use different sound drivers for each to produce great sound quality, although it's still mono. While there are mods out there that can further increase the volume of the OnePlus One, none of them can produce true stereo sound.

Garlic: almost every cuisine in the world considers it a staple, and for good reason. Its pungent flavor gives depth and character to food. Dishes made without it seem bland and forgettable. And on top of all that, it's been studied for its potential anti-cancer properties (and don't forget: it's been mythologized for warding off vampires).

If you have ever attempted to mix and shape your own meatballs or burger patties, you may have endured bits of meat continuously and stubbornly sticking to your hands. This can make shaping more challenging than it should be.

When Yosemite was released, a more detailed boot screen came to your Mac. So now, just like on Apple's mobile devices, you will see a loading bar telling you how far into the startup process you are. Apple also decided to add a black version of this boot screen to newer Macs, leaving those of us who purchased a computer before 2011 out of the loop.

Admit it: when nothing's at stake other than your boss's disapproval, you don't exactly feel the urge to get working. Finding the motivation to take on a task, whether at work or home, can be a constant struggle. Though working through your laziness might seem like the best course of action, a meaner method can make more of an impact on your productivity.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Investing is like exercise—we all know we should be doing more of it, but we often just can't find the time. I mean, really, who's got the hours, inclination, and skill to pour through volumes of data and put together a balanced yet sophisticated portfolio of investment vehicles tailored specifically to optimize their returns while mitigating potential risks. Not me, that's for sure.

Garlic isn't just a food, it's a legend. It's been found in the pyramids of Egypt and is referenced in the Bible. Hippocrates, the father of Western medicine, prescribed it regularly, and it was given to the first Olympic athletes in Ancient Greece to enhance performance (take that, Lance Armstrong). And, of course, it's famed for its ability to ward off evil, whether it's in the form of vampires, demons, or werewolves.

Losing your phone is a much bigger ordeal today than it was just 10 years ago. Our smartphones carry with them lots of sensitive data that, in the wrong hands, is capable of being used for identity theft and fraud.
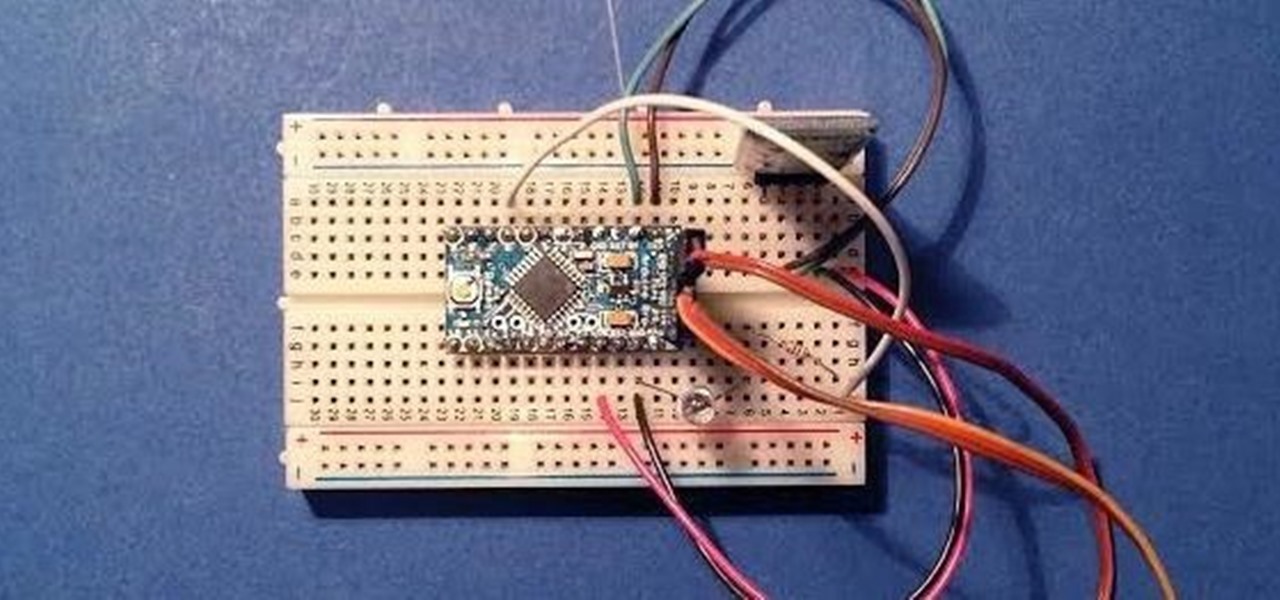
Since its creation, Arduino has been growing exponentially more popular as DIY enthusiasts and Makers alike realize its potential. As new versions of the device are released, many easy-to-use peripherals are showing up on the market also.

Sometimes, it helps to be prepared before jumping into a new relationship; look before you leap! To have a healthy relationship with someone who has an STI, it is advisable that you enter the relationship knowledgeable about sexually transmitted infections and what your risks might be.
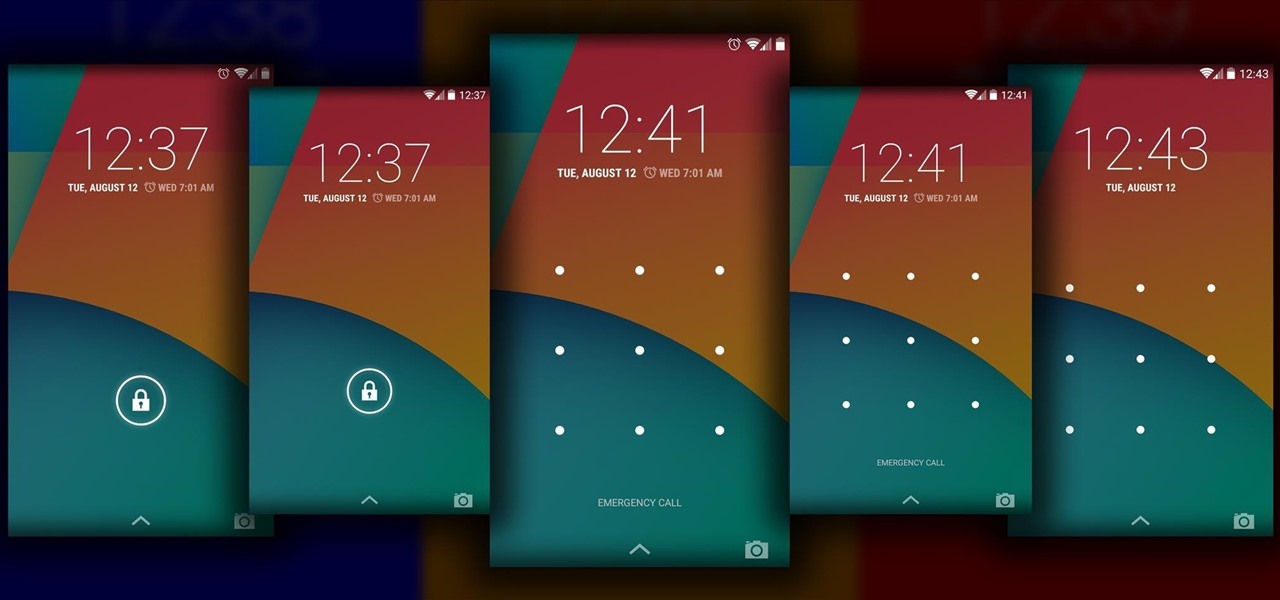
The Android lock screen interface is an integral part of our everyday use. For those of us who use lock screen security, it functions as a barrier between the sensitive data contained within our smartphones and potential outside access. Even if you don't use a pattern or PIN to secure your phone, you still interact with the lock screen every time you go to use it.

You're in your car. You've got a bag of piping-hot French fries with you. You want those fries in your mouth ASAP, but you also want to dip them in ketchup. So what do you do?
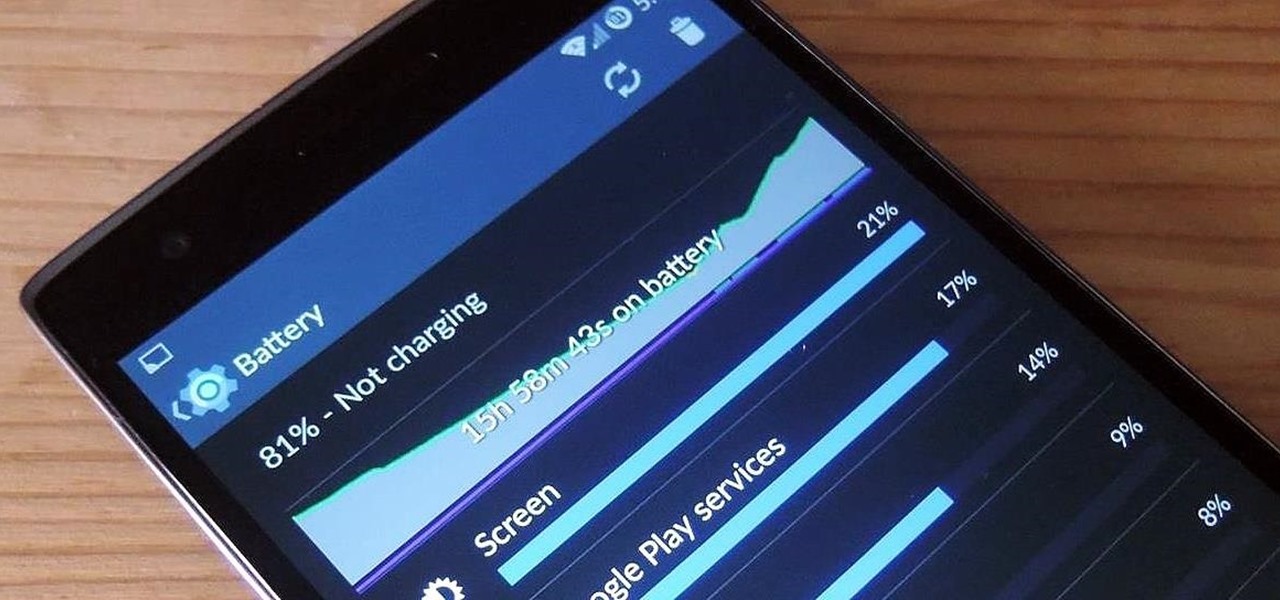
The new OnePlus One packs a 3,100 mAh battery that promises to last all day and night. While that will work for most, some of us don't quite know how to put our phone down and save some juice.

Time is money, and if your job requires sending out hundreds of generic emails—think "Thank You" notes and sales pitches—you could save days of work by creating templates stored within your Gmail called "canned responses."

Koushik Dutta, the developer behind the Android app AllCast, has made the leap over to the realm of personal computers with his latest offering.
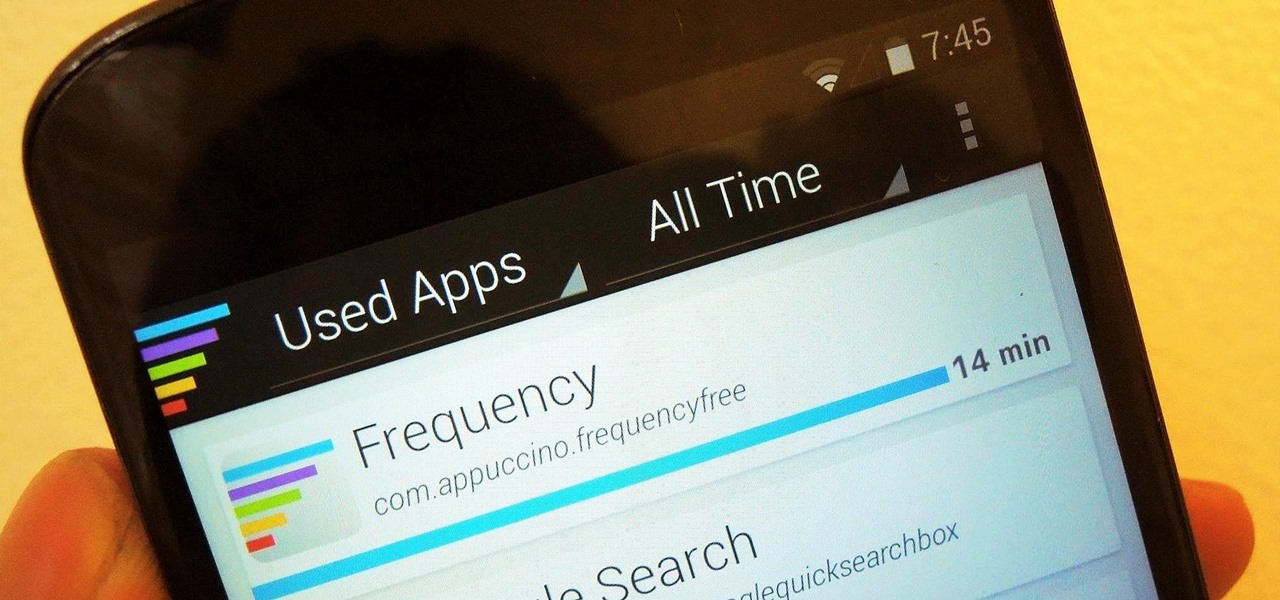
As a parent, navigating smartphone usage with your children can be a perilous journey as you hand them that new device they've always wanted, or even your older hand-me-down phone or tablet.

Facebook rolled out a new feature that lets your friends ask you about your current relationship status. This is great feature if you use Facebook for finding hookups, but if you use it mostly to connect with family and friends, a bunch of questions about your dating status can get annoying real quick.