Even when no one is in your kitchen, it is crowded. The refrigerator, sink, and counters are all covered with microbes that are just hanging around. They are inadvertent remnants from the raw chicken you used in that recipe last night, brewing a bacterial cocktail in your Nespresso machine, or just growing their merry little colonies on your leftovers.

Each generation of smartphones ushers in a new set of top-of-the-line specs, with processing power, battery size, and display resolution growing by the year. These headlining features get the most press, but there's one unsung hero that has the potential to make the biggest difference when it comes to real-world performance: RAM, or random-access memory.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Google is working on something so big they had to name it after an entire galaxy: A new operating system that merges Android and Chrome OS into one unified front.
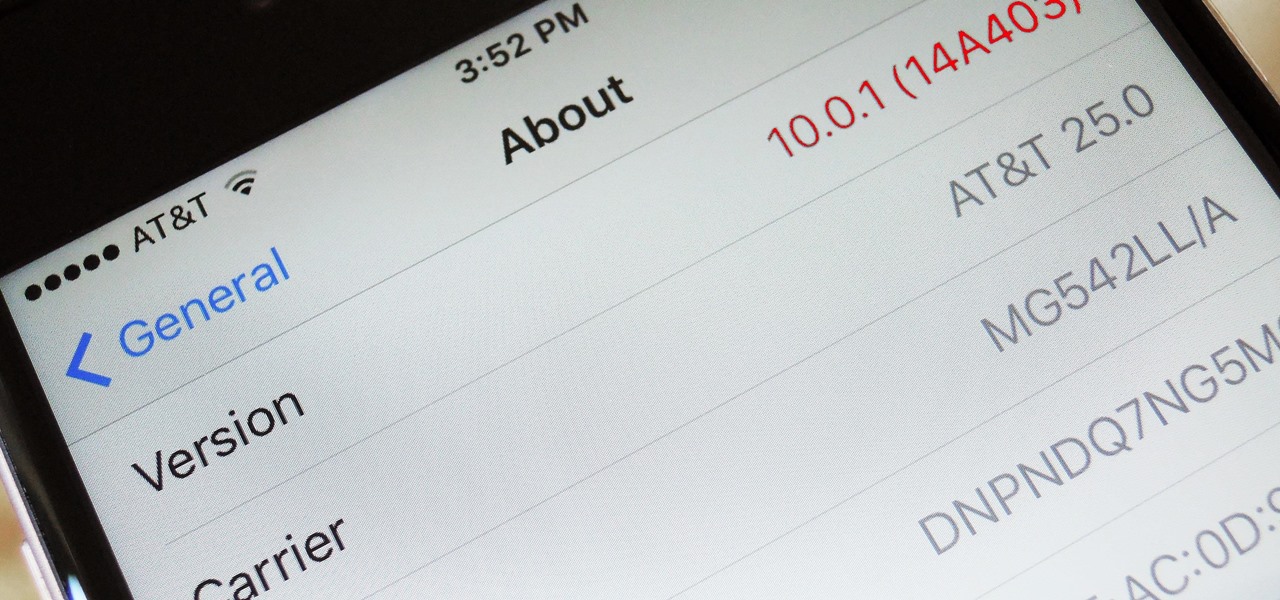
When a new version of iOS comes out, everybody gets caught up in the craze of finding features and playing around with new functionality. But this generally leads to a lack of coverage on the finer aspects of the update—things like bugs, minor tweaks, and pain points that users discover along the way.
Throwaway phones aren't just for seedy criminals and spies—they can be useful for many everyday situations.

Watching an ice cream pro build you a custom frozen treat mixed with your favorite fruit, candy, and/or toppings makes buying a cone even more exciting. But why go out for ice cream when you can create your favorite combinations in your own kitchen? While you might not have an expensive frozen slab for ice cream topping your kitchen counters, you can mimic the creamy consistency and customizable options from Cold Stone Creamery and Marble Slab any time you're craving it. Best of all, you don'...

Pokémon GO made waves as the first augmented reality game to gain popular adoption. In fact, it was so popular that it only took a few days to uncover some the benefits and serious issues with combining physical and digital worlds.

Our future technology has a lot of amazing possibilities, and few have more promise than augmented and mixed reality headsets. But these advancements come with several concerns over privacy, and if we don't understand them, we may lose control of our own data without even knowing.

It was definitely a shocker when Microsoft proposed cross-network play between the Xbox One and PlayStation 4 last month. After all, Microsoft and Sony have been competing for the same user base for more than a decade now, and this new feature might actually decrease console sales as a whole.

Okay, so you finally got around to rooting your Android device—now what? Well, to get the most out of your Superuser status, you'll need to find some good root apps, which will allow you to easily add features, reduce battery drain, remove ads, and much more.

My daughter moved into her first apartment last year, a huge rite of passage in any young person's life. With a mother and two grandmothers who are good cooks (to say the least, in the case of the latter), it's not surprising that she turned to us for some advice about how to improve her own skills in the kitchen. Without question, the single best piece of advice we have given her is to employ mise en place each and every time she prepares a meal.

Smartphones have been a hot button issue around school campuses for several years now—some schools allow them, others confiscate them on sight. But the fact of the matter is, when used correctly, a smartphone can be just as much of a learning tool as a textbook or school-issued laptop.

Amazon is slowly trying to gain as much influence in the tech world as it has in the consumer market, and with the Amazon Fire HD 7, they have their eyes set on taking on the "budget tablet" space.

In the last iteration of how to train your python, we covered if/else and conditional statements. We're going to diverge a little today and cover lists. Lists are simply that, lists. It is a set of values located under one variable. Now that we know the definition of a list, let's learn about them! List Basics

Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know-how can change your memories for their own personal benefit, and you can do so to others, too.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Hello my fellow hackers, it's been a while since my last post, I can't get the time now-a-days for the posts but can manage to tend to comments.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

What's your top pet peeve? Open-mouthed chewing? Nail biting and knuckle cracking? The sound of silverware scraping? Or perhaps it's a bigger behavior, like leaving the toilet seat up?

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

The telecommunications industry has come a long way since Ma Bell opened the first telephone exchange in the late 1800s. With the advent of fiber optics and wireless broadband technology, we no longer have a need for a dedicated phone connection, as today's data networks can carry much more than a simple voice conversation.

Both the Galaxy S6 and S6 Edge have had root methods available to them before the phones were even released, but the problem with these existing root methods is that they would trip the KNOX counter on your device.

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

Without a comprehensive root method for all Android phones and tablets, a device-specific approach is needed. And since we always cover new rooting methods for all the popular phones here at Gadget Hacks, we've built this always-updated guide to rooting many mainstream Android devices.

If you've already read the first part exploring what geniuses actually eat as opposed to what the rest of us are told to eat for brain health, you've noticed that there are some big discrepancies. Instead of favoring healthy, wholesome foods high in antioxidants, lots of high-achieving types tend to go for caffeine, sugar, and processed foods. One notable health habit practiced by many: eating breakfast.

Welcome back, my apprentice hackers! In this series on password cracking, I have been attempting to develop your skills in the age-old art of password cracking. Although it might seem like a simple and straightforward exercise, those of you who have attempted password cracking know that there are many subtleties to this art.

With a root bounty of over $18,000 up for the taking, developers were highly motivated to get the AT&T and Verizon Wireless variants of the Samsung Galaxy S5 rooted. Legendary hacker George Hotz, aka Geohot, has won the race and can now step up to claim his prize.

A friend of mine has a crazy amount of Reddit karma and gold, and yesterday he let me in on his secret. This person, who will remain unnamed for obvious reasons, created a Python script called Reddit Karma Crawler that finds rising posts before they get too popular.

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.

While landing a job isn't the easiest thing in the world, you can probably blame your résumé for a number of lost opportunities. Writing up a cover letter and résumé is frustrating and time-consuming, but if you spend the time to get them right, the effort will drastically increase your chances of getting employed.

Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by developing your scripting skills.

Welcome back, my aspiring hackers! Those of you who've been reading my tutorials for some time now know that I am adamant regarding the necessity of learning and using Linux to hack. There is no substitute, period.

You probably already know by now that a custom Android ROM can change your user experience and give you what feels like a new OS on your device, and there's no shortage of them out there to try out.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

I've never had a black eye, but I was in a car accident that turned my entire ear dark purple a few years ago. Believe me; it was enough to get more than a few funny looks.

Why can't I see who is stalking my Facebook profile?

Last time, I showed how to start putting together an AC arc welder from scavenged microwave parts, focusing on the transformer modifications. Now, I'll show you how to finish up your DIY stick welding machine by fixing up the electrical system and performing the finishing touches.