
How To: Get Fortnite Battle Royale Running on Almost ANY Android Device — No Root Needed
UPDATE: The ported APK covered below is now obsolete because Fortnite beta is officially available for all Android devices!


UPDATE: The ported APK covered below is now obsolete because Fortnite beta is officially available for all Android devices!
If you're a console or PC gamer, you may be quick to ignore the mobile version of Fortnite Battle Royale. The lower graphics and the switch to touchscreen controls may be enough reason to dismiss this version of the game. But don't be so quick to judge — there are actually some clear advantages to playing on mobile.
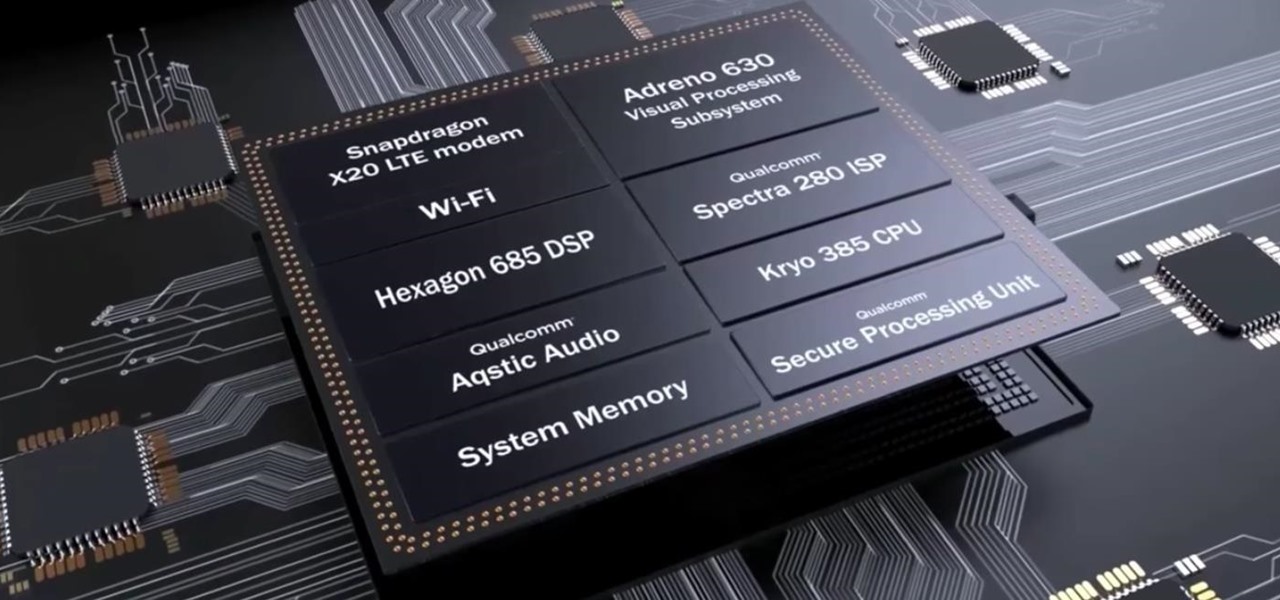
After the success of the Snapdragon 835, Qualcomm now has its eyes set towards the future with the arrival of its next-generation SoC, the Snapdragon 845. Debuting alongside the Samsung Galaxy S9, the 845 is now set to take over the market for flagship Android phones in 2018.

One of the standout features of Nova Launcher is its vast customization options. Not only does it includes numerous tweaks to alter the aesthetics of your home screen, but it even has plenty of features that reduce clutter. One area of our device that has a high potential for disarray is our home screen.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

Andre was enjoying the carefree life of a 12-year-old with his friends, riding his bike and playing sports, like all kids that age. Schoolwork wasn't hard for him, and his grades showed that.
The growing list of dangerous antibiotic resistant organisms has just acquired three new members. Researchers have discovered three new species of Klebsiella bacteria, all of which can cause life-threatening infections and have genes that make them resistant to commonly used antibiotics.

More than one in ten people in the US have type 2 diabetes — that's over 29 million people. It's characterized by excessive sugar (glucose) in the blood due to the development of resistance to insulin, the hormone that normally metabolizes glucose.

For a company more associated with debugging computer programs, Google's parent company, Alphabet, is making a name for itself by taking on the real thing — mosquitoes.

Sex makes the world go 'round, and when it does, so does gonorrhea. Finally some good news on the growing menace of drug-resistant gonorrhea — a large, long-term study shows a vaccine may work in reducing the incidence of an increasingly dangerous infection.

Peach trees and other related plants are susceptible to the devastation caused by fire blight, a contagious bacterial disease. Once contracted, infected trees have to be burned to contain the disease and prevent spread to nearby trees. Increasing resistance to antibiotic treatment has sent scientists in search of alternative ways to deal with the bacteria and prevent its catastrophic damage.

The search is on to find antibiotics that will work against superbugs — bacteria that are rapidly becoming resistant to many drugs in our antibiotic arsenal.

Despite the threat of superbugs, physicians continue to prescribe antibiotics when they might not be needed, and patients are suffering.

The leading platforms enabling augmented reality technology lead our headlines in Market Reality this week.

The problem with HIV is that it attacks and kills the very cells of the immune system that are supposed to protect us from infections — white blood cells. But a new technique, developed by scientists at The Scripps Research Institute (TSRI) in La Jolla, California, offers a distinct HIV-killing advantage.

An innovative new wound dressing has been developed by a research team at Lodz University of Technology in Poland that uses crustacean shells to create a bandage that packs an antimicrobial punch — and even more potential to help solve a global problem.

Mixed reality display manufacturer Realfiction has developed a 64-inch display capable of delivering 3D holograms without a headset.

Our quest to find new antibiotics has taken a turn — a turn down the road, that is. A team of scientists from the University of Oklahoma is scooping up roadkill and searching for bacteria on them that might yield the world's next antibiotic.

If you ever imagined turning the surface of your desk into one large augmented computer, well the future might not be far off, my friends. Lampix, the company that transforms any surface into a smart surface, is currently working on a portable and quite fashionable lamp to project an augmented computer onto any surface that you can interact with using your hands.

The search for a cancer treatment that selectively finds and kills only the cancerous cells has just made a giant leap forward.

Hospitals are places we go to get well, and we don't expect to get sick or sicker there. But a study from researchers at the Cleveland Clinic, Case Western Reserve University School of Medicine, and Cleveland VA Medical Center in Ohio found that hospital floors in patient rooms were frequently contaminated with healthcare-associated pathogens—often dangerous multi-drug resistant bacteria.

Somewhere around 600–800 million people in the world are infected with whipworm (Trichuris trichiura), an infection they got from ingesting soil or water contaminated with feces of infected animals or people containing the parasite's eggs.

Responding to the rapid emergence of dangerous pathogens around the world, a new initiative to prevent or contain pandemics was announced in Davos, Switzerland, yesterday. If you ever worried that a highly contagious pathogen could take down your community, or the country, this news is for you.

Using mathematical modeling, researchers suggest weather and warming created the "perfect storm" that drove the Zika outbreak in 2016.
Starting in October, many Nexus 6P users have been experiencing a bug that causes their phone to completely shut down, even though there was 20% or more battery life remaining. At first, it was thought to be a direct result of the recent Android Nougat update, but a combination of factors indicate that this isn't necessarily the case—or, at least, it's not the only problem.

Drones are popular little toys, but they're not the easiest things to control. While hand gestures may not change that too much, donning a HoloLens and flying a physical object with a wave of your hand at least makes the process feel a lot more like a telekinesis.

Today I decided to try out a cool new DIY craft! But seriously, Superwowstyle and DIY crafts! Did you expect? Nah! Neither did I! But these bling shoes were a DIY fashion that I simply could not resist when I realized what potential these old shoes have. the shoes decoration just had to happen once the idea hit my head!

For those who like grilling fruit and desserts in general, we take it up a notch with this great video tutorial that shows you how to make a great dish from cooking Peaches directly on hot coals.

Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

If you're ever worried about your bObsweep's well being, you can always do a home check-up test to make sure all of bOb's parts are in working shape. As long as bOb has some charge, you can diagnose any potential issues by following the video guide for performing bObsweep Standard's check up test.

There are certain foods and beverages that can actually brighten your smile or improve your dental health when you chew or sip them. Once you understand their chemical properties or textures, you can look to items you already have in your cupboards or refrigerator to help keep your teeth looking and feeling their best.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Being the bearer of bad news is unpleasant; there's nothing more uncomfortable than offering up a spoonful of negativity. Whether you're a supervisor who spends a lot of time interviewing and rejecting candidates, or simply someone who has to say "no" to a friend, it's never fun to break bad news. But sharing unpleasant words or feedback with another person can become less of a burden with a few simple steps.
It's been rumored for months, but now we've got some official news about Google's newest music offering, YouTube Music Key. The subscription service will allow for an ad-free experience with background listening (i.e., having your screen off) and offline playback.

The Spanish and Portuguese introduced many things (some desirable, some not, depending on your POV) to Mexico in the sixteenth century: Christianity, language, and lots of flora and fauna.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

I know Americans love to hate on the French, but from my standpoint, they've given us a lot of things we should all be thankful for, like French kissing, casual sex, Pepé le Pew, and of course, French fries. Well, maybe not...

EXPAND YOUR VISION: So many people don't achieve their goals and dreams in life because they don't have a big enough vision for themselves. The biggest enemy lies within. Picture and see yourself achieving your goals, becoming financially independent, making yourself more valuable to the market place, or losing that excess weight that you have always wanted to lose.

Finding love is tough. Movies like The Notebook and Twilight have ruined the expectations of love and relationships for us guys. Some women's ideal love situation is being kissed by a glittery sparkling vampire. "I know we only met a few seconds ago, but I'm deeply in love with you."