Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know-how can change your memories for their own personal benefit, and you can do so to others, too.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Hello my fellow hackers, it's been a while since my last post, I can't get the time now-a-days for the posts but can manage to tend to comments.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

What's your top pet peeve? Open-mouthed chewing? Nail biting and knuckle cracking? The sound of silverware scraping? Or perhaps it's a bigger behavior, like leaving the toilet seat up?

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

The telecommunications industry has come a long way since Ma Bell opened the first telephone exchange in the late 1800s. With the advent of fiber optics and wireless broadband technology, we no longer have a need for a dedicated phone connection, as today's data networks can carry much more than a simple voice conversation.

Both the Galaxy S6 and S6 Edge have had root methods available to them before the phones were even released, but the problem with these existing root methods is that they would trip the KNOX counter on your device.

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

Without a comprehensive root method for all Android phones and tablets, a device-specific approach is needed. And since we always cover new rooting methods for all the popular phones here at Gadget Hacks, we've built this always-updated guide to rooting many mainstream Android devices.

If you've already read the first part exploring what geniuses actually eat as opposed to what the rest of us are told to eat for brain health, you've noticed that there are some big discrepancies. Instead of favoring healthy, wholesome foods high in antioxidants, lots of high-achieving types tend to go for caffeine, sugar, and processed foods. One notable health habit practiced by many: eating breakfast.

Welcome back, my apprentice hackers! In this series on password cracking, I have been attempting to develop your skills in the age-old art of password cracking. Although it might seem like a simple and straightforward exercise, those of you who have attempted password cracking know that there are many subtleties to this art.

With a root bounty of over $18,000 up for the taking, developers were highly motivated to get the AT&T and Verizon Wireless variants of the Samsung Galaxy S5 rooted. Legendary hacker George Hotz, aka Geohot, has won the race and can now step up to claim his prize.

A friend of mine has a crazy amount of Reddit karma and gold, and yesterday he let me in on his secret. This person, who will remain unnamed for obvious reasons, created a Python script called Reddit Karma Crawler that finds rising posts before they get too popular.

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.

While landing a job isn't the easiest thing in the world, you can probably blame your résumé for a number of lost opportunities. Writing up a cover letter and résumé is frustrating and time-consuming, but if you spend the time to get them right, the effort will drastically increase your chances of getting employed.

Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by developing your scripting skills.

Welcome back, my aspiring hackers! Those of you who've been reading my tutorials for some time now know that I am adamant regarding the necessity of learning and using Linux to hack. There is no substitute, period.

You probably already know by now that a custom Android ROM can change your user experience and give you what feels like a new OS on your device, and there's no shortage of them out there to try out.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

I've never had a black eye, but I was in a car accident that turned my entire ear dark purple a few years ago. Believe me; it was enough to get more than a few funny looks.

Why can't I see who is stalking my Facebook profile?

Last time, I showed how to start putting together an AC arc welder from scavenged microwave parts, focusing on the transformer modifications. Now, I'll show you how to finish up your DIY stick welding machine by fixing up the electrical system and performing the finishing touches.

Deep in the crevasses of the Songshan mountain range, an Indian dhyana master established the first Shaolin Monastery in 477 AD, seeking to spread the relatively new teachings of Buddha at the time. This monastery then bred the Shaolin monks, who are now popular for their incredible feats with Chinese martial arts, particularly with Shaolin Kung Fu.

There's definitely a lot of new things to get used to in iOS 6, with over 200 added features, but which ones stand out about the rest? Well, it all depends on what device you're using. Some features will only work on newer models, but most of the hidden features are accessible to all.

Tech tends to move forward without looking back, but that doesn't mean new is always better. One feature that dominated mobile phones in the late '90s had made a comeback thanks to Apple, and you can take advantage of it on your iPhone when making calls.

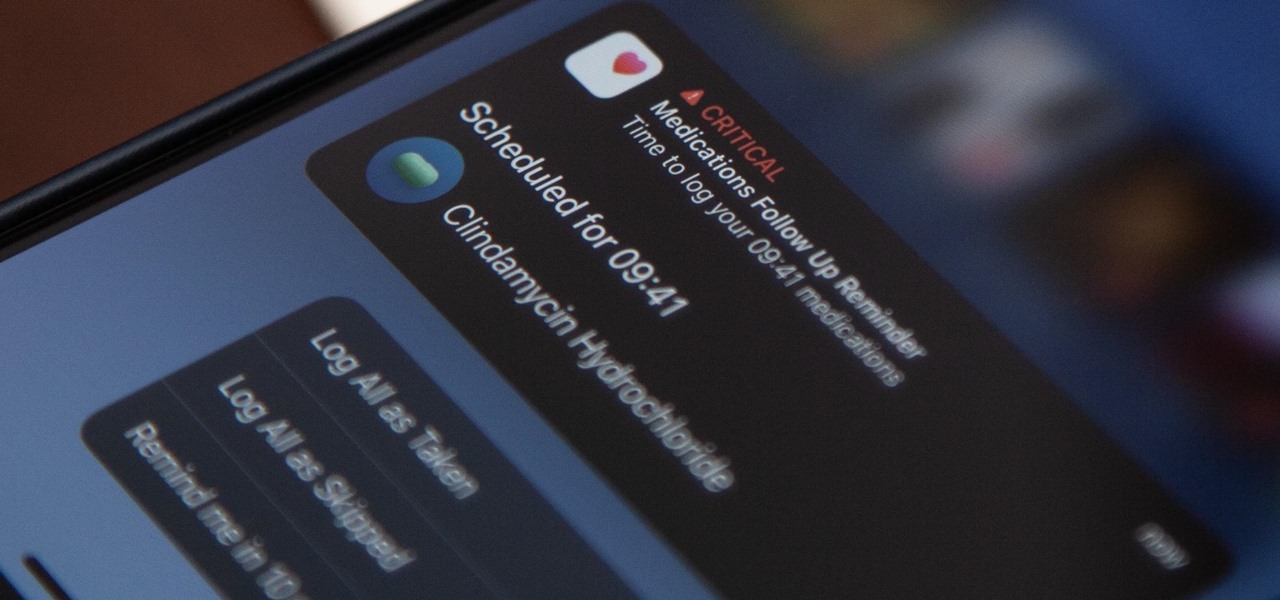
Since iOS 16, you've been able to add and track medication in the Health app, learn about potential drug interactions, and receive dose reminders. With iOS 17, Apple improves that last aspect with even more notification options to ensure you take your medicine on time and never miss a dose.

While most iOS updates will only improve the experience on your iPhone, some can cause more havoc than good. If an update unexpectedly breaks or degrades certain functions on your iPhone, you may be able to roll it back to the previous software.

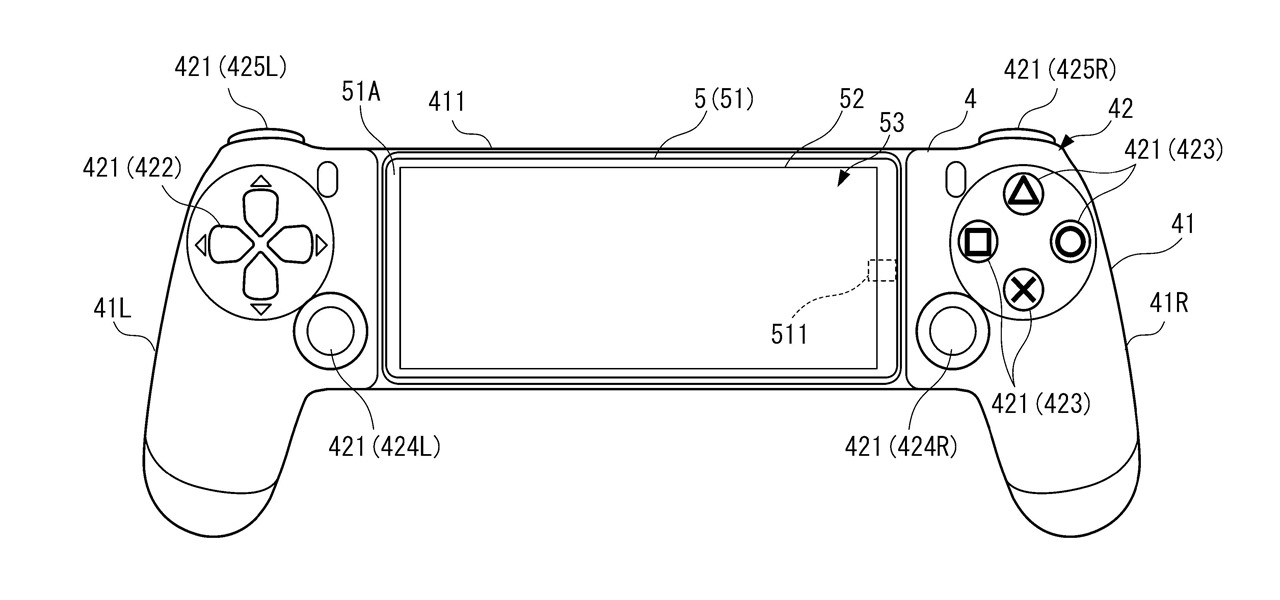
A new Sony patent shows the company doubling down on mobile gaming, and it could mean more advanced controller features for your iPhone or Android phone, similar to those in PlayStation's DualSense and DualShock controllers.

One of the primary assumptions in the world of VR and augmented reality is that the user has the ability to "see" virtual objects and the real world structures around them. But what if the user doesn't have perfect eyesight, or any eyesight at all?

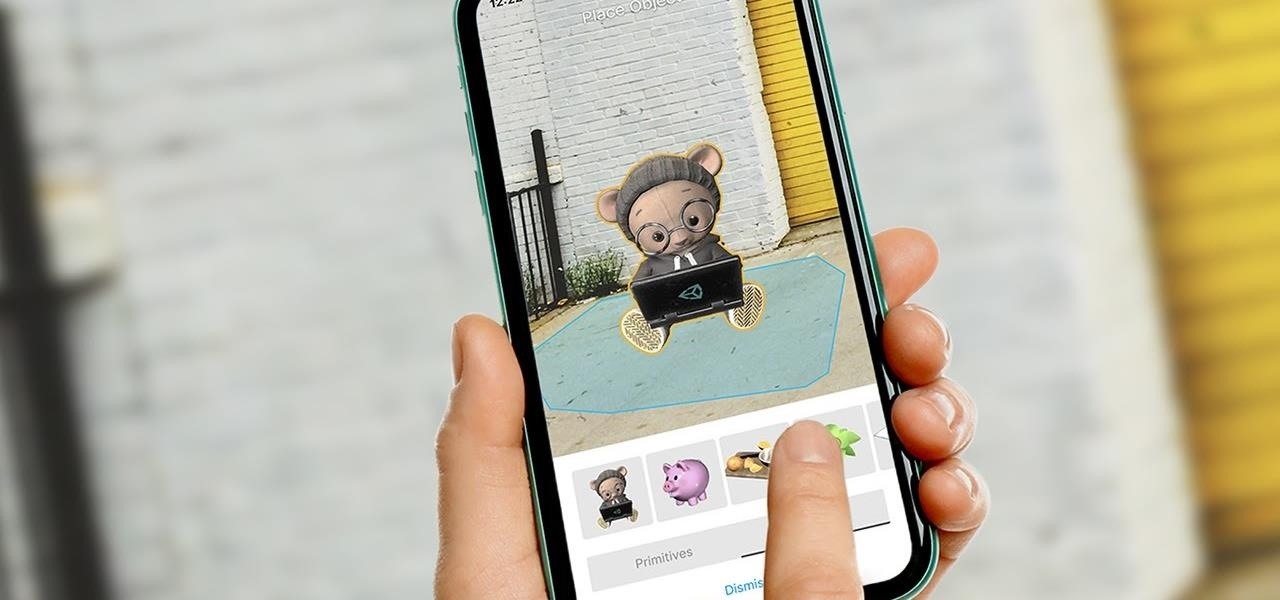
With the release of Object Capture this fall, Apple is giving everyone with a Mac and a camera the means to create their own 3D objects.

For awhile now, Google has offered the ability to translate text through smartphone cameras via Google Translate and Google Lens, with Apple bringing similar technology to iPhones via Live Text.

The COVID-19 pandemic has increased the demand for virtual and remote collaboration, and Microsoft has a solution that may serve as the catalyst for more such apps for augmented and virtual reality in the near future.

Apparently, we learned nothing from Jurassic Park, as scientists are still working on bringing extinct species back to life. Until that day comes, you can interact with long-lost animals through augmented reality...if you have a newer model iPhone.

Unity often reminds us that the majority of AR apps and experiences are built with the Unity 3D engine, and now the Unity MARS service, which facilitates easy AR creation for seasoned coders and newcomers.

I must admit, upon learning that the NFL was broadcasting the contest between the New Orleans Saints and Chicago Bears on CBS, Amazon Prime Video, and Nickelodeon, the latter was the only option I wanted, purely for the novelty of the experience.

The latest generation of Spectacles aren't AR smartglasses per se, but Snap is intent on demonstrating that the wearables are capable of storytelling powered by augmented reality.

The iPhone 12, 12 mini, 12 Pro, and 12 Pro Max are capable of shooting 4K video using HDR with Dolby Vision, producing content unthinkable in an Apple smartphone just years ago. That said, it's quite easy to miss the full potential of your iPhone's camera, iPhone 12 or not. If you want the best quality video possible on the iPhone XS and newer models, make sure you don't make this one mistake.

You're out and about, and nothing on your iPhone will load. A glance at the settings shows a saved Wi-Fi network with full bars that your iPhone had connected to automatically, but you're not getting any internet. If you've experienced this, you're not alone, and there's something you can do about it. You'll even increase privacy and security on your iPhone in the process.