Nvidia has emerged as the indisputable leader in chips for Level 3 and even more advanced driverless applications, catching some of the world's largest semiconductor makers and automotive suppliers by surprise.

Facebook really wants us to use Messenger. For the most part, they've succeeded; theirs is one of the most popular messaging apps right now. And with yesterday's announcement of new features, Facebook is only going to make their flagship chat application better.

An outbreak of anthrax from contaminated meat in Tanzania sickened dozens of people and moves the danger of this deadly bacteria back into focus.

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

Back in August, Google introduced Android Device Manager. This new service allowed you to locate, lock, or wipe a lost or stolen Android device from either a companion app or a web interface. Effectively, this is the "kill switch" that legislators are clamoring for.

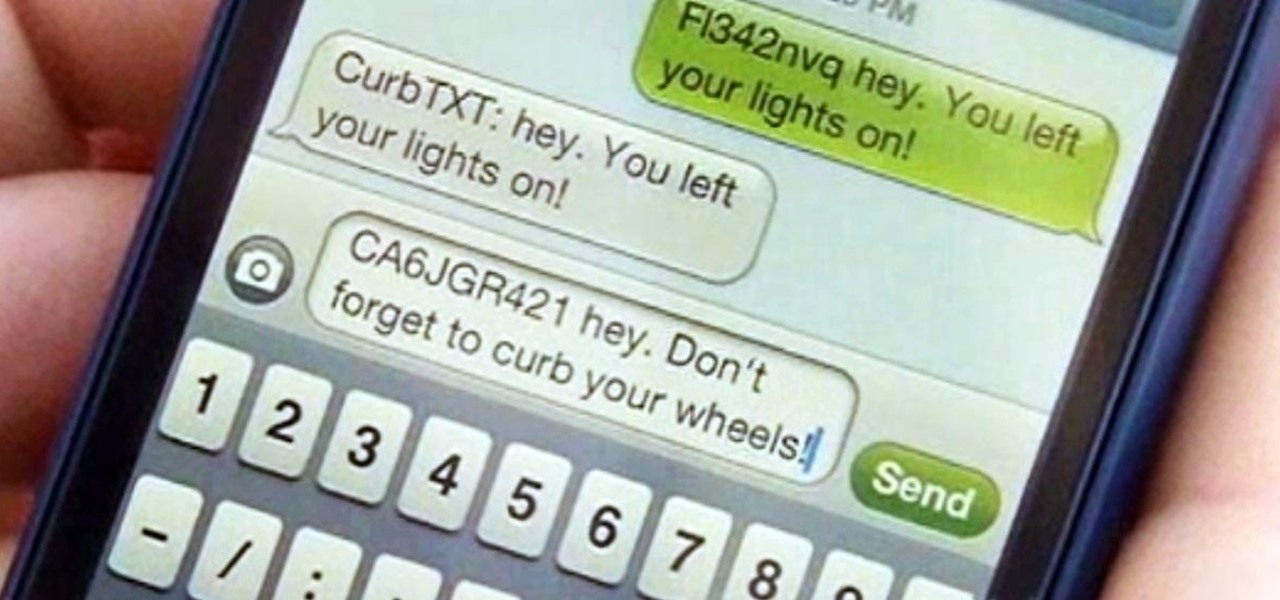
Parking. Ugh. Parking is about as fun as running through a swarm of bees while being chased by a pack of wolves from The Grey.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

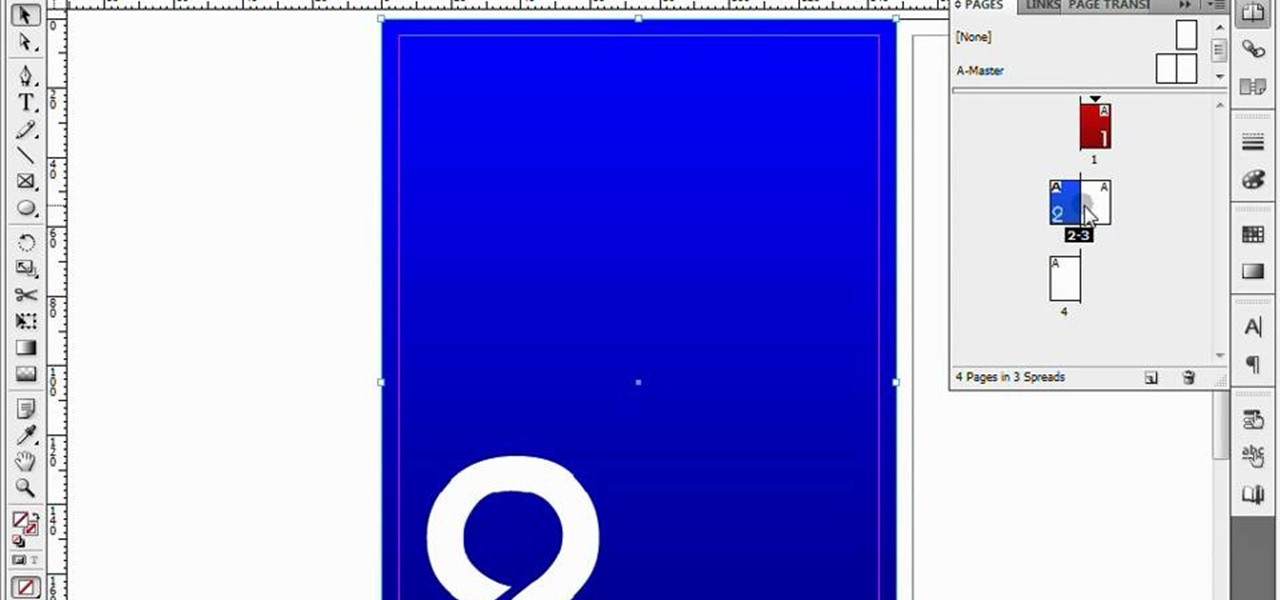
This tutorial will explain how to make buttons and links to flip between pages in InDesign files. Create sleek looking, easy to use documents that can be used as websites or PDFs. This video will show you how to use InDesign to its full potential.

Your baby is ready to be born - but there can still be problems with delivery. A breech birth, macrosomia, or cord prolapse can all require an emergency c-section. Be prepared for potential delivery problems in advance, by watching this video.

Wiping our shoes off as we enter the home reduces the amount of contaminated dirt tracked in. Large mats, that cover two or three strides, will ensure that even those that refuse to wipe will leave most of the dirt clinging to their shoes on the mat rather than your carpet.

If you think you might be a likely target of a black-hat hacker, there's a new iOS security feature that offers extreme protection for your iPhone against spyware, phishing attempts, and other highly sophisticated cyberattacks.

Confused by TikTok? Trying to grow your Instagram fanbase? Aiming to create the perfect Facebook ad? Growing an audience might be challenging, but with the right strategies, it is possible — and fun.

The words of three of tech's most important executives in the last 48 hours are providing some valuable insight into the near term future of augmented reality and the cloud infrastructures that support it.

After stealing the show at the HoloLens 2 launch and starring in Qualcomm's unveiling the Snapdragon XR2, holographic video conferencing app Spatial has landed a leading role in Magic Leap's second act with the enterprise segment.

Dark mode themes for mobile apps are all the rage these days, but YouTube is taking that a bit literally with its latest augmented reality experience.

For Snapchat users wondering if that selfie is ready to send to their crush, independent Lens Studio creator Andrew Mendez created a handy tool called the Smile Rater.

After testing the waters with a few pop-up stores along the West Coast earlier this year, North is bringing its smartglasses to more cities across the US and Canada.

In just a few weeks, on May 29, the annual AWE (Augmented World Expo) conference will take place once again in Silicon Valley (Santa Clara, California, to be exact).

While the tech industries giants and eager startups chase the dream of widespread consumer augmented reality, enterprise AR is living the dream today.

As the stigma of online dating fades and swiping potential suitors on your phone becomes the new norm, one very real issue that you may have to deal with is catfishing: the act of being deceived by a fictional online persona. Although dating apps do their best to weed out fake accounts, a few of them slip through the cracks and take advantage of innocent people just looking for a connection.

The thrill and excitement of great tourism generally requires visitors to take part in the country's local fare in person. But Air New Zealand's new augmented reality experience for the Magic Leap One gives visitors an immersive taste of what the country has to offer without ever setting foot in the country.

Four months after unveiling the latest productivity apps for the HoloLens, Microsoft now has a series of compelling real-world use case videos showing how the augmented reality device and its apps are helping oil giant Chevron.

Your childhood "social networking" may have been to go outdoors to the neighbor's — and outdoors is a great place for kids to be. But these days, the terms educational, digital media, entertainment, and toddlers don't have to be mutually exclusive. Like most things in life, it's about balance, and these apps can aid your child with social-emotional development when not playing with friends.

Now that the iPhone XS is officially available for pre-order, Verizon and Apple are giving Snapchat users the opportunity to win the device through an augmented reality scavenger hunt rather than forking over $1,000 for one.

On Wednesday, the tech world woke up to fairly shocking news with the announcement that AT&T would be the exclusive wireless carrier for the forthcoming Magic Leap One, as well as an investor in Magic Leap.

For years, Magic Leap has promised to deliver stunning augmented reality experiences that will outperform any other competitor, and a newly revealed partnership hints that the company may be able to deliver on those promises.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Part of the Star Wars: Jedi Challenges experience that was once exclusive to users of Lenovo's Mirage AR headset is now available to anyone with an ARKit-compatible iOS device.

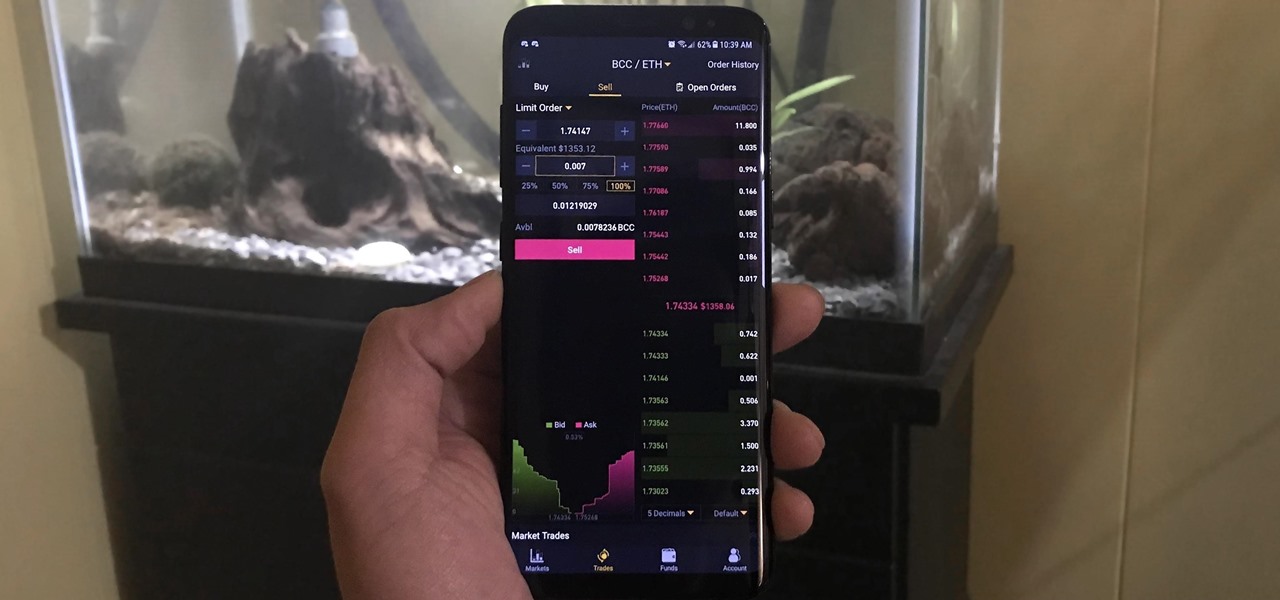
Selling alt-coins like Stellar (XLM) or Ripple (XRP) in exchange for more widespread coins like Ethereum (ETH) or Bitcoin (BTC) can be a daunting task if you're new to cryptocurrency. Though you'll still need to do your research to avoid potential disasters, Binance takes the hassle out of trading digital currencies on your smartphone.

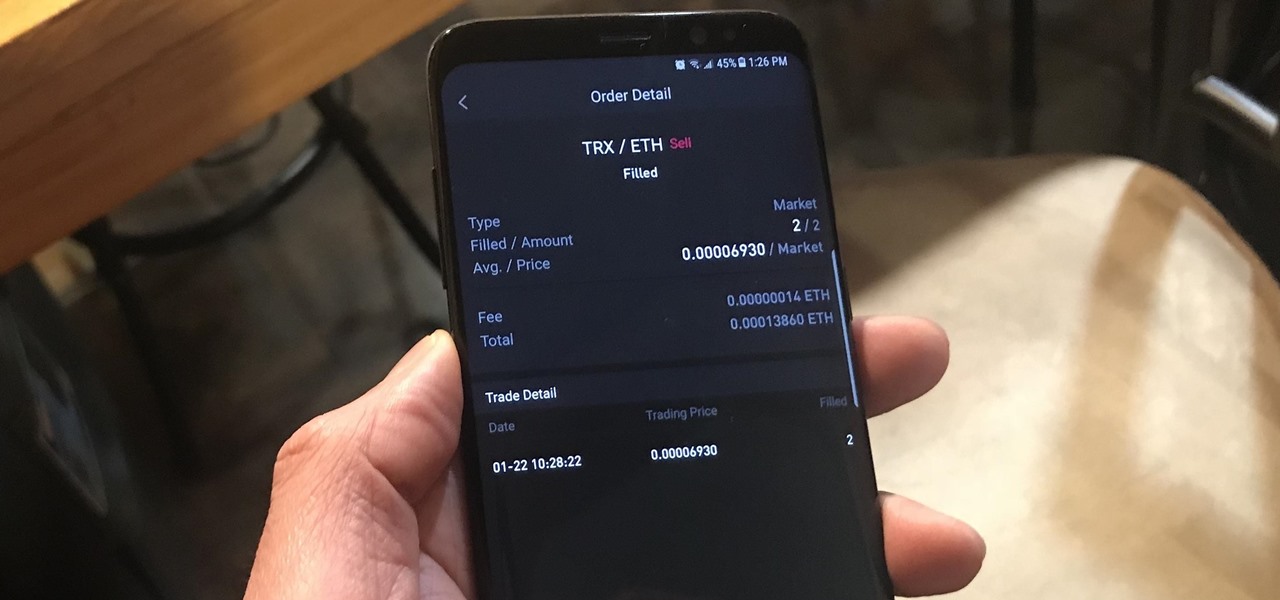
Using Bitcoin (BTC) or Ethereum (ETH) to buy alt-coins like TRON (TRX), Stellar (XLM), or Ripple (XRP) can seem intimidating if you're new to cryptocurrency. Though you'll still need to do your research to avoid potential disasters, Binance takes the hassle out of trading digital currencies on your smartphone.

The Star Wars saga may have occurred a long time ago in a galaxy far, far away, but Nissan is using a futuristic technology to bring stormtroopers and droids into its dealerships.

With the recent launch of the LG V30 and the Pixel 2 XL, LG has reintroduced the world to POLED. This display tech was showcased at CES 2015 and billed as a rival to Samsung's AMOLED displays, then promptly disappeared from the market for two years. But now that two of the biggest flagship phones this year are using the technology, many folks will be wondering what makes POLED different.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

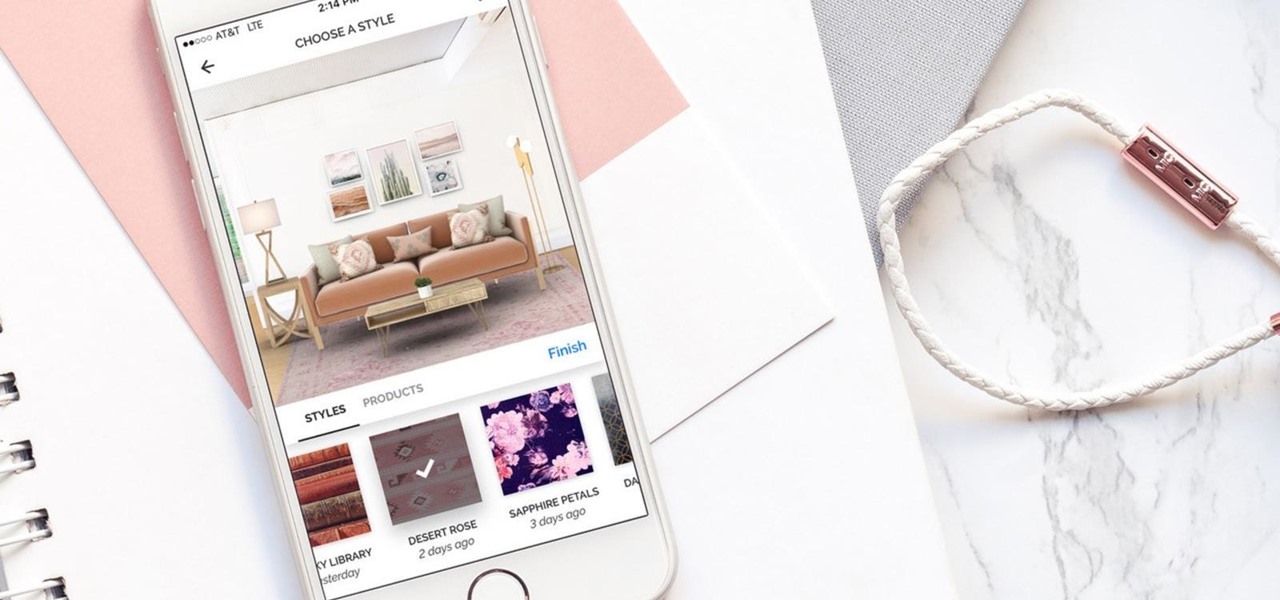
Hutch Interiors, Inc., makers of an eponymous augmented reality home design app for iOS and Android, has closed a series A round of funding, led by online real estate company Zillow Group, totaling $10 million.

Today in Santa Clara, California, at the Augmented World Expo, Scope AR revealed a major new update that will add markerless tracking for their remote assistance application, Remote AR, on standard devices.

UPDATE 5/12: According to Bloomberg, it looks like the merger is on. Anonymous sources claim discussions have already begun about consolidation. Looks like there might be a new 5G powerhouse after all.

Intel launched their Advanced Vehicle Lab in Silicon Valley this week, and the tech giant is now on the hunt for potential partners.

Beware: After a new caucus — the Congressional Caucus on Virtual, Augmented, and Mixed Reality Technologies for the 115th Congress — formed in the US House of Representatives, the government has decided to go after all mixed reality head-mounted displays. The HoloLens, Magic Leap — nothing is safe anymore.