Why do you need augmented reality? Because enterprise, they say. And while that's certainly true for several disciplines, there's still that mainstream use case hanging out there waiting for users to discover beyond the realm of enterprise and gaming.

Since the Razer Phone's announcement in 2017, we've seen a new subgroup of phones emerge. Gaming phones are now a thing, leading to companies like ASUS creating phones that are thoroughly optimized for the mobile gaming experience. And with their second iteration, they perfected it.

The "controversial" Pixel. No phone in the history of Google's Pixel lineup deserves this title more than the Pixel 3 XL. For some (including myself), the design is a welcome change that embodies the modern design of 2018 flagship phones. For others, it has an ugly huge display notch that destroys symmetry.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

Straight out of the box, the Nexus 5 is an awesome device, but even it can be faster with better battery life. Luckily, one of the things that makes it so awesome is that there are tons of developers creating mods for it, since it runs stock Android by default. When it comes to gaining speed and better battery life, flashing a custom kernel is the way to go.

Apple has finally given Control Center the love that it needs with an updated interface design and more customizations than ever before. Taking the more customizable overhaul one step further, iOS 18 and iPadOS 18 have elevated controls beyond Control Center, so you can use controls from other places on your iPhone or iPad for even faster access to your most-used shortcuts.

So, someone on your shopping list has an iPhone. Lucky for you, Apple's line of smartphones are practically made for accessories. From AirPods to adapters, there's something for every iPhone user in your life. Are you feeling overwhelmed by the options? You've come to the right place.

Whether you're in an airport, restaurant or waiting room, the insidious grip of televisions on human life is omnipresent. Sometimes it's nice to talk to other human beings while looking at them directly—actually hearing what they have to say.

One of the biggest and most important appliances in a home is the furnace. It's the one source of heat that can't be unkept. Changing the filters, or cleaning the filters, on a regular basis is key to making sure your furnace is pumping out the heat properly. Keep your furnace working as efficiently as possible by following these simple steps.

Electronics seem to fail on you at the worst moments, don't they? Luckily, if your iPod freezes, there is a quick and easy fix. Check out this video and learn how to reboot your iPod on the spot and solve many issues.

If you're in the market for a new lawn mower, there are plenty of options, and it might be hard making a decision on which one is right for you. This video breaks down what you need to consider before buying a lawn mower and how to find one that best fits your needs.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

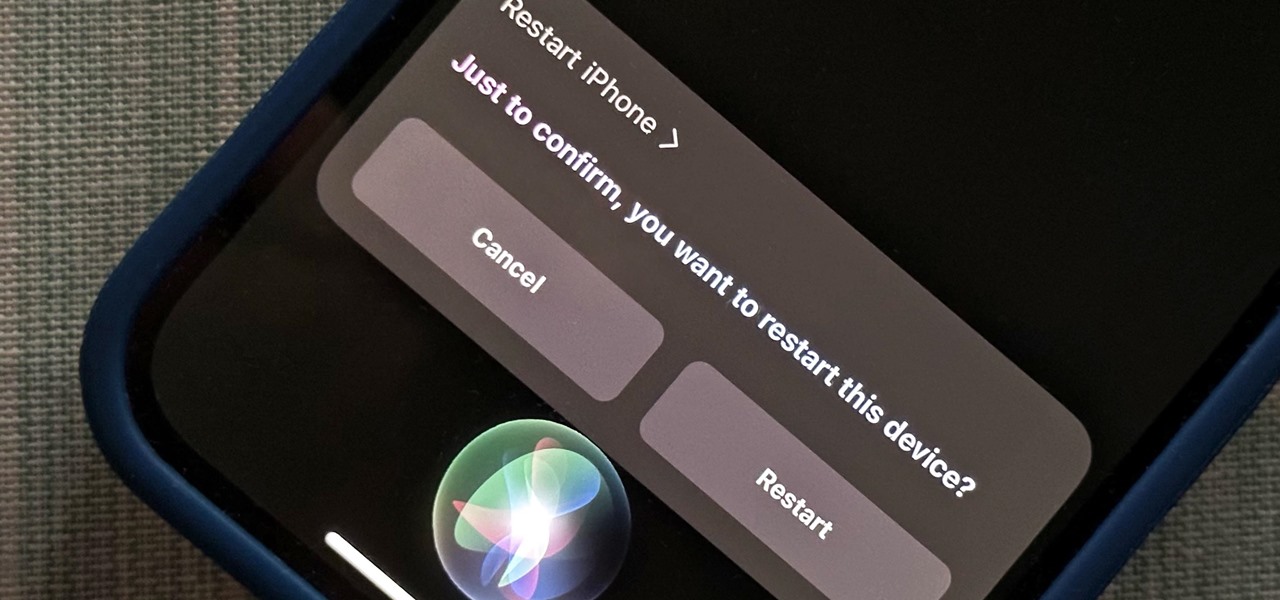
The iPhone 15, iPhone 15 Plus, iPhone 15 Pro, and iPhone 15 Pro Max are Apple's most powerful iPhones to date with features like USB-C connectivity, improved camera capabilities, and faster CPUs. But no matter how impressive these phones are, they can still freeze, become unresponsive, or get stuck when powering on — and a force restart is how you get things working again.

Siri can perform many actions for you on your iPhone, such as sending messages, providing information, getting directions, looking up a contact, and playing music. Still, there are even more important Siri voice commands that every iPhone owner should know — even the ones who hate Siri.

The story of the HoloLens has been a mix of work and play. But while many developers have devoted time to creating gaming and entertainment apps for the HoloLens 1, with the HoloLens 2, Microsoft has been encouraging everyone to focus more on the enterprise side of things.

If you've spotted an unintended Ethernet connection and wondered what you could do with all of the information coursing through those wires, there's an easy way to hack into it and find out.

Recovery mode and download mode are useful for modding and they can come in handy in a pinch. Booting into recovery mode to do a factory reset or wipe cache fan save your Galaxy S20 from a soft brick, and entering download mode lets you install firmware with utilities like Odin and Smart Switch.

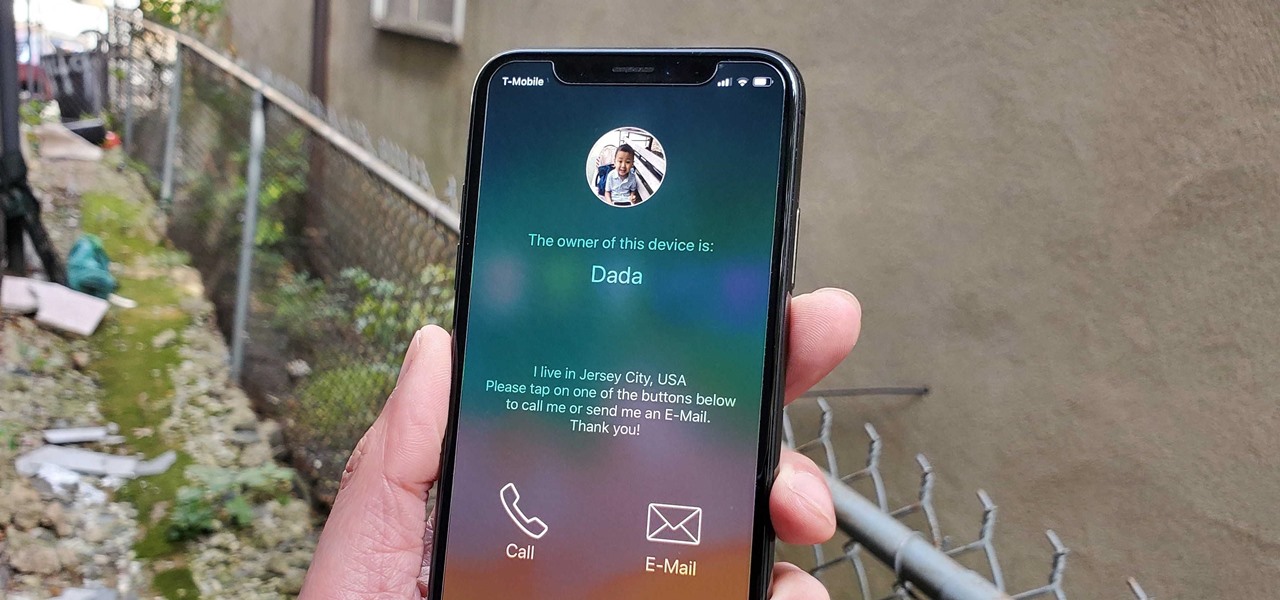
The prospect of loss or theft is something we constantly live with. Stolen iPhones fetch a premium price on the black market for parts like OLED display assemblies, frames, and charging ports. Making matters worse, if someone were to steal your phone, they could simply turn it off to avoid anti-theft features like Find My iPhone.

The OnePlus 7 Pro is truly the best phone that the company has ever created to date — it's even one of the hottest phones around regardless of OEM. It offers an awesome display with minimal bezels, a smooth 90-hertz refresh rate, a pop-up selfie camera, and the best triple camera system in a OnePlus phone so far. It can truly compete with other flagship phones while keeping the cost down.

The natural marriage between fashion and augmented reality is charging onward, but not just from the major brands we already know about.

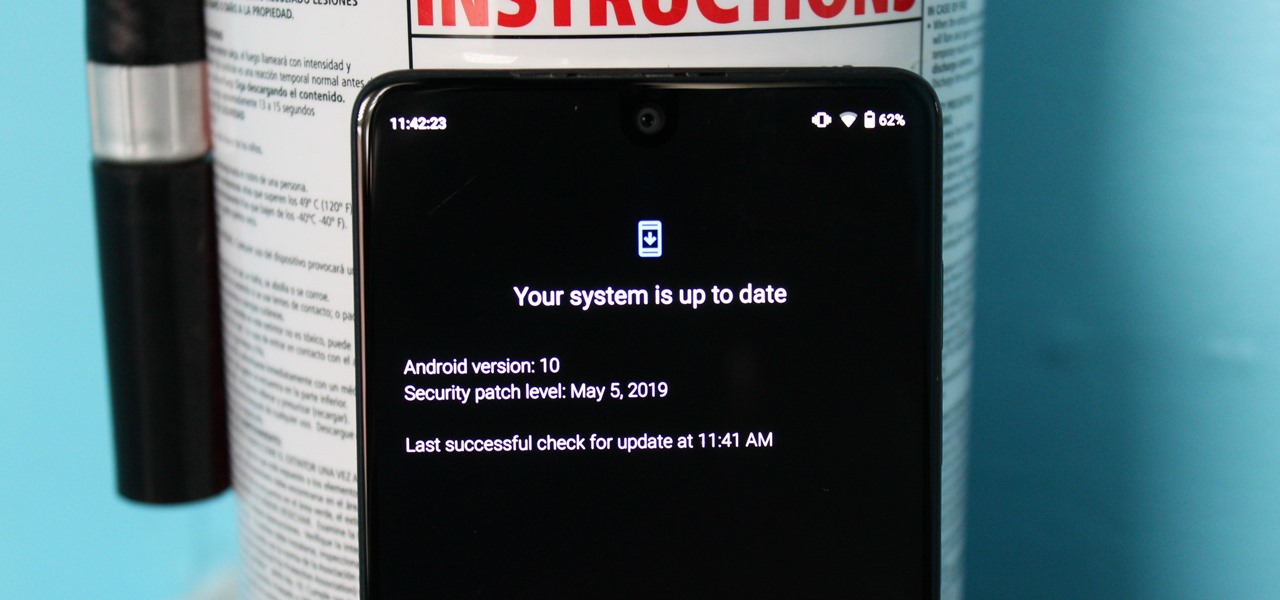
Like last year's beta release of Android Pie, Google has allowed the Android Q Developer Previews to support some non-Pixel devices. Announced at Google I/O 2019, there are 15 non-Pixel smartphones eligible for the Android 10 Beta, including 2017's Essential PH-1.

It's no secret that Google is all about AI. In their eyes, machine learning is the future of software development, and you can see evidence of this all over the last couple Android updates. They've used it to power all sorts of features in their Pixel phones, and they've even donated some of their AI smarts to AOSP for all Android manufacturers to share. But it looks like Samsung isn't exactly on board.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2018 selection of hacker holiday gifts.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

In this jam-packed October, the Huawei Mate 20 Pro has flown under the radar in the US. Due to Huawei's lack of presence in the States, many are unfamiliar with the second largest OEM in the world. Huawei has continuously put out amazing mobile devices, and this year they released a phone that's nearly perfect on paper.

It wouldn't be iPhone season without a new controversy. Chargegate, Apple's latest PR nightmare, is the name being used for charging issues on some iPhone XS and XS Max devices. If you plug in your iPhone at night — or whenever — then wake up or come back later and see that your iPhone has even less battery power, you're affected. But there is a fix you can implement right now.

The on-screen gestures on the iPhone X have taken touchscreen interaction to a whole new level. While they're needed due to a nearly bezel-less display and lack of a Home button, you can actually get these iPhone X-exclusive swipe gestures on any other model iPhone. The only catch is that you need to be jailbroken.

While Vuzix is beefing up the processing power of its next-generation smartglasses with the Qualcomm Snapdragon XR1, the company will also give its devices an upgraded display engine.

Microsoft's Monday keynote introduced the fourth generation of the company's Kinect sensor during Build 2018 in Seattle.

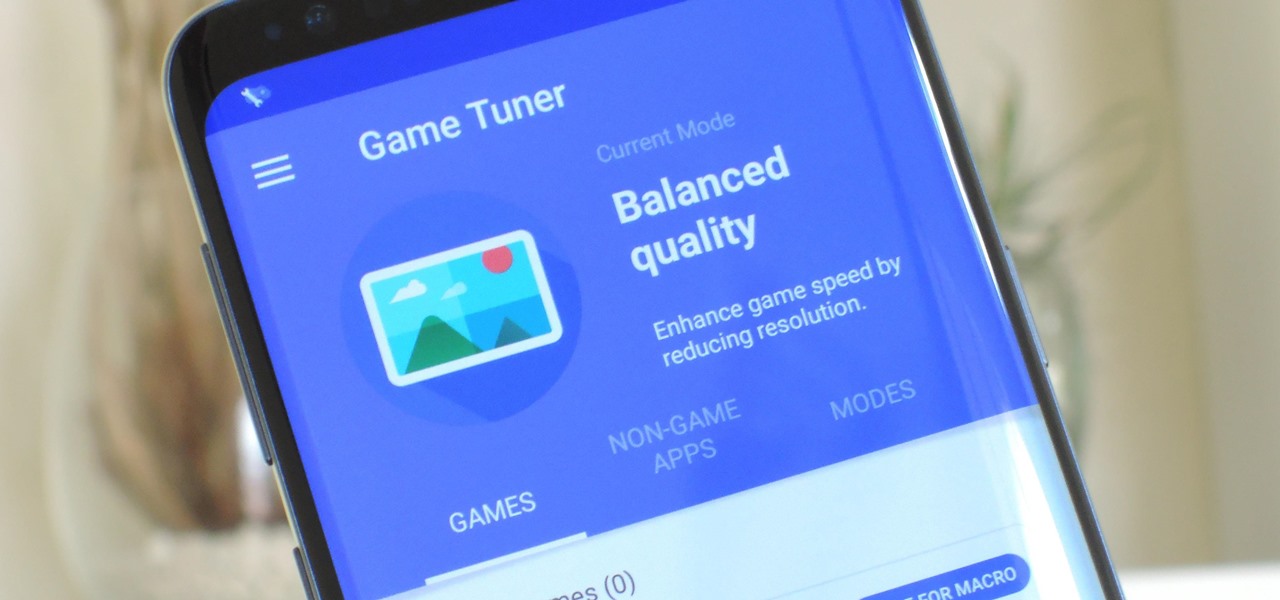
Samsung's Galaxy S9 is a powerhouse, driven by the Snapdragon 845. Still, this SoC lags behind the A11 Bionic chip that's inside the iPhone X — meaning you'll need a few tricks in order to squeeze out some extra performance from your phone. Fortunately, there's an app made by Samsung that will help you do just that.

Following in iOS 11's footsteps, Android 9.0 Pie will include a security feature that lets you immediately disable the fingerprint scanner as well as extended Smart Lock features. After initiating the feature, you will be required to insert your PIN, pattern, or password before any other unlock methods will work again.

In a LinkedIn post published on Tuesday, Microsoft's leading advocate for the HoloLens made a prediction that the mixing of immersive technologies will define augmented reality in 2018.

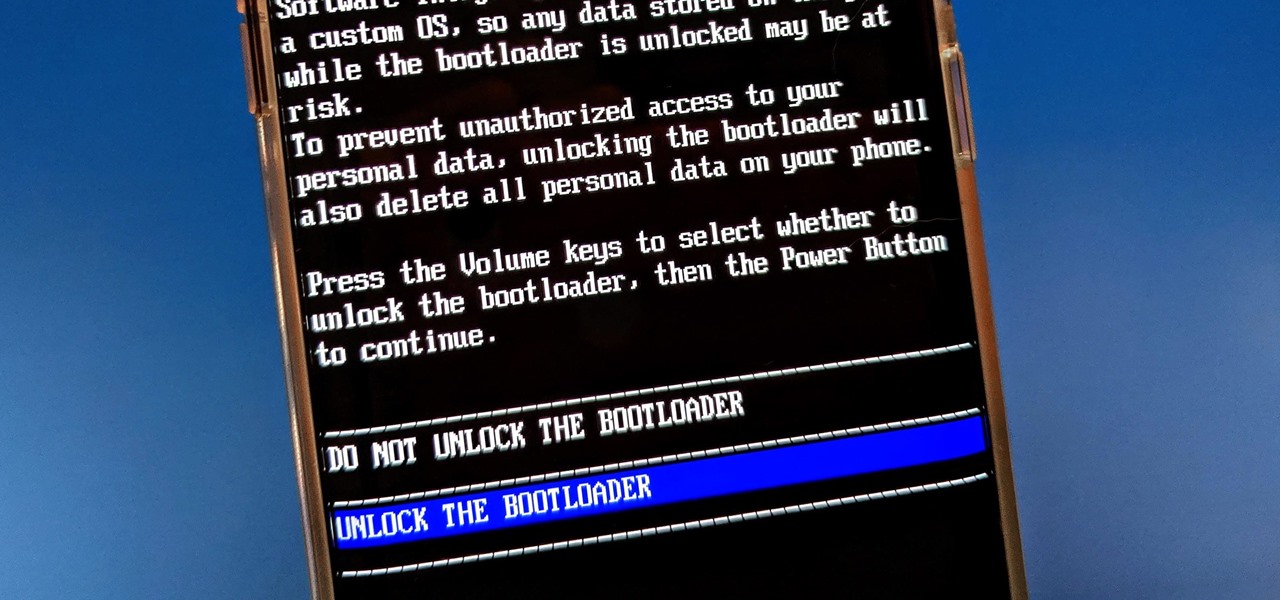
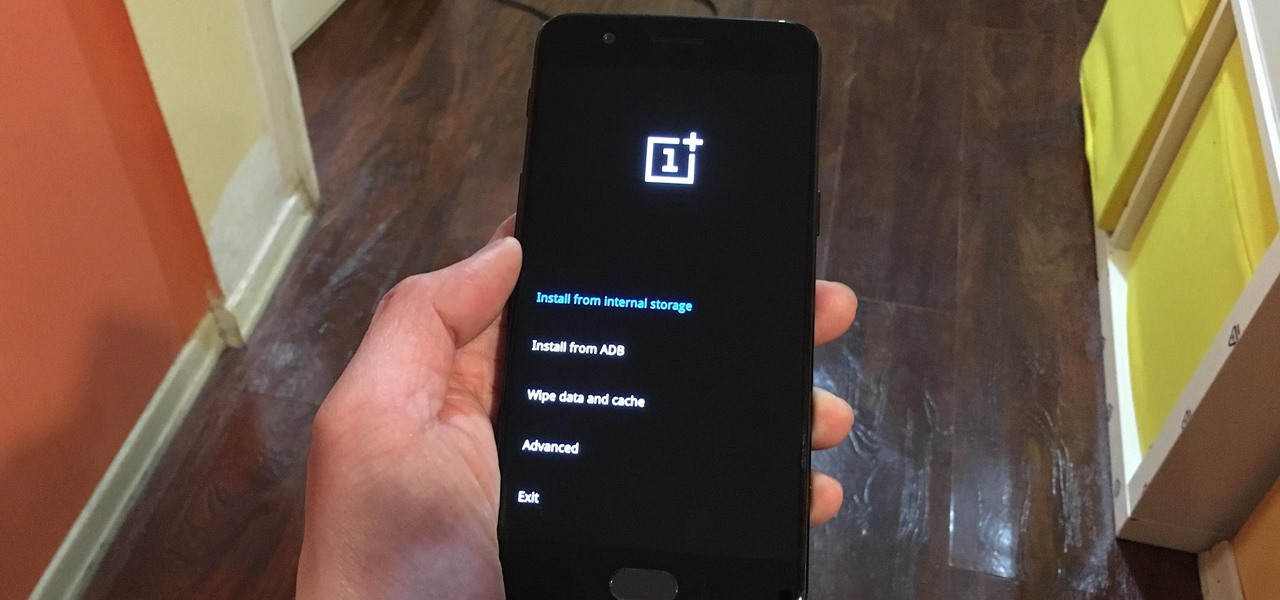
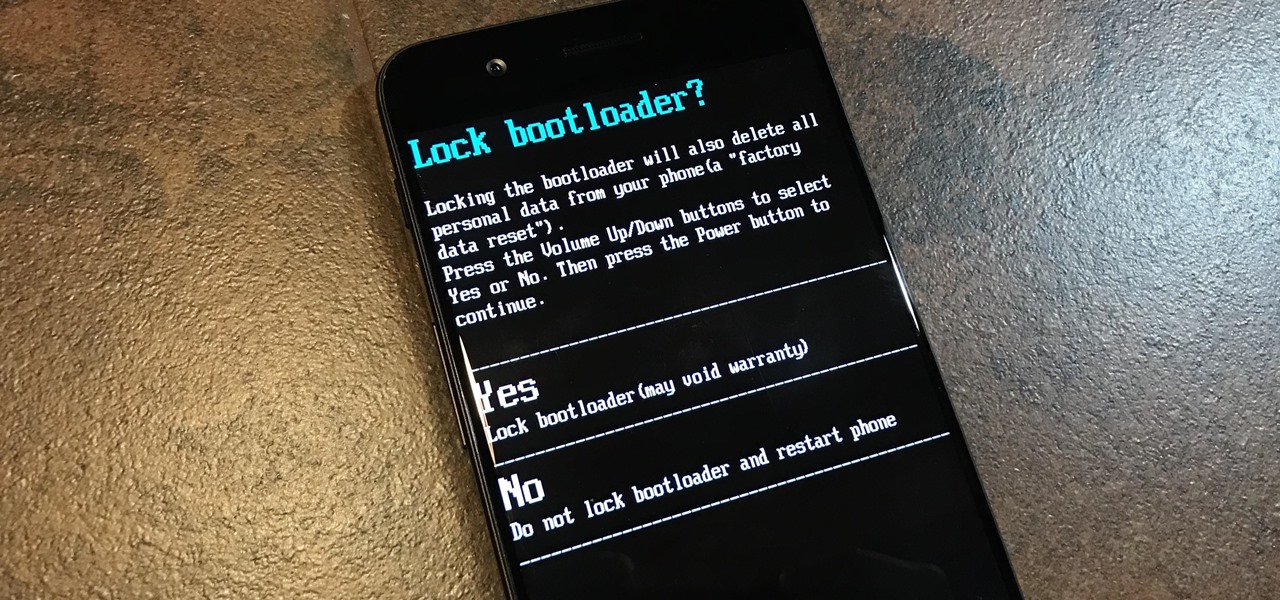
Both the OnePlus 5 and 5T have two pre-boot menus that every owner should know about: Recovery mode and bootloader mode. The recovery screen lets you wipe cache, perform a factory reset, or install firmware, which can help save the phone from a soft-brick. Bootloader mode, on the other hand, lets you send Fastboot commands via PC or Mac to lock or unlock your bootloader or flash images.

To please those of us who love to mod and root our Androids, OnePlus has made both the OnePlus 5 and 5T relatively easy to customize — so much so that the 5T topped our list for the best phones for rooting. Unfortunately, unlocking the bootloader and using root to modify the firmware on your OnePlus 5 or 5T makes it hard to update to a new firmware such as Oreo when compared to stock.

As smartphones become more accessible, billions of people have come to depend on their features for daily life. One of the most important aspects these days is the camera. OEMs have been working for years to improve camera quality, and they seem to have finally figured it out — the best way to achieve DSLR-quality photos wasn't just with better sensors, but with better intelligence.

Cyber Week 2017 is still upon us. If you're looking for an iPhone X deal, you might still have time to score one. But maybe you already have — a reported six million people purchased the newest iPhone over the Black Friday weekend. If you're one of those lucky millions, there's a slight learning curve to using the X over other iPhone models.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

Google might be taking the lead on artificial intelligence in smartphones with their latest announcement, MobileNets. MobileNets is a series of TensorFlow vision models built for mobile devices, described by Google as "mobile-first."